Mobile Device Protection
Mobile devices are popular targets for a cyberattack for several reasons:
- More people go mobile, storing more of their valuable data on devices. A hacked device is also a gate for accessing user’s data in the cloud.
- Mobile users actively engage in social networks and are easier to manipulate via social engineering.
- Misconfiguration of public Internet access points makes online devices vulnerable to Wi-Fi hotspot-based network attacks that steal the data users send to the Internet.
- Mobile banking-related data is also a profitable attack target.
- The spread of BYOD and practices of using the same device for business and personal means makes corporate mobile users a promising target for business espionage.
Kaspersky Lab products use the whole range of advanced technologies to fight mobile threats. Here are our main protection tools for mobile devices:
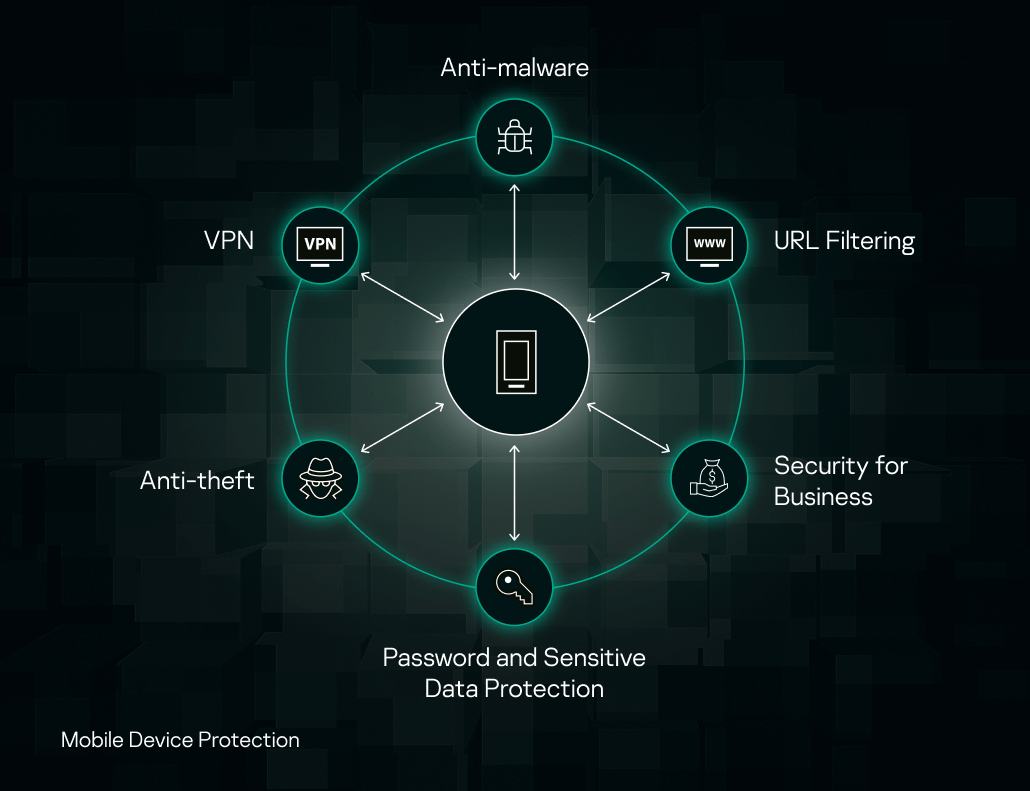
URL filtering: protection from accessing bad URLs
One kind of attack on a mobile device is convincing a user to go to a bad web link, initiate the download and install the malware. Kaspersky Internet Security for Android prevents users from accessing URLs with a bad reputation. Kaspersky QR Scanner checks the reputation of URLs in QR codes. The URL reputation is checked online, in the KSN cloud.
Anti-malware: protection from malware execution
In iOS, device protection from malware execution is based on the fact that the OS allows the installation of apps only from the App Store, which is strictly moderated by Apple. However, new malware that is able to sidestep this protection keeps emerging.
Making a classical antimalware app for iOS is not allowed by the OS design: apps cannot scan memory from another app or device. But the combination of Apple’s approach to App Store moderation with protection from accessing bad URLs is a good cybersecurity strategy for iOS.
On Android devices, users can install files from a variety of sources and app markets. Kaspersky Internet Security for Android scans an app when the app installer file appears in a file storage (even if the file gets to the device via Bluetooth connection or is copied via a USB cable, it gets scanned), and also after the app is installed. The file scan involves detection in the KSN cloud and by local antimalware bases.
It's worth to note that the cloud allows us to benefit from Cloud ML for Android system for mobile threats detection. Its predictive model takes the form of a Decision Tree Ensemble trained on millions of samples so it can detect malware with high accuracy. But this machine learning technique requires lots of resources to run which would be hard to provide on a simple mobile device. This is where we benefit from the KSN cloud approach: ML model is trained in-lab, while a mobile product just applies it for fast, real-time detection based on features of an Android application in question.
VPN: protection against data interception
The Kaspersky Secure Connection app protects against attacks by traffic interception from rogue Wi-Fi hotspots and proximate connection infrastructure by building an encrypted virtual private network (VPN) tunnel.
Kaspersky Lab’s VPN is adaptive. It can automatically enable VPN protection in sensitive contexts: connecting via a vulnerable hotspot (e.g. with weak encryption), accessing a URL or using an app related to sensitive data. Data seen as sensitive is that related to finance, banking, social media, shopping. In assessing hotspots, URLs and apps, Kaspersky Secure Connection relies on their locally available features as well as on cloud reputation.
Anti-theft: physical theft counteraction for Android
Physical theft is a way to access data on a device (photos, videos, personal and corporate documents, addresses) or even use a device as a portal for accessing corporate IT infrastructure. The anti-theft component in Kaspersky Lab mobile protection apps helps you to respond to device theft
- You can remotely wipe and reset the device to factory defaults.
- You get assistance in finding the device by locating it via the Kaspersky web portal and silently taking the thief’s photo.
Password and sensitive data protection
The Kaspersky Password Manager app allows users to enable strong unique passwords in web services and apps they use. This secures users from losing access due to attacks against weak passwords. The app automatically fills passwords in web pages, so you don’t need to fill logon forms by manual copying. Along with logon data, the app stores credit card data, important photos and other sensitive information.
Security for business (MTD)
The presence of many mobile devices in corporate environment creates mobile-specific cyberattack vectors on a company. To counter that, companies implement Mobile Threat Defense (MTD) solutions.
MTD protects company IT system from threats on mobile platforms: at the device, network and application level. It provides protection by preventing, detecting and remediating attacks. MTD is an additional layer of cyber protection over individual device protection tools like those we’ve discussed above.
Kaspersky Security for Mobile, as a part of Kaspersky Endpoint Security for Business, is a MTD solution for corporate mobile user protection. It provides:
- Threat management and protection: Real-time antimalware protection, web URL filtering and other individual device protection features
- Security policy assigning, compliance monitoring and violation response: Application management, root detect, remote wipe etc.
- Addition of security to existing third-party enterprise mobile management (EMM) solutions


