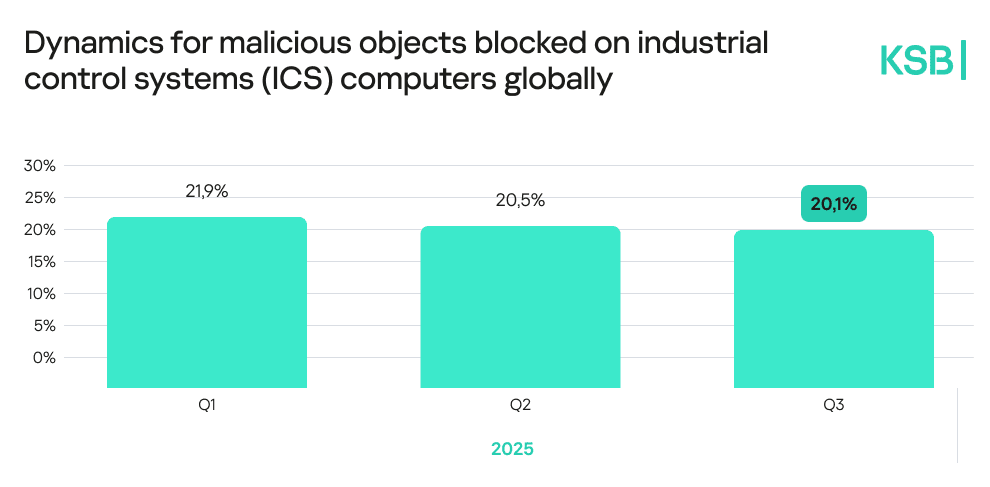
2025 has been a year defined by sustained pressure on industrial environments mirrored by increasingly complex global threat dynamics. According to the new Kaspersky Security Bulletin report, the share of ICS computers attacked with malware remained high, hovering around 21.9% in Q1 before declining to 20% by Q3.
This demonstrates incremental defensive gains in terms of cybersecurity on behalf of organizations amid continuously evolving attacker tactics. There are regional disparities, with Africa, South-East Asia, East Asia, the Middle East, and South Asia recording the highest shares of attacked ICS devices.
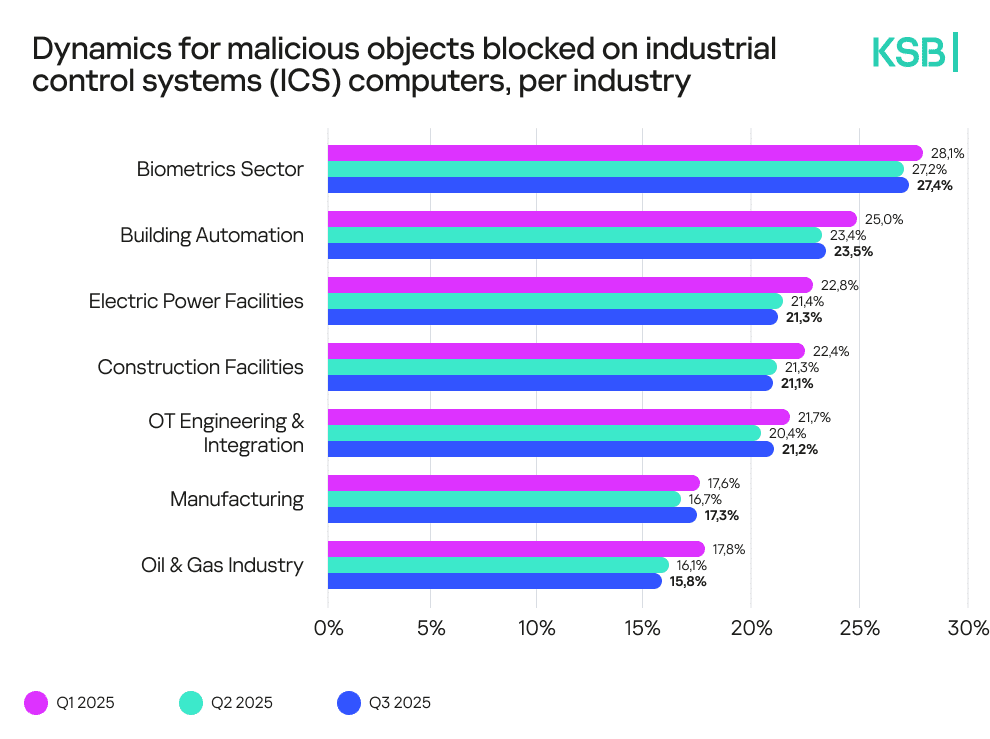
Threats by industries
Industrial sectors experienced uneven exposure to attacks, with biometrics topping the list at 27.4% of ICS computers with blocked malicious objects, followed by building automation (23.5%), electric power (21.3%), construction (21.1%), OT engineering and integration (21.2%), manufacturing (17.3%), and oil & gas (15.8%). These figures show that all critical sectors remain prime targets for threat actors.
Key trends in cyberattacks on industrial organizations
Adversaries further intensified their use of supply-chain and trusted-relationship attacks – exploiting local vendors, contractors, and mission-critical service providers such as telecommunications operators – to bypass traditional defense perimeters. AI-powered attacks expanded sharply, from using AI as a disguise for malware, to employing autonomous agent-driven intrusion operations. Additional growth was observed in attacks on Internet-exposed OT equipment, especially remote sites relying on OT firewalls not designed to withstand modern Internet-borne threats.
Predictions for 2026
2026 will likely bring an escalation of incidents disrupting global logistics and high-tech supply chains, along with more attacks on non-traditional targets such as smart transportation systems, vessels, trains, public transit, smart buildings, and satellite communications. Threat actors – including APTs, regional groups, hacktivists, and ransomware gangs – are expected to increasingly shift activity toward Asia, the Middle East, and Latin America, while AI-agent-based operations and autonomous malicious orchestration frameworks lower the barrier for mass-scale industrial campaigns.
“Industrial organizations are confronting an environment where attacks are faster, smarter, and more asymmetric than ever. This year alone, we investigated campaigns like Salmon Slalom, which targeted manufacturing, telecom, and logistics firms via advanced phishing and DLL sideloading, and the Librarian Ghouls espionage operation which compromised engineering schools and industrial design environments. These attacks show that both multinational supply chains and local technical ecosystems are at risk, and every industrial enterprise must assume it is already a target and act accordingly,” comments Evgeny Goncharov, Head of Kaspersky ICS CERT.
Read more on the Kaspersky Security Bulletin page.
To keep OT computers protected from various threats, Kaspersky ICS CERT recommends:
- Conducting regular security assessments of OT systems to identify and eliminate possible cyber security issues.
- Establishing continuous vulnerability assessment and triage as a foundation for effective vulnerability management processes. Dedicated solutions like Kaspersky Industrial CyberSecurity may become an efficient assistant and a source of unique actionable information, not fully available in the public domain.
- Performing timely updates for the key components of the enterprise’s OT network; applying security fixes and patches or implementing compensating measures as soon as it is technically possible is crucial for preventing a major incident that might cost millions due to the interruption of the production process.
- Using EDR solutions such as Kaspersky Next EDR Expert for timely detection of sophisticated threats, investigation, and effective remediation of incidents.
- Improving the response to new and advanced malicious techniques by building and strengthening teams’ skills in incident prevention, detection, and response. Dedicated OT security training for IT security staff and OT personnel is one of the key measures helping to achieve this.
