Between June and August 2025, Kaspersky’s Global Research and Analysis Team (GReAT) identified a new wave of attacks carried out by RevengeHotels, also known as TA558, a threat group which has been active since 2015. In this campaign, the group targeted the tourism and hospitality sector in Brazil and several Spanish-speaking countries, stealing banking card data from hotel guests. The actor has significantly enhanced its capabilities, adopting new tactics and using AI to expand operations into additional regions.
Although Brazilian hotels are the primary targets of the new campaign, the activity has also extended to Spanish-speaking countries, including Argentina, Bolivia, Chile, Costa Rica, Mexico, and Spain. Earlier another campaign from the same actor was discovered targeting users in Russia, Belarus, Turkey, Malaysia, Italy and Egypt.
The threat actor uses phishing emails disguised as requests for reservation, urging recipients to review the attached documents. The website link in the documents lure the user to install a Remote Access Trojan (RAT) allowing to issue commands which control compromised systems and steal sensitive data. The messages are typically sent to email addresses associated with hotel reservations. In recent cases, however, the theme has shifted to fake job applications, where attackers send CVs in an attempt to exploit potential vacancies at targeted hotels. For payload delivery, the attackers leverage legitimate hosting services, often registering Portuguese-themed domain names.
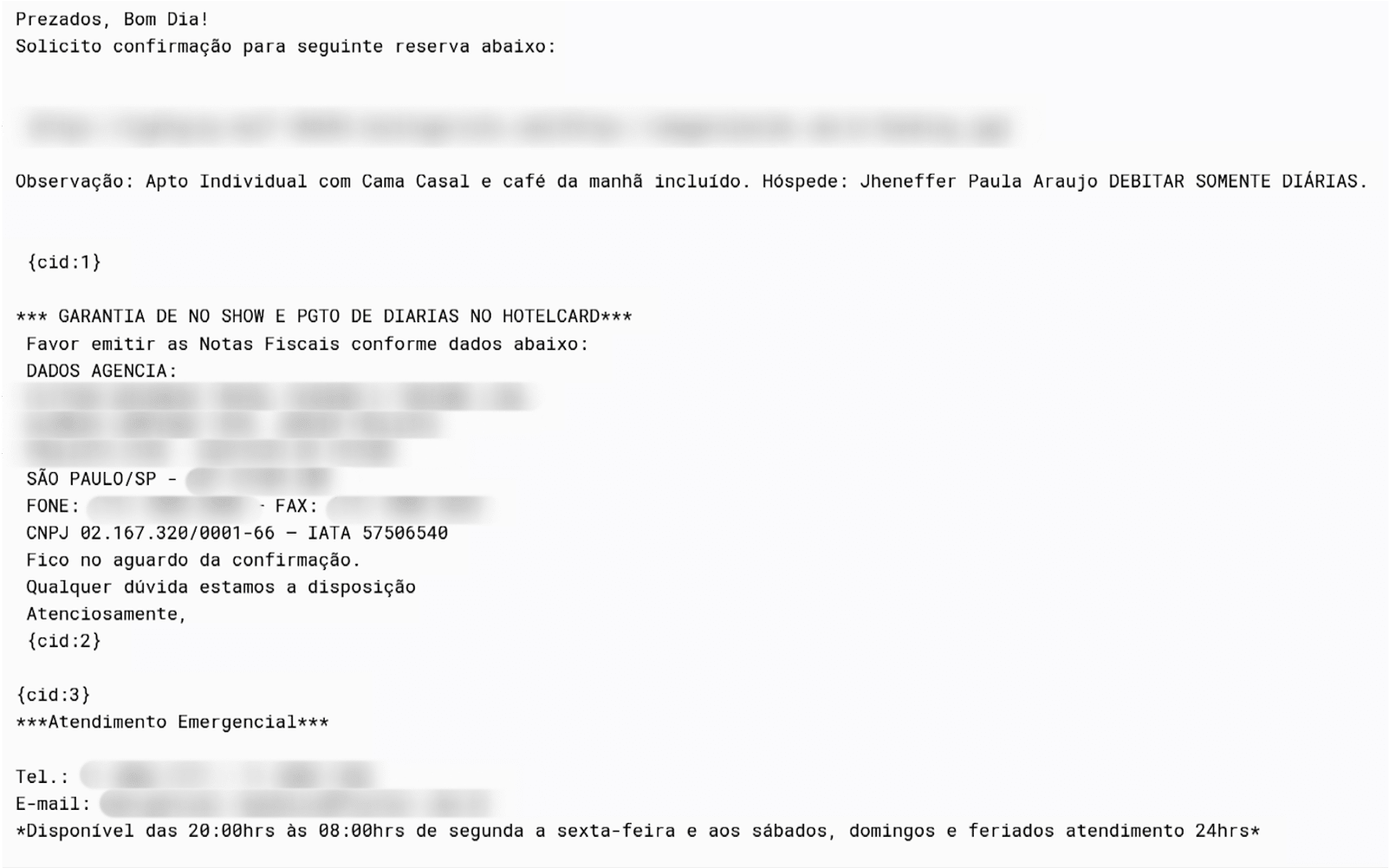 Example of a phishing email about reservation
confirmation
Example of a phishing email about reservation
confirmation
PowerShell downloaders, a tactic consistent with the group’s attack patterns. VenomRAT is distributed on dark web resources, with a lifetime license costing up to $650. It extends the functionality of QuasarRAT, offering features such as HVNC hidden desktop, file and credential theft, reverse proxy, and UAC exploit. Analysis shows that many of the newly created initial infectors by RevengeHotels include code likely produced using AI.
“Although the actor’s style is still recognizable, this campaign shows some new features: a large part of the initial infector and downloader code appears to be generated using Large Language Model (LLM) agents. This highlights a growing trend of threat actors leveraging AI to expand and evolve their capabilities, which has also been observed in other cybercriminal groups,” comments Lisandro Ubiedo, senior security expert at Kaspersky’s Global Research and Analysis Team.
Kaspersky products detect these threats as HEUR:Trojan-Downloader.Script.Agent.gen, HEUR:Trojan.Win32.Generic, HEUR:Trojan.MSIL.Agent.gen, Trojan-Downloader.PowerShell.Agent.ady, Trojan.PowerShell.Agent.aqx.
More information is available in a report on Securelist.com
To stay safe, Kaspersky recommends:
- Even if an email seems friendly, treat links and attachments with care. To protect your company use solutions from the Kaspersky Next product line that provide real-time protection, threat visibility, investigation and response capabilities of EDR and XDR for organizations of any size and industry.
- Cybercriminals often distribute fake email messages mimicking email notifications from an online store or a bank, luring a user to click on a malicious link and distribute malware. If attackers are specifically targeting your organization, the email text may be more customized, mimicking services or scenarios familiar to your company. With that in mind, fine-tune your antispam settings and never open attachments sent by an unknown sender.
- Try not to open unexpected files sent by you massively. They may be ransomware or even spyware, even attachments from official-looking emails.
About the Global Research & Analysis Team
Established in 2008, Global Research & Analysis Team (GReAT) operates at the very heart of Kaspersky, uncovering APTs, cyber-espionage campaigns, major malware, ransomware and underground cyber-criminal trends across the world. Today GReAT consists of 35+ experts working globally – in Europe, Russia, Latin America, Asia and the Middle East. Talented security professionals provide company leadership in anti-malware research and innovation, bringing unrivaled expertise, passion and curiosity to the discovery and analysis of cyberthreats.
