
World War II information security: Navajo VPN
During WW2 modern cryptography principles were often coupled with ‘amateur’ ciphering methods. Curiously, the latter ones often proved to be equally reliable
262 articles

During WW2 modern cryptography principles were often coupled with ‘amateur’ ciphering methods. Curiously, the latter ones often proved to be equally reliable
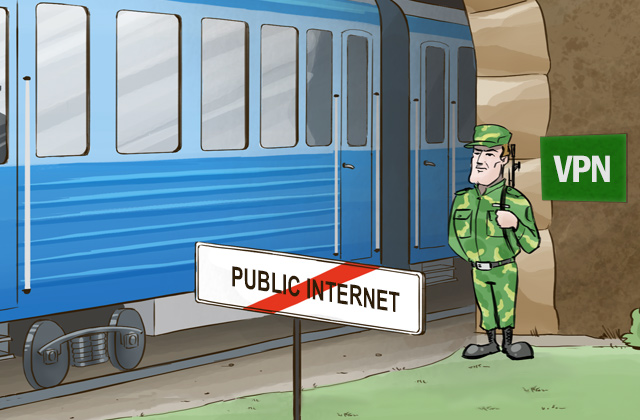
Virtual Private Networks, or VPNs for short, have become increasingly essential of late as we more often access sensitive data from remote locations — and as the threat of having our

What corporate security teams should do about the “viral” AI agent.

NFC relay attacks, pre-installed Trojans, and other nasties ruining the Android experience in 2026.

Our Android apps are no longer available on Google Play. We explain how to download, install, and update them by alternative means.

Eight digital New Year’s resolutions you absolutely need to keep.

We’ve identified a new infostealer named Stealka, which masquerades as pirated software and game mods. It targets data stored inside browsers, locally installed applications, and crypto wallets.

How automation turns legitimate tools into a channel for malware delivery.

A new wave of ClickFix attacks spreading a macOS infostealer are posting malicious user guides on the official ChatGPT website by piggybacking the chatbot’s chat-sharing feature.

The Whisper Leak attack allows its perpetrator to guess the topic of your conversation with an AI assistant — without decrypting the traffic. We explore how this is possible, and what you can do to protect your AI chats.

We examine how popular Canon printers could become a foothold for attackers within an organization’s network.

Researchers have discovered that 50% of data transmitted via satellites is unencrypted. This includes your mobile calls and texts, along with banking, military, government, and other sensitive information. How did this happen, and what can we do about it?

Kaspersky for Linux is now available to home users.

We explain what data DeepSeek collects, who it shares it with, how to configure the chatbot for maximum privacy, and how to install a local version.

The internet never forgets — and what kids post or share today can come back to hurt them, either right away or years down the line. Here’s how to shrink your child’s digital footprint without resorting to battles or bans.

Using anomalies in the behavior of users, devices, applications, and other entities to detect cyberthreats.

Why advanced attackers are interested in your home Wi-Fi access points, and how they maintain control over your devices.

This report delves into the cyberthreat landscape that has exploited Gen Z’s favorite streaming services, films, series and anime from Q2 2024 to Q1 2025, highlighting the related dangers and providing insights on how to protect yourself from these threats.

How the situation with ransomware attacks on companies has changed, and why paying a ransom has become an even worse and more useless idea in 2025.

Cybercriminals behind the Fog ransomware publish leaked data along with the IP addresses of attacked computers.