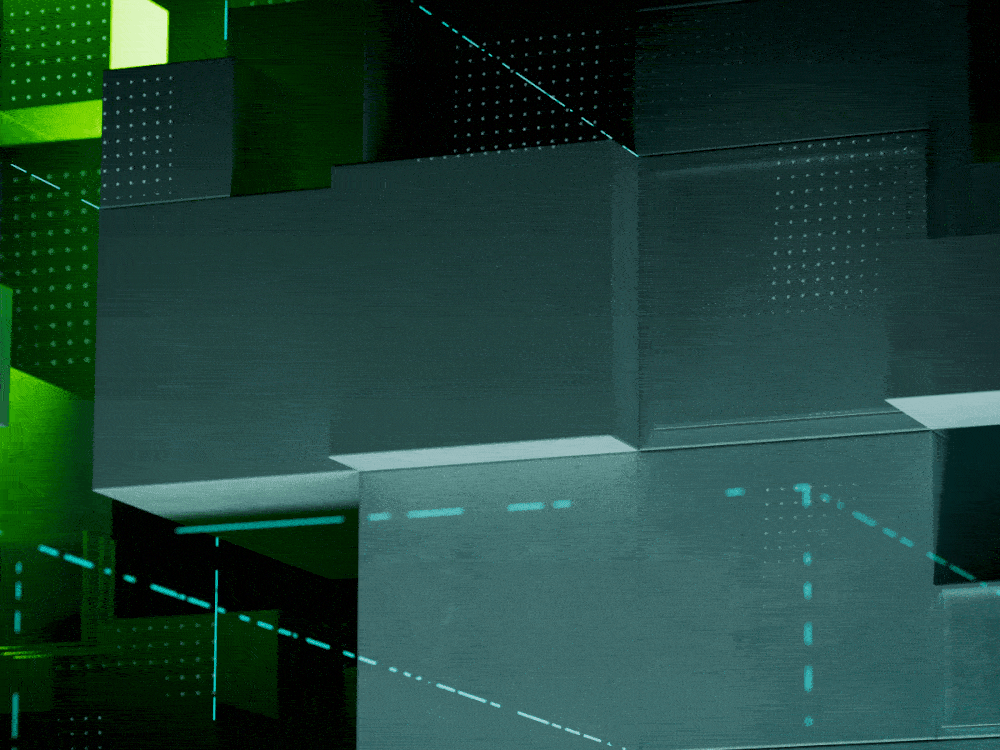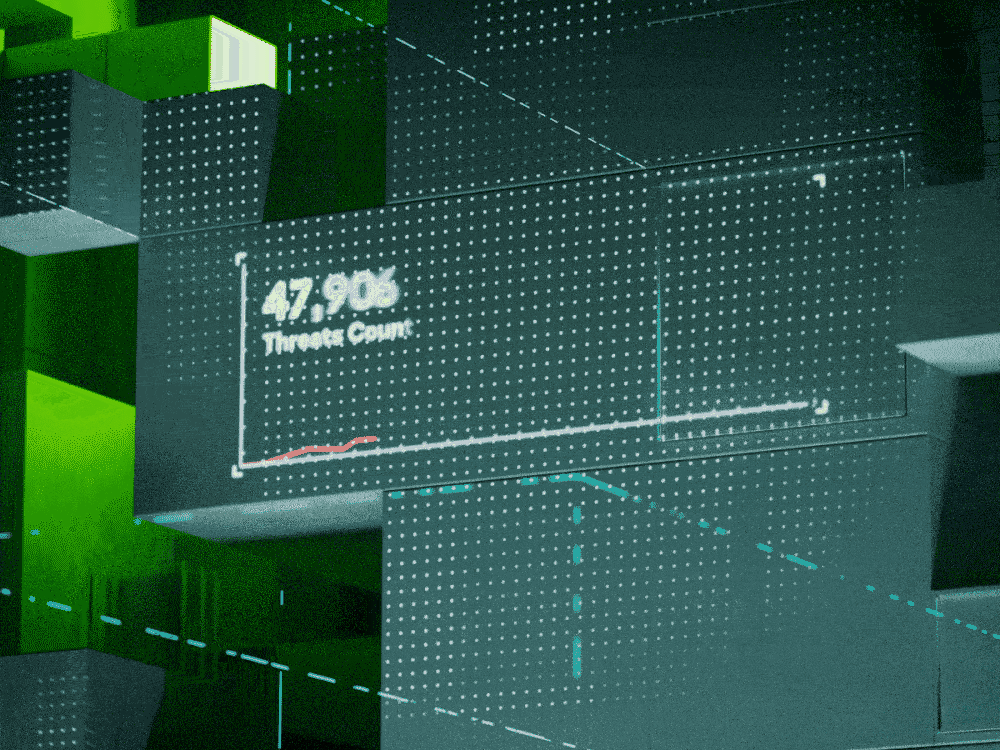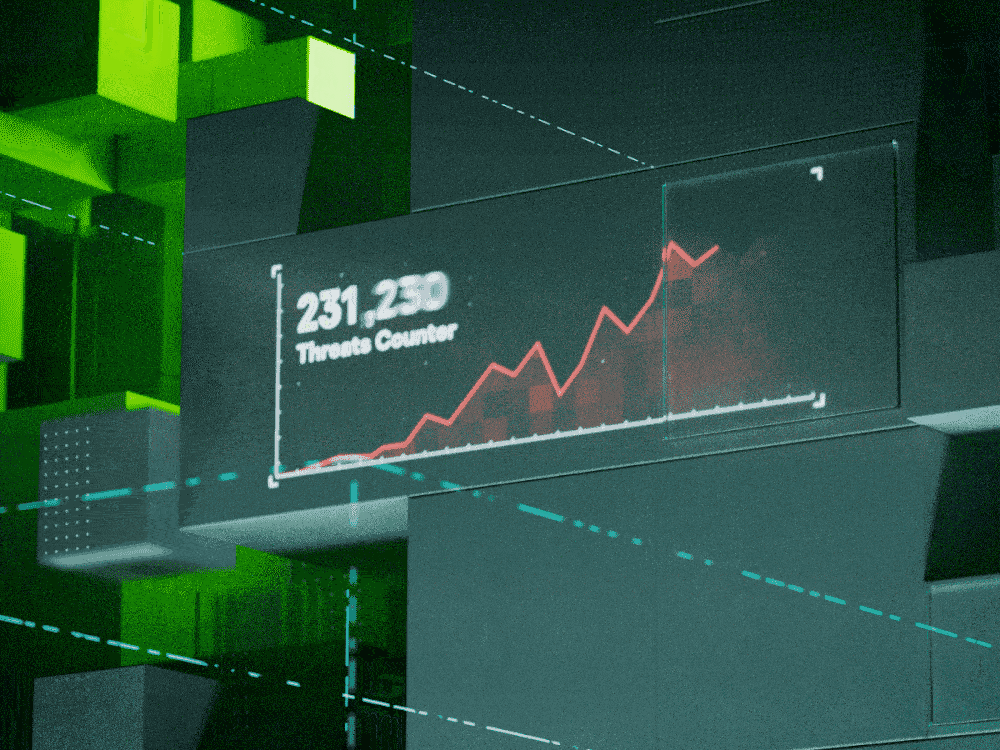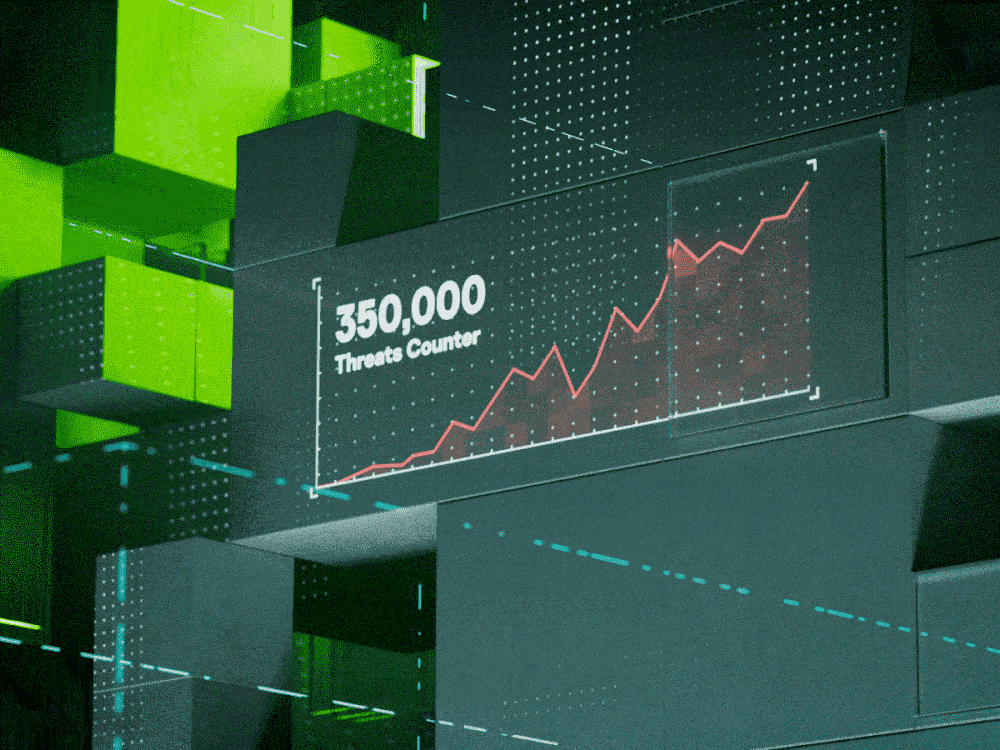
Tech is now your business – whatever your business. Senior executives must be thinking of cybersecurity as an urgent strategic issue. But the landscape is jargon-filled and constantly evolving. We explain in everyday language nine of today’s biggest threats to business, so you can be fearless and focus on the future.
1. Attacking low-hanging clouds
As businesses use more cloud-based applications and data storage, don’t rely on your cloud provider for security. You need your own cybersecurity too.
Kaspersky research found just 47 percent of enterprises using public cloud have tailored protection. Without it, their clouds are vulnerable to expensive data breaches through low-hanging entry points like weak passwords.
What to do:
If your business relies on the cloud, cloud security must be a board-level priority. You should also have endpoint security and cybersecurity training as essential budget lines. And remember, you’ll need Security-as-a-Service (SaaS) when migrating to the cloud.
2. Holding your data to ransom
Every day in businesses worldwide, employees find when they try to use work resources, a cybercriminal has locked everything they need and is demanding payment for access.
It’s called a ransomware attack, and they’re common. Research by IDC showed a third of businesses had a ransomware attack in the past 12 months with an average ransom payment of 250 000 US dollars.
What to do: Pay attention to this type of cybercrime before it happens. Plan your organization’s ransomware response and get free anti-ransomware tools from No More Ransom.
3. Manipulating your people
Social engineering is a form of cybercrime using techniques to trick employees into handing over sensitive information, spreading malware or giving access to private systems.
It may sound like something no smart employee would fall for, but it happens all the time. Nine out of 10 cloud data breaches use social engineering. These kinds of attacks can cost an enterprise over 2 million US dollars.
As technology gets more sophisticated, so do cybercriminals. Attackers now use artificial intelligence (AI) to manipulate people with sophisticated impersonations. With a ‘deepfake‘ impression of someone important like the CEO, cybercriminals can manipulate employees into doing almost anything.
