Kaspersky's Global Research and Analysis Team (GReAT) discovered that the recently exploited ToolShell vulnerabilities in Microsoft SharePoint originate from an incomplete fix for CVE-2020-1147, first reported in 2020.
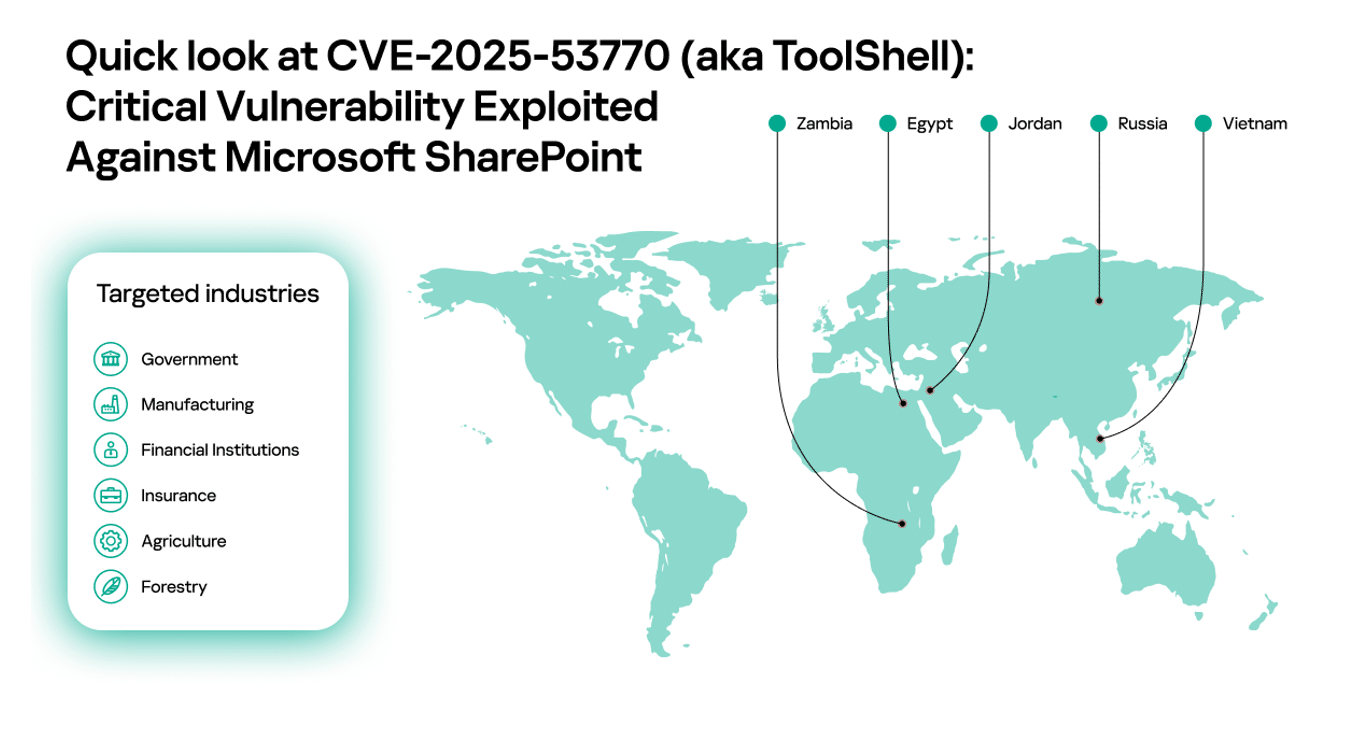
The SharePoint vulnerabilities have emerged as a major cybersecurity threat this year amid active exploitation. Kaspersky Security Network showed exploitation attempts worldwide, including in Egypt, Jordan, Russia, Vietnam and Zambia. The attacks target organizations across government, finance, manufacturing, forestry and agriculture sectors. Kaspersky solutions proactively detected and blocked ToolShell attacks before the vulnerabilities were publicly disclosed.
Kaspersky GReAT researchers analyzed the published ToolShell exploit and found it alarmingly similar to the 2020 CVE-2020-1147 exploit. This suggests that the CVE-2025-53770 patch is, in fact, an effective fix for the vulnerability that CVE-2020-1147 attempted to address five years ago.
The connection to CVE-2020-1147 became evident following the discovery of CVE-2025-49704 and CVE-2025-49706, patched on July 8. However, these fixes could be bypassed by adding a single forward slash to the exploit payload. Once Microsoft learned of active exploitation of these vulnerabilities, they responded with comprehensive patches that addressed potential bypass methods, designating the vulnerabilities as CVE-2025-53770 and CVE-2025-53771. The surge in attacks against SharePoint servers worldwide occurred during the window between initial exploitation and full patch deployment.
Despite patches now being available for the ToolShell vulnerabilities, Kaspersky expects attackers will continue exploiting this chain for years to come.
"Many high-profile vulnerabilities remain actively exploited years after discovery — ProxyLogon, PrintNightmare and EternalBlue still compromise unpatched systems today. We expect ToolShell to follow the same pattern: its ease of exploitation means the public exploit will soon appear in popular penetration testing tools, ensuring prolonged use by attackers," said Boris Larin, principal security researcher at Kaspersky GReAT.
Read the full report on Securelist.com
To stay safe, Kaspersky recommends:
- Organizations using Microsoft SharePoint must apply the latest security patches immediately. This applies to all high-risk vulnerabilities, as even brief exposure can lead to compromise.
- Deploy cybersecurity solutions that protect against zero-day exploits when patches aren't yet available. Kaspersky Next, with its Behavior Detection component, proactively blocks exploitation of such vulnerabilities.
About the Global Research & Analysis Team
Established in 2008, Global Research & Analysis Team (GReAT) operates at the very heart of Kaspersky, uncovering APTs, cyber-espionage campaigns, major malware, ransomware and underground cyber-criminal trends across the world. Today GReAT consists of 35+ experts working globally – in Europe, Russia, Latin America, Asia and the Middle East. Talented security professionals provide company leadership in anti-malware research and innovation, bringing unrivaled expertise, passion and curiosity to the discovery and analysis of cyberthreats.
