New Kaspersky data has shown that more Windows and Linux users faced vulnerability exploits in the first half of 2025 compared to 2024. The total number of vulnerabilities registered in the first half of 2025, according to cve.org, also increased compared to previous periods, with аttackers actively using exploits as a tool to access user systems.
Full information is available in Kaspersky’s new report Exploits and Vulnerabilities in Q2 2025.
An exploit is a type of malware that is designed to take advantage of an existing bug or vulnerability in an application or operating system to gain unauthorized access to systems. Kaspersky research shows that the share of exploits targeting critical vulnerabilities in operating systems reached 64% in Q2 2025 (up from 48% in Q1 2025), with third-party apps (29%) and browsers (7%) following.
The number of Linux users encountering exploits shows an upward trend in 2025 compared to 2024. Specifically, in Q2 2025 the number of such users was over 50 points higher than in Q2 2024, and the Q1 2025 figure was almost 2 times higher than the same period of 2024.
The number of Windows users who encountered exploits also showed an upward trend for Q1 and Q2 2025: There was a 25 point growth in Q1 2025 compared to Q1 2024 and an 8 point growth in Q2 2025 compared to Q2 2024.
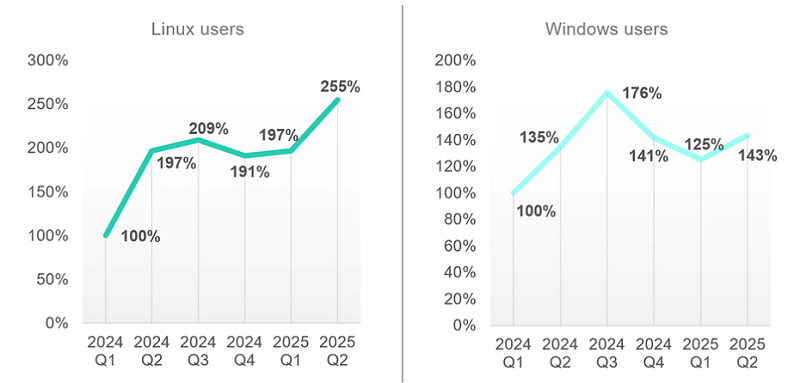
Number of users
protected by Kaspersky solutions and facing vulnerability exploits in 2024-2025
(Q1 2024 figures are taken as 100%)
Among the vulnerabilities used in advanced attacks (Advanced Persistent Threat, APT) are both new 0-days and vulnerabilities that had been known before. Most often, these are tools for accessing the system and escalating privileges. More detailed information is available in the report on Securelist.
“Attackers increasingly use methods to escalate privileges and exploit weaknesses in digital systems. As the number of vulnerabilities continues to grow, it is very important to constantly prioritize patching known vulnerabilities and use software that can mitigate post-exploitation actions. CISOs should counter the consequences of exploitation by searching for and neutralizing command and control implants that can be used by attackers on a compromised system,” says Alexander Kolesnikov, a security expert at Kaspersky.
According to cve.org, both the number of critical vulnerabilities and the overall number of registered CVEs (Common Vulnerabilities and Exposures) surged in the first half of 2025. At the beginning of 2024 there were around 2600 CVEs registered monthly, with the number increasing throughout the year. In comparison, 2025 has already seen over 4000 CVEs registered monthly.
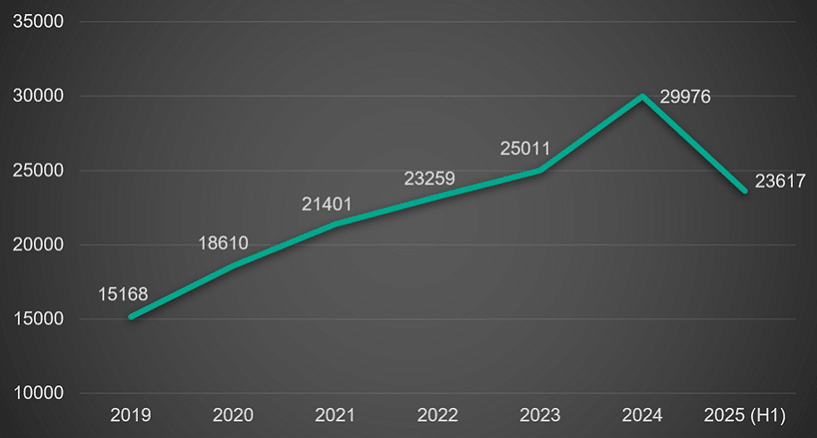 New CVEs with the share of critical vulnerabilities,
2019-2025. Source: cve.org
New CVEs with the share of critical vulnerabilities,
2019-2025. Source: cve.org
To stay secure in this shifting threat landscape, Kaspersky advises organizations to:
- Investigate vulnerability exploits exclusively within secure virtual environments.
- Ensure 24/7 monitoring of infrastructure, with a focus on perimeter defenses.
- Maintain a robust patch management process by promptly installing security updates. To set up and automate this, use Vulnerability Assessment and Patch Management and Kaspersky Vulnerability Data Feed.
- Deploy reliable solutions to detect and block malicious software on corporate devices, alongside comprehensive tools that include incident response scenarios, employee training programs, and an up-to-date cyberthreat database.
