Ransomware Protection
Ransomware is a type of Trojan that modifies user data on a victim’s computer so that the victim can no longer use the data or fully run the computer.. Once the data has been “taken hostage” (blocked or encrypted), the user receives a ransom demand. The last tells the victim to send the malefactor money; on receipt of this, the cybercriminal promises to send a program to the victim to restore the data or restore the computer’s performance.
Ransomware is one of the most popular threats now facing the cyberworld due to the following reasons:
- This threat has clear monetization model
- It is easy to implement such malware
Ransomware can be complex or simple, depending on the planned victims:
- Common ransomware is widely spread via malicious spam campaigns, exploit kits, etc.
- Complex ransomware is used in targeted attacks
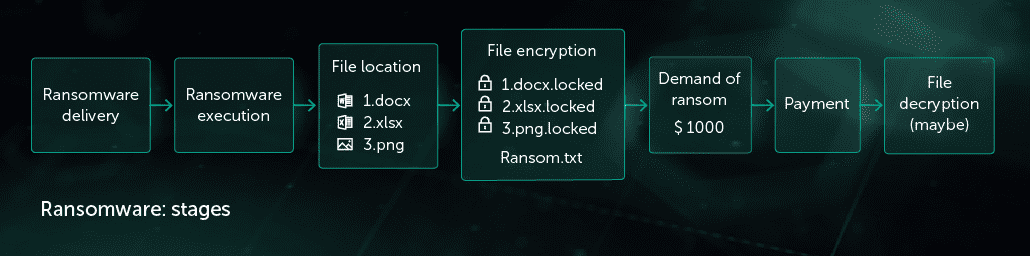
Ransomware attack has several stages:
- Delivery to a victim machine: malicious attachment in spam letter, vulnerability exploitation, penetration in case of targeted attack
- Execution: encrypting of important user files
- Ransom demand
- Data decryption (optional)
For efficient protection against ransomware, a security solution has to use a multi-layered protection model. Kaspersky Lab’s multi-layered, next generation protection lets products detect ransomware at both the delivery stage and execution stage of the attack. Let’s look deeper at these stages.
Delivery stage: Vulnerability Exploitation
Exploit Prevention (EP) is a special component to stop malware (including ransomware) penetration through software vulnerabilities. Among the most important applications protected by EP are browsers, office applications, pdf readers, and so on. On every suspicious action from the mentioned software, like child process start, the component applies additional security analysis of their behavior against malicious patterns. EP helps to block ransomware, including CryptXXX and many others.
In 2017, the world become aware of the use of network vulnerabilities as a method of ransomware distribution. WannaCry ransomware was proliferated by means of SMB vulnerability exploitation. Such an exploit can only be stopped on the network level. Kaspersky Lab’s products have a special component for network traffic analysis – intrusion detection system (IDS). This component analyses network packets in low level and applies heuristic patterns to them to detect malicious network activity. This component successfully detects EternalBlue/EternalRomance exploits. This helped to prevent the WannaCry infection.
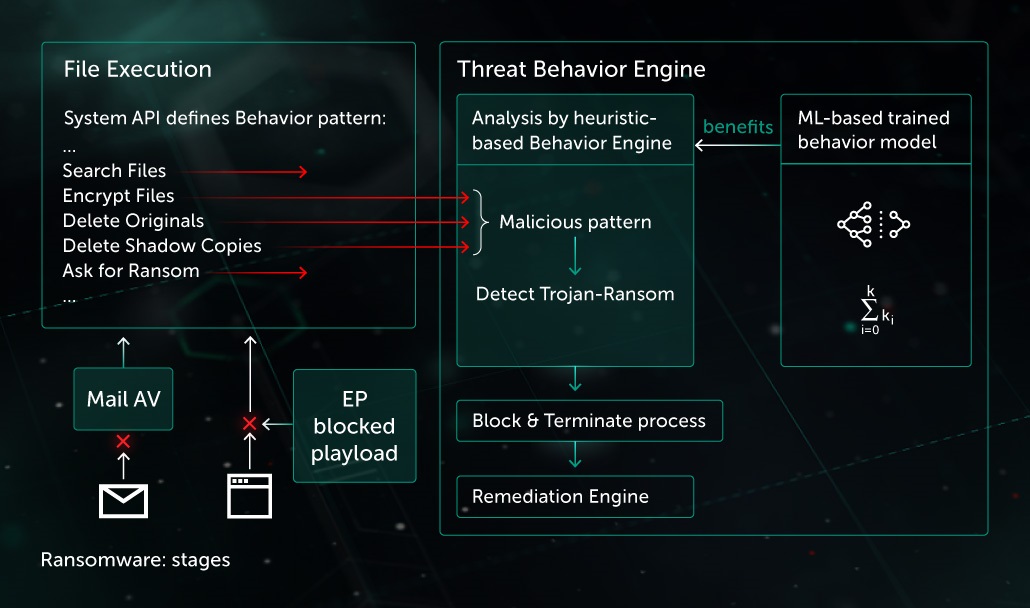
Execution stage
Threat actors try to bypass static detection by different methods. In this case Behavioral Detection becomes the last but the most powerful line of defense. Analysis of each process activity allows to reveal the malicious patterns. After that the product terminates the process and rollback the changes with Remediation Engine. Behavioral based detection is efficient even with previously unknown threats, including ransomware. A basic ransomware pattern consists of several steps:
1. Find important files on victim’s machine
2. Read content of each file
3. Encrypt content and save changes to disk
Matching such malicious behavior pattern, Behavior Engine blocks the process and rollback the changes with Remediation Engine. Among examples of successful ransomware detection by means of such pattern are Polyglot, WannaCry (encryption part of the malware), etc.
Detection of ransomware is not limited by the mentioned pattern, and many others could be efficient against these type of threats.
Efficiency of the approach was proven during the July 2017 attack by ransomware ExPetr. Threat actors used the low level part of Petya ransomware for Primary File Table (PFT, contains all file, directory and file metadata of NTFS file system) encryption. To execute it, they ran a high-level component, which rewrites the Primary Boot Record (PBR) of hard disk. Threat Behaviour Engine component marks such behaviour as malicious and stops the process. Even if other threat actors write similar ransomware, its functionality would fail regardless of the used types of obfuscation / anti-emulation techniques.
Ransomware in targeted attacks
In 2017, Kaspersky Lab registered several groups which were attacking organizations with one main goal: encrypt their data.

In many cases of targeted attacks, legitimate utilities for disk/file encryption were used. For example, DiskCryptor for encryption and PSExec for mass installation through corporate network. Static and basic behavior-based detections of legitimate utilities would be inefficient due to producing false positives in case of legitimate usage. This creates requirement of collecting and analyzing full context of utility usage. For the mentioned example, the pattern of installation of the legitimate utility for encryption through PSExec utility could be suspicious and corresponding protection enforcement by the product would prevent data from damaging without extra False Alarms for other users.