What to do:
People are your biggest risk and your best defense. Building a cyberaware culture throughout your organization defends against social engineering attacks. By training employees to be more aware of cyberthreats, you’ll build safe habits and lower the risk of attack.
4. Getting in through trusted sources
In supply chain attacks, cybercriminals insert malicious code into trusted software or hardware. Through this type of attack, they can use any application, software update or equipment as a ‘Trojan horse’ to launch an attack. The threat may then spread from your system to other companies you work with.
What to do:
Empower security from within. Improving cyber hygiene across the board helps close loopholes like weak passwords, lacking security protocols and insecure software. Read more on how to detect and prevent supply chain attacks.
5. Lying in wait for the right time to strike
An Advanced Persistent Threat (APT) involves sneaky, sophisticated hacking techniques.
They often hide malicious software in your system for long periods, stealing information or waiting for the moment to cause maximum damage.
APTs usually target big enterprises or nation-states, but they can also affect smaller companies in the supply chain. Cybersecurity skills cooperative SANS Institute found 48 percent of enterprises say they have a gap in detecting advanced threats.
What to do:
Arm employees with the knowledge they need to protect your organization. Get APT threat reports on SecureList.
6. Turning off your business
Distributed Denial of Service (DDoS) attacks are the cybercriminal’s go-to targeted attack. They overwhelm a server, service or network with a flood of traffic, so you can’t give your customers reliable online service. They may aim to essentially shut your company off from network systems like servers, cloud services and websites.
DDOS attacks can cost 20,000 to 40,000 US dollars per hour. There’s reputation and damage to customer relationships on top of direct costs.
What to do:
Make sure DDoS attack mitigation is part of your cybersecurity solution. Equip your IT teams with free DDoS reports on SecureList.

7. Attacking connected ‘things’
The Internet of Things (IoT) is a fast-growing ecosystem – forecasts predict we’ll use more than 75 billion IoT devices by 2025.
Connected devices like elevators, sensors and printers are now common in homes and workplaces, and they’re increasingly part of manufacturing and industry processes. Many industrial IoT devices run on outdated, vulnerable operating systems, becoming an easy entry point for hackers to bring down a whole business.
Just 19 percent of companies have active network and traffic monitoring for IoT devices.
What to do:
Look for solutions that protect IoT by transferring data from industrial equipment to cloud platforms, creating a secure connection between IoT and your corporate network. Read more about how to minimize the risk of attack through IoT devices.
8. The most common cyberthreat
Malware is common and fast becoming the most dangerous, costly type of attack for enterprises, which are feeling the effects of serious attacks like Emotet and related ransomware. It damages business operations by stealing, altering and deleting sensitive information or taking control of systems. In the European Union, 70 percent of internet users’ computers have had at least one malware attack.
What to do:
Blocking malware attacks is starting to require more advanced threat protection. Read about the benefits of using Endpoint Detection Response (EDR) for automated protection.
9. Trouble through doorways
Endpoints are the ‘doorways’ your employees use to access business data and systems, like laptops, mobile phones and servers. Cybercriminals love to attack them.
In 2019, 68 percent of organizations had one or more endpoint attack that compromised data. And with the new reality of employees working from home, organizations must further strengthen their endpoint security.
What to do:
To protect office-based, remote and hybrid workers, consider Endpoint Detection and Response (EDR) to monitor endpoints continually. Read more about how strengthening cybersecurity for remote working can reduce cyberattacks.
How to get ahead of advanced threats
Advanced cyberthreats are common and have a big impact on business reputation and bottom line. When business leaders take action on cybersecurity, they’re safeguarding their business and avoiding spending more time later to mop up damage from a cyberattack.
Kaspersky’s stage-by-stage cybersecurity framework keeps your enterprise safe from all common, pervasive and financially damaging threats.
Find out more and sign up for the latest enterprise cybersecurity report from Kaspersky produced in partnership with the commercial department of the Financial Times.





