Wilhelm Conrad Röntgen’s accidental discovery of the X-ray 125 years ago launched a new era of medical breakthroughs. Without the X-ray, we wouldn’t have CT scans and MRIs. Now, the internet of things (IoT,) alongside big data and cloud computing, bring another new age – one of ‘smart’ healthcare that drastically improves patient care and operational efficiency.
These technologies also bring new risks. IoT medical devices connect to each other, to the network and to public internet. Many weren’t designed with cybersecurity in mind from the beginning. What might this mean for protecting patient privacy?
Poor prognosis for patching and updates
Information security veteran and entrepreneur Aviram Jenik believes healthcare faces a perfect storm. He’s co-founder and CEO of US-based Beyond Security, a company that assesses and manages network vulnerability.
“IoT devices use common web browsing engineers and operating systems. If there’s a security hole one of these platforms, the device is vulnerable,” he says.
Unlike those common platforms, it’s harder – sometimes impossible – to patch devices for vulnerabilities. Medical devices tend to have a life cycle of 15 to 20 years, so it’s more likely they’re running on outdated or unsupported operating systems.
“Just because the operating system is at the end of life, it doesn’t mean medical manufacturers can swap it out,” says John Gomez, CEO of Sensato, a US company providing cybersecurity for medical devices. “It’s a quandary for everybody, financially as well as technically.”
The rise of the internet of medical things
The dilemma of weighing the risks vulnerabilities pose against the cost of patching or replacing devices will intensify as the market grows. Healthcare’s adoption of the internet of medical things (IoMT) is in its infancy, but moving fast.
Healthcare is the third fastest-growing sector for IoT globally, according to market analysis company IDC. Global accounting and audit giant Deloitte forecasts the medical device market will more than triple between 2017 and 2022, reaching a value of 52 billion US dollars.
A 2019 IBM study found data breaches are most costly in healthcare, averaging nearly 6.5 million US dollars. Healthcare is a constant target, as seen in incidents like Singapore’s health service data breach, affecting 1.5 million patients, or the ransomware attack that disabled IT systems at a French hospital.
As IoMT matures, and concerns about security grow, manufacturers need to rethink their approach to design. But what happens in the meantime?
Healthcare’s IT support sparse and jumbled
Looking at data from seven years of running projects with hospitals, Sensato found 60 percent of medical devices are at their end of life with no patches available. Just months before Microsoft support for Windows 7, 2008 and Mobile were to expire, security firm Forescout found 71 percent of Windows devices in healthcare used those outdated operating systems.
The devices, Sensato’s Gomez notes, are only part of the problem. There are few IT staff in most healthcare organizations. A hospital with 6,000 to 7,000 staff may have only one or two IT personnel.
“They’re managing complicated infrastructure with hundreds of servers and applications that communicate with other healthcare organizations,” Gomez says. “The problem exponentially grows when adding IoT or IoMT devices,” he adds. “IT staff may not even have visibility into them because their management falls to other departments, such as facilities or clinical care.”
Gomez continues, “You’re trying to secure an environment where you don’t even know everything because it’s not part of the IT department. It’s a daunting task to lock down the devices.”
Healthcare data is attractive to cybercriminals. It has a high dark market value. Healthcare organizations may also be more inclined to pay out in ransomware attacks to avoid disrupting patient care.
“Many healthcare organizations are still struggling to understand the risks. Growing device connectivity makes safeguarding data a bigger challenge. Connected medical devices not visible to IT are still visible to attackers,” says Oleg Gorobets, Kaspersky’s Senior Global Product Marketing Manager.
Fast-growing awareness, slow improvement
A few years ago, there was little conversation outside of the information security community about the risks of connected devices in healthcare. Todd Weber, Chief Technology Officer for security solutions integrator Optiv Security, notes there’s also the mindset among healthcare leaders that hospitals are safe places.
“Healthcare organizations have more of an open environment, which makes them vulnerable,” Weber says. “It’s a huge mindset to get over, to understand that hospitals are being purposefully attacked.”
But awareness of security problems with IoMT is growing. “For security, we like to say that awareness is 90 percent of the battle, and we have that,” Jenik of Beyond Security says. “Everybody involved wants IoMT to be secure, so there’s no conflict.”
Regulation may be helping
Regulatory agencies around the world – like the US Food and Drug Administration (FDA) and the China Food and Drug Administration (CFDA) – have started pushing for better security.
The FDA publishes security guidelines for manufacturers and issues advisories when vulnerabilities are discovered. This action ripples worldwide because eight of the world’s top ten medical device companies are US-based, and about half their sales go offshore.
While the FDA guidelines are non-binding, China took a more assertive stance, including mandatory security assessment and registration of networked devices, with fines for those who don’t comply.
The European Commission brought in sweeping changes in 2020: The Medical Device Regulation (MDR). As the regulation impacts all manufacturers selling in the European Union, it will have global effects.
Like many in security, Gomez of Sensato isn’t fond of regulation. But in healthcare, he thinks it could catalyze change. “Security in healthcare is behind, so you get a domino effect,” he says. “At some point, only regulation or something like a terrorist attack will be a wake-up call.”
