
A Skype Trojan steals your CPU power
Kaspersky Lab experts have discovered a new trojan virus attacking skype users. Find out how to recognize it before you fall victim.
772 articles

Kaspersky Lab experts have discovered a new trojan virus attacking skype users. Find out how to recognize it before you fall victim.

Just a few years ago, it was rare to find someone who had more than one or maybe two Internet-connected devices in their home. Now, you’d have to look high

For most of us, April 1 is that one day each year we get to pull pranks and lie unashamedly to scare and confuse our friends and family — more

Imagine a world where, for every useful message, you also get three advertising, fraudulent or malicious ones in your mailbox. Suddenly the convenience of keeping in touch via email would

The threats facing mobile devices are among the fastest growing and most serious dangers to the digital world. We gathered your questions on the subject and passed them on to

Isolation is a key concept in information security. For example, computers critical to services such as electric utilities or financial systems are often kept isolated, or air-gapped, from the Internet.

Despite cries and outrage from the security industry that passwords are an inadequate form of authentication for access to computers and online services, so many mechanisms depend on these secret

The steady growth in the number of malicious programs targeting the Android operating system was one of the most significant IT security issues in 2011. Today, almost 90% of mobile

Creating backup copies is one of the most reliable methods of safeguarding important data: whatever happens to your valuable files, you will always have a copy at hand. This is

Watch how Kaspersky Anti-Virus blocks threats and uses cloud-based technology to provide real-time protection. And, yes, it’s fully compatible with Windows 8.

User friendliness and ease of use are up there with reliable protection when deciding on IT security solutions. One might think that these two requirements are incompatible – a complex

RSA is like the Hogwarts of Security, the annual reunion for cyber jedi masters or the secret fight club for private security companies, governmental agencies and international organizations. We’ve got

RSA is the major event in security. Basically it’s like the Big 8 International Conference or, better yet – the Olympics of security – except nobody is throwing spears and

Young researchers, original security projects, making contacts among your peers, and a stepping-stone into the professional community – these are the key ingredients of Kaspersky Academy’s ‘CyberSecurity for the Next

Due to a lack of malicious activity targeting Mac OS X it has been considered a relatively safe operating system for some time now. But times change, and that complacency
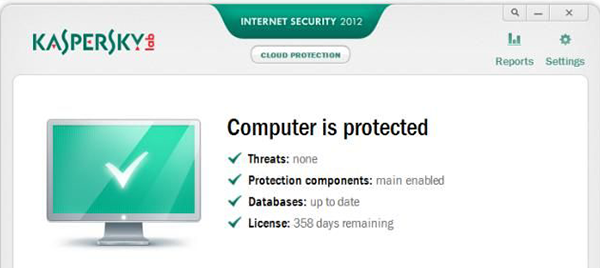
Home PCs and laptops remain an important place for storing sensitive information, including personal emails, logins and passwords, photos, financial data and more. Of course, this information needs to be

We were able to sit down with the students and graduates who present their researches at Kaspersky Lab`s “Cybersecurity for the Next Generation” students conference that took place last week

All industries, including IT, need emerging talent and ambitious specialists joining their ranks, bringing with them fresh ideas that help create a foundation for future innovations. Every year millions of

Stefan Tanase, Kaspersky Lab’s Senior Security Researcher, Global Research & Analysis Team, answers users’ questions about social networks, malware and everything in between. There is a saying: “information is power”

Olga Rumyantseva has succeeded in her solo-climb of the highest volcano in Antarctica – Mount Sidley! Olga was lucky with the weather (though you could be forgiven for thinking otherwise

Renowned mountaineer Olga Rumyantseva has started her first ascent of the Kaspersky 7 Volcanoes expedition. Olga is set to solo-climb the highest volcano on each continent and a week ago