Kaspersky took part in the MITRE ATT&CK Evaluation Round 2, where our security products were tested against the attack techniques of APT29 threat group. In this article we will touch on the product configuration during this evaluation and the available capabilities of the product’s real-world deployment, as well as the testing requirements and restrictions.
MITRE test restrictions: what we had to turn off
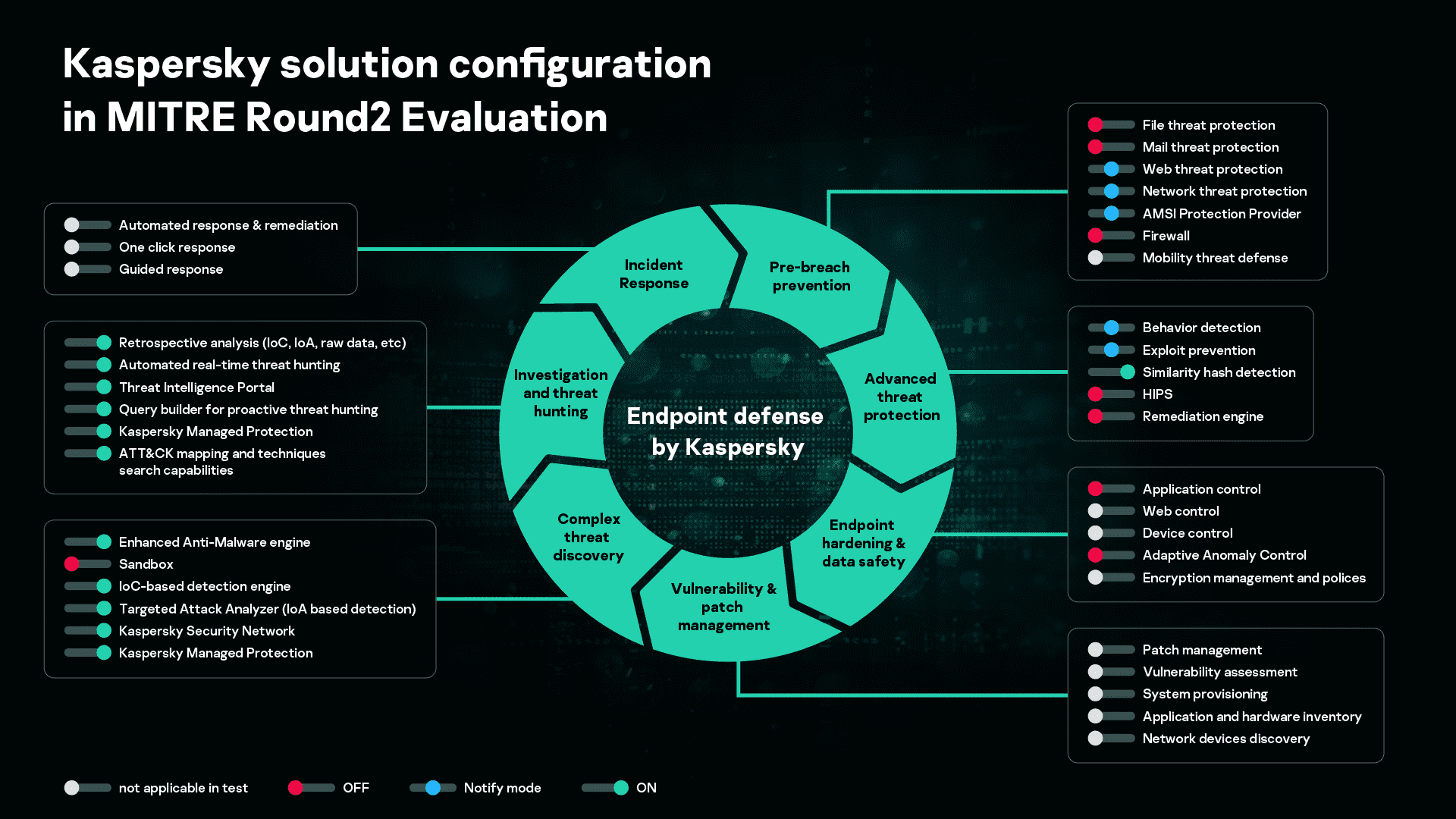
During the MITRE ATT&CK Evaluation Round 2, Kaspersky participated with the following:
- Kaspersky EDR (ver. 3.6) with Kaspersky Endpoint Security for Business agent (ver. 11.1)
- Kaspersky Managed Protection (MDR service)
To meet participation requirements, the following changes to the default configuration were implemented:
- To meet MITRE’s Azure deployment requirements, the on-premise sandbox and network sensors (web and mail) were not deployed.
