The rapid rise of cloud adoption
As many organizations are digitizing their operations, the popularity of the cloud has risen rapidly amongst both enterprises and small to medium-sized businesses (SMBs). Gartner has estimated that the public cloud market revenue is expected to grow a further 17% in 2019.
Recent research from Kaspersky Lab suggests this rate of adoption is well on track. In fact, more than a third (37%) of SMBs and half (50%) of enterprises are either currently using or planning to increase their usage of public cloud services.
It’s no surprise that the technology has taken off. The cloud has enabled businesses to improve the agility of their IT infrastructure and the reliability of their services as well as increase their ability to deliver new products and services faster.
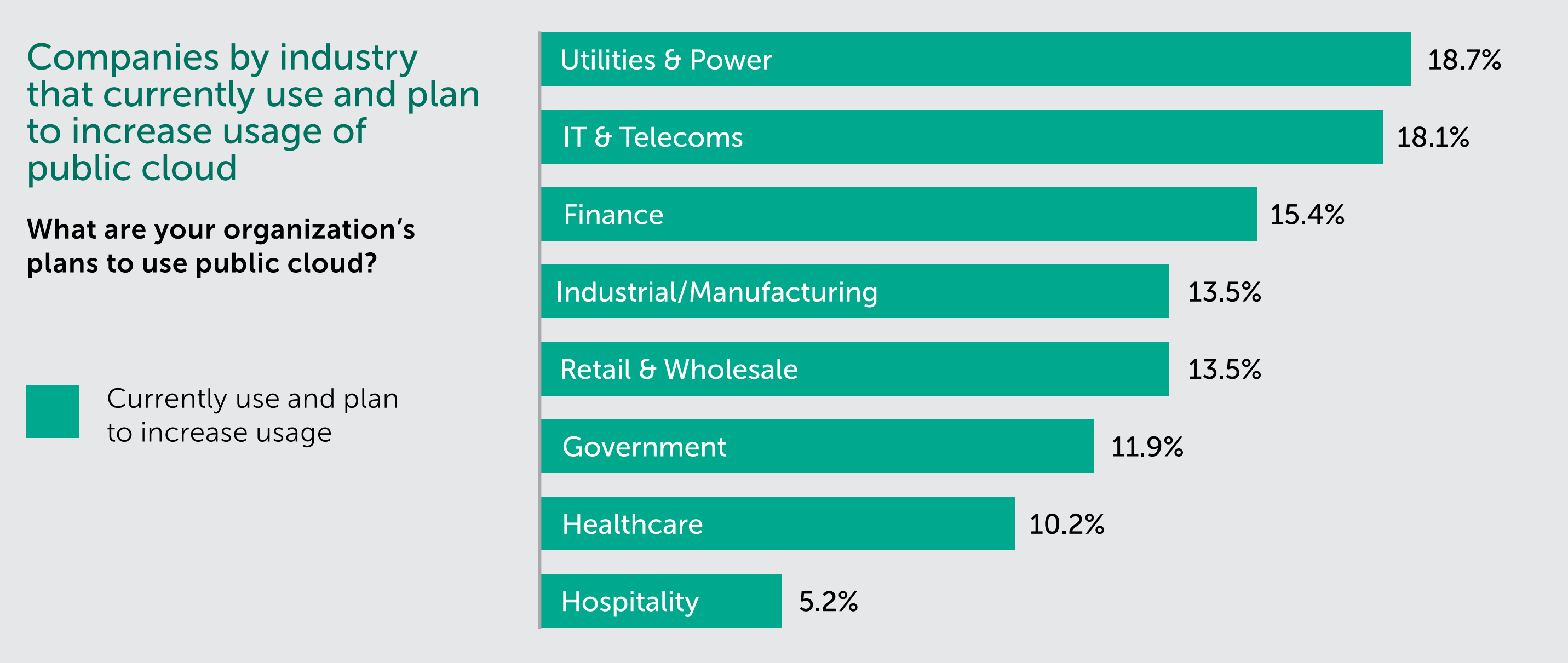
There is also the financial incentive to reduce capital expenditure. It costs two-fifths of organizations more than $100,000 a year to store data on outdated IT hardware. The surprise is that this change is most prevalent within heavy regulated industries. Cloud adoption has, thus far, been most popular amongst utility providers, followed by IT and telecom companies, and then financial services.
Whether businesses are dealing with a customer’s connectivity, finances or energy needs, the cloud offers exciting possibilities in how to manage information, process applications and stay connected. However, as with any other rapidly growing new technology, it brings new risks and new headaches for businesses. This report examines the risks companies recognize could impact their cloud infrastructure, which threats they are preparing for and which affect them the most. It also looks at how organizations should approach cybersecurity of cloud infrastructure to protect themselves and their customers.
Methodology
The Kaspersky Lab Global Corporate IT Security Risks Survey is an annual study into the state of IT security within organizations across the world. It is now in its 8th year and builds upon findings in the previous year.
A total of 7,186 interviews took place in 24 countries. Companies of different sizes – including very small businesses with 1-50 staff members, SMBs with 51-999 employees and major corporations/enterprises with over 1,000 employees. Fieldwork was completed in March-April 2018.
