Sorting Out Digital Clutter In Business
Kaspersky Lab brings together digital workplace and personal habits to assess cyber risk
Introduction
Digital clutter at work is a very real problem…
In an increasingly digital world we are creating digital documents and files at an unstoppable rate. Working environments have transformed and, while we’re no longer surrounded by filing cabinets and paperwork, the digital environment we work in is often crowded with the digital equivalent of these.
Keeping track of all these documents, ensuring that they have the right access permissions, are deleted when appropriate and don’t go beyond the company walls, can be a difficult task. Consequently, they can amount to what we’re calling ‘digital clutter’.
Digital clutter potentially presents a security risk to businesses. The data that is contained in these documents and files can travel beyond a business’s control and be used against the organisation. Whether it’s an organised hacker, a malicious insider or a disgruntled ex-employee, digital clutter becomes a problem when it compromises data security.
The choices we make when we save files, monitor permissions and access to documents and decide what we delete and save form our digital lives, is arguably guided by those everyday habits which also have a bearing on the way we behave in other situations in everyday life.
Are you typically an organised type of person, for example?
How likely are you to attempt to add organisation to a situation to make it less chaotic?
Consequently, there may be connections between your digital clutter at work and clutter in other areas of your life. From being able to find a receipt you filed 10 years ago to remembering to delete confidential information you were sent to book a holiday for a friend, through to how tidy your fridge is.
…and it got us thinking about causes of the corporate digital clutter…
For example, what does the organisation of your fridge say about your natural habits?
Do the same human habits that drive our digital clutter, drive our inclination to have a messy fridge?
To understand if this was true, we at Kaspersky Lab commissioned OnePoll, an online quantitative survey specialist, for a global research project to dig into those human habits and understand how they may translate across our work and home lives.
We surveyed 7,000 employed adults from December 2018 to January 2019 across the UK, USA, France, Spain, Germany, Italy, Brazil, China, Mexico, Japan, Malaysia, South Africa, Russia and Turkey who work in an office and use computers. They were asked a number of questions around their personal use of digital documents, including the type of information it included as well as how they manage access rights. The same respondents also answered questions on the organisation of their fridge, how often they de-clutter and other questions which could indicate the human habits that guide both digital clutter at work and fridge organisation.
We took a look at:
- What sort of digital clutter exists in a typical working environment?
- What type of people are most likely to create digital clutter?
- Whether our tendency to create digital clutter points to a trend in our human habits?
- Whether those human habits also manifest in other ways in our everyday lives?
- And, therefore, is there a connection between the human habits that guide the organisation of our fridge and the digital clutter we create at work?
…because this impacts your – and your company’s – resilience to cyber attack
Digital clutter presents a significant cyber risk for organisations. With so many digital documents and files in our working lives, maintaining access controls, ensuring confidential information is protected and doing this across every digital asset is no small task.
It doesn’t take much for a disgruntled ex-employee or negatively motivated competitor or an accidental malware infection to compromise corporate perimeter security. From here, they can steal the data and use it to launch further attacks – either through distributing further malware or using ransomware – putting the business, employees and the data at risk.
Key stats:
- More than a third (37%) of people have accidentally found confidential information of their colleagues e.g. salaries / bonuses at work
- A third (33%) of people claim to have access to files from a previous workplace
- 80% of people don’t think they are responsible for ensuring documents such as emails, files and documents have the appropriate access controls or limits
- 72% of employees store documents at work that contain personally identifiable information or sensitive data
- 95% of people who claimed to have an organised or somewhat organised fridge, also claimed to have an organised or somewhat organised digital life
Does your digital clutter make you a security threat at work?
Digital clutter can exist in any office and represents a systematic organisational problem.
In the world we live in, we need digital documents to get our day-to-day work done. Whether it be the accounts team digitally filing away spreadsheets to be used for forecasting or the HR team digitally storing job descriptions for a company. For every digital document and every folder there needs to be a consideration around who should have access, how long for and the level of security the data contained requires. In some instances, this may require robust encryption and an expiration on access to the file, in others the file may need to be saved somewhere specific to automatically apply access rights – for example in a shared folder, where only the relevant people can access the document.
