Kaspersky has discovered a new sophisticated multi-stage attack campaign targeting cryptowallets in Europe, USA and Latin America. The attack involves the DoubleFinger loader, a complex crimeware that deploys the GreetingGhoul cryptocurrency stealer and the Remcos Remote Access Trojan (RAT). Kaspersky’s analysis highlights the advanced techniques and high level of skill employed by cybercriminals in this evolving threat landscape.
As Kaspersky’s investigation shows, the multi-stage DoubleFinger loader initiates its attack when the victim unwittingly opens a malicious PIF attachment in an email message. This action triggers the execution of the loader’s first stage, a modified Windows DLL binary, and then a malicious shellcode is executed. Next, the shellcode downloads a PNG image that includes a payload that is supposed to be launched later within the attack.
A .png file with embedded shellcode
In all, it takes DoubleFinger five stages to create a scheduled task that executes the GreetingGhoul stealer every day at a specific time. It then downloads another PNG file, decrypts it and then executes it. GreetingGhoul is a stealer designed to steal cryptocurrency-related credentials that consists of two components: the first one uses MS WebView2 to create overlays on cryptocurrency wallet interfaces, and the second is designed to detect cryptocurrency wallet apps and steals the sensitive information, such as keys, recovery phrases, and so on.
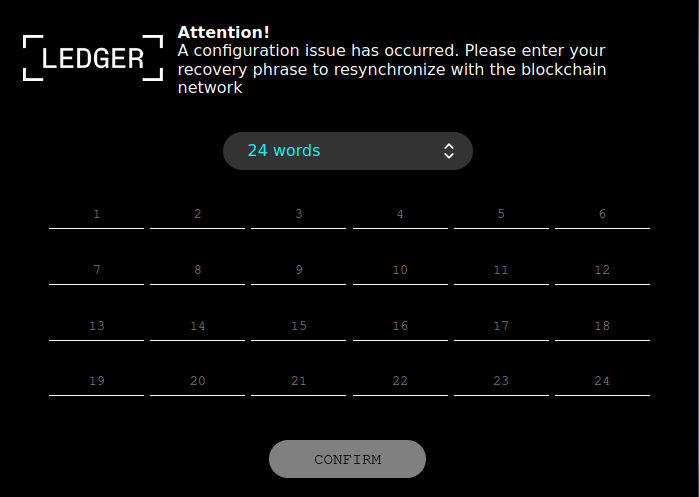
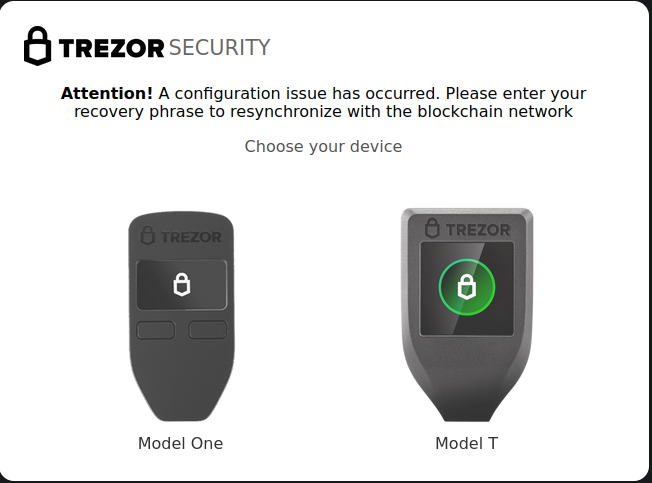
Examples of fake windows
Besides GreetingGhoul stealer, Kaspersky also found DoubleFinger samples that downloaded the Remcos RAT. Remcos is a well-known commercial RAT often used by cybercriminals in targeted attacks against businesses and organizations. The multi-staged, shellcode-style loader with steganography capabilities, the use of Windows COM interfaces for stealthy execution, and the implementation of process doppelgänging for injection into remote processes all point to a well-crafted and complex crimeware.
“As the value and popularity of cryptocurrencies continue to rise, so does the interest of cybercriminals. The group behind the DoubleFinger loader and GreetingGhoul malware stands out as a sophisticated actor with high skills in crimeware development, akin to advanced persistent threats. Protecting cryptowallets is a shared responsibility between the wallet providers, individuals, and the broader cryptocurrency community. And, by staying vigilant, implementing strong security measures, and staying informed about the latest threats, we can mitigate the risks and ensure the safety of our valuable digital assets,” says Sergey Lozhkin, a lead security researcher at Kaspersky’s GReAT.
Learn more about the DoubleFinger campaign on Securelist.
To keep crypto assets safe, Kaspersky experts also recommend:
· Purchase from official sources: Only buy hardware wallets from official and trusted sources, such as the manufacturer's website or authorized resellers. With hardware wallets, you should never fill your recovery seed on the computer. A hardware wallets vendor will never you ask for that.
· Check for signs of tampering: Before using a new hardware wallet, inspect it for any signs of tampering, such as scratches, glue, or mismatched components.
· Verify the firmware: Always verify that the firmware on the hardware wallet is legitimate and up-to-date. This can be done by checking the manufacturer’s website for the latest version.
· Secure your seed phrase: When setting up your hardware wallet, make sure to write down and securely store your seed phrase. A reliable security solution, such as Kaspersky Premium, will protect your crypto details stored on your mobile or PC.
· Use a strong password: If your hardware wallet allows for a password, use a strong and unique one. Avoid using easily guessable passwords or reusing passwords from other accounts.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection, specialized security products and services, as well as Cyber Immune solutions to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help over 220,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
