A breach in a system's safety is not the biggest threat of RTF files RTF (Rich Text Format), as presented to many users, is considered to be a so-called universal remedy against obtrusive macro-viruses and any other sort of malicious code. Numerous anti-virus companies categorically recommend not...
A breach in a system's safety is not the biggest threat of RTF files
RTF (Rich Text Format), as presented to many users, is considered to be a so-called universal remedy against obtrusive macro-viruses and any other sort of malicious code. Numerous anti-virus companies categorically recommend not accepting any standard MS Word (DOC) files. It is true that RTF files cannot contain a macro-program (macros) in basic form - in the instance of conversion by standard means from other formats, the macros are automatically deleted - however, this same RTF feature has a flip side to it: users are lulled into a sense of security, ignoring the basic principles of safety when working with RTF documents.
What is RTF?
Rich Text Format is the most widespread standard for presenting graphical and text data. Practically all text editors functioning on various types of processors and operating systems support RTF, which, when created on a PC compatible with Windows, easily allows, for example, for MacOS users to read the files interchangeably.
A standard RTF-file structure presents itself as a succession of cell data contained in special labels (tags) indicating the section beginning or end to the program processor. The data could be of different types: text block, graphics, datasheets, executable files, etc.
Upon starting up an RTF file, a processor views its contents and automatically executes all known sections and passes those unknown. Moreover, the RTF structure features the seamless leading into other sections necessary for a user to complete specific tasks. These new sections do not have any effect on the overall document operability.
A fly in the ointment
As with any remedy connected with information technology, a standard RTF file also has not been able to avoid contamination by a fly - in this case, two.
Firstly, the most widespread RTF-file processor, Microsoft Word, as is the case with many other applications and operating systems, has not been able to thwart a breach in system safety. On May 21 of this year, Microsoft issued a report about the latest security breach allowing an unwitting user to launch macro-viruses from an RTF file.
As is known, the macro-viruses are malicious macros capable of carrying out various actions and gaining access to other files without user permission. The macros may be found directly in documents (or templates), or they may be downloaded from other (even remote) sources using hyperlinks. In both cases, MS Word should automatically display a warning about unknown macros possibly containing viruses found in the document.
However, as it turned out, this defense doesn't work for RTF files. As a result of this, malefactors can copy a link to the document directed to a remote Web site containing a macro-virus infected template. When reading the RTF file, MS Word, automatically and without any kind of a warning, downloads this template and imperceptibly starts the virus. At the same time, the virus writer can at any time modify the saved file on the Web site, adding additional functionality.
Microsoft, by the way, has already released a patch for this security breach. At this time, there has not been one piece of malicious code detected exploiting this system breach. In spite of this, however, Kaspersky Lab recommends downloading and installing the patch available on the Microsoft company site ASAP, because history has proven itself to not be on the side of the heedless user. At the beginning of 1999, the same kind of breach was detected in the MS Word DOC-file processor. The first virus, ATU-created by the infamous Australian hacker going by the pseudonym of "1nternal," who used the virus in order to hack into computers-appeared within two days following the patch's release. Naturally, the virus' spreading was attributable user apathy in installing the patch on the necessary software.
The second fly in the ointment dispelling the myth surrounding RTF files' apparent safety is that they can contain typical executable files; however, in order to activate them, a user must click on the link present in the RTF-document text. Most recently, this method of hacking has become more popular amongst Trojan horse programs. Together with typical EXE files that draw immediate suspicion unto themselves, RTF documents display an alluring text and suggest the clicking of a little icon found in the text body. The icon could contain some harmless name and even some extension, enabling the virus writer simply to take advantage of a user's lack of knowledge about the hidden danger in RTF files.
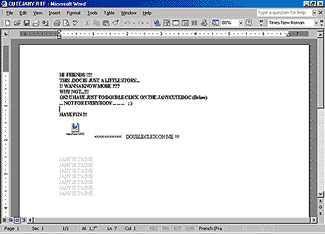
Right after it is executed, MS Word transfers the binary code from the RTF file to the operating system, which automatically defines the type of binary code, checks the file associations table and invokes the correspondent file processor for binary code execution. In the case of a VBS file, it will be Windows Scripting Host, and with an EXE file, it will be a Widows command processor, etc. As a result, a user could be victimized by the viruses such as LoveLetter or Chernobyl embedded in an RTF document.
RTF or not RTF?
The main purpose of this article is to bring to light the danger awaiting users working with documents in RTF format, and to recommend the safest means for dealing with such a danger.
If the level of safety in DOC and RTF files is assessed as a whole, it follows to recognize the fact that DOC files conceal more danger, and they could also carry embedded executable files triggered by one click of an icon. In addition to this, they could contain macro-viruses - one of the most widespread types of malicious code. If a choice is to be made between these two formats (DOC or RTF), Kaspersky Lab recommends RTF; however, it is necessary to adhere to the following when working with RTF files:
- Install the proper patches in a timely manner for use with the text editor, especially if they concern working with RTF documents.
- It is absolutely necessary to check RTF documents using an anti-virus containing the latest updates of the anti-virus database.
- Under no circumstances start up the contents in RTF documents directly from the links to any files.
Kaspersky Anti-Virus can be purchased in the Kaspersky Lab online store or from a worldwide network of Kaspersky Anti-Virus distributors and resellers.
Download the FREE time-limited trial version of Kaspersky Anti-Virus here.
Subscribe to Kaspersky Lab' FREE information service here.
Related Links:
