Kaspersky Lab, a leading developer of Internet threat management solutions that protect against all forms of malicious software including viruses, spyware, hacker attacks and spam, reports that the script Trojan-Downloader program, Gumblar, has made a resurgence to dominate the Internet threat...
Kaspersky Lab, a leading developer of Internet threat management solutions that protect against all forms of malicious software including viruses, spyware, hacker attacks and spam, reports that the script Trojan-Downloader program, Gumblar, has made a resurgence to dominate the Internet threat landscape throughout February 2010.
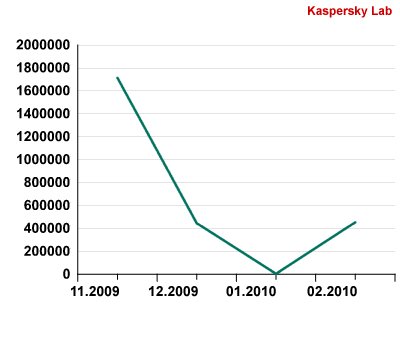
During last month, Kaspersky Lab recorded a dramatic surge in the variant, Gumblar.x, with 453,985 infections recorded, following a disappearance from the threat landscape altogether in January. Gumblar hit the headlines at the end of May 2009 when it went straight to the top of Kaspersky Lab’s Top Twenty ranking of threats on the Internet. In October, the company reported that new variants of the program (Gumblar.x and Gumblar.w) had been detected, using more sophisticated technologies than their predecessors, with the number of attempted downloads recorded at 740,836.
For the second consecutive month Trojan variants continue to dominate the online threat landscape. Kaspersky Lab expected a further resurgence of Gumblar and this new attack didn’t take long to materialise. However, this time the black hats haven’t changed their approach in any significant way and have simply been gathering new data that can be used to access websites prior to infecting them en masse.
The early incarnations of Gumblar demonstrated how Cybercriminals are able to take old attack methods and rework them. Initially, the program would contact dedicated malicious servers to fetch more malware. This evolved and later versions of Gumblar that are downloaded as password stealers, used to compromise legitimate websites.
The number of websites infected by Gumblar.x
Another Trojan-Downloader program worthy of note for its high level activity during February is Pegel, which grew almost six-fold throughout the month and has now reached epidemic proportions since being first detected in January. This program has similarities to Gumblar, in that it also infects perfectly legitimate websites. A user that visits an infected web site is redirected by the malicious script to a Cybercriminal resource and to ensure users don’t suspect anything, the names of popular websites are used in the addresses of malicious pages.
From the reports of the first two months of 2010 it is clear that Kaspersky Lab’s forecast of more sophisticated malware are being held to be true.
Top twenty ranking for February 2010 - Malicious programs, adware and potentially unwanted programs that were detected and neutralised when accessed for the first time, i.e. by the on-access scanner.
| Position | Change in position | Name | Number of infected computers |
| 1 | Net-Worm.Win32.Kido.ir | 274729 | |
| 2 | Virus.Win32.Sality.aa | 179218 | |
| 3 | Net-Worm.Win32.Kido.ih | 163467 | |
| 4 | Net-Worm.Win32.Kido.iq | 121130 | |
| 5 | Worm.Win32.FlyStudio.cu | 85345 | |
| 6 | Trojan-Downloader.Win32.VB.eql | 56998 | |
| 7 | Exploit.JS.Aurora.a | 49090 | |
| 8 | Worm.Win32.AutoIt.tc | 48418 | |
| 9 | Virus.Win32.Virut.ce | 47842 | |
| 10 | Packed.Win32.Krap.l | 47375 | |
| 11 | Trojan-Downloader.WMA.GetCodec.s | 43295 | |
| 12 | Virus.Win32.Induc.a | 40257 | |
| 13 | not-a-virus:AdWare.Win32.RK.aw | 39608 | |
| 14 | not-a-virus:AdWare.Win32.Boran.z | 39404 | |
| 15 | Worm.Win32.Mabezat.b | 38905 | |
| 16 | Trojan.JS.Agent.bau | 34842 | |
| 17 | Packed.Win32.Black.a | 32439 | |
| 18 | Trojan-Dropper.Win32.Flystud.yo | 32268 | |
| 19 |  Return Return | Worm.Win32.AutoRun.dui | 32077 |
| 20 | not-a-virus:AdWare.Win32.FunWeb.q | 30942 |
Top twenty ranking for February 2010 - Malicious programs on the Internet, reflecting the online threat landscape. This ranking includes malicious programs detected on web pages and malware downloaded to victim machines from web pages.
| Position | Change in position | Name | Number of attempted downloads |
| 1 |  Return Return | Trojan-Downloader.JS.Gumblar.x | 453985 |
| 2 | Trojan.JS.Redirector.l | 346637 | |
| 3 | Trojan-Downloader.JS.Pegel.b | 198348 | |
| 4 | not-a-virus:AdWare.Win32.Boran.z | 80185 | |
| 5 | Trojan-Downloader.JS.Zapchast.m | 80121 | |
| 6 | Trojan-Clicker.JS.Iframe.ea | 77067 | |
| 7 | Trojan.JS.Popupper.ap | 77015 | |
| 8 | Trojan.JS.Popupper.t | 64506 | |
| 9 | Exploit.JS.Aurora.a | 54102 | |
| 10 | Trojan.JS.Agent.aui | 53415 | |
| 11 | Trojan-Downloader.JS.Pegel.l | 51019 | |
| 12 | Trojan-Downloader.Java.Agent.an | 47765 | |
| 13 | Trojan-Clicker.JS.Agent.ma | 45525 | |
| 14 | Trojan-Downloader.Java.Agent.ab | 42830 | |
| 15 | Trojan-Downloader.JS.Pegel.f | 41526 | |
| 16 |  Return Return | Packed.Win32.Krap.ai | 38567 |
| 17 | Trojan-Downloader.Win32.Lipler.axkd | 38466 | |
| 18 | Exploit.JS.Agent.awd | 35024 | |
| 19 | Trojan-Downloader.JS.Pegel.k | 34665 | |
| 20 | Packed.Win32.Krap.an | 33538 |
To find out more about computer threats visit: www.kaspersky.co.uk/threats.
To read the latest security news please visit: threatpost.com.