Recognizing responsibility to protect sensitive data
Our study revealed that despite our reliance on cloud platforms, businesses are still concerned about the safety of their workloads and the data stored in the cloud. SMBs and enterprises alike are increasingly storing sensitive personal information in the cloud, meaning customer trust is at stake should a breach occur. In fact, a fifth (21%) of businesses have already moved to the cloud to store sensitive personal information that reveals a customer’s identity. It is easy to assume that the responsibility for keeping what is stored in the cloud secure should lie with the provider of cloud platform. However, the responsibility to mitigate the threat of a data breach does not solely lie with them. In fact, it remains much more likely for organizations to suffer a breach due to simple and preventable staff mistakes.
Many businesses are still reporting threats from a well-known and traditional type of cyberattack – social engineering. Kaspersky Lab has found that a third (33%) of incidents affecting infrastructure hosted by a third party were caused by phishing or other social engineering techniques. If a user is enticed to open a fake email, download a harmful program, or click on an illegitimate web link, they then become responsible for compromising their corporate network rather than the service provider supplying the infrastructure. When we examine the origin of the attacks, just 11% of incidents were caused by the cloud provider. This makes it clear that the responsibility to ensure the cloud is safe should not be delegated to the cloud provider by default but should be shared amongst everyone involved.
When it comes to human factor, sensitive data suffers the most. Around nine-in-ten SMBs (88%) and enterprises (91%) that have experienced a data breach affecting the public cloud infrastructure they use, said social engineering was part of the attack. The top three types of data that were stolen were: information that confirms customer identity, customer payment information and user authentication credentials. The ramifications can be stark. Whilst on average, a successful breach carried out in this manner will cost an SMBs $206,000, it will cost enterprises significantly more ($2,016,000).
Businesses, though, shouldn’t ignore threats specifically created to harm their key infrastructure too. The research discovered that almost as many (26%) could be attributed to this type of targeted attack.
Are businesses protecting themselves?
With downtime, financial loss, company reputation and hard-earned customer loyalty all at stake should disaster strike, businesses are under increasing pressure to protect their networks. Nearly two-fifths of enterprises (39%) and more than a third (35%) of SMBs have revealed they are worried about incidents that affect IT infrastructure hosted by a third party provider.
So, after establishing that organizations are more likely to be breached due to social engineering rather than a fault that lies at the door of the service provider, businesses need to establish measures of protection to keep the visibility of cloud environments, along with good security management and the safety of data stored in there. Whilst specific solutions to fulfil this requirement are readily available, our research shows that most businesses are yet to adopt and implement them.
For example, more than a quarter (28%) of SMBs and a fifth (22%) of enterprises feel they are either not equipped or just ‘somewhat’ equipped with security solutions for cloud applications, infrastructure and platforms delivered as a service. Perhaps more alarmingly, less than two-fifths (39%) of SMBs and half (47%) of enterprises have adopted tailored protection for cloud infrastructures to safeguard themselves against data leaks. So, despite the concern surrounding cloud platforms, some businesses are not acting to fully protect their networks, not to mention, there should be also strong process-oriented and educational measures to avoid risks such as human factor.
How can businesses secure the cloud?
Our research shows that there is still a long way to go for businesses to adequately protect themselves against threats to third party cloud platforms. This is putting entire business operations, networks and processes at risk. From defending themselves against the scourge of social engineering and conventional malware, to preempting targeted attacks, the responsibility lies with businesses to adopt the requisite solutions that keep third party infrastructures secure. It is simply not enough to rely on the cloud provider to do it. Kaspersky Lab recommends the following steps to keep businesses protected:
- Raise awareness amongst employees about the cybersecurity threats they can become victims of. They mustn’t click on links or open attachments in communications from unknown users nor download files or programs from untrusted sources. For this purpose, Kaspersky Lab has dedicated awareness gamified trainings — Kaspersky Security Awareness.
- Sometimes different departments use cloud platforms bypassing IT and IT security teams. To minimize the risk of unapproved use of cloud platforms, educate staff about the negative effect of shadow IT and establish procedures of purchasing and consuming cloud infrastructure for each department.
- Use an endpoint security solution to prevent social engineering attack vectors. It should include protection for mail servers, mail clients and browsers.
- Do not delay implementation of the protection for cloud infrastructure. When migrating to the cloud, understand your migration roadmap and areas of responsibility for each type of cloud platform you use.
- Cloud infrastructure is often a dynamic object that lacks transparency. It is optimal to use a dedicated cybersecurity solution that has a unified management console to manage security across all cloud platforms, and supports automatic detection of cloud hosts, as well as autoscaling to roll out protection on each of them.
- Kaspersky Hybrid Cloud Security offers businesses multi-layered protection for multi-cloud environments, unified cybersecurity and seamless orchestration. The solution detects common and complex threats and protects the entire cloud infrastructure from on-premise virtualized environments to public cloud platforms, such as AWS and Microsoft Azure.
More information about Kaspersky Hybrid Cloud Security can be found by visiting our official website.