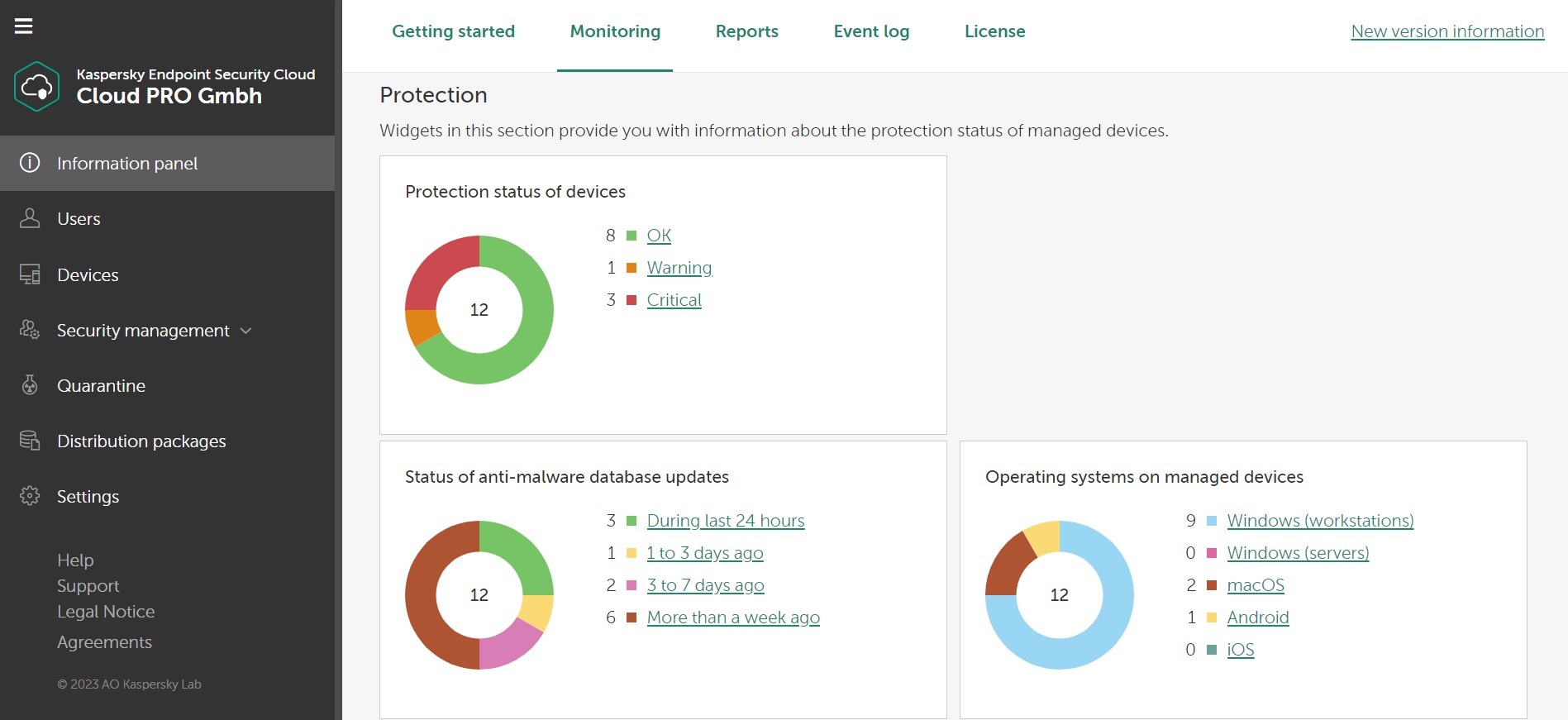
Kaspersky Endpoint Security Cloud is a comprehensive solution that protects you on all your devices. Working on all main operating systems – including Windows, iOS, macOS and Android – it comes with a range of advanced security tools and technologies, including ones that adapt in real-time to protect you 24/7.