Cybersecurity risk taken to heart
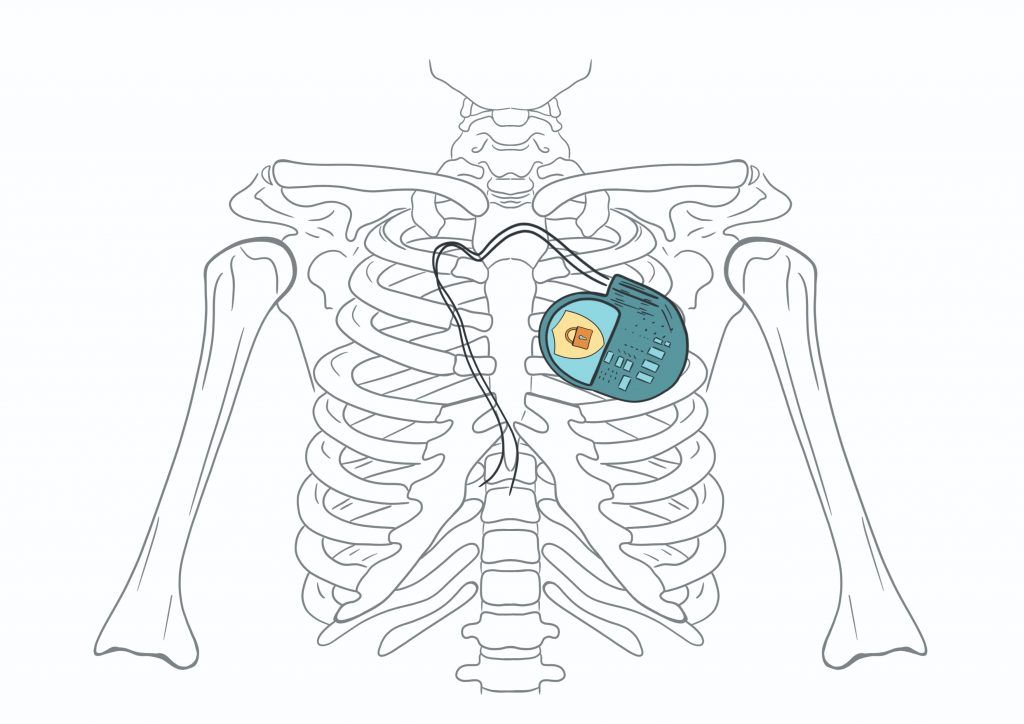
Awareness may be growing, but the pace of change in healthcare is slow. “It’s for good reason because the stakes are different. You’re impacting human lives,” Weber says.
Potentially vulnerable devices include implantable cardiac defibrillators (ICDs) and pacemakers. These use a wireless communication protocol so physicians can collect data and change therapy. In 2007, US Vice President Dick Cheney had his pacemaker’s wireless communication disabled to avoid attack. Still, in 2016, researchers found a “weak adversary” could reverse-engineer a proprietary protocol used in 10 products with inexpensive, off-the-shelf equipment.
Attacks on medical devices in the wild
So far, cybercriminals haven’t taken advantage of known vulnerabilities in cardiac devices, but security experts think risks will grow as many security holes open new opportunities for attack.
It’s just a matter of time before we see attacks on medical devices in the wild. Centralized networks of wearable and implanted medical devices will mean a new threat: A single point of entry to attack all patients using these devices.
Yury Namestnikov
Kaspersky's Head of Research Center, Russia
That open environment in hospitals Weber noted means other weaknesses. Medical equipment is not only easily accessible, it often connects to the same network as hospital computers. “Even with a segregated IoMT network, cyberattackers can use one device to get to others,” Kaspersky’s Gorobets adds.
Is 5G a symptom or treatment?
A lot of buzz surrounds the emerging technology 5G, even though it’s a few years away from its full potential. Telecommunications multinational Ericsson forecasts cellular IoT connections will quadruple to five billion by 2025.
Weber says for security, 5G is another way to attack. “IoT devices will be able to communicate with networks in different ways. With 5G, many become easier to exploit because access is outside corporate governance.”
But Gomez speculates 5G may improve security. 5G has higher encryption levels because of its greater bandwidth capacity. Some leaders of new hospital projects may decide 5G makes financial sense. They could reduce their wireless infrastructure and use 5G providers for direct cloud access from every device.
“5G also allows for software-defined networking, where you can put in place a powerful set of tools and lockdowns for the user and access controls based on traffic,” Gomez says.
The path to hospital-grade IoMT security
Beyond Security’s Jenik says after awareness, the next step is to work out how to secure devices. Consumers could also have a voice. “We should all push manufacturers and healthcare providers to meet security standards,” he says.
Kaspersky’s Gorobets says healthcare institutions should take immediate action. “Implement better IT practices, like segmenting networks and controlling access, cybersecurity awareness training and using specialized solutions to lock down what can be secured now.”
Healthcare providers can’t sit and wait for manufacturers to take action. But they can do something now to safeguard patients’ lives in the future.




