Introduction
Reputation is the new currency of the digital age. Like it or not, it plays an important role in both our professional and personal lives. In fact, the dystopian fiction TV series Black Mirror has offered a glimpse into what a future stoked by a modern obsession with quantifying reputation could look like in the episode “Nosedive”, where people rate each other based on the interactions they have, which in turn impacts their socio-economic status.
While such a reality remains quite a distant future, for now, most of our current concerns when it comes to managing our digital reputation often revolve around issues of data privacy or our consumption habits when it comes to social and online media. In an age where data breaches are becoming increasingly commonplace, these issues may no longer sound like headline grabbing fireworks, but they bear significant implications on how seriously we are taken online, as well as affect our ability to protect ourselves in a period where the use of technology is expected to grow even more.
“The exponential growth of the Internet has played a key role in the way human beings socialise and define their identities in relation to each other. As a result, an argument can be made that reputation is now a resource more valuable than gold or diamonds in today’s digital age. We’re now at a historical crossroads where an individual’s or a business’ digital reputation also has the power to reshape relationships in an offline environment. Through this study, we hope to better understand where the divergences are, and hopefully provide some pointers to strengthen an individual’s digital reputation to minimise the gap,” says Chris Connell, Managing Director for Asia Pacific at Kaspersky.
As you continue to review your real-world experiences on online platforms like Lazada and Foodpanda, Kaspersky has taken some time to identify what it means to build a virtual reputation and stay secure online, especially on social media. This report explores some of the common attitudes people in the Asia Pacific (APAC) region hold towards privacy, while shedding light on areas which have become key topical discussions in today’s emotionally hyper-charged environment such as how do we share information online and the manner it affects our digital reputation.
The report also includes insights and tips from Kaspersky’s cybersecurity experts, to equip people and businesses with the right tools and information to build and bullet-proof their online identities. Kaspersky’s main aim is to help people reap all the benefits of being a participant in the digital reputation economy, without being held hostage to some of the undesirable side-effects it may bring.
Key Findings
- 39% of respondents spend an additional 1-2 hours per day on social media after the pandemic
- 58% of respondents said that they were equally concerned about their privacy both online and offline
- 32% of those surveyed reported owning an anonymous social media account
- 54% of respondents said that they will verify news sources before sharing it on social media
- 49% of respondents surveyed will check the social media accounts of brands and businesses before deciding whether to use their products or solutions
- 50% of all respondents said that the online reputation of a company matters
- Deepfakes, biometrics and smart technology are the upcoming threats to our digital reputation
Methodology
The Kaspersky “Making sense of our place in the digital reputation economy” report studies attitudes of individuals in Asia Pacific towards building a secure and reputable online identity on social media. It also looks into how tainted digital reputation of businesses are perceived.
The study was conducted by research agency YouGov in Australia, India, Malaysia, Philippines, Singapore, and Vietnam last November 2020. A total of 1,240 respondents were surveyed across the stated countries.
The respondents ranged from 18-65 years of age, all of which are working professionals who are active on social media (spending at least 1 hour a day on social media).
Through this paper, when the behaviour of the population of a market is generalised, it is in reference to the group of respondents sampled above.
Gauging our reliance on social media
In the wake of the COVID-19 pandemic, individuals have become more reliant on social media with their devices to entertain themselves as well as get news updates. With the ‘new normal’ in full swing, this section will investigate how our consumption habits on social media have changed, and the mediums we use to access social media.
How much time do we spend on social media daily?
Across the markets surveyed, 33% of respondents reported spending between 1-2 hours a day on social media. This was followed by 25% who spent between 2-3 hours a day, 18% who spent 3-4 hours a day, 9% who spent 5-6 hours a day, and 15% reporting that they spent more than 6 hours a day on social media.