- To satisfy the requirements of the evaluation that discovered threats should not be blocked by solution components, a number of technologies in the endpoint agent were set either to ‘OFF’ mode (File Threat Protection, Mail Threat Protection, HIPS, Adaptive Anomaly Control, Remediation Engine, Firewall) or to ‘Notify’ mode (Behavior Detection, Exploit Prevention, Web Threat Protection, Network Threat Protection, AMSI Protection Provider). These configurations resulted in limitations to the detection capabilities. In a real-world deployment, these components are turned on by default, enabling optimum detection and an automatic response to cyberthreats. This should be taken into consideration when analyzing Round 2 results.
- In MITRE’s configuration, two out of the five hosts participating in the test were not entered into the domain, so a special product patch was applied for these two hosts. In standard use, the corporate domain policy is configured to prevent non-domain hosts from gaining access to the corporate network’s resources. Customers requiring similar configurations are currently provided with the necessary patch, and it’s planned to include this in the next public release.
- A list of Windows registry branches was configured with Kaspersky EDR, so that changes here could be controlled and monitored.
Product description: Kaspersky EDR with Kaspersky Endpoint Security for Business
Kaspersky EDR is designed to defend endpoints against evasive threats and complex attacks, and to provide IT security/SOC teams with a powerful tool for threat discovery, in-depth incident investigation, proactive threat hunting and a centralized response. Together with Kaspersky Endpoint Security for Business, it represents a complete endpoint defense providing EPP and EDR capabilities through a single agent. This solution provides the following capabilities:
Endpoint threat protection technologies:
- Behavior detection, including ransomware and fileless threat protection
- Exploit prevention
- Adaptive Anomaly Control
- Endpoint hardening (application, web and device controls)
- Vulnerability assessment and patch management
- Similarity hash detection
- File threat protection
- Mail threat protection
- Web threat protection
- Network threat protection
- HIPS
- Firewall
- Remediation engine
Anti-targeted attack centralized components:
- Enhanced anti-malware engine
- Sandbox
- IDS
- URL reputation (URLs, IPs, domains)
- Indicator of Compromise (IoC)-based detection engine
- Targeted Attack Analyzer with Indicator of Attack (IoA) detection
- MITRE ATT&CK mapping and techniques search capabilities
- YARA rules
- Threat intelligence (delivered automatically via Kaspersky Security Network)
Deep investigation and threat hunting capabilities:
- Supports centralized IoC loading from threat data sources and automatic scheduled IoC scanning, streamlining analysts’ work. Retrospective database scans can be used to enrich the quality of previously flagged security events and incidents.
- Retrospective analysis in support of multi-stage attack investigation, even where compromised endpoints are inaccessible or when data has been encrypted by cybercriminals.
- Option to take arbitrary files from hosts for sandbox processing and scanning according to YARA rules, in addition to endpoint protection.
- Automated real-time threat hunting – events are correlated with unique Indicators of Attack (IoA) generated by Kaspersky threat hunters, and mapped to the MITRE ATT&CK knowledgebase, to provide clear event descriptions and examples as well as response recommendations.
- IT security specialists can create their own database of custom IoA based on endpoint event attributes.
- Access to the Kaspersky Threat Intelligence Portal to gain additional enhanced context about suspicious objects (such as reputation, related known global incidents, etc).
- A powerful, flexible query builder for proactive threat hunting, to help analysts build complex queries in searching for atypical behavior, suspicious events and threats specific to the infrastructure. The query builder also enables hunting against individual MITRE ATT&CK techniques.
Incident response and remediation:
- Automated response and remediation
- One-click response (for example, suspicious host isolation, file quarantine, prevention of executable files/documents/scripts from executing, file deletion, process kill, etc.)
- Guided response (lookup in Kaspersky Threat Intelligence Portal, Sandbox report, related alerts search, IoA creation from alert indicators, etc.)
MDR service description: Kaspersky Managed Protection
Kaspersky Managed Protection is a complete managed service, deploying a unique range of advanced techniques to detect and respond to targeted attacks. The service includes round-the-clock monitoring and continuous analysis of cyberthreat data by Kaspersky experts, ensuring the real-time detection of targeted attacks. Kaspersky Managed Protection provides detailed and immediate reports on suspicious activities, together with guidance on effective response and mitigation, and can be complemented with full-scale remote or on-site incident response services.
Conclusion
The restrictions on product configuration during the MITRE evaluation process have an impact on product effectiveness – without these restrictions, performance levels would certainly be even higher. But we understand that MITRE has every right to impose such restrictions, and we are proud to have participated in the evaluation, despite these limitations. MITRE is the first in the industry to assess EDR vendors, and we very much appreciate the work they do. Before every evaluation round, MITRE collects cyberthreat data with the participation of global cybersecurity vendors, helping prepare attack emulations which are very accurate simulations of real APT attacks, maximising the effectiveness of the evaluation process. As a result, organizations can now compare solutions tested under identical conditions, and gain an insight into the true capabilities of each EDR product.