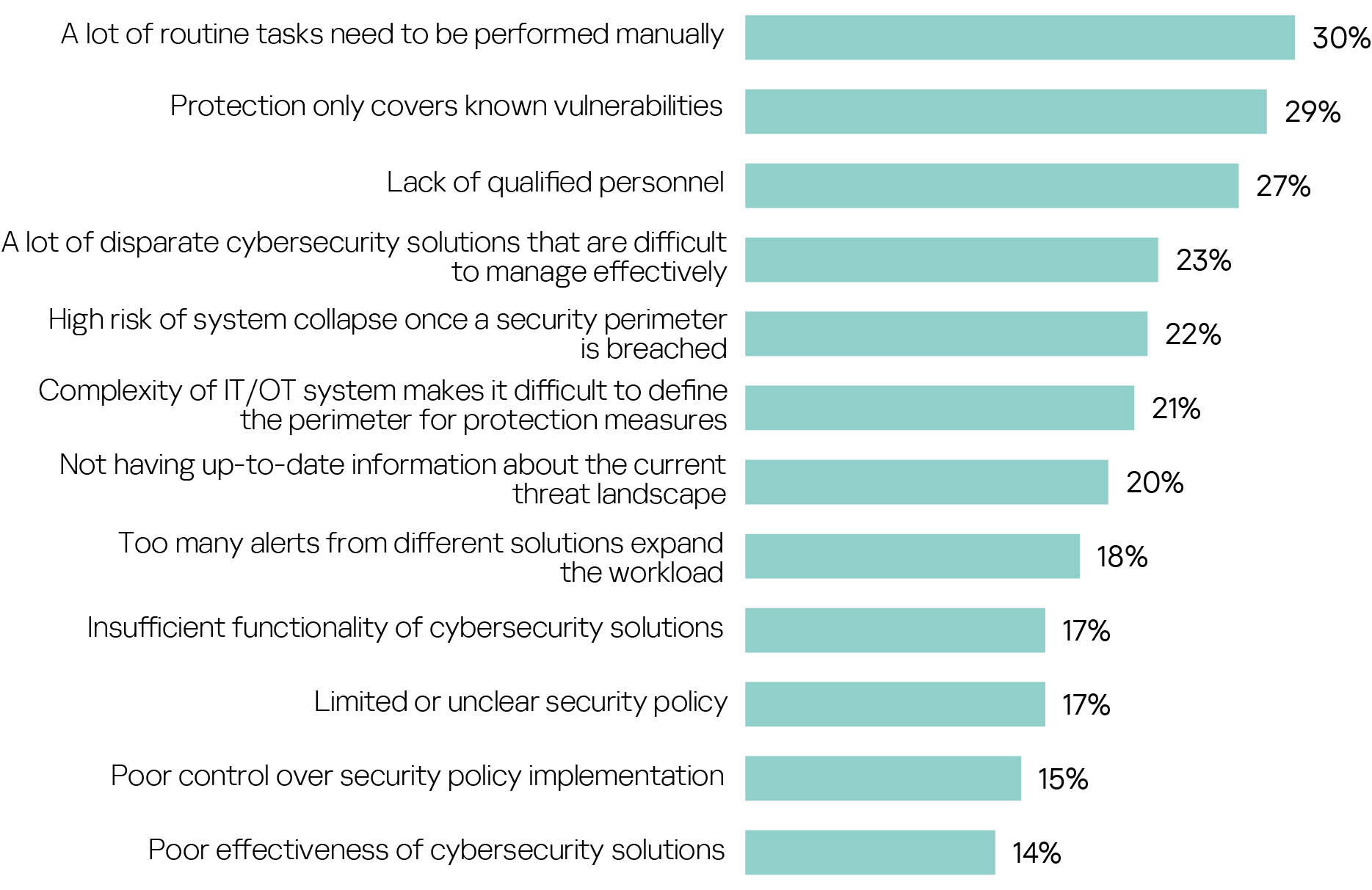As threats to the cybersecurity of companies worldwide become more sophisticated, the ongoing race between cybercriminals and cybersecurity vendors is heating up. Cybercriminals are actively exploiting new opportunities to increase the volume and effectiveness of their attacks using AI, while cybersecurity vendors are rapidly upgrading existing solutions to better protect their clients. Alongside these enhanced security systems, new approaches like Cyber Immunity are being developed to further increase the innate resilience of networks and systems, including against AI-supported assaults.
Broadening from a primarily defensive to a more proactive cybersecurity approach can make a significant difference in the ongoing battle over access control—by defending against unknown vulnerabilities and creating systems that are not invulnerable but resilient and resistant to attacks, thereby making hacking ineffective. In a new global study, Kaspersky investigated the strategies and practices of cybersecurity teams in larger companies around the world to understand how they currently manage their cybersecurity and how they plan to prepare for an increasingly unpredictable future.
Methodology and audiences
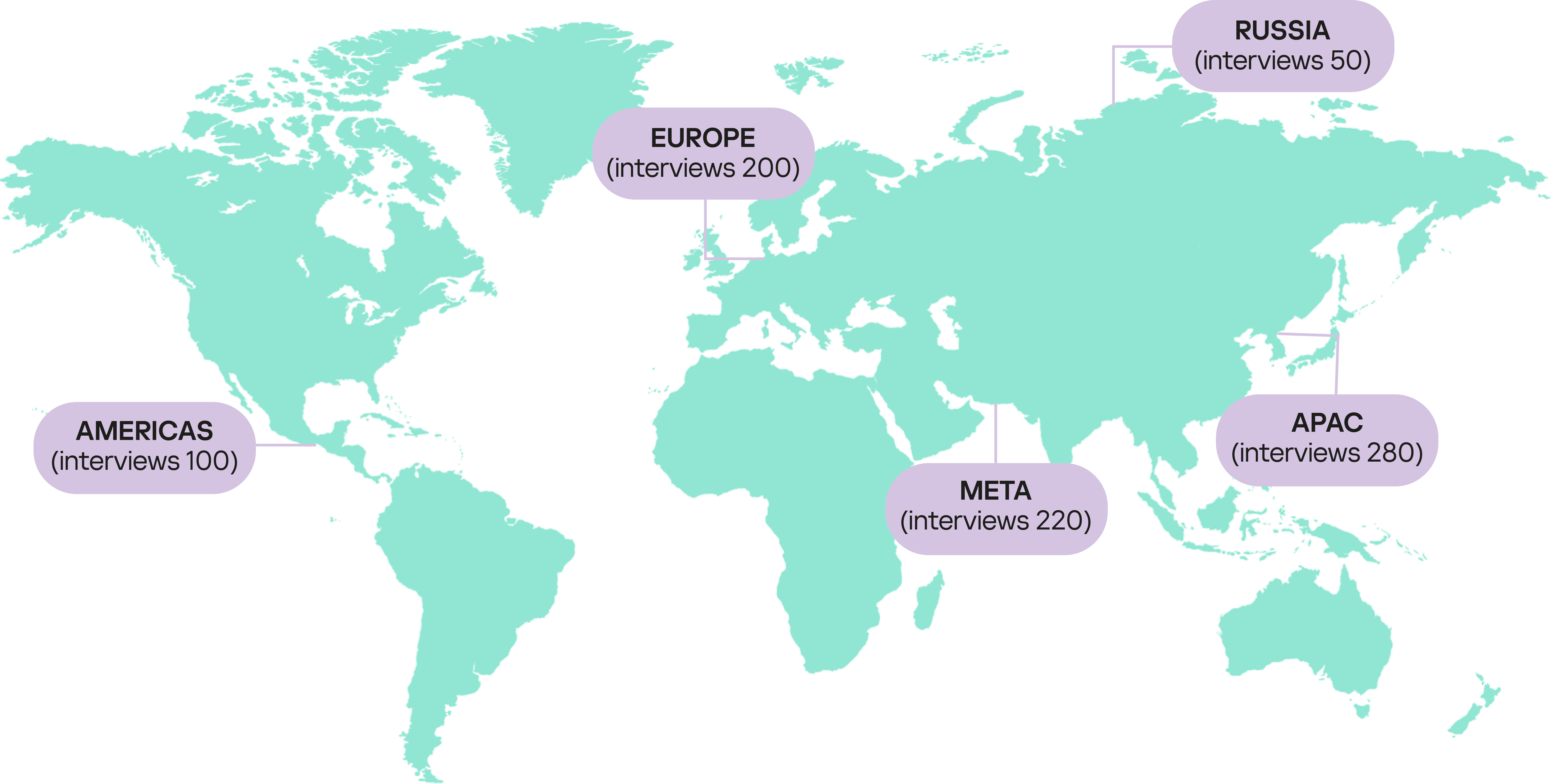
Kaspersky commissioned Arlington Research to carry out 850 online interviews with IT professionals at different levels of authority, who spend a significant amount of time on cybersecurity. They work for companies in a wide range of sectors and have from 500 to over 10,000 employees in Europe (France, Germany, the UK, Spain), the Americas (Brazil, Mexico), in the Asia-Pacific (Singapore, China, Japan, India, Indonesia, Malaysia, South Korea) and the Middle East, Turkey & Africa region (Saudi Arabia, South Africa, Turkey, Egypt, United Arab Emirates) and Russia.
The current state of cybersecurity
Level of satisfaction with current cybersecurity systems
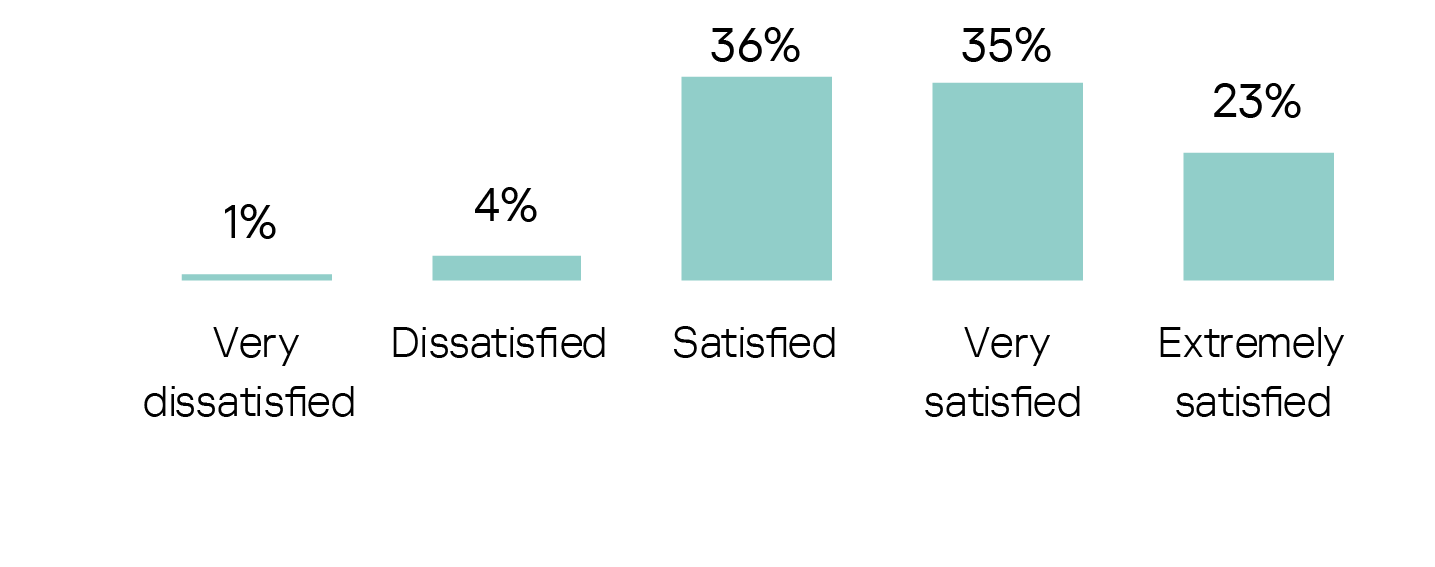
Satisfaction with their current cybersecurity set-up is generally high amongst those responsible for keeping their companies’ data and systems safe from attack: as many as 58% are very or extremely satisfied with the current level of protection.
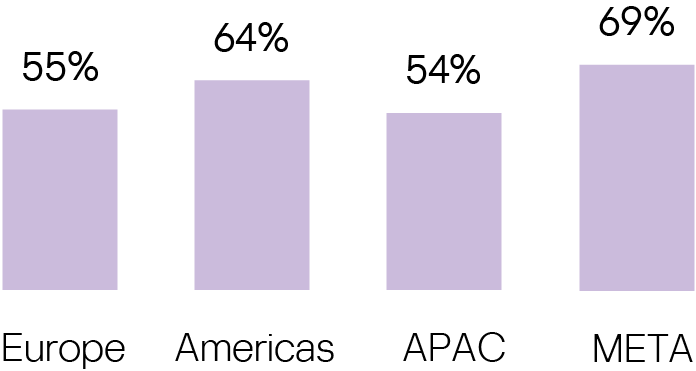
Satisfaction amongst cybersecurity professionals with their current set-up is particularly high in META (69%), followed by those in the Americas (64%). In APAC, it is significantly lower with only 54%.
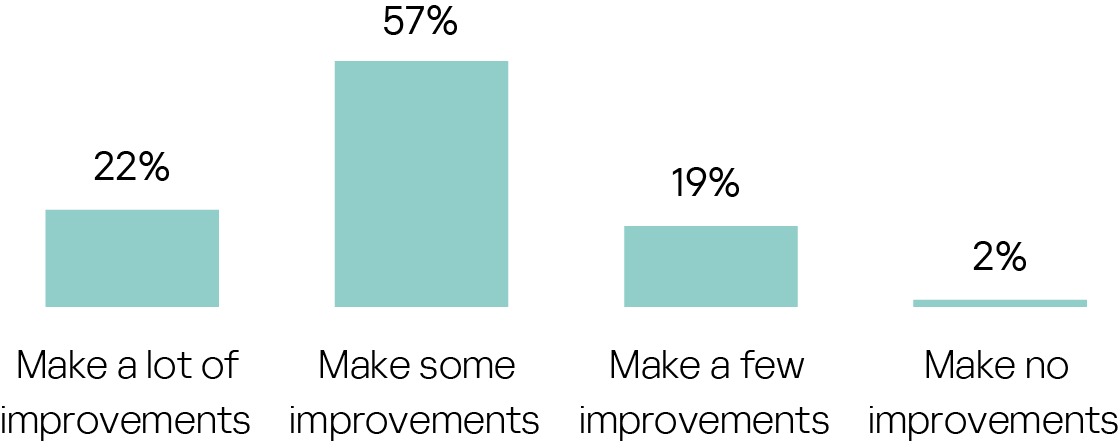
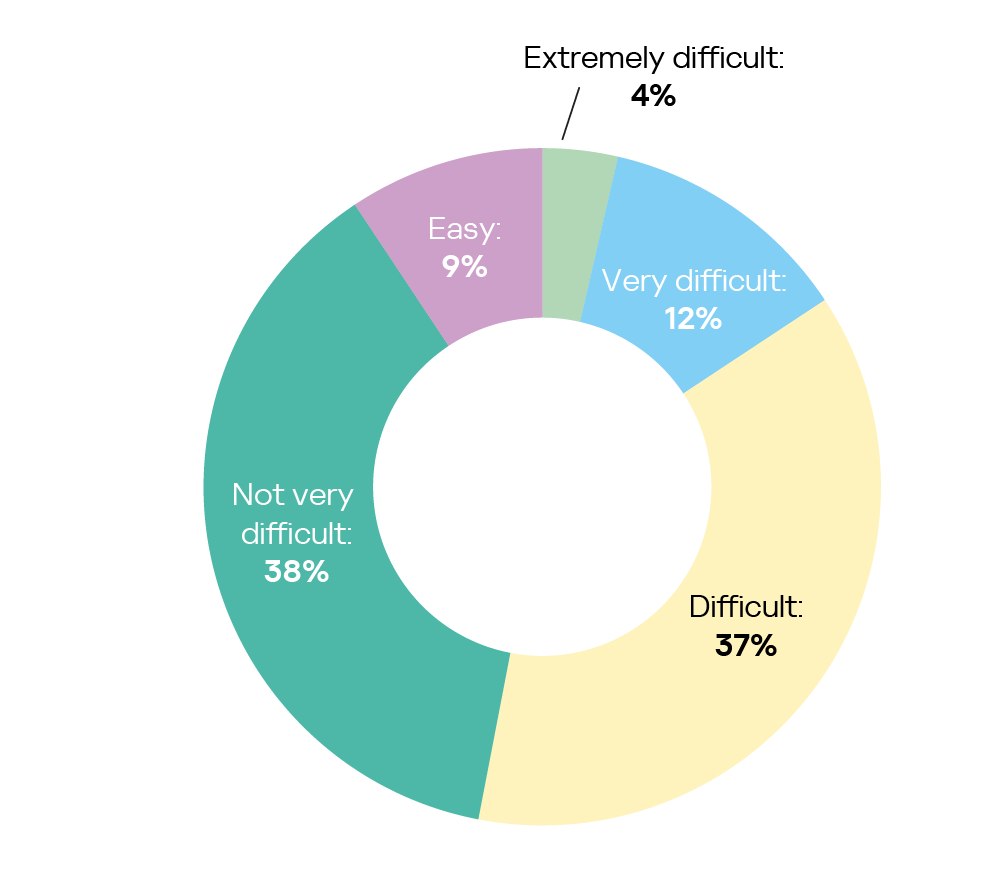
Despite this largely positive picture, there is widespread conviction that improvements are needed to ensure the security of data, networks and systems going forward: more than 20% believe that a lot of positive change is needed, and as many as 78% regard at least some improvements as a necessity.
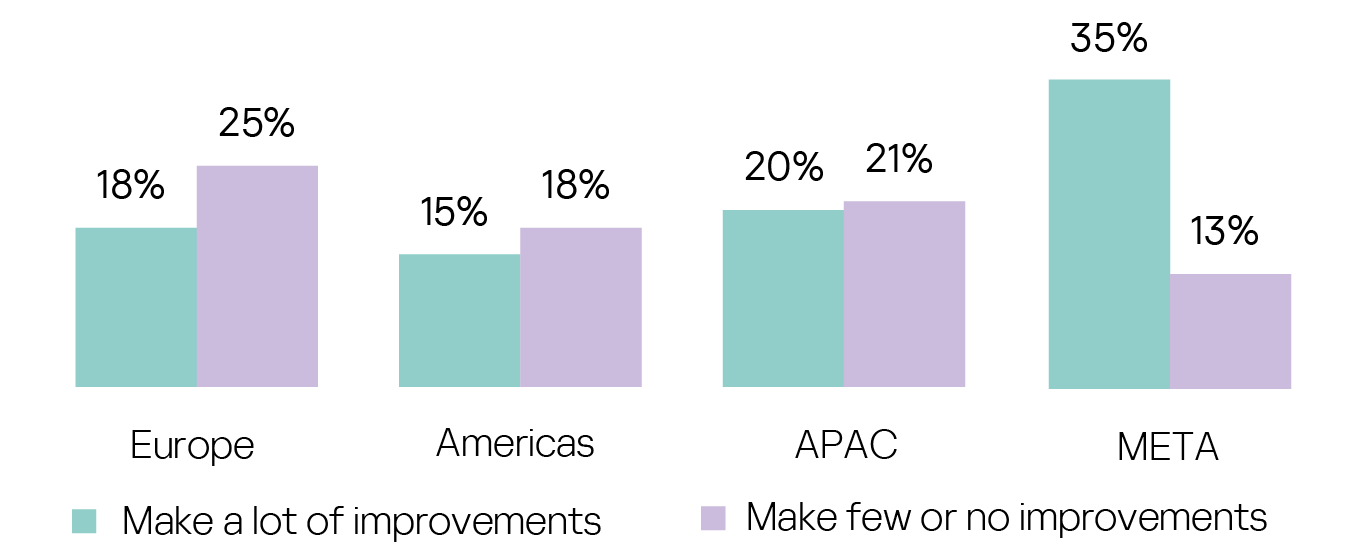
The greatest perceived need for a lot of improvements is shown in META (35%), and the greatest confidence that few or no improvements are required is evident in Europe (25%):
The weakest parts of current cybersecurity systems are the need to perform a large number of routine tasks manually taking up a lot of valuable time (named by 30%), protection limited to known vulnerabilities without proactive identification of new system weaknesses (29%), the lack of qualified personnel (27%) and the difficult management of a lot of disparate cybersecurity solutions (23%).
Disparate cybersecurity solutions are a headache for companies
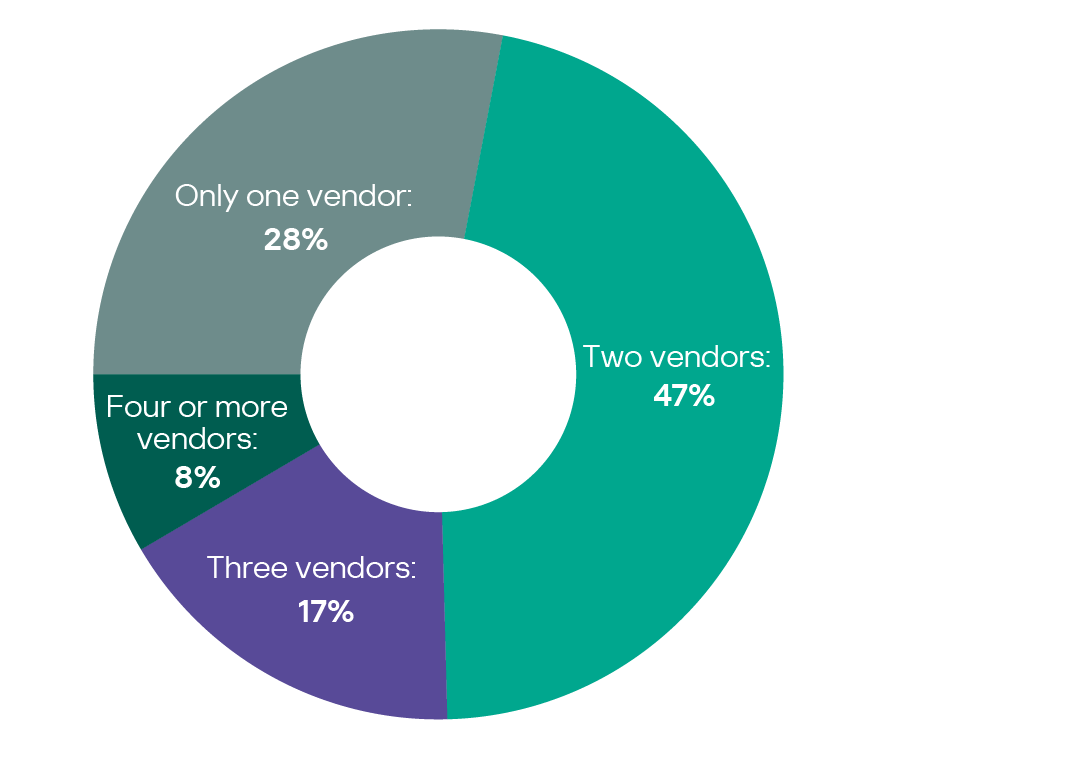
According to the respondents, just over a quarter (28%) use only one cybersecurity vendor, most use two (47%), three vendors are used by 17%, and 8% even use four or more.
For those who have more than one vendor’s solutions in use, managing disparity between them can be a challenge: around half find it difficult (53% globally).
The issues arising in this context range from managing an overly complex, disparate security tech stack (43%), budget overruns (42%) and the inability to consolidate to automate, as different solutions lead different processes (41%). A lack of systems transparency, too many alerts and insufficient expertise in managing disparate security building blocks coming from different vendors are also issues for more than a third overall.
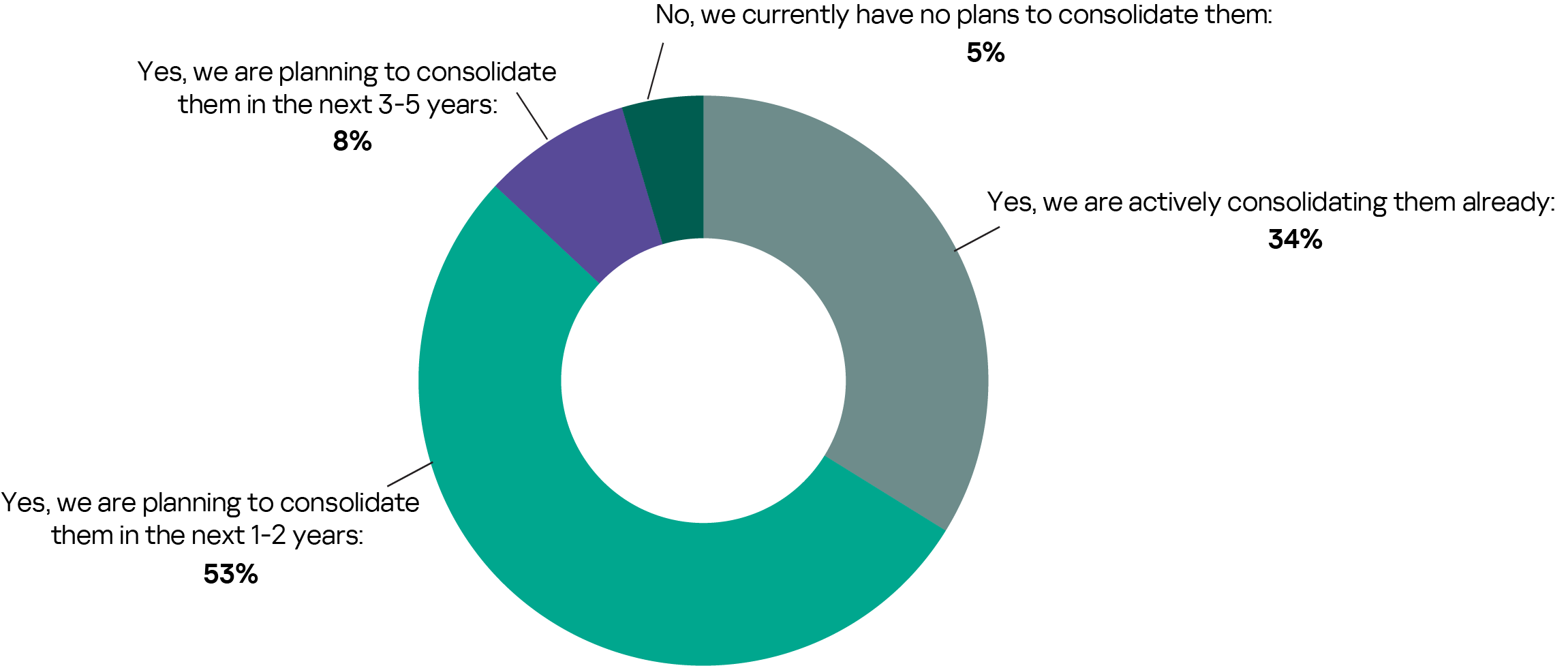
Most companies (87%) using disparate cybersecurity solutions are actively consolidating them right now or will do so in the near future to address these issues.
Threat Intelligence: the foundation of successful protection
Planning and implementing an effective cybersecurity strategy increasingly require in-depth threat intelligence to enable security professionals to choose the right tools and solutions to optimize their cyber protection. Looking at what is available in the market generally, the vast majority of respondents is satisfied with the threat intelligence information available to them (86% say satisfied or very satisfied).
The main sources of threat intelligence used by companies are TI vendors (42%). Nearly a third (29%) share threat intelligence with other companies, swapping information to get a complete picture of the current threat status. More than a quarter (27%) collect threat intelligence from open sources. Only 2% do not use any threat intelligence.
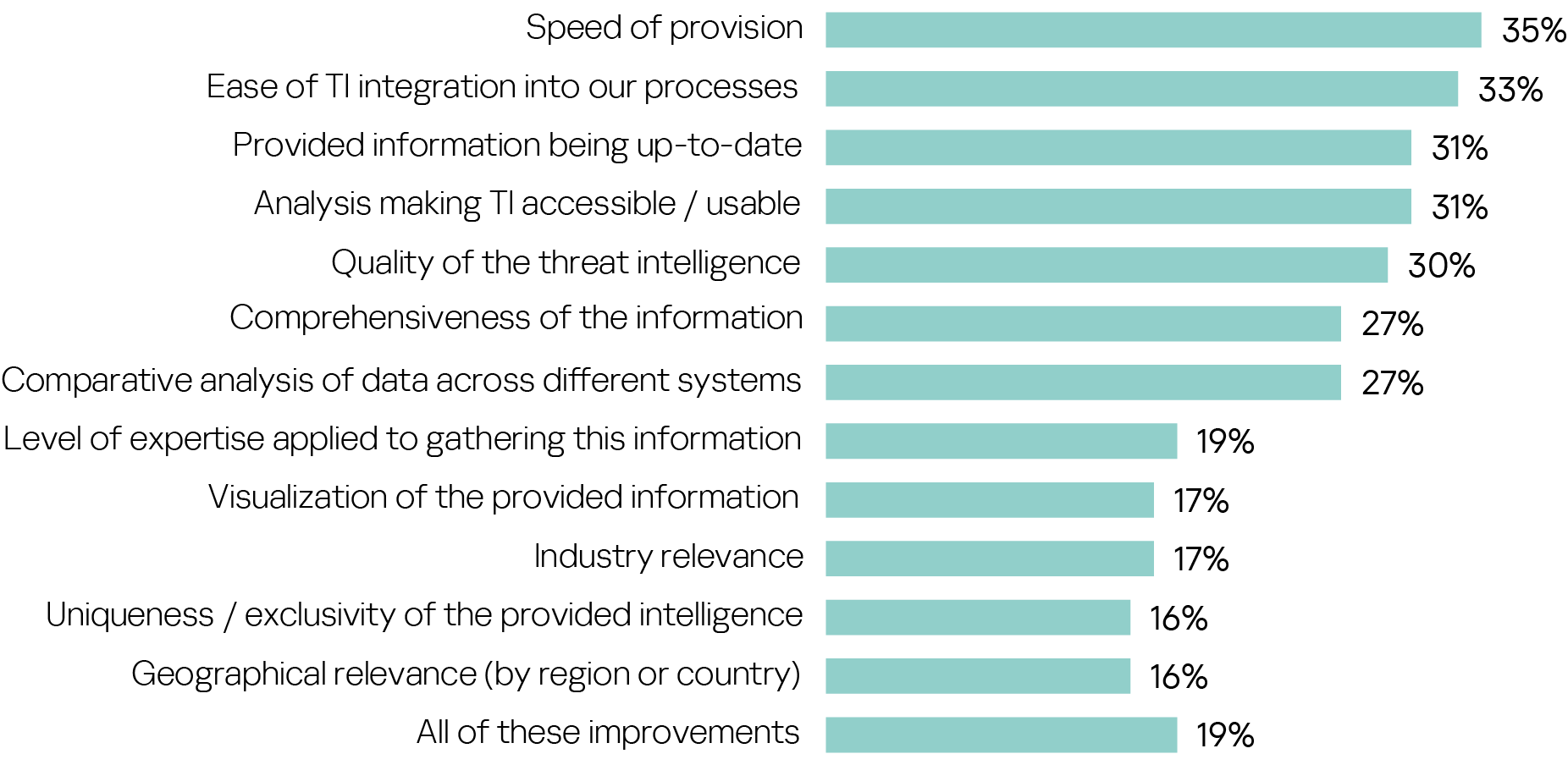
For those who expressed dissatisfaction with the threat intelligence information they are sourcing for their organizations, the main improvements they want to see relate to the speed of provision (35%), the ease of integrating the intelligence into existing processes (33%), the extent to which the information is up-to-date, and analysis helping them to make the threat intelligence usable within their company’s protection set-up (both 31%).
The most important change cybersecurity professionals want to see when asked to choose only one thing they would improve: making threat intelligence easier to integrate into their processes (20%).
Cyber Immunity: creating systems with in-built protection
Cybersecurity vendors vs cyber criminals: an ongoing technology race
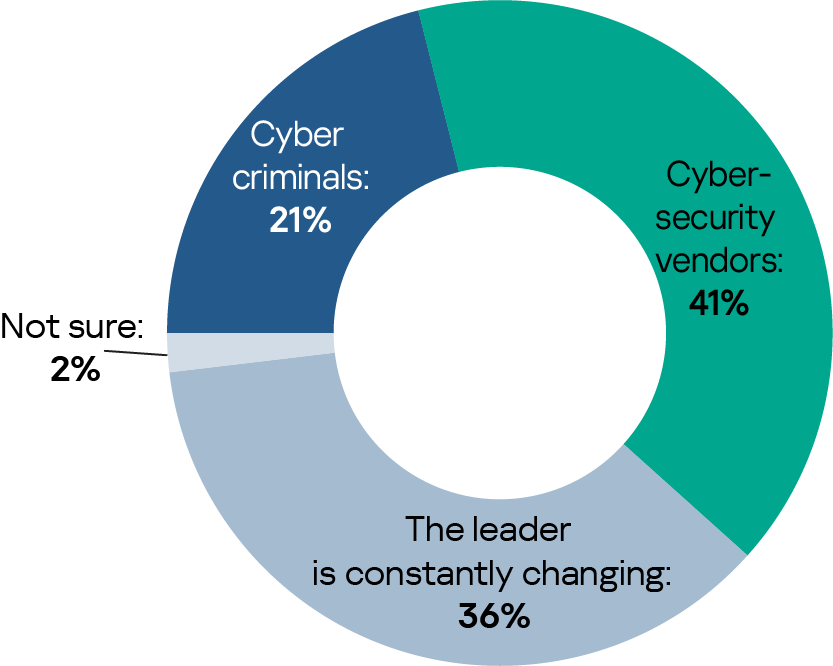
Security breaches are daily occurrences in the life of cybersecurity professionals, and the competition between those developing new ways to protect data and systems (cybersecurity vendors) and those who seek to find ways to hack and damage them is getting fiercer. Asked who is in the lead in this ongoing race, more companies believe that cybersecurity vendors are ahead of cybercriminals (41%), only one in five (21%) sees cybercriminals in front, and just over a third (36%) sees the leader changing all the time.
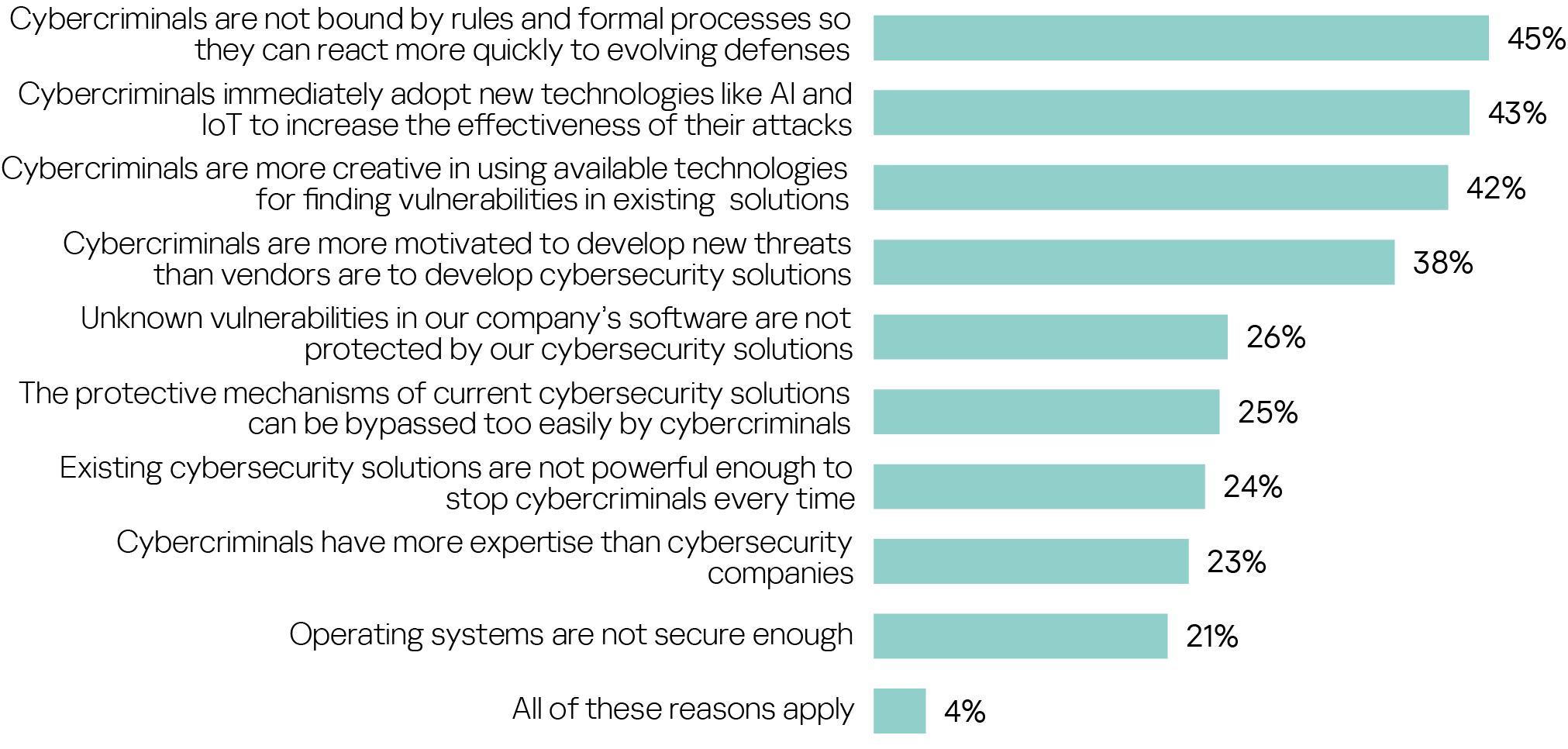
The reasons why cybercriminals can achieve a leading position in this race focus particularly on the lack of control through regulation, creativity, greater expertise and motivation. But systemic weaknesses on the side of those under attack also play an important role:
An alternative approach for enabling cybersecurity
How to build more effective cybersecurity systems will rely on strategies that reflect exactly these aspects: resilience, expertise and flexibility. Asked about systems designed to withstand cyber-attacks successfully without the need for additional cybersecurity solutions, only a minority (17%) believed that this exists already. 37% said this was definitely possible and 39% said maybe, highlighting the need for more education across the cybersecurity profession.
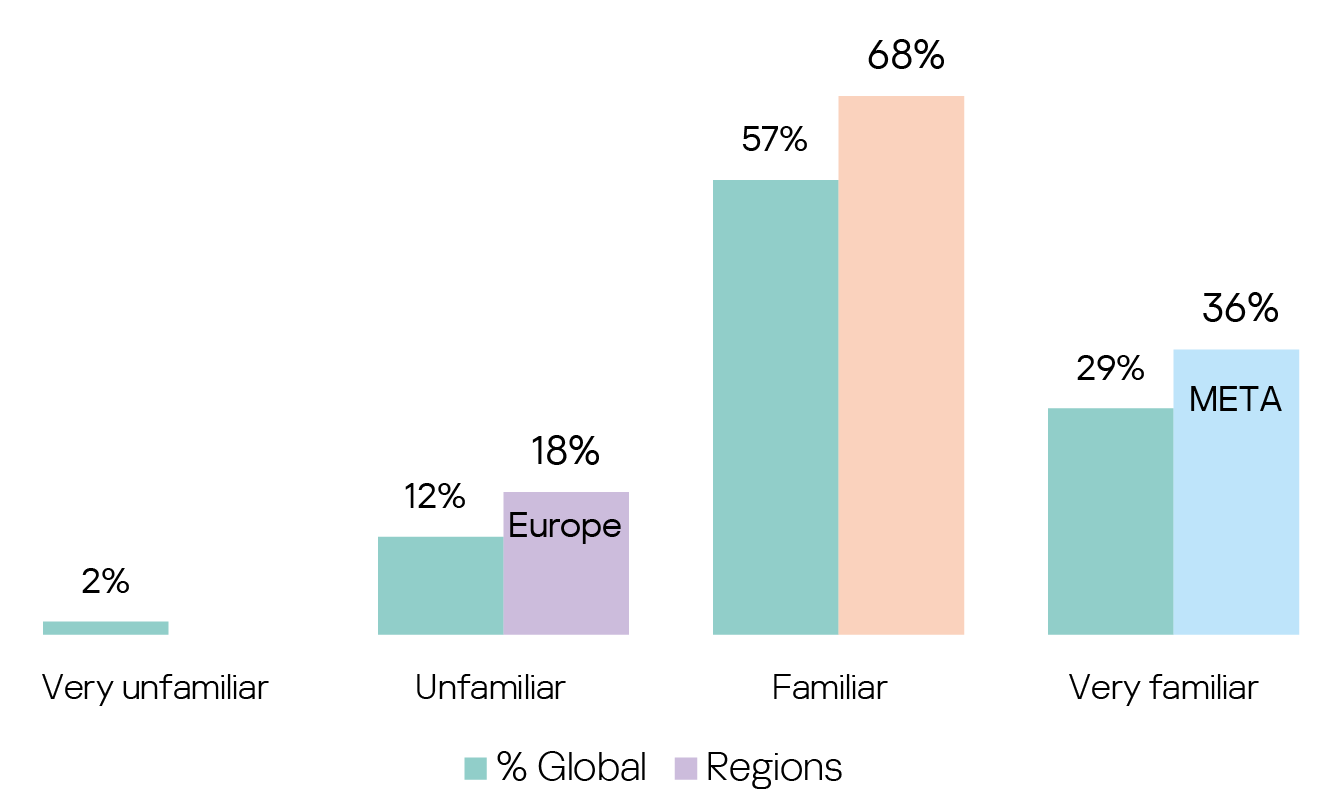
In contrast, as many as 86% claim familiarity with a secure-by-design approach, again with some interesting regional differences: European cybersecurity professionals are least familiar with the concept, whilst META has the greatest number of those “very familiar” with this idea.
Confidence in the effectiveness of designing systems in this way could be stronger: whilst 38% do believe that it would be effective to a great extent, 54% sit on the fence and only say “to some extent”. The remainder is unconvinced or unsure (9%).
Moving from being on the defensive to a more proactive approach to cybersecurity can make the difference in the battle over access control, disarming attacks before they can become effective. New approaches like Cyber Immunity offer great opportunities to combat AI-supported assaults and potentially growing risks for networks and systems.
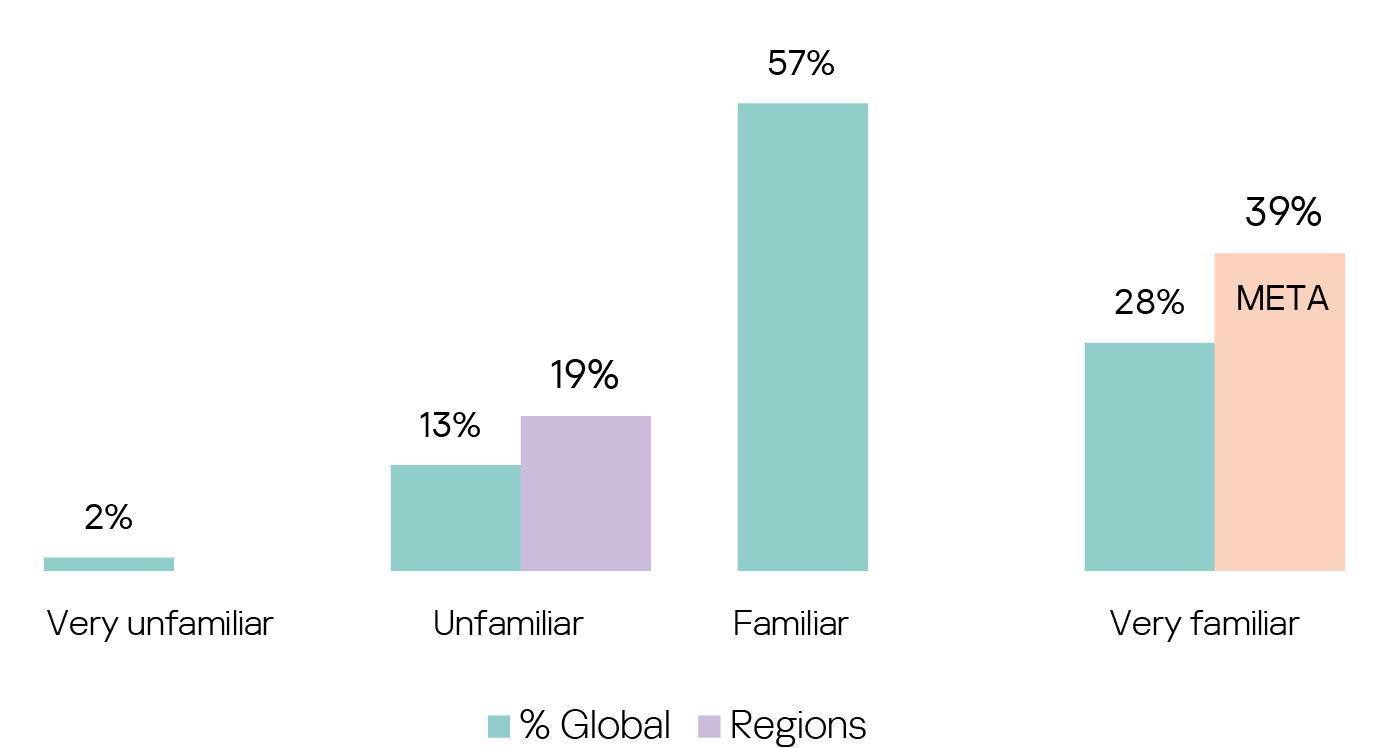
Familiarity with this concept is equally high (85% very familiar or familiar), with similar variations across the regions: those in META again have the highest contingent of “very familiar” cybersecurity professionals (39%), and those in Europe are least familiar with it (19% are unfamiliar).
However, there are quite different ideas of what Cyber Immunity actually means: a type of system design, policies and tech in combination or highly qualified high-speed responders, making claimed “familiarity” more a matter of belief than actual experience:
An interesting aspect is the connection with biology made by 39%, drawing on knowledge of the natural world to increase system resilience. This is particularly popular in APAC, where as many as 46% link this idea with Cyber Immunity.
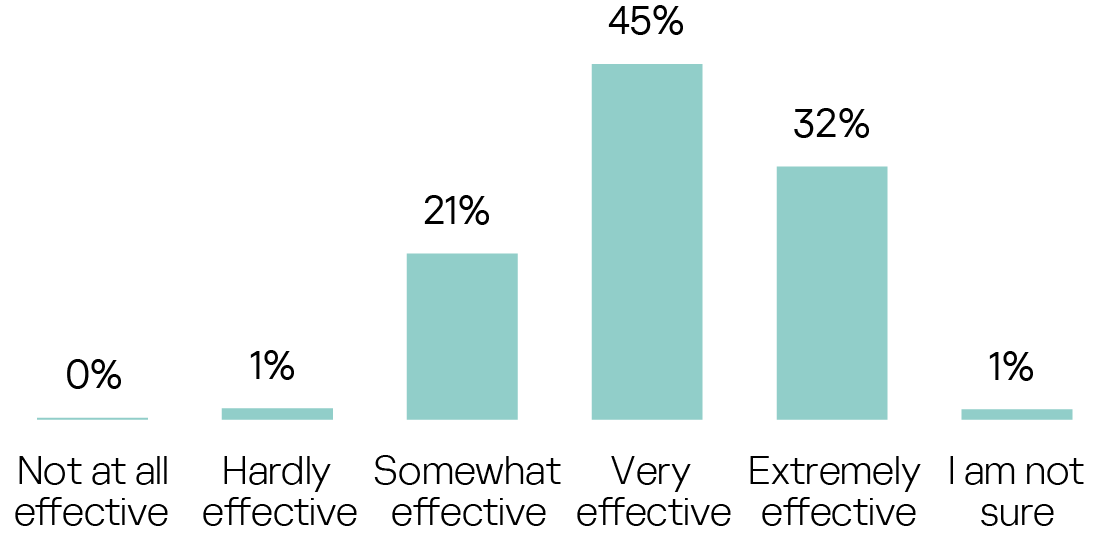
Yet whatever it is believed to be, Cyber Immunity has made a very positive impression on the professional cybersecurity community. 77% of those who see secure-by-design as an essential component believe it to be very or extremely effective in fighting cybercrime.
Looking to the future, almost all of those who see secure-by-design as an essential part of Cyber Immunity and believe it to be effective in at least some way (98%, saying somewhat to extremely effective) expect Cyber Immunity to change the cybersecurity landscape for the better, by reducing the frequency of cyber-attacks (32%), their negative impact (30%), or both (38%).
Dmitry Lukiyan, Head of KasperskyOS Business Unit:
This research confirms what we’re already seeing across the market: adding traditional security tools on top of existing infrastructure is no longer enough. More and more organizations are seeking built-in protection: systems that are secure-by-design. That’s exactly what we at Kaspersky implement through our Cyber Immunity approach. It doesn’t replace traditional cybersecurity – it strengthens the system itself on the architectural level. This helps our clients reduce risk, lower total cost of ownership, and build digital infrastructure that’s ready for the future. For us and our partners, that’s not just a technical benefit — it’s a long-term competitive advantage.
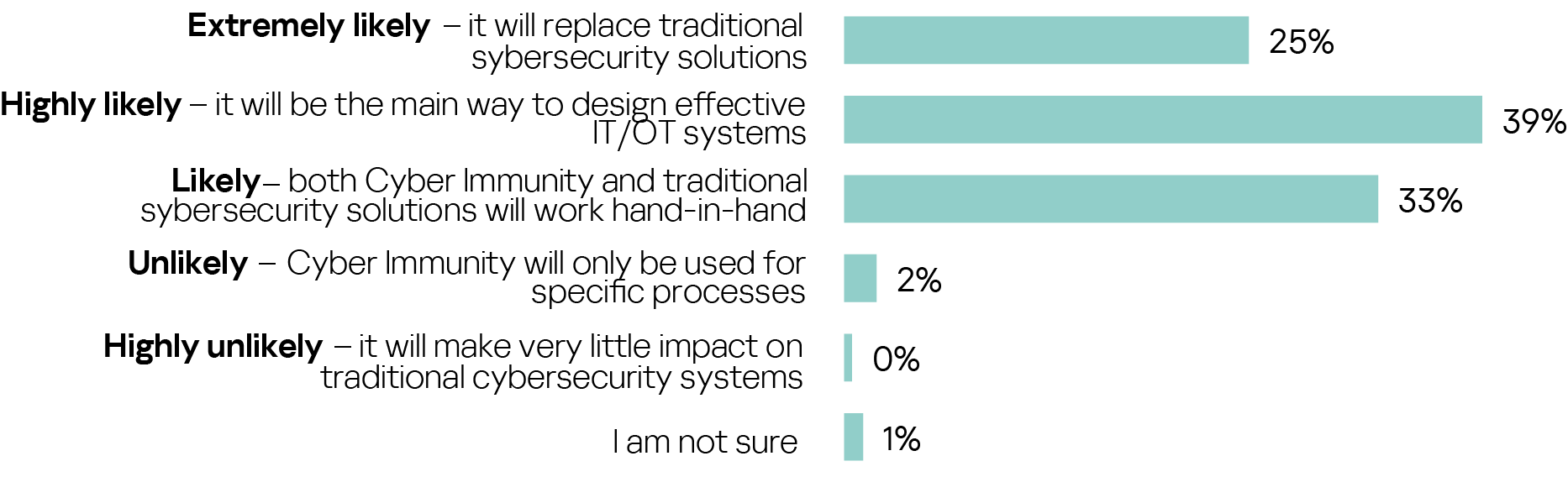
Expectations of its integration with established protection approaches vary, but those linking secure-by-design with Cyber Immunity were mostly confident that Cyber Immunity as an approach will take a central role in transforming and replacing traditional cybersecurity design strategies, clearly pointing to this concept as an important part of future cybersecurity strategy globally.
Conclusion
The threat landscape is changing rapidly, with no decrease in criminal attempts to gain unauthorized access to data and systems. Finding new ways to defend against such attacks and looking beyond mere protection—specifically, how to build systems that do not require additional security measures after deployment—is a high priority for cybersecurity vendors, software developers, and companies alike. This is especially true in the face of unknown vulnerabilities being discovered and exploited more effectively than ever before, often through the malicious use of AI and increasingly powerful processors.
Alongside enhancing traditional cybersecurity solutions, vendors are developing innovative approaches: shifting from protecting inherently vulnerable software with applied security measures toward creating secure-by-design systems with innate resilience. These systems are capable of safeguarding their core assets even when compromised, often with minimal or no additional cybersecurity spending.
Looking ahead, the concept of Cyber Immunity could fundamentally change how IT and OT systems are designed from the ground up. It would also raise the bar for cybercriminals by making breaches significantly more difficult through innate resilience. The increased effort required to penetrate secure-by-design systems will make attacks less attractive for cybercriminals, as it would demand more time and resources—reducing the likelihood of a profitable payoff.
On the way towards this fundamental shift, existing systems will increasingly require support through high-quality threat intelligence, up-to-date detection technologies and comprehensive visibility. Maximizing the protection capabilities of existing cybersecurity set-ups requires systems transparency above all – without constant and reliable feedback from all assets, breaches will remain undetected until it is too late to prevent them from causing damage and disruption. Delivering 360° monitoring with telemetry from all systems assets will support instant threat detection and response, and the elimination of vulnerabilities as soon as they arise.
Effective threat intelligence is a vital tool to guide the constant adaptation of these detection and feedback processes. This needs to be up-to-date, tailored and usable to inform the work of cybersecurity professionals, so they can apply their extensive expertise to monitoring the threat landscape, adapting and upgrading their tools for defending their companies’ systems and networks.
List of recommendations
- To enable comprehensive protection of all your assets, use centralized and automated solutions such as Kaspersky Next XDR Expert. By aggregating and correlating data from multiple sources in one place and using machine-learning technologies, this solution provides effective threat detection and fast automated response. Out-of-the-box integrations, automation features and case management help make infrastructure complexity much less of an issue.
- Provide security professionals with an in-depth visibility into cyberthreats targeting your organization. Kaspersky Threat Intelligence will provide your team with rich and meaningful context across the entire incident management cycle and helps identify cyber risks in a timely manner.
- Invest in additional cybersecurity courses for your staff to keep them up to date with the latest knowledge. With practically-oriented Kaspersky Expert training, Security professionals can advance their hard skills and defend their companies against sophisticated attacks, while Kaspersky Security Awareness can ensure IT professionals and other employees are aware of the most common cyber threats, malicious techniques and protection ways.
- As an alternative to traditional cybersecurity, develop secure-by-design solutions and protect them at the code and architecture levels. Based on KasperskyOS, a Kaspersky’s operating system, your products can be inherently protected and can perform their critical functions even in an aggressive environment with no additional cybersecurity solutions.