Kaspersky experts have discovered how cybercriminals are using IPFS file distribution in email phishing attacks. Since late 2022, fraudsters have been using this safe, decentralized and reliable way for file distribution – considered to be one of the cutting-edge technologies of Web 3.0 – to target companies around the world. In a new report by Kaspersky, researchers reveal how attackers are putting phishing HTML files in IPFS to cut web hosting costs. This technique, used for both ongoing mass and targeted phishing campaigns, saw almost 400,000 phishing emails detected in February 2023.
IPFS (InterPlanetary File System) is a peer-to-peer distributed file system enabling users around the world to exchange files. Unlike centralized systems, IPFS uses addressing performed according to unique content identifiers (CID), and not file paths. The file itself resides on the computer of the user who had “uploaded” it to IPFS and downloaded directly from that computer. By default, uploading or downloading a file to IPFS requires special software (IPFS client). For users to view the files residing in IPFS freely without installing any software, the so-called gateways are provided.
In 2022, scammers began actively using IPFS for email phishing attacks. They place HTML files containing a phishing form in IPFS and use gateways as proxies, so that victims can open the file, whether or not they are running an IPFS client on their devices. The scammers also include file access links via a gateway into phishing letters dispatched to would-be victims.
The use of a distributed file system allows attackers to cut back on phishing page hosting costs. Besides, it’s impossible to delete files uploaded by third parties from IPFS. If somebody wants a file to disappear from the system completely, they can urge its owners to delete it, but the method will probably never work with cybercriminals anyway.
IPFS gateway providers attempt to combat IPFS phishing by regularly deleting links to fraudulent files.
Phishing page deletion notification
Yet detection and deletion of links at gateway level does not always happen as quickly as the blocking of a phishing website, cloud form, or document. The URL addresses of IPFS files were first appeared in October 2022. As for now, the campaign is ongoing and being blocked by Kaspersky.
Phishing letters containing IPFS links are hardly ever too original — they contain the typical phishing content the purpose of which is to obtain the victim’s account login and password. What is interesting about this technique is where the HTML pages links go.
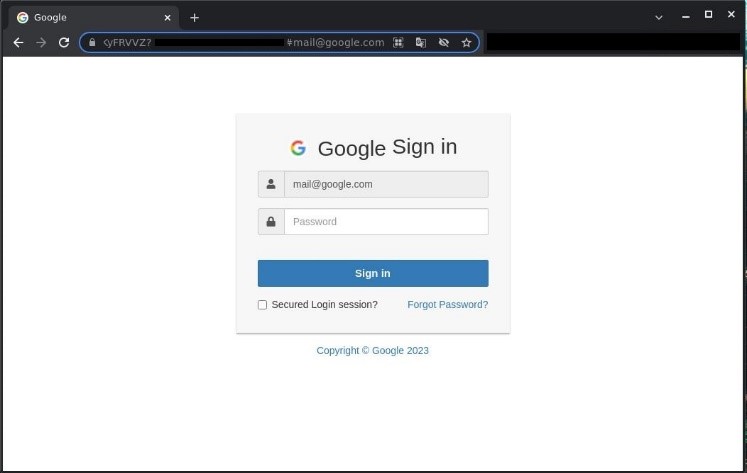
HTML page used for phishing
The URL parameter contains the recipient’s email address. Once modified, the corporate logo on top of the phishing form and email address entered into the login field will change too. This way, one link can be used in several phishing campaigns targeting different users — sometimes even in dozens of campaigns.
In late 2022, Kaspersky observed two – 15,000 IPFS phishing letters-a-day for most of the time. Starting this year, IPFS phishing began to grow in scale, reaching more than 24,000 letters-a-day in January and February.