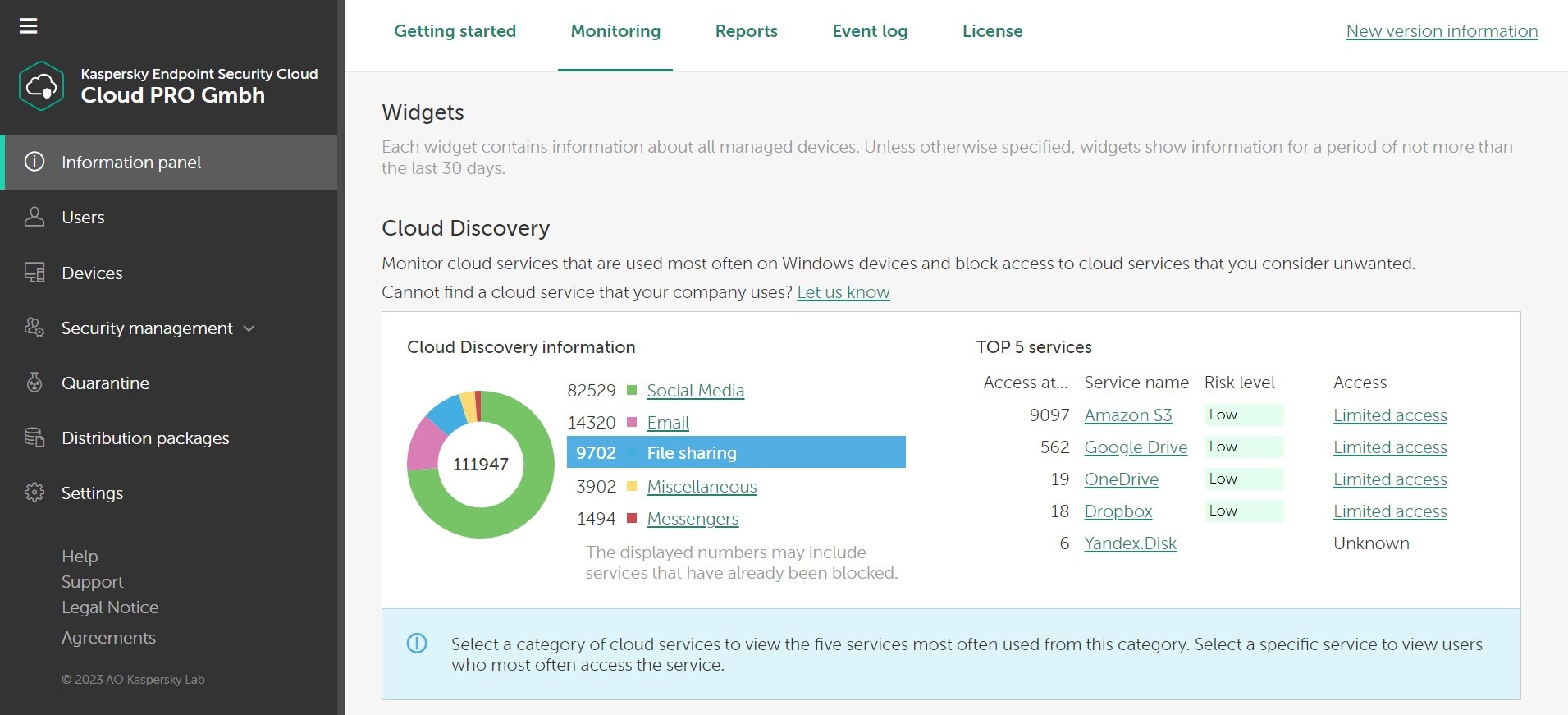
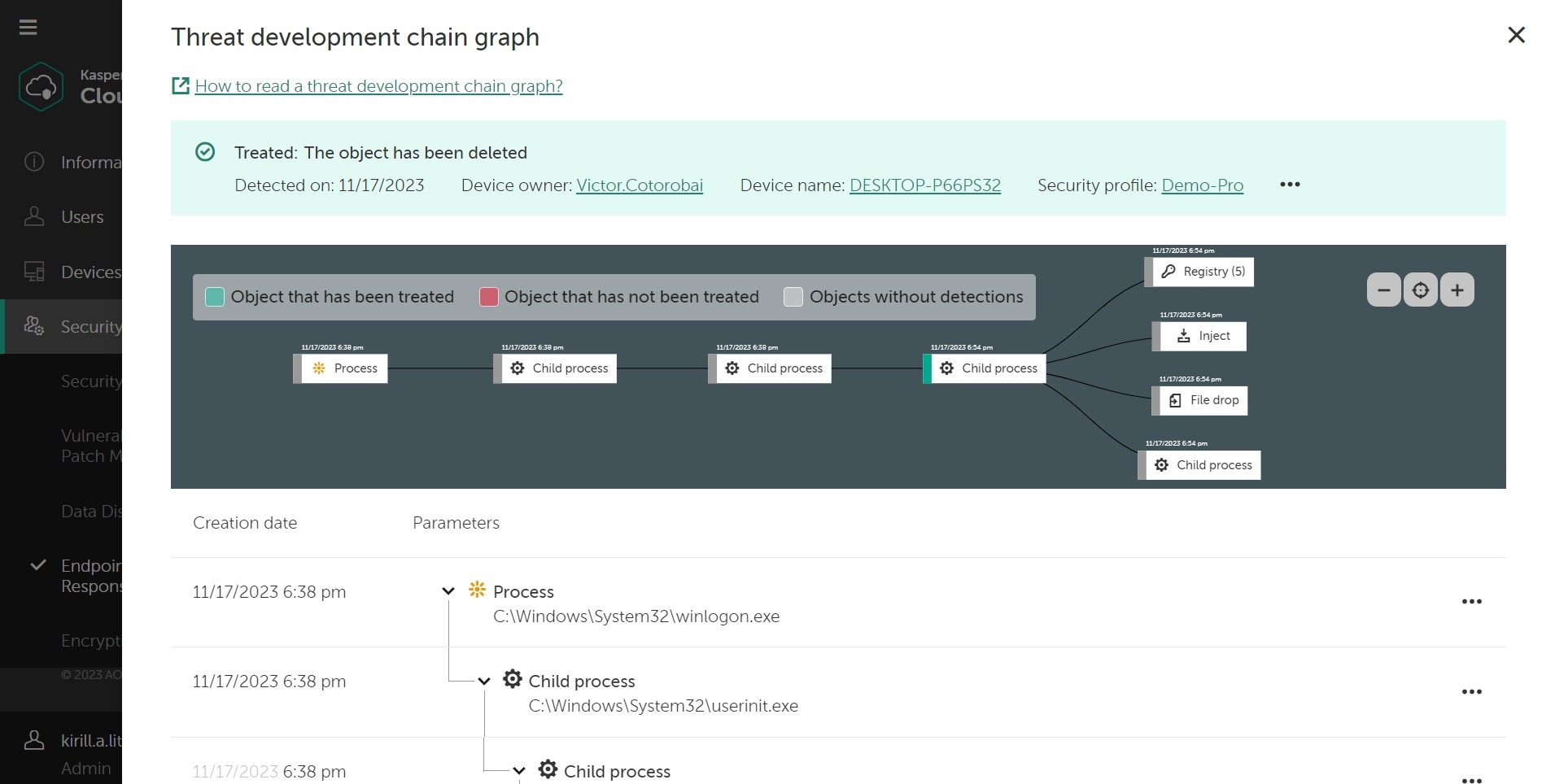
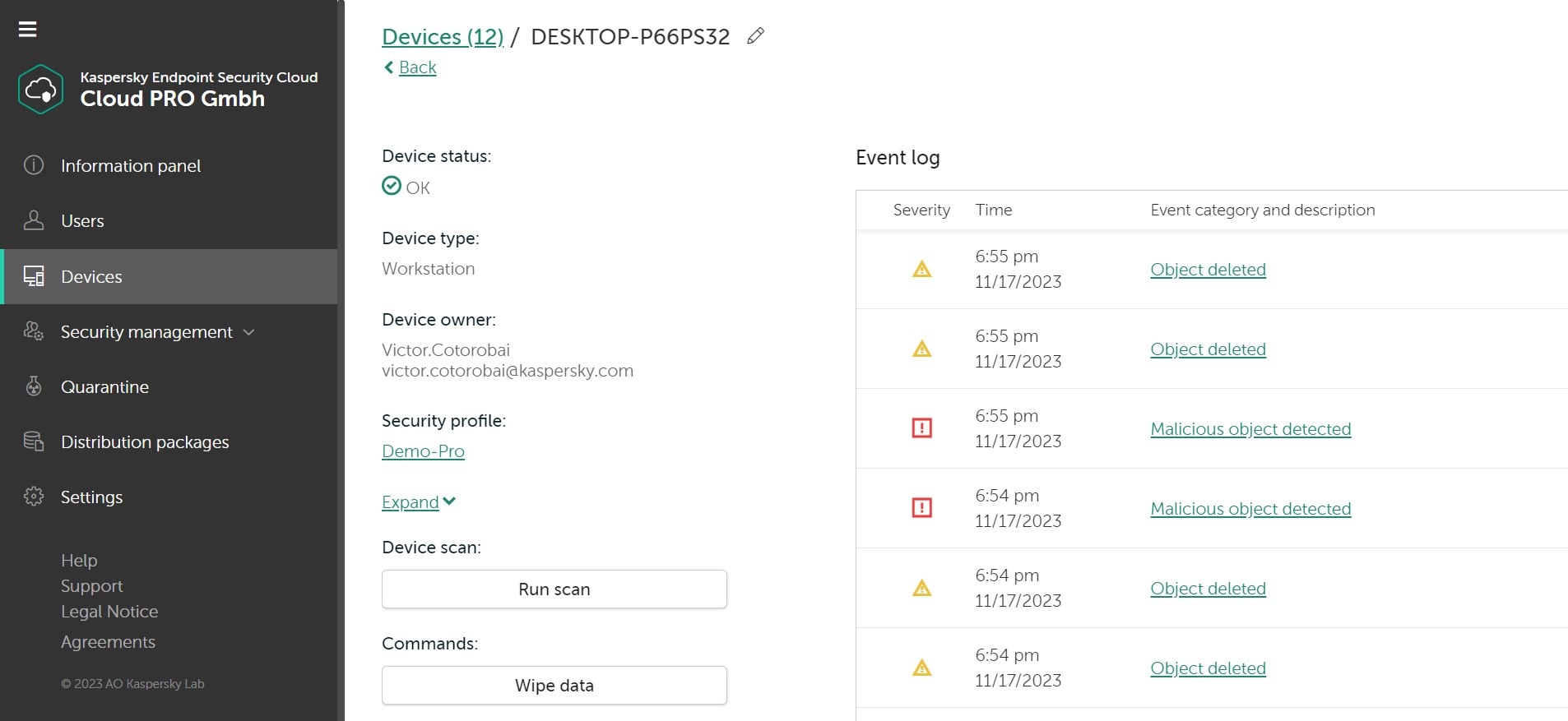
Furthermore, Kaspersky Endpoint Security Cloud is packed full of features including anti-virus, anti-ransomware, password management, data leak detection, home Wi-Fi network monitoring, HDD health check and parental controls. All designed to give you peace of mind that whatever you do online, your data and privacy and are always protected.
For example, enjoy exclusive benefits like finding out in real-time if an unauthorized device connects to your network, or discovering if your private account data has been leaked online. Plus as the subscription owner, the solution is linked to your own online account. Which means you can manage your security settings easily from anywhere you can get online.