In the beginning of 2012, I got a MacBook. At the time, I knew little about gadgets, and I was not planning to buy any other Apple devices. I powered up the laptop and created an Apple ID account. As requested, I chose a password and several security questions.
Four years later, I have an iPad as well, and of course I’ve purchased several interesting apps (some of them I found in this list made by my colleague). My account became valuable to me, and I started thinking about its protection. That’s why I decided to turn on two-factor authentication.
It wasn’t as easy as it should have been; Apple wouldn’t allow me to change anything in the Security tab until I could answer my security questions perfectly. And the answers I put in did not match.
When I tried to change the security questions, I found out that the secondary e-mail used to perform such operations was not verified. I still have no idea why Apple would treat an unverified e-mail as active, but it did, and thus began an endless circle.
I clicked the Verify Email link several times but received no confirmation e-mails. Everything was going wrong. It wasn’t a good time to ask tech support for help, so I had only one way out — I had to hack my own security questions.
How I hacked the questions
The questions that I chose four years ago were not so difficult. But thinking about the answers, I realized that anybody could figure them out by looking at my CV or social network account.
— Where was your first job?
LinkedIn is an obvious place to find the answer to this question.
— Where did your mother and father meet?
My parents grew up, met each other, and got married in the same city where I was born. A lot of people have the same life story. And many people list their native cities on social networks (and social networks usually ask people to do that!). This question is not secure at all.
— What is your favorite children’s book?
Well, I had several favorite books as a child, but the most likely answer was The Hobbit, by J. R. R. Tolkien. Like the other answers, this one wasn’t exactly a secret: First, the book is very popular. Second, my university friends and classmates know that I wrote several term papers about The Hobbit. My half-finished dissertation was devoted to eleven translations of The Hobbit into Russian! In the end, the only mystery about this question was whether I wrote the shorter title or the full name — “The Hobbit, or There and Back Again” — four years ago.