With so many documents and so many security considerations, losing track of these documents and their respective security conditions becomes a very real possibility. Which is why digital clutter should be more than just a productivity concern, it is a security issue as well.
What’s more, if businesses and employees aren’t aware of the fact that they even have digital clutter, let alone the security implications of it, the consequences could be significant.
We talk about how data could become the currency of the future and consequently these documents and folders represent pockets of value. Value that is recognised not least by hackers. Each document an attacker can get into presents a wealth of opportunity to compromise security and access a network. Financial information could be so valuable that they can hold the company to ransom over the data, for example. Job vacancy information could enable a frustrated employ to spoof a job applicant email and serve malware to an HR administrator with very little hacking knowledge, for example.
A third of people confess to experiencing security incidents that could have been the result of digital clutter
In our global research into digital clutter in a working environment we found that more than a third (37%) of people have accidentally found confidential information such as information on salaries and bonuses while at work. If an employee can accidentally come across this type of sensitive information, so might a hacker.
Another very real implication of digital clutter is that if documents and files are forgotten but live online – for example in collaboration apps or documents stored in cloud storage or databases – people can gain access to the document even when they have left a company. Indeed, more than a third (33%) of people claim to still have access to files from a previous workplace.
For the business this represents a huge problem. Insider threat – when an employee exploits their privileged access to compromise the security of a business – is always a threat to businesses, but with cloud environments and access that exists beyond an employee’s tenure at an organisation.
Scenario:
Imagine you’re the owner of a small to medium sized business. Can you confidently say you know where all of the confidential data your business holds resides as well as the security that surrounds it? Can you confidentially say that you know for sure that your employees haven’t stumbled across confidential information? Do you know what your company’s policy is for reneging access of employees that have left the business? Is it feasible to imagine that an ex-employee could have access to a Google document on an event they worked on when they were an employee?
Let’s talk about security
There are a number of examples of breaches that have potentially been caused by digital clutter, from the Yandex search system posting results including Google Documents because they weren’t protected by passwords, through to insider threat which becomes a very external problem when an employee leaves but still has access to employee data on their personal hard drive – as was the case with Coca-Cola. That’s not to mention that with the prolific use of collaboration tools, attackers can easily launch a phishing attack mimicking the types of emails sent by these services; such as access requests or updates.
Is generation Z the worst digital clutter culprit?

Figure 1: Have you ever shared your username and password credentials for your work device(s) with a co-worker? (Chart 5*)
If you compare the digital clutter habits of 18-24 year olds at work to those over the age of 55, there are some clear differences. The younger group are significantly more likely to have accidentally found confidential information at work and be able to access files from a previous workplace.
You would think that this recognition of finding confidential information and having access to files they shouldn’t, would make the younger generations more security aware. Our research found the opposite: 18-24 year olds are nearly doubly as likely (30% compared to 18% for 55+ years olds) to have shared their username and password for a work device with a co-worker.
Modern-day employees take little responsibility for workplace digital clutter
Digital clutter in the workplace is a by-product of the digital age, where we create documents saved on servers and in cloud environments that offer the opportunity to collaboratively work and contribute to documents. With an effective policy to protect these documents and manage access rights, security is maintained and the business is protected from hackers. Digital clutter at work doesn’t have to be a problem.
What business department is responsible for ensuring access rights and security is maintained?
How much responsibility should be on employees who create and manage documents?
The issue here is the fact that in the vast majority of businesses employees are seemingly not taking any responsibility for the documents they are creating. Indeed, our global research showed that two thirds (66%)[i] of people don’t remember all the data they have in shared documents, let alone remembered whether they have secured it or amended the access rights in line with changes in the organisation – e.g. employees leaving.
A staggering 80% of employees don’t think they are responsible for ensuring documents such as emails, files and documents have the appropriate access controls or limits, regardless of whether they have created these. A worrying statistic, considering only the employees involved may be even aware that the document or email has been created.
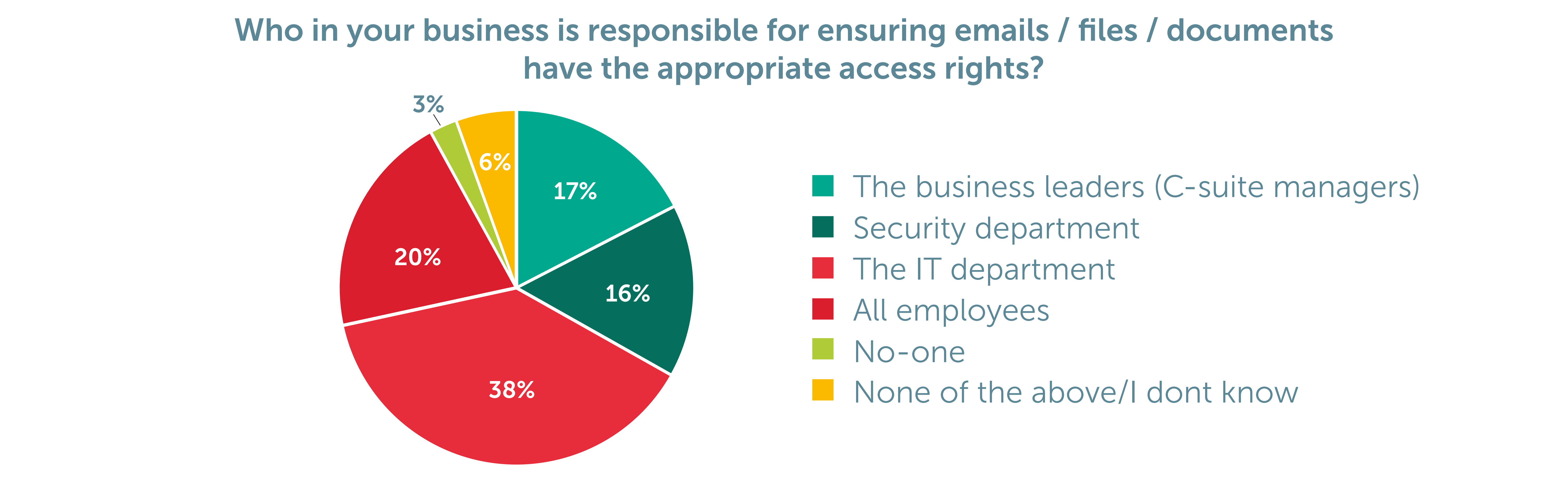
Figure 2: Who in your business do you think is primarily responsible for ensuring emails/files/documents have the appropriate access controls or limits? (Chart 13)
When you drill down into the statistics, habits relating to the responsibility of securing digital clutter seem to be significantly better in the case of workers maintaining the state of their email inbox; 56% globally delete outdated items from their email inbox on a regular basis for example. Only 34% of employees by comparison do this for their hard drive[ii].
When you consider that 72% of employees store documents at work that contain personally identifiable information or sensitive data, the true significance of the data that is under threat is concerning. More worrying is that there is a lack of responsibility being taken for this.
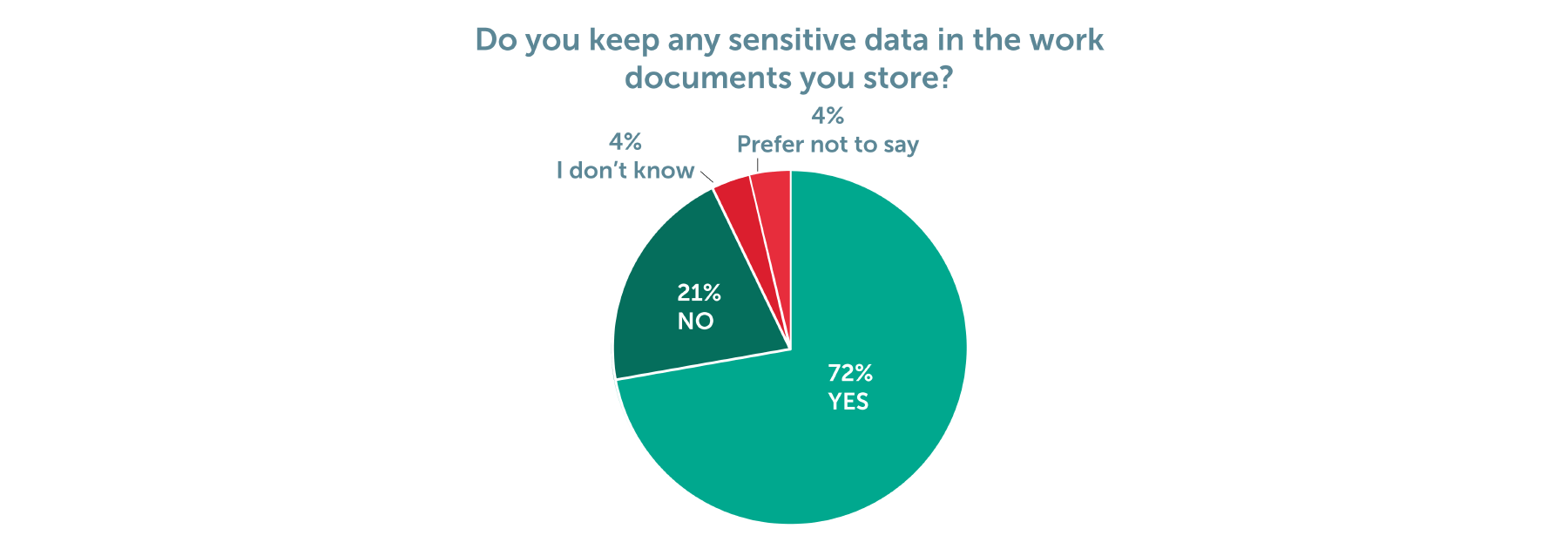
Figure 3: Do any of the work documents you store contain personally identifiable or sensitive data in? (i.e. names, addresses, email addresses, dates of birth, financial information) (Chart 3)
Scenario:
Imagine you’re in charge of sales for a small consultancy firm and your managing director asks you for a summary of the top customer wins that quarter and possible leads for the next quarter. You pull the information into a document with your team and present it to the managing director.
A member of your team then leaves the company, you don’t know where they’re heading until they pop up at a competitor consultancy firm, selling similar services. It now dawns on you that you haven’t reneged their access to the Google document summarising the key wins and prospects for the next quarter that was sent to your managing director. IT wouldn’t have locked the employee out, because they weren’t aware that the document had been created and the employee requested to login from a person Gmail account.
By this point the ex-employee has likely made a note of all your potential sales leads and recently won accounts; information that could cause your business significant financial loss and should never have leaked from the corporate network.
Scenario:
You’ve recently negotiated a pay increase as a result of some stellar work you’ve done to improve the marketing function at your insurance firm. You’ve had a conversation over email with your boss to confirm the new pay, your boss has forwarded this to finance and between the finance team they have found and updated the system with the new information.
As part of the process you remember that you want to change the bank account that your wages go into, so you also forward the new details on to the finance team. They have a discussion over who has updated the system, whether they can amend your details in time for the next pay round, all with your details on the email.
No-one deletes the email from their inbox.
A few months later an unsuspecting member of the finance team does a search for your name in their inbox to show a new team member how to act on a salary increase. They forward the email chain with your finance details included to the new staff member. But, they get the email address wrong and the email chain makes its way to someone else within the company. Unbeknownst to you, your salary is now the topic of conversation among your colleagues, damaging for you personally and a security breach.
