Kaspersky Security Services experts have identified a sophisticated cyberattack campaign targeting containerized environments to deploy a miner for the Dero cryptocurrency. The attackers abuse exposed Docker APIs — parts of Docker, an open-source container development platform. In 2025, there are a significant number of Docker API default ports that are insecurely published, accounting for almost 500 occurrences worldwide on average each month. In the discovered campaign, cybercriminals inject two types of malwares into the compromised systems: one is the miner itself and the other is a propagation malware that can spread the campaign to other insecure container networks.
Kaspersky experts discovered this malicious campaign as part of a compromise assessment project. According to expert estimates, any organization that operates containerized infrastructure — while exposing Docker APIs without robust security controls — can be a potential target. These may include technology companies, software development firms, hosting providers, cloud service providers and more enterprises.
According to Shodan, in 2025, there are 485 published Docker API default ports[1] worldwide each month on average. This figure illustrates the campaign’s potential attack surface by tallying the “entry points” — or insecurely exposed ports that attackers might target. China accounted for the largest average number monthly — nearly 138 occurrences — followed by Germany (97), the U.S. (58), Brazil (16), and Singapore (13).
Once attackers identify an insecurely published Docker API, they either compromise existing containers or create new malicious ones based on a legitimate standard Ubuntu image. They then inject two malware types into the compromised containers: “nginx” and “cloud”. The latter is a Dero cryptocurrency miner, while “nginx” is a malicious software that maintains persistence, ensures execution of the miner and scans for other exposed environments. This malware allows attackers to operate without traditional Command-and-Control (C2) servers; instead, each infected container independently scans the internet and can spread the miner to new targets.
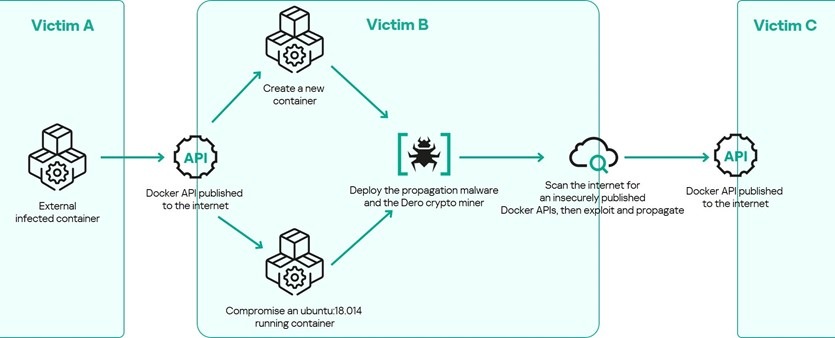
An infection chain scheme
“This demonstrates that the campaign has the potential for exponential growth of infections, with each compromised container acting as a new source of attack, if security measures are not immediately put in place in the potentially targeted networks,” explains Amged Wageh, an incident response and a compromise assessment expert at Kaspersky Security Services. “Сontainers are foundational to software development, deployment, and scalability. Their widespread use across cloud-native environments, DevOps, and microservices architectures makes them an attractive target for cyber attackers. This growing reliance demands organizations adopt a 360-degree approach to security — combining robust security solutions with proactive threat hunting and regular compromise assessments”.
The attackers embedded the names “nginx” and “cloud” directly in the binary — an inflexible executable file composed of instructions and data for the processor, not for humans. This is a classic masquerading tactic that lets the payload pose as a legitimate tool, trying to deceive both analysts and automated defenses.
The full technical analysis is available on Securelist. Kaspersky products detect these
malicious implants with the following verdicts: Trojan.Linux.Agent.gen and
RiskTool.Linux.Miner.gen.
To mitigate against container-related threats, Kaspersky recommends:
● Companies that use Docker APIs should immediately review the security of any potentially exposed infrastructure — specifically, refrain from publishing the Docker APIs unless there is an operational need and consider securing the published Docker APIs via TLS.
● Uncover active cyberattacks and previous unknown attacks that flew under the radar with Kaspersky Compromise Assessment.
● Containerization is the most popular application development method at the moment. But risks can emerge in each component of a container’s infrastructure and may heavily impact business processes. The protection of containerized environments is crucial and requires specialized security solutions.Kaspersky Container Security provides security for all stages of containerized application development. Besides the development process, the solution protects runtime, for example, it controls the launch of only trusted containers, the operation of the applications and services inside the containers and monitors the traffic.
● Adopt managed security services by Kaspersky such asCompromise Assessment,Managed Detection and Response (MDR) and / or Incident Response, covering the entire incident management cycle – from threat identification to continuous protection and remediation. They help to protect against evasive cyberattacks, investigate incidents and get additional expertise even if a company lacks cybersecurity workers.
The Security Services
Delivering
hundreds of information security projects every year for Fortune 500
organizations worldwide: incident response, managed detection, SOC consulting,
red teaming, penetration testing, application security, digital risks
protection.
[1] Analysis includes insecurely published Docker’s default API port 2375