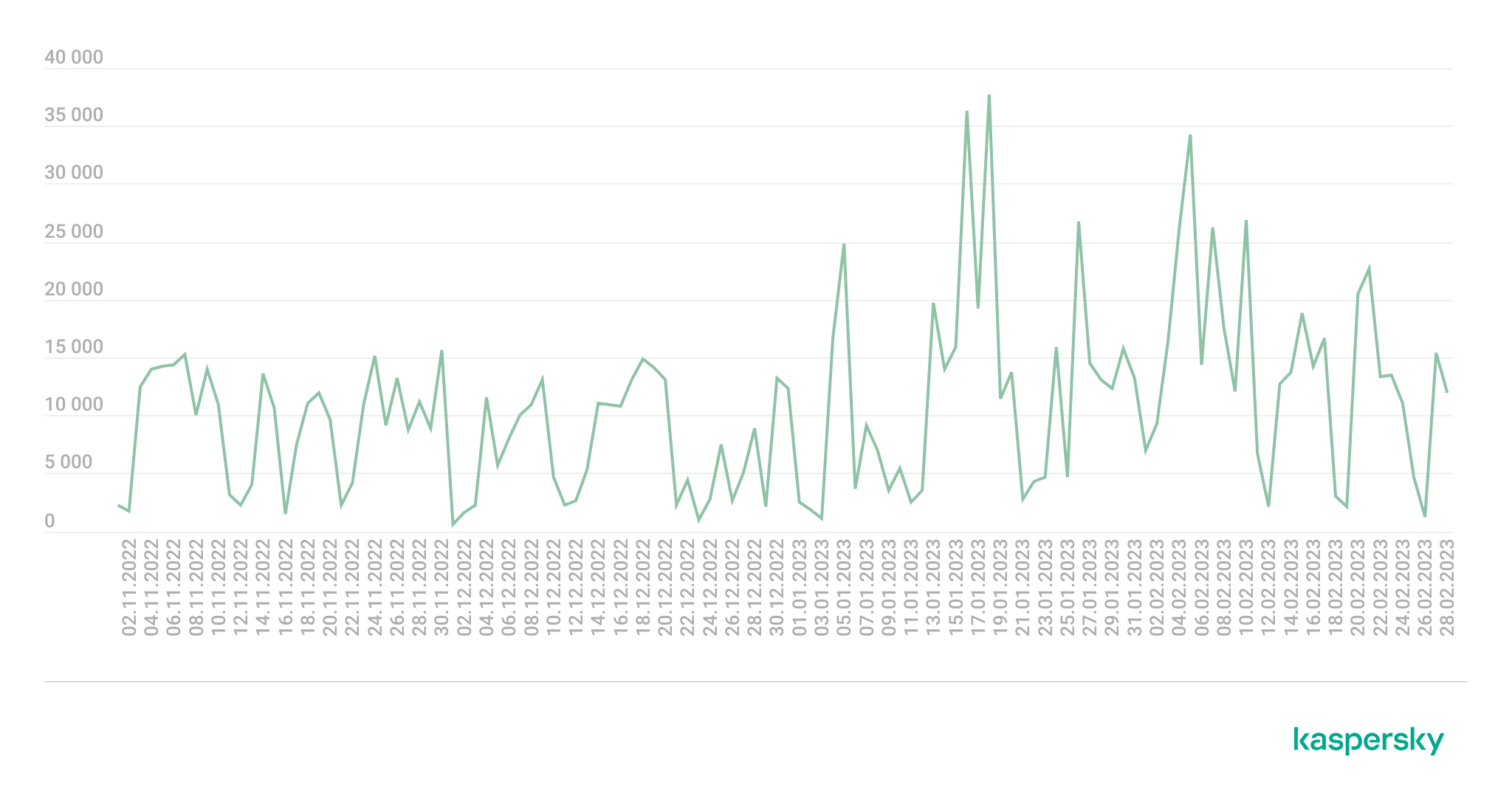
Dynamics of the number of IPFS phishing attacks, November 2022 — February 2023
February was the busiest month in terms of IPFS phishing activity. In that month alone, researchers observed almost 400,000 letters – a 100,000 increase than in November and December 2022.
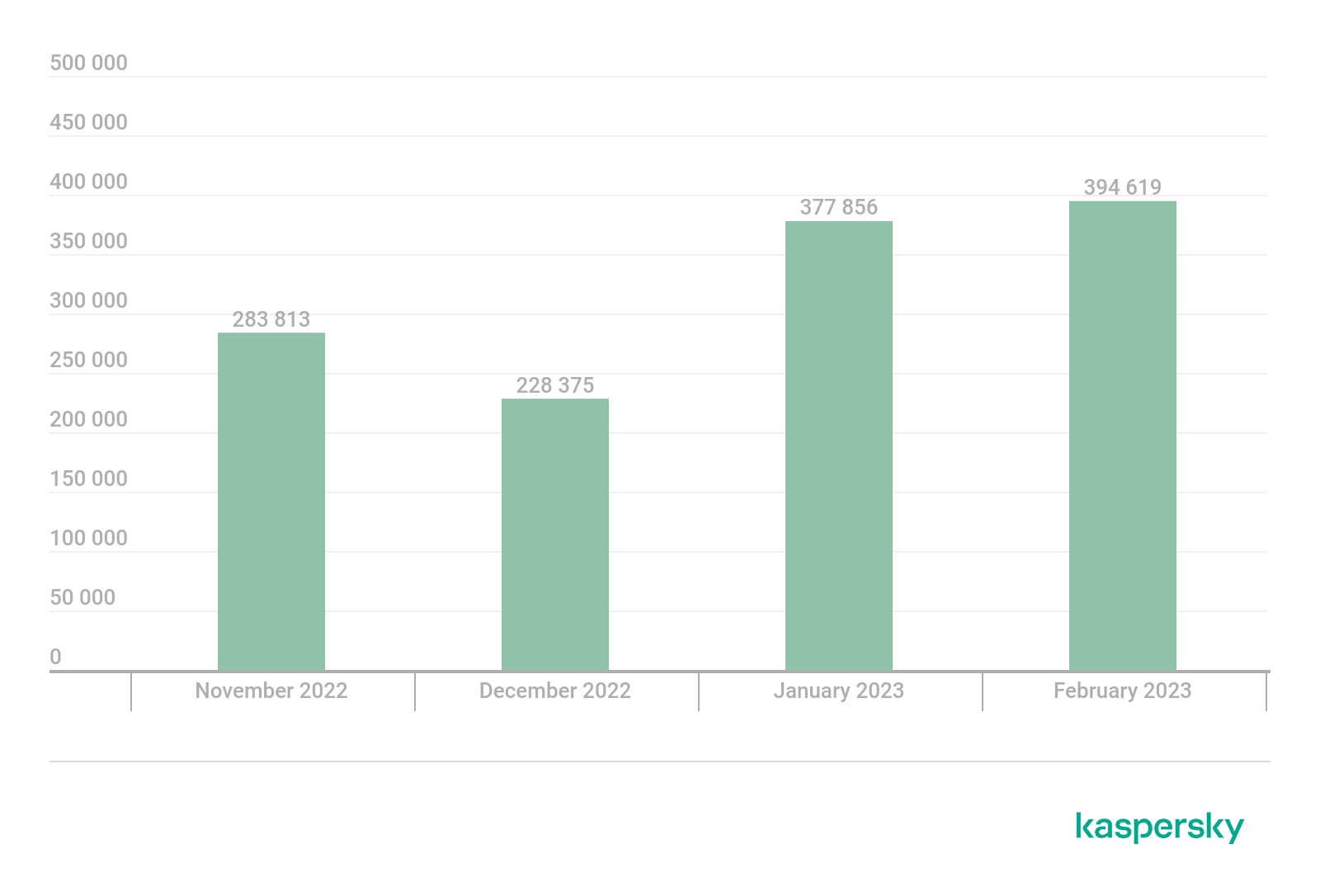
IPFS phishing letters distribution by month, November 2022 — February 2023
“Attackers have and will continue to use cutting-edge technologies to reap profits. As of late, we have observes an increase in the number of IPFS phishing attacks — both mass and targeted. The distributed file system allows scammers to save money on domain purchase. Plus, it is not easy to completely delete a file, although, there are attempts to combat fraud at IPFS gateway level. The good news is that anti-spam solutions detect and block links to phishing files in IPFS, just like any other phishing links. In particular, Kaspersky products employ a number of heuristics to detect IPFS phishing,” comments Roman Dedenok, a security expert at Kaspersky.
Learn more about the IPFS phishing scheme on Securelist.
To protect yourself and your company from spam email campaigns, Kaspersky recommends the following:
- Provide your staff with basic cybersecurity hygiene training. Conduct a simulated phishing attack to ensure that they know how to distinguish phishing emails
- Use a protection solution for endpoints and mail servers with anti-phishing capabilities, such as Kaspersky Endpoint Security for Business, to decrease the chance of infection through a phishing email.
- If using Microsoft 365 cloud service, don’t forget to protect it too. Kaspersky Security for Microsoft Office 365 has a dedicated anti-spam and anti-phishing as well as protection for SharePoint, Teams and OneDrive apps for secure business communications.
