Kaspersky Global Research and Analysis Team (GReAT) has discovered a new botnet created by a resurfaced threat actor in July 2025. To lure victims, the attacker uses an MSI installer disguised as a fake setup for popular games, particularly shooters such as ‘Valorant’, ‘CS2’, or ‘R6x’, as well as other software. The botnet is currently expanding and poses an active threat to Windows users. It has already been detected by Kaspersky in Mexico, Chile, Russia, and Kazakhstan.
The Tsundere botnet employs an increasingly popular approach by using Web3 smart contracts to store its command-and-control (C2) addresses, significantly improving the robustness of its infrastructure. Its C2 panel supports two distribution formats: an MSI installer and a PowerShell script with implants generated automatically. These implants will install a bot capable of persistently executing the JavaScript code that receives dynamically – through an encrypted WebSocket channel – from the C2, which could lead to malicious execution of code sent by the threat actor.
To manage infections and update C2 locations, Tsundere botnet uses fixed references on the Ethereum blockchain, such as a designated wallet and contract. Changing the C2 server requires only a single transaction that updates the contract’s state variable with a new address. The botnet’s ecosystem also includes an integrated marketplace and control panel accessible through the same interface.
The analysis indicates with high confidence that the threat actor behind the Tsundere botnet is likely Russian-speaking, as shown by the use of Russian language in the code, which aligns with previous attacks linked to the same actor. The research also suggests a connection between the Tsundere botnet and the 123 Stealer created by ‘koneko’, which is offered on an underground forum for $120 per month.
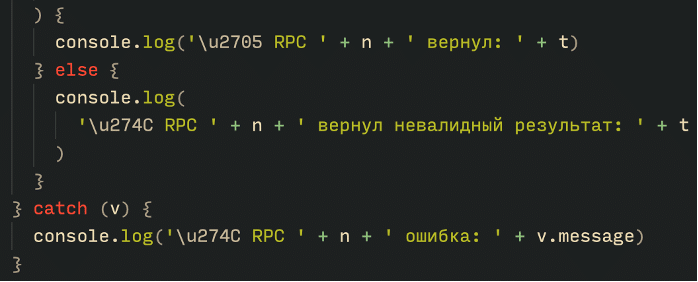
Russian language being used throughout the Tsundere botnet code
“Tsundere demonstrates how quickly cybercriminals adapt: it represents a renewed effort by a presumably identified threat actor to revamp their toolset. By shifting to Web3 mechanisms, its infrastructure becomes far more flexible and resilient. We’re already seeing active distribution through fake game installers and links to previously observed malicious activity, so further development of this botnet is highly likely,” – says Lisandro Ubiedo, senior security expert at Kaspersky’s Global Research and Analysis Team. For more details and indicators of compromise, see the article on Securelist.com. To stay safe, Kaspersky recommends:
- Exclusively utilize licensed software and official gaming platforms from verified publishers. This practice is essential for protecting your device from unauthorized access by malicious actors.
- Install a trusted security solution and follow its recommendations. Secure solutions will solve the majority of problems automatically and send alerts.
- Refrain from downloading executable files from unknown or untrusted sources.
- Beware of phishing emails urging you to install applications from unknown sites.
- Stick to best practice including regular software updates, enforcing strong passwords and two-factor authentication, as well as continuous monitoring for signs of compromise.
About the Global Research & Analysis Team
Established in 2008, Global Research & Analysis Team (GReAT) operates at the very heart of Kaspersky, uncovering APTs, cyber-espionage campaigns, major malware, ransomware and underground cyber-criminal trends across the world. Today GReAT consists of 35+ experts working globally – in Europe, Russia, Latin America, Asia and the Middle East. Talented security professionals provide company leadership in anti-malware research and innovation, bringing unrivaled expertise, passion and curiosity to the discovery and analysis of cyberthreats.
