Exploit Prevention
Exploit Prevention (EP), part of Kaspersky Lab’s multi-layered, next generation protection, specifically targets malware that takes advantage of software vulnerabilities. It was designed to add an additional layer of protection for the most frequently targeted programs and technologies. EP provides an efficient and non-intrusive way for blocking and detection of both known and unknown exploits. EP is an integral part of Kaspersky Lab’s behavior-based detection capabilities.
Exploit “kill chains” consist of multiple stages. For example, web-based exploits often utilize drive-by download attacks. Infection starts when a victim visits a compromised website injected with malicious Javascript code. After multiple checks, the victim is finally redirected to a landing page with a Flash, Silverlight, Java or Web Browser exploit. For Microsoft Office or Adobe Reader vulnerabilities, on the other hand, the initial infection vector can be a phishing email or malicious attachment.
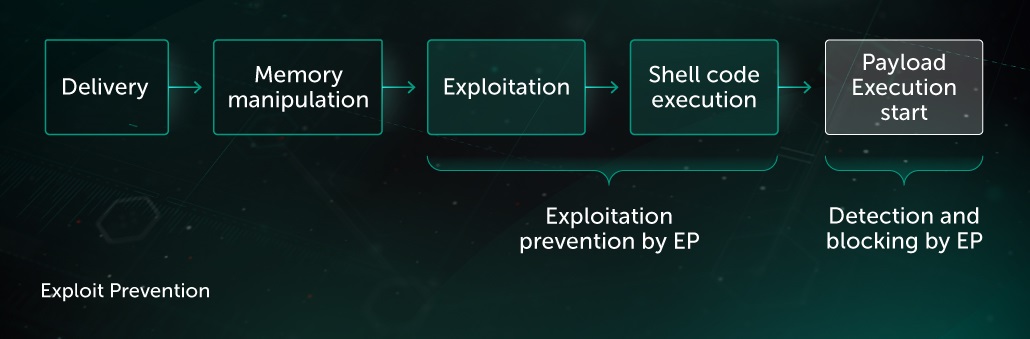
After performing the initial delivery stage, the attacker exploits one or more software vulnerabilities to get control of the process execution flow and moves on to the exploitation stage. Due to Operating System built-in security mitigations, directly running arbitrary code is often not possible, so the attacker must first bypass them. Successful exploitation allows for a shellcode execution, where the attacker’s arbitrary code starts to run, finally resulting in a payload execution. Payloads can be downloaded as a file, or even loaded and executed directly from system memory.
No matter how initial steps are performed – the ultimate goal of an attacker is to launch the payload and start the malicious activity. Launching another application or execution thread can be very suspicious, especially if the app in question is known to be lacking such functionality. Exploit Prevention technology monitors those actions, and pauses execution flow of an application, applying additional analysis to check whether the attempted action was legal or not. Program activity that took place before the suspicious code launch (memory changes in particular memory areas, as well as source of the attempted code launch) is used to identify if an action was made by an exploit. Not only that, EP also applies a number of security mitigation to address most of the attacking techniques used in exploits, including Dll Hijacking, Reflective Dll Injection, Heap Spray Allocation, Stack Pivot and so on. Those additional behavioral indicators, provided by an execution tracking mechanism of the Behavior Detection component, allow the technology to block payload execution with confidence.
