
Thieving spam: it’s no longer about just advertising
As cybercrime keeps focusing on profit, the share of plainly malicious spam, spreading out Trojans, phishing links, etc., will grow.
976 articles

As cybercrime keeps focusing on profit, the share of plainly malicious spam, spreading out Trojans, phishing links, etc., will grow.

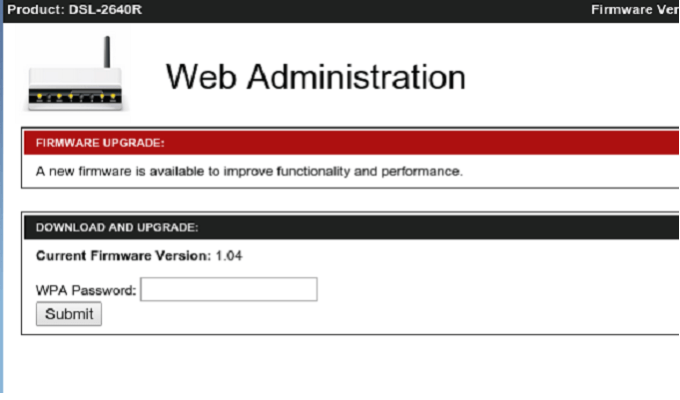
A large-scale “pharming” campaign targeting home routers took place in South America, the latest in a trend Kaspersky Lab’s experts have been monitoring for awhile. Home routers are frequently used

Fraudsters hacked Skype and tricked people from a contact list to send them about $5,000 over the course of a few days. Skype support, local banks and the police refused to do anything.

One dollar lesson is a new interactive project by Kaspersky Lab that aims to help you stay protected from online money frauds. Learn three simple lessons right now!
Today we discuss the most important news on information security from January.

Kaspersky Lab has discovered the first APT campaign launched by Arabic speakers, operating in the Middle East.

Kaspersky Lab has discovered an ultra-massive money-stealing campaign codenamed Carbanak APT with total losses summing up to $1 bn so far.

The Carbanak APT group managed to steal a total of $1 bln from dozens of banks worldwide

It’s always nice to see high marks and awards from independent testing labs. The latest roundup shows that Kaspersky Lab’s product performance is consistently great over the time.
Blackhat was finally released in theaters and its strongest aspect is its technological portrayal of hacking.

Cryptolocker is still making the rounds, even though its peak seems to have passed. Or is it just an illusion? How does it affect businesses? Read some real stories and explanations in the new blogpost at Kaspersky Business.

Gaming is enormously popular. Thus, it’s an easy target for cybercriminals looking for a never-ending source of money.

We have constructed a list of promises that you should make to yourself this year to stay safe both online and offline.

Anyone who goes online could be hacked. During Christmas time, this possibility doubles as we make a number of purchases and get so excited that we forget about security.

A new variant of the Zeus banking trojan has emerged, targeting consumer accounts at 150 banks in 15 countries.

Kaspersky Lab experts unveiled new Linux-targeting malware related to the infamous Turla APT. Such modules were known to exist before, but never met in the wild. Until now.

The RedOctober operation was hastily wrapped-up just after a Kaspersky Lab’s publication in January 2013, but it was expected to return. And it did.

Sony Pictures Entertainment fell victim to a massive hack. Attackers used destructive malware to bring SPE networks down, while stealing up to 11 TB of data, which included both trade secrets, yellow press fodder, passwords to social networks accounts, and a lot of private information.

Cybercrime is a rather lucrative business. Cybercriminals are earning a lot, or at least their effort-to-profit rate is good enough for them to keep going. But how good is it?

Online games these days are products of years of development with budgets approaching those in Hollywood, and with similar marketing support. And if we speak of massively multiuser online games

Recent news concerning “hacked webcams” or “breached baby monitors” appears to be all over the place. Let’s take a closer look at the situation.