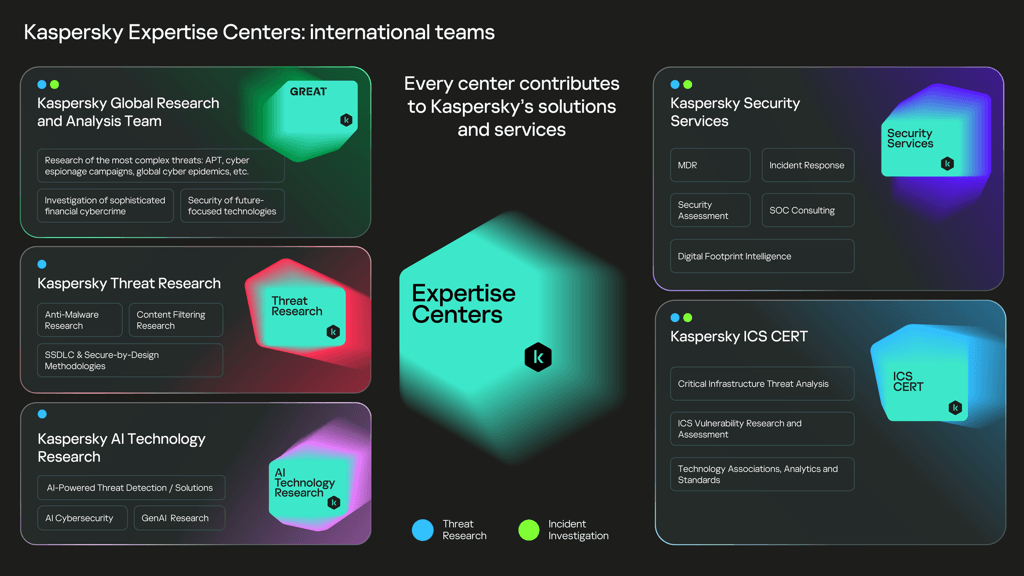
When writing about threats, vulnerabilities, high-profile investigations or technologies, we often mention our experts of various specializations. Generally speaking, Kaspersky’s experts are highly qualified employees specialized in their particular field who research new cyberthreats, invent and implement breakthrough methods to combat them, and also help our clients and to deal with the most serious of incidents. There are many fields for using their talents; most of them fall within the competence of one of our five so-called “centers of expertise”.
Kaspersky Global Research and Analysis Team (GReAT)

Our best known team in the cybersecurity industry is the Global Research and Analysis Team (GReAT). It’s a tightly knit collective of top-notch cybersecurity researchers specializing in studying APT attacks, cyber espionage campaigns, and trends in international cybercrime. Representatives of this international team are strategically located in our offices around the world to ensure immersion into regional realities and provide the company with a global perspective of the most advanced threats emerging in cyberspace. In addition to identifying sophisticated threats, GReAT experts also analyze cyber-incidents related to APT attacks, and monitor the activity of more than 200 APT groups. As a result of their work, our clients receive improved tools to combat advanced threats, as well as exclusive Kaspersky APT and Crimeware Intelligence reports, containing tactics, techniques and procedures (TTP), and indicators of compromise (IoC) useful for building reliable protection.
Kaspersky Threat Research
 Kaspersky Threat Research are the experts whose work lies at the foundation of our products’ protective mechanisms – as they study all the details of attackers’ tactics, techniques and procedures, and drive the development of new cybersecurity technologies. These experts are primarily engaged in analyzing new cyberthreats and are responsible for ensuring that our products successfully identify and block them (detection engineering). Threat Research includes (i) Anti-Malware Research (AMR), whose experts deal with software (including malware, LolBins, greyware, etc.) used by cyberattackers; and (ii) Content Filtering Research (CFR), which is responsible for analysis of threats associated with communication via the internet (such as phishing schemes and spam mailings).
Kaspersky Threat Research are the experts whose work lies at the foundation of our products’ protective mechanisms – as they study all the details of attackers’ tactics, techniques and procedures, and drive the development of new cybersecurity technologies. These experts are primarily engaged in analyzing new cyberthreats and are responsible for ensuring that our products successfully identify and block them (detection engineering). Threat Research includes (i) Anti-Malware Research (AMR), whose experts deal with software (including malware, LolBins, greyware, etc.) used by cyberattackers; and (ii) Content Filtering Research (CFR), which is responsible for analysis of threats associated with communication via the internet (such as phishing schemes and spam mailings).
Attackers work hard to circumvent protective technologies, which is why we pay special attention to the security of our own products. The Threat Research expertise center also includes the Software Security team, which mitigates the risks of vulnerabilities in Kaspersky solutions. In particular, they’re responsible for the secure software development life cycle (SSDLC) process, bug bounty program, and for ensuring that our secure-by-design solutions (our own operating system – KasperskyOS – and products based on it) really are truly secure.
Kaspersky AI technology research

We all know how hyped AI technology is today, and how popular the topics of AI in cybersecurity and Secure AI are on the market. Our team provides a range of options in our solutions from ML (machine learning) and AI-enhanced threat discovery and triage alerts to prototype GenAI-driven Threat Intelligence.
For over two decades, our products and services have incorporated aspects of artificial intelligence to enhance security, privacy, and business protection. Kaspersky AI Technology Research applies data science and machine learning to detect various cyberthreats, including malware, phishing and spam on a large scale – contributing to detection of more than 400,000 malicious objects daily.
To detect more complex, targeted attacks, you have to juggle massive numbers of events and alerts coming from different levels of the IT infrastructure. Proper aggregation and prioritization of these alerts are crucial. Without AI-powered automation, it’s easy for a security-operations-center analyst to get overwhelmed and overlook critical alerts amid the multitude of security notifications. Better alert triage and prioritization – especially with machine learning – is top priority for our detection and response solutions (EDR, SIEM, XDR and MDR services).
Generative AI (GenAI) technologies open up new possibilities in cybersecurity. Kaspersky researchers are working on applying GenAI to various tasks in products ranging from XDR to Threat Intelligence to help cybersecurity analysts cope with the daily deluge of information, automate routine tasks, and get faster insights, amplifying their analytical capabilities and enabling them to focus more on investigating complex cases and researching complex threats.
We also use artificial intelligence to protect complex industrial systems. Our Kaspersky Machine Learning for Anomaly Detection (MLAD) solution enables our products to detect anomalies in industrial environments – helping identify early signs of potential compromise.
As AI systems are inherently complex, Kaspersky AI Technology Research also works on identifying potential risks and vulnerabilities in AI systems – from adversarial attacks to new GenAI attack vectors.
Kaspersky Security Services

Kaspersky Security Services experts provide complimentary services for information security departments at the largest enterprises worldwide. Its service portfolio is built around the main task of security departments – addressing incidents and their impact: detection, response, exercises, and process-wise operations excellence.
Whenever organizations face a security crisis, our team is dedicated to building a complete picture of the identified attack, and sharing recommendations for response and impact minimization. Our Global Emergency Response Team is located on all continents and is involved in hundreds of incident responses yearly.
For organizations that require continuous incident detection, there’s our Managed Detection and Response service. The Kaspersky SOC experts behind this service monitor suspicious activity in the customer’s infrastructure, and help to timely respond to incidents and minimize impact. Our MDR operates worldwide and is top-rated by customers.
Developing and measuring security maturity, preparing for real-world attacks, discovering vulnerabilities and more are the goals of our various Security Assessment services. Among other things, they can: evaluate SOC readiness to protect critical business functions with attack simulations (red teams); assess attackers’ chances of penetrating your network and gaining access to critical business assets with penetration testing service; and identify critical vulnerabilities by deeply analyzing complex software solutions with our application security service.
If a company needs to build its own SOC, or assess the maturity level or development capabilities of an existing one, our SOC Consulting experts share their vast experience in security operations gained while working with different industries, organizations of different sizes and with different budgets.
Before, during and after an attack, cybercriminals leave traces of their activities outside the attacked organization. Our Digital Footprint Intelligence experts identify suspicious activities on cybercriminal marketplaces, forums, instant messengers and other sources to timely notify an organization about compromised credentials, or someone selling access to their internal corporate network or data from their internal databases, and so on.
Kaspersky ICS CERT
 Our industrial systems cybersecurity research center (Kaspersky ICS CERT) is a global project whose main goal is assisting manufacturers, owners and operators, and research teams in ensuring the cybersecurity of industrial automation systems and other M2M (machine-to-machine) solutions (building automation systems, transportation, medical systems and so on).
Our industrial systems cybersecurity research center (Kaspersky ICS CERT) is a global project whose main goal is assisting manufacturers, owners and operators, and research teams in ensuring the cybersecurity of industrial automation systems and other M2M (machine-to-machine) solutions (building automation systems, transportation, medical systems and so on).
Kaspersky ICS CERT experts constantly analyze various products and technologies, evaluate their security level, report information about vulnerabilities to their manufacturers, and inform users of vulnerable solutions about the corresponding risks. In addition to searching for zero-day vulnerabilities, our CERT team analyzes publicly available information on vulnerabilities in ICS products, finds and eliminates multiple inaccuracies in it, and adds its own recommendations for reducing the risks to end-users.
Also, Kaspersky ICS CERT specialists identify and study attacks on organizations in the industrial sector, provide assistance in incident response and digital forensics, and share analytical information about attacks as well as indicators-of-compromise data feeds based on the results of their research.
In addition, our experts contribute to the engineering of sectoral and governmental regulations in the field of industrial cybersecurity, transportation, and the industrial Internet of Things; develop and conduct training for information-security specialists and employees of industrial organizations; and provide various consulting services.
Kaspersky spends huge amounts of resources – including a significant portion of its profits – on developing its expertise. Our experts research cyberthreats relevant to even the most remote corners of the globe, and understand the specific needs of all customers – no matter where they are. Thanks to the contribution of the above-listed centers of expertise, our services and solutions are constantly being improved and so always remain ready to counter the most non-trivial of attacks and identify the latest cyberthreats.
 expertise
expertise

 Tips
Tips