The CVE-2010-2568 vulnerability was discovered back in 2010 at the same time as the notorious Stuxnet worm.
The 0-day Vulnerability exploited by Stuxnet still threatens users, Kaspersky Lab study finds
Kaspersky Lab presented its "Windows usage and vulnerabilities" research conducted in 2014. According to it the CVE-2010-2568 vulnerability was discovered back in 2010 at the same time as the notorious Stuxnet worm. Even today malware programme’s exploiting this vulnerability remains widespread and poses a threat to users: 19,000,000 users encountered it in an eight-month timeframe from November 2013 to June 2014.
CVE-2010-2568 is a shortcut handling error in Windows, allowing attackers to load an arbitrary DLL without the user's knowledge. This vulnerability affects Windows XP, Vista and Windows 7 as well as Windows Server 2003 and 2008. It was most famously exploited by Stuxnet – the worm detected in June 2010 and notorious in that it apparently led to the physical destruction of uranium enrichment equipment at nuclear facilities located in Iran.
As early as in the autumn of 2010, security updates were released which patched this vulnerability. However, in spite of this, Kaspersky Lab's detection systems still register millions of instances in which malware exploiting this vulnerability is detected. When viewed country by country malware instances targeting this vulnerability were most often detected in November 2013 - June 2014 on the computers of users residing in Vietnam (42.45%), India (11.7%), Indonesia (9.43%), Brazil (5.52%) and Algeria (3.74%).
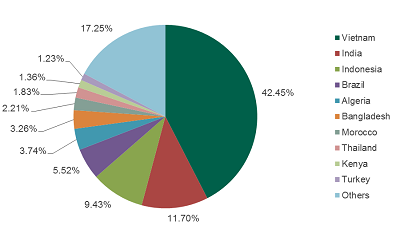
The geographical distribution of all registered CVE-2010-2568 detections
Remarkably, the same research indicates that Vietnam, India and Algeria are both on the list of countries with most CVE-2010-2568 detections, and among the leaders in terms of the numbers of users still using Windows XP. That very operating system occupies first place for CVE-2010-2568 detections: 64.19% of detections were reported from computers running under Windows XP. Windows 7, currently the most widely used in the world, is only in second with 27.99% detections. Next come Windows Server 2008 and 2003 with 3.99% and 1.58% detections respectively.
Kaspersky Lab's experts would particularly like to emphasise that in this specific case, the large number of detections does not directly translate into a large number of attacks. Due to the peculiar ways this vulnerability is exploited, it is impossible to accurately differentiate between cases when Kaspersky Lab's product protected from real attacks involving malware exploiting CVE-2010-2568, and the cases when they only detected vulnerable shortcuts automatically generated by a specific worm.
The large number of CVE-2010-2568 detections is a testimony to the fact that globally there are still many computers that are vulnerable to attacks involving malware exploiting this vulnerability. Kaspersky Lab's experts presume that most of these detections stem from poorly maintained servers without regular updates or a security solution; such servers may be inhabited by a worm that uses malware exploiting this vulnerability. Following their designed logic, such malware programmes routinely create malicious shortcuts in a general access folder; each time a user protected by a Kaspersky Lab's solution and having access to that folder clicks on such a shortcut, the detection takes place.
"This type of situation obviously creates an on-going risk of malware infection in organisations where these vulnerable servers still operate," says Vyacheslav Zakorzhevsky, Head of the Vulnerability Research Team at Kaspersky Lab. "Therefore we urge corporate IT managers to devote more attention to ensuring that software is kept up to date on corporate computers, and to employ adequate cyberthreat protection tools."
To minimise the risk of encountering attacks involving vulnerabilities, Kaspersky Lab's experts recommend that users update their software regularly, delete unused software and use a reliable security solution equipped with technologies to counteract exploit attacks.
For example, Automatic Exploit Prevention from Kaspersky Lab is able to fight attempts to exploit currently unknown software vulnerabilities thanks to heuristic detection, and its effectiveness is confirmed by independent researchers. This technology is incorporated in Kaspersky Lab's home and corporate products such as Kaspersky Internet Security Multi-Device, Kaspersky Small Office Security and Kaspersky Endpoint Security for Business.
Read more at securelist.com.