How to recognise digital clutter at work – check your fridge!
Digital clutter is clearly a concern for businesses, with intellectual property, highly confidential information and sensitive data to steal. It is a concern for the employee too though and with data increasingly residing in the hands of its owner and being compromised in this way, doing everything you can to ensure you and your company are not breached is critical.
This is why understanding the security threat posed by digital clutter to a business and to you personally is so important.
So, back to our hypothesis – can human habits help us understand what to look out for to minimise the risk our digital clutter represents at work?
Yes, they can!
As part of our deep dive into digital clutter, we also ran research to understand what habits are behind the digital clutter we create in the workplace. Simultaneously, we also asked people questions about how those habits may manifest themselves in the organisation of their fridge.
And, what did we find? Your fridge CAN indicate the security risk of your digital clutter.
Here are some top stats that could guide you on how to recognise digital clutter at work and what warning signs your human habits might reveal:
- 95% of the people who claimed to have an organised or somewhat organised fridge, also claimed to have an organised or somewhat organised digital life. This is significantly more than those that claim to have a disorganised fridge but an organised digital life[iii]

Figure 4: How organised would you say you were in your digital life at work compared to with your fridge (Chart 22)
- 88% of those who re-organise their fridge before a holiday, also do so for their digital files before a holiday. This is significantly more than those who wouldn’t organise their fridge before a holiday but would organise their digital life

Figure 5: Before leaving the house for a long time, e.g. going on a vacation, do you usually empty/ your fridge/check best before dates of products there and organize your files/emails at work before taking holiday from work? (Chart 23)
- Two thirds (66%) of those who have bought the same item to go in their fridge twice, by accident, have also found it difficult to locate a document or file while at work.

Figure 6: Have you ever bought the same food item twice because you hadn’t realized it was already in your fridge and found it difficult to locate a document or file while at work (Chart 24)
So, next time you open your fridge and see an array of containers, mouldy cheese and dubious looking leftovers, spare a thought for your digital clutter, and consider if a spring clean is in order.
Here is our advice to businesses
Beyond checking your fridge, it’s important for businesses to consider the following actionable advice on what to do to minimise digital clutter and the security risk it represents. Our top tips for businesses include:
- Getting employees trained up – most security breaches come down to a genuine mistake from employees. It is very important that training teaches practical skills applicable to employees’ daily work in a way that isn’t boring or laborious. Using short engaging lessons based on real life events such as with Kaspersky Automated Security Awareness Platform works well.
- Regularly reminding staff how important it is to follow cybersecurity rules to not to let cyber skills fade away. For example, hanging posters in the office or handing out take-away cards with simple and practical advice.
- Making backups of essential data to ensure corporate information is safe and regularly updating IT equipment and applications to avoid unpatched vulnerabilities that may allow malware to penetrate the corporate network.
- Finding a dedicated solution for small and medium businesses with simple management and proven protection features; such as Kaspersky Endpoint Security Cloud. Alternatively, delegate cybersecurity maintenance to a service provider that can offer tailored protection.
And, some tips for employees to keep them digitally safe:
- Do not click on links in emails if they come from people or organizations you don’t know, or have suspicious or unusual addresses. Make sure all links are legitimate one and start with ‘https’, when any information is requested.
- Use your work email only for sites related to your work.
- Use only legitimate software, downloaded from official sources. If you have any problems with the installation, ask your IT team to help with it.
- Do not download, open or store random files on your work computer as they could be malicious to the whole company.
- Don’t use any personal details in your passwords. In order to ensure the greatest password strength avoid using your name, birthday, street address and other personal information.
- Keep all your passwords secure – for instance, start using Kaspersky Password Manager. This is a reliable solution that stores passwords and other sensitive data in an encrypted private vault.
[i] Question not asked to UK audience
[ii] Question not asked to UK audience
[iii] 14% more. 81% of respondents has a disorganised fridge but an organised digital life

