WINDOWS VIRUSES Win32.Devir NETWORK WORMS Worm.Cheese Worm.Sadmind Worm.SadMind.b Worm.SadMind.c I-Worm.HappyTime I-Worm.Moncher I-Worm.Puron I-Worm.Hydra I-Worm.Mari WINDOWS VIRUSES Win32.Devir This is a per-process memory resident parasitic poly-morphic Win32-virus. The virus infects PE EXE files...
WINDOWS VIRUSES
NETWORK WORMS
WINDOWS VIRUSES
Win32.Devir
The PE EXE infection method is a complex and is similar to the Win32.Driller virus. The block of host file code that is overwritten by the virus poly-morphic routine in some cases may be also compressed during infection.
The virus also contains a backdoor routine that opens an Internet connection, waits for its author's instructions and then follows them: sends/receives files, executes programs, reports system information, etc.
The virus contains the following "copyright" text:
Intruder v.0.1 by Deviator//HAZARD
NETWORK WORMS
Worm.Cheese
This is an Internet worm that replicates between systems that were previously hacked by the "Ramen" Linux worm, and not the "Lion" or "Adore" worms as it is stated in other various descriptions, or the worm itself. (see the text below) "Cheese" will also act as a "security patch" that removes the backdoors added by previous attacks, but it will not remove or patch the vulnerabilities used to hack the respective systems; thus, the machines will still remain vulnerable to the original attack(s) used to compromise them. The worm contains the following text:
> # removes rootshells running from /etc/inetd.conf
> # after a l10n infection... (to stop pesky haqz0rs
> # messing up your box even worse than it is already)
> # This code was not written with malicious intent.
> # Infact, it was written to try and do some good.
No matter how good the original intention of the author was, "Cheese" remains a piece of replicative "malware" that eats up resources such as CPU, memory, disk space or Internet bandwidth from infected systems; thus,
remaining a "bad thing".
[ More... ]
Worm.Sadmind
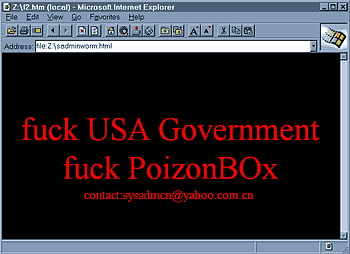
The worm was apparently written by someone with strong pro-Chinese views: "PoizonBOx" is a group of hackers that attacks and defaces US Web sites over the Internet.
[ More... ]
Worm.SadMind.b
Worm.SadMind.c
I-Worm.HappyTime
Additionally, the worm infects all .HTT files in the "WEB" subfolder of the Windows folder. Windows uses these files to customize some folders in view in Explorer when the Web mode is enabled (for example, the Program Files folder). Infection of these files causes the execution of the worm code each time a specific folder is displayed.
[ More... ]
I-Worm.Moncher
INSTALL
Install complete.
ERROR!
Unable to run program!
Subject: With Love
Body: Whit all my love for you. :)
Attach: Winhlp.exe ��� MonCherry.zip
On January 13th, the worm overwrites the C:\AUTOEXEC.BAT file with a DOS batch program that will format the C: drive upon the next reboot.
[ More... ]
I-Worm.Puron
The worm code has the "copyright" text strings:
(c)Vecna
Vecna is a punk rocker now...
The infected messages are of HTML format and have fields:
From: "Mondo bizarro" [mourning@obituary.org]
Subject: Joey is dead, man... :-(
Text: A tribute to Joey Ramone (1951-2001)
Attach: ramones.mp3.exe
The worm uses one of the security vulnerabilities (Vulnerability identifier: CAN-2001-0154) that were found in MS Windows in 2001. The result of this breach is the possibility of spawning an attached EXE file without a user's action. When an infected e-mail is opened for reading or preview, the worm's EXE file is automatically run.
[ More... ]
I-Worm.Hydra
[I-Worm.Hydra] ...by gl_st0rm of [mions]
"AVP Monitor"
"AntiVir"
"Vshwin"
"F-STOPW"
"F-Secure"
"vettray"
"InoculateIT"
"Norman Virus Control"
"navpw32"
"Norton AntiVirus"
"Iomon98"
"AVG"
"NOD32"
"Dr.Web"
"Amon"
"Trend PC-cillin"
"File Monitor"
"Registry Monitor"
"Registry Editor"
"Task Manager"
The worm also kills Kaspersky Anti-Virus (former AVP) anti-virus databases
[ More... ]
I-Worm.Mari
Subject: Hi!
Body: check this out!!!
Attach: system32.exe

Upon a mouse click on the icon, the worm displays the message:
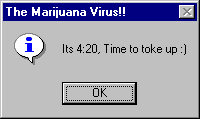
IMPORTANT: PLEASE READI think i speak for every pot smoker in North America when i say: *Legalize Marijuana*...I mean if people with AIDS, Cancer and other deaises can use it then why cant the rest of us (pot smokers) use it?, I dont think that's very fair (Do you?). If it's legal to grow and use in places like: Australia (for personal use) then why not in North America? If doctors are useing it as a treatment for illness then it must not be *THAT* harmful (So why can't other people use it?). I really do think the federal goverment should consider legalization of marijuana. Well that's really all i have to say on the matter, but i do hope somebody, somewhere listens to what i have to say and does not just regard this as just another *virus* because it's more then that, it's a message, a message for freedom, the freedom to smoke up and have the chose to do so *WITHOUT* fear of punishment from the law and the goverment. Thank you for your time.
At 4:20 and 16:20, the worm displays the message box:
[ More... ]