Additionally, the usage of social media during the pandemic also increased by:
- An additional 1-2 hours per day – 39%
- An additional 2-4 hours per day – 26%
- An additional 4-6 hours per day – 14%
- Don’t know – 8%
- Remained the same – 13%
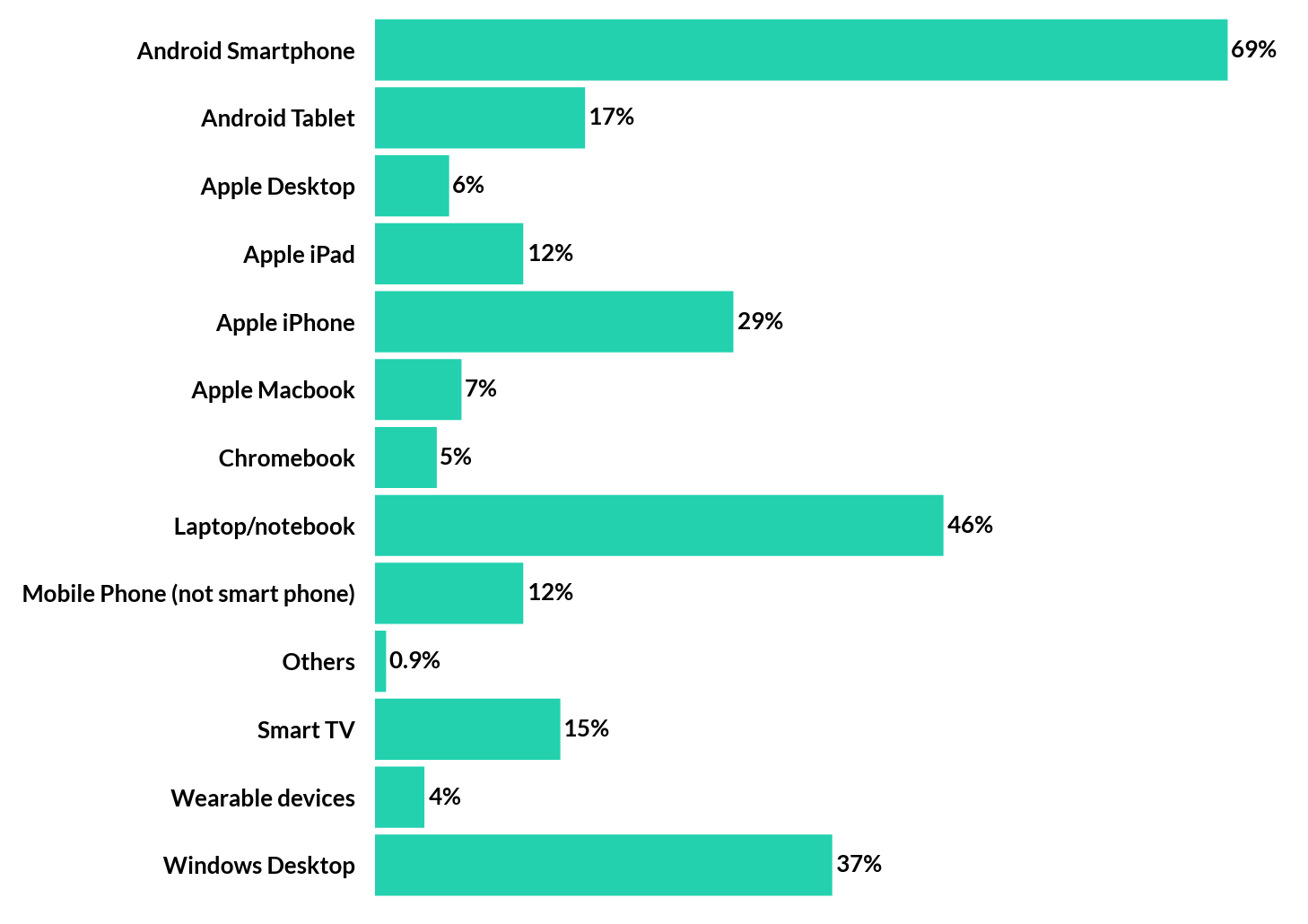
What devices do we use for social media?
Personal devices used for Social Media
Without a doubt, the most common devices being used to access social media are mobile phones and computers (either desktop or laptop).
In a separate survey “More Connected Than Ever Before: How We Build Our Digital Comfort Zones” we conducted earlier this year, it was discovered that 81% of households have a least one device connected to the internet constantly. The implications of this taken together with our findings in this report underline the simple but significant fact that social media is easily accessible and has become a ubiquitous part of our lives.
Decoding the paradox of online privacy
Data privacy is an ongoing debate fraught with complexities. On one hand, the sharing of personal information is essential for us to partake in online shopping or applying for jobs via online portals. Yet, the unprecedented growth in digital data has also resulted in challenges where our personal information could be misused. To successfully manage the potential and risks of a digital economy, it is worth considering the need for a digital social contract – a set of rules that can help govern how we interact and share data online. Before we do so, let us find out where we stand currently.
As of now, more than half (58%) of respondents said that they were equally concerned about their privacy both online and offline, with a quarter (26%) stating that they were more concerned about their online privacy as opposed to offline. At the other end of the spectrum, 10% commented that they were more focused on safeguarding their privacy offline instead of online, with 6% expressing no concerns over privacy at all.
Evidently, the concept of privacy appears to be one that people are well acquainted with. In fact, the areas that we focus on keeping private offline often has a direct correlation with our online privacy, but what are some of the areas individuals are interested in keeping away from the prying eyes of the internet?
- 76% of respondents kept their financial information offline
- 64% surveyed did not post their personal details (identity number, date of birth, etc.) online
- 61% were protective of information pertaining to their family members
- 53% did not want to share their current location online
- 46% preferred to keep private their job details
- 25% opted for anonymity online
- 24% of those surveyed kept their civil status offline
- 22% would rather not share their vice activities (gambling, pornography, etc.) online
Sharing personal and valuable information with people close to you, including your friends, families and colleagues may seem like a symbol of trust. But this practice can result in security and privacy risks for both parties. People can end up sharing confidential data by accident, or unknowingly disclose secrets about themselves or their close ones. With so many devices and online channels at our fingertips, it has become very easy to post an unguarded message or accidentally share information about ourselves or others with the wrong people. Once it’s online, it’s saved forever, and through this, we divulge pieces of ourselves online that will always remain public,” comments Vitaly Kamluk, Director of Global Research and Analysis Team (GReAT) in Asia Pacific (APAC) at Kaspersky.
These figures paint a very straightforward picture of how respondents in APAC understand the concept of privacy, allied closely with concerns that cybercriminals (73%), generic public on the internet (58%), and social networks (42%), who feature in the top three list of targets, should not have access to the information they wanted to keep offline.
When we dug a little bit deeper, figures from this report reflected different attitudes from respondents in APAC on the groups of people they wanted to keep their data private from, as compared to others from the rest of the world.
It appears that individuals in APAC expressed a greater degree of trust in people they interacted on a closer basis, with only 8% wanting to keep their personal information away from their spouses, 12% from their friends and 13% from their employers in a roundup of the top three social groups.
However, in a separate global report “Defending digital privacy: taking personal protection to the next level” that was commissioned by Kaspersky earlier this year, family members, colleagues and the government made up the top three groups of people we do not want to know certain things about us.
Looking at this, perhaps an argument could be made for how different societal attitudes on the element of trust in relationships can influence our understanding of privacy, with respondents from APAC exhibiting a higher degree of trust in social groups deemed to be closer to them.
To confirm our hypothesis, we spoke to Ms. Beverly Leow, a psychologist at Mind What Matters in Singapore. Ms Leow shared that a reason for APAC respondents exhibiting a higher degree of trust could be attributed to the collectivistic and interdependence nature of APAC societies. Additionally, an individual’s expression of emotion and thought (such as the sharing of information online) is often regulated by the consideration of others’ reaction. Hence, it does not come as a surprise as individuals in APAC exhibit a higher degree of trust, as they are in turn motivated by eliciting positive responses to their expressions, which helps define their sense of identity.
Do you have any anonymous social media account and what do you use it for?
How we exercise the power of anonymity could have important implications on the management of one’s digital reputation. Often understood as an entitlement, the use of anonymous social media accounts could either allow us to engage in meaningful free speech, or use it to take pot shots at others without any repercussions.
In this report, we found that 32% of respondents owned an anonymous social media account, with 68% indicating otherwise. Of the 32%, Facebook was identified as the most popular platform (70%) to have an anonymous profile, followed by YouTube (37%), Instagram (33%), and Twitter (25%).
Where this gets interesting, is when we consider the rationale for having an anonymous account. 49% of those surveyed stated that it was for the purpose of exercising their freedom of speech without affecting their reputation, while 48% wanted to indulge in their secret interests that they were not too keen on having their friends find out about.
Although 30% used an anonymous social media account for the fairly innocuous activity of sharing information about their favourite artists and interests, 22% were also engaged in online stalking as well. With almost a quarter of respondents having admitted to online stalking, there is a need for us to pay more attention to this space, especially when the threat landscape for stalkerware widened by 31% in 2019. As this space continues to evolve and grow in the coming years, so too will the possibilities for intrusion into an individual’s private life.
Only a small percentage (3%) reported using an anonymous account to deflect spam emails from their actual accounts, avoid doxing, serve as an alternative for other purposes such as gaming and prevent external agencies from having access to their real email accounts. In this context, it is interesting how some individuals have developed their own innovative ways of practicing good cyber hygiene by creating additional layers of anonymity to safeguard their privacy.
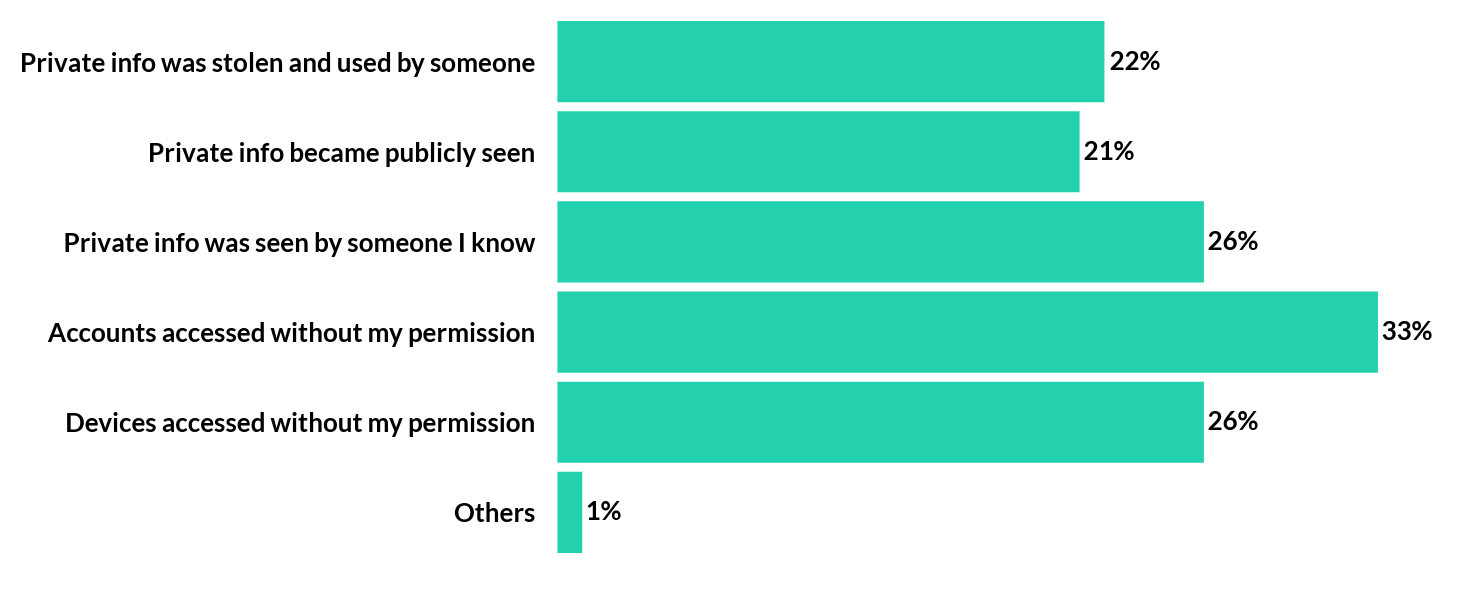
What negative experiences have you faced online?
While the internet offers many opportunities for people to share and consume information, it also presents many unwelcome challenges as well. Although 37% of respondents shared that they have had no negative experience online, 33% stated that someone managed to gain access to their accounts without their permission, with 26% reported having their private or secret information being seen by someone they did not want to let see.
Examples of personal online negative experience
It was also clear that the way people use social media had far reaching effects on their privacy and sense of well-being as well. Predictably, maintaining an active social media presence resulted in users getting disturbed with spams and advertisements (39%), but adopting a laissez-faire approach to social media usage also resulted in 29% of respondents feeling stressed at times, while 10% said that they were blackmailed as a result of sharing too much confidential data.
Additionally, activity on social media created unwanted ill-effects on their relationships with others as well. 15% of respondents reported that their social media posts embarrassed or offended someone, with 13% and 9% indicating that their relationships with their friends/family and partners were damaged, respectively.
Perhaps what is worth highlighting most here is the impact of one’s social media activities on instances of respondents having their visa application denied (4%) and career damaged (7%). While these figures may appear to be low, their impact cannot be understated, with 70% of employers using social media to screen candidates before hiring.
Interestingly enough, exactly a third of respondents provided feedback that they have yet to experience any of the scenarios outlined above, which is close to approximating the 37% who shared that they have had no negative experiences online. But you do not have to look far beyond examples such as an employer who had his residential address posted online after airing his grievances in a Facebook post over millennial job seekers to show that negative experiences in the digital world do not discriminate, it can happen to us all.
Separating fact from fiction
In today’s hyper-connected societies, social media is now a key conduit for the exchange of information. Subsequently, the social media space has also evolved to become a battleground where multiple voices are competing to be the arbiter of truth. In an age where demagogues are blurring the boundaries between fact and fiction, how astute are we when it comes to consuming information on social media platforms?
Almost 71% of respondents stated that they get their news from social media, confirming the widely held perception that social media has become the primary news source for most people. Positive trends were also interpreted from the survey results, with 54% checking the news sources and 51% reading the full article before sharing it on social media.
When we consider why there remains a sizeable portion who fail to verify news sources before sharing it, Leow opined that such behaviour can be understood by the self-presentation theory, where the individual desires to present him/herself in a certain way. In this scenario, it is quite likely the desire to be viewed as updated and well-informed netizens has contributed to the figures we are seeing in this report.
Additionally, a sizeable portion of respondents also identified strongly against the dissemination of fake news, with 34% unfriending/blocking contacts who shared false information, and 29% confronting their friends and family members who disseminated unsubstantiated news reports with each other.
Only a minority of respondents expressed a cavalier attitude towards the sharing of information on social media platforms, with 19% sharing news and 17% forwarding juicy gossips about companies and celebrities before verifying whether they were true.
How does digital reputation matter for businesses?
Two key considerations come into mind when it comes to understanding why digital reputation matters for businesses and organisations. First, cyberattacks can cripple the operations of enterprises and small businesses. Second, the social media has become an important validating tool for an organisation’s product or solution. Together, these two interact to amplify the challenges faced by any business looking to build a positive digital reputation.
What we found in this report is that the discipline and rigour applied to the sharing of news on social media was also evident in how individuals assessed the reputation of brands and companies. 49% of respondents shared that they will check the social media accounts of a brand or company before purchasing their goods or services, with 48% avoiding those who were involved in a scandal or had received negative news coverage online.
49% of social media users in APAC will check online accounts of a brand or a company before a purchase
Additionally, 38% also stopped using a company’s or brand’s products once they were embroiled in some kind of crisis online. In terms of brand’s transparency on their online pages, 50% of users in APAC think that companies should not delete negative comments on their social media accounts. Almost half (41%) also revealed that the reputation of the brand’s endorsers affect their view of the brand.
In a separate survey conducted by Kaspersky last year, “IT Security Economics Report”, enterprise companies and small and medium-sized businesses lost an average of $1.4 million and $108,000 respectively to cyberattacks. While cybersecurity threats can come in the form of phishing or crypto-mining attacks and affect an organisation’s ability to function properly, the resulting damage is not just financial in nature, but also reputational especially when scrutiny of the business can be easily done on any online platform.
In a nutshell, when we look at user attitudes towards the sharing of fake news on social media platforms and how they interacted with businesses – it was clear that the sanctity of digital reputation was a key consideration in determining how individuals socialised with each other, as well as with companies too. Leow agreed, stating that as human beings, we tend to have a stronger preference and favour others who have a reputation for being kind, sociable and empathetic. Without a doubt, social media has now become an important interlocutor on conversations pertaining to both personal and business conversations online.
“Social media has come a long way since the launch of Six Degrees back in 1997. Users are no longer using social media as a forum to keep in touch with each other and to provide updates on their lives, but are also using it as a validation tool to assess the digital reputations of individuals and businesses. Emerging parallel to this trend, is also the rise of phishing attempts on social media platforms such as YouTube, Facebook and WhatsApp where we’ve seen fake accounts attempting to unravel scams on unsuspecting users. Hence, it is important that we step up our scrutiny on the information being shared online in this area as well,” adds Connell.
How well are we protecting our online privacy?
Internet security software is often understood as the first line of defence when it comes to safeguarding our personal information, and the findings reveal that:
- 55% of respondents surveyed have internet security software installed on their devices
- 33% do not have any internet security software installed
- 12% do not know how or are unsure if they have any software installed on their devices
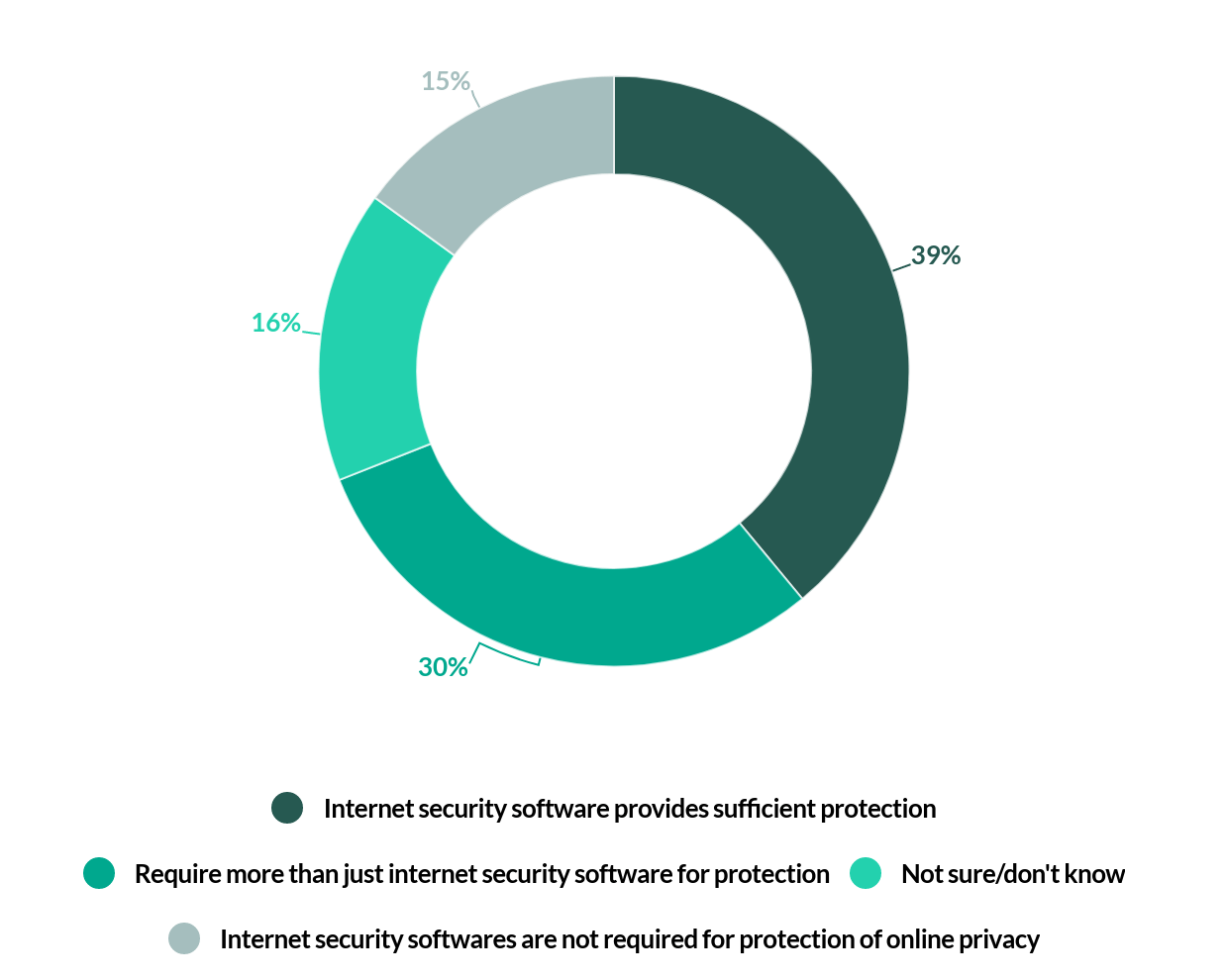
Which of the following statements best reflect your opinion about the efficiency of antivirus software for the protection of online privacy?
With these statistics in mind, it is important to understand the thinking that has accounted for these statistics. With a complete picture of what user attitudes are when it comes to the use of internet security software, we can piece together where the gaps and opportunities are.
With these statistics in mind, it is important to understand the thinking that has accounted for these statistics. With a complete picture of what user attitudes are when it comes to the use of internet security software, we can piece together where the gaps and opportunities are.
How efficient is internet security software when it comes to the protection of online privacy?
There are many ways where hackers can violate your online privacy and fortunately, there is now a wide range of software available that are designed to prevent websites from tracking you, or prevent hackers from installing malware on your devices. While it won’t stop the most determined hacker, the use of internet security software can go a long way in preventing them from getting access to your data.
“Adopting a layered approach as an additional protection measure is crucial as cyber-attacks evolve in complexity and sophistication. The use of multiple levels of security must cover every touchpoint we use to interact with the online world and involve layers of varied nature to protect privacy and data. From what we can see, it appears that there is a need to drive higher levels of awareness when it comes to protecting one’s privacy in the region. To do this, it is essential that stakeholders such as governments, private enterprises and the public cooperate more closely. Along with the thoughtful use of cybersecurity solutions, we will then be able to elevate our cyber-resilience to the next level,” Kamluk highlights.
Our findings showed that 39% felt that internet security software provided sufficient protection against hackers, with 30% wanting more than just internet security software to protect their online privacy. On top of this, 16% were unsure if they were efficient, with 15% reporting that it was acceptable not to use internet security software to safeguard their personal data. Although a majority (69%) firmly recognised the importance of having internet security software as a foundation for data protection, the fact that 31% remain unconvinced or are unsure of the utilities of such protection suggests that there is much more to go when it comes to raising public awareness on the importance of using the right cybersecurity solution when it comes to preventing any unauthorised access.
What do you regularly do to keep your data private on your devices?
For the cyber-savvy, kudos to you for taking the necessary steps to keep your data private. But are you doing it right and is it sufficient? An overwhelming 72% of respondents reported that their devices were protected with passwords, with 53% also indicating that they checked and changed their privacy settings on their devices. With our increasing dependency on online accounts to conduct our daily affairs, these figures paint a positive picture that individuals have rightfully identified password protection as the first line of defence.
However, in the same survey “More Connected Than Ever Before: How We Build Our Digital Comfort Zones” we conducted earlier this year, 46% of respondents said that they were sharing passwords for Netflix/Hulu, with 33% sharing their Wi-Fi passwords with their housemates. Hence, while it is a good thing to have in place passwords for your devices and user accounts, it is equally important to not share your password or consider introducing more security measures to keep your data private.
This brings us to the next set of statistics where our report found that 49% avoided the use of illegal software, with 28% and 24% using special software for system cleaning and encrypting their data respectively. The key takeaway from this is that only approximately a quarter of respondents adopted additional measures such as system cleaning tools and data encryption, which more or less corresponds to the 30% wanting more than internet security software to protect their digital privacy. From this, it is clear that users need to prioritise upgrading and increasing their security measures to ensure that they are comprehensively protected.
Interestingly, 30% of respondents also made it a point to cover webcams on their computers to avoid spying. During this period where most of us are working from home, it is important that we prevent our webcams from staying ‘active’ when we are not using Zoom, Skype or Microsoft Teams for work, study or virtual socialising.
What will you do if your social media account was compromised?
Despite your best efforts to protect your social media account from being hacked, you are now a potential victim of a cyber-breach. Such moments can be quite stressful, as cybercriminals can use your account to make offending posts or spread misinformation, resulting in your digital reputation being damaged.
When it comes to rectifying social media account breaches, our survey found that:
- 33% of respondents tried to regain control of their accounts by requesting a password reset
- 27% reported the incident to the social media platform
- 18% informed their family and friends
- 14% reported the breach to authorities
- 4% created a new account
“While the survey shows that netizens are generally familiar with what to do when their social media accounts have been compromised, there are some areas for improvement. First, more can be done when it comes to warning as many people as possible when your account has been hacked. If your account is compromised, hackers may start sending requests in your name. For example, they can tell your contacts that you are in an emergency and desperately need cash. Also, it is worth making a list of the most important services linked with your hacked account. It is important to change the passwords for the associated accounts to ensure that they don’t gain access to your other accounts and end up doing more damage,” recommends Connell.
Anticipating future challenges to our digital reputation
According to Gartner, 65% of the world’s population will have its personal information covered under modern privacy regulations by 2023, up from 10% today. However, can the enactment of privacy and data protection laws keep pace with the rapid advancements in technology, especially in a post-COVID world? What are some of the emerging technologies we need to pay attention to in order to further safeguard our digital reputation?
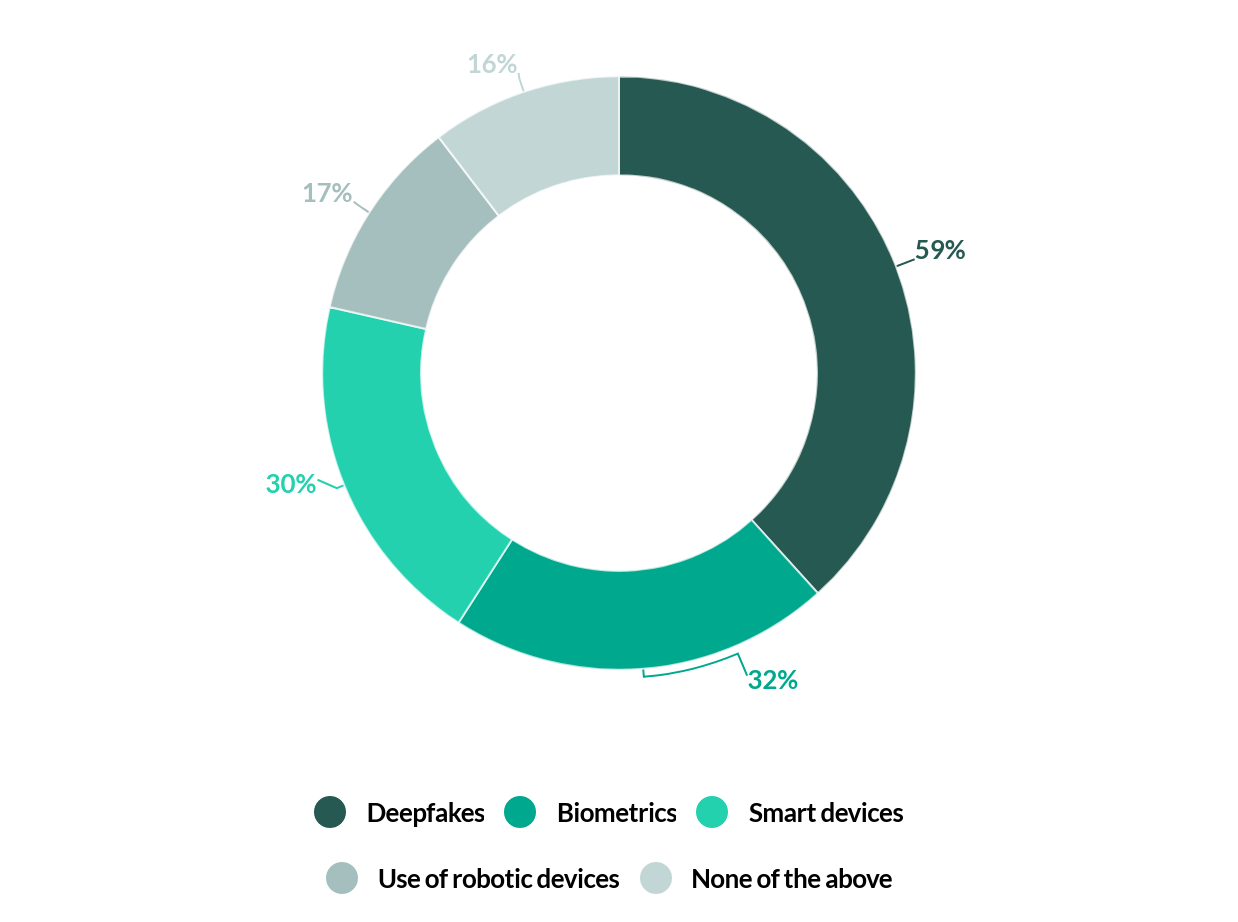
While Deepfakes remain a relatively developing phenomenon, 59% of respondents recognised their potential to distort and manipulate reality. Till date, Deepfake videos have been used for political purposes, but they are increasingly being used for blackmail and fraud as well. For example, the CEO of a British energy firm was tricked out of $243,000 by a voice Deepfake of the head of his parent company requesting an emergency transfer of funds. Additionally, Deepfake pornorgraphic videos have also been used to blackmail female reporters and journalists, such as Rana Ayyub in India, who exposes abuses of power.
What emerging technologies are you afraid of?
Another notable issue that was raised by respondents in our survey is the use of biometrics, with 32% expressing concerns with how biometric identification could compromise our privacy. Although biometrics provide a quick and reliable way to identify and authenticate people by their unique physical characteristics, it is worth remembering that it is not foolproof.
To put it simply, any digital data can be hacked and misappropriated, especially in an environment where our iris and fingerprint data are stored on our phones, social media and law enforcement databases. While the greatest appeal of biometrics lie in its immutable quality, it also represents the worst drawback since you cannot reset such data like how you would with a password, as well as open yourself to greater scrutiny to unwanted government and private sector surveillance.
Finally, with the advent of the Internet of Things (IoT), we have seen a wave of integration of technology into our lives and surroundings. This is especially true for countries such as Australia and Singapore, who are now leading the way in smart city development. However, the proliferation of connected devices also undermine a fundamental principle of privacy – that is, the ability to separate contexts as and when we deem fit. Hence, it came as no surprise that 30% of respondents expressed a certain degree of discomfort with how smart technology was being integrated into cars, traffic lights, etc.
Let us use the example of smart cars. According to our researchers, third party apps that help your car connect to the internet, download maps and perform remote diagnosis and maintenance could offer a gateway to attackers to gain unlimited control over the vehicle. By doing so, cybercriminals can monitor the car’s movements, eavesdrop on conversations and even inject ransomware that prevents the vehicle from moving until the owner pays up in cryptocurrency.
The usual suspect cases where personal information on social media and e-commerce platforms will continue to dominate conversations on data privacy for the foreseeable future. However, we should expect and be prepared that threat actors will continue to dive deeper and leverage on the emergence of new technologies such as Deepfakes, biometrics and IoT to hunt for more sensitive leaks. These technologies will push the limits of our understanding of privacy, as well as escalate the complexity of cybersecurity challenges. Consequently, it is important for us to not only explore how we can leverage these technologies to our benefit, but also examine how we can create deeper synergies on how they should be regulated,” recommends Kamluk.
Conclusion
The value of reputation is not entirely new to the online world. Many of us have been doing it since eBay pioneered the use of feedback for both sellers and buyers. We are even more doing it on a daily basis, whether it is unwittingly or on purpose, as we scroll through Instagram or be another faceless statistic on an e-commerce store’s overall sales volume. As the days goes by and we turn to our electronic devices to deal with the vicissitudes of the new normal, social and online media will not just amplify existing privacy and reputational challenges, but create new ones as well.
In this report, we’ve charted out attitudes which illustrate that the power of anonymity on social media can empower us with greater levels of free speech. Yet, unfettered communication without any filter also impinges on a person’s online rights, and at the very core of this lies the concept of digital reputation.
As a useful starting point, determining the veracity of news sources before sharing them on social media, practising good cyber hygiene in the form of using the right cybersecurity solutions, protecting your devices/accounts with passwords, as well as encrypting our data should be held as the core tenets of safeguarding one’s digital reputation and privacy. But that is not all.
At its core, digital reputation is an amorphous concept. It is fluid and dynamic and everyone has their own interpretation of what digital reputation means to them. However, from the research findings, a few key takeaways can be gleaned.
Whether it involves someone gaining access to your private data, or how you determine whether to buy or use a product from a brand or company involved in a scandal, these activities contribute to the increasing circulation of ‘social capital’ or reputation as we have mentioned in this report.
Moving forward, the importance of a digital reputation economy will become even more valuable, especially with the emergence of Deepfakes and IoT. This would mean that us as voracious consumers of content, will need to learn how to strike a fine balancing act between privacy and cybersecurity.
It may seem like we are asking you to shift the mountains and shake the hills, but we hope that through the sharing of our findings with you in this report, we have provided some hints as to how to move from this new normal to a new future where technology can be used to deliv+6er that holy grail for you – a positive and secure digital reputation.
How to safeguard your digital reputation
The result of this report highlights an urgent need for us to implement protective measures to protect our online privacy better. Here are some five important steps that we can all take to ensure that we are protected and secure online:
- Remember your digital reputation is also linked to your personal reputation. Everything that is posted on the internet remains on the internet, including harsh and radical judgments. These can lead to unpleasant explanations at the workplace or during hiring processes.
- To protect your digital reputation, it’s better to be more cautious than to reveal personal information about yourself, especially on social profiles. Never divulge too much, stick to basics and share only things that are necessary and needed. The more your share, the more appealing you are to an attacker who is looking to steal your personal data or even your identity.
- Delete accounts and data – we all have dozens of accounts, many of which are barely used or forgotten. Many of them persist and any one of them could leak your information.
- Preventing personal data abuse – if apps are asking for sensitive data, take a look at its privacy policy, which might openly state that your data will be passed to third-party companies. Don’t give apps more information than necessary – think carefully about what they genuinely need and what they can do without. Remember that any information you hand over to apps is unlikely to remain completely private.
- A combined solution of security products and practical steps can minimise the threats and keep your data safe online. Reliable security solutions for comprehensive protection from a wide range of threats – such as Kaspersky Security Cloud and Kaspersky Internet Security, coupled with the use of Kaspersky Password Manager to safely store your valuable digital data – can help solve the problem of keeping your personal information under control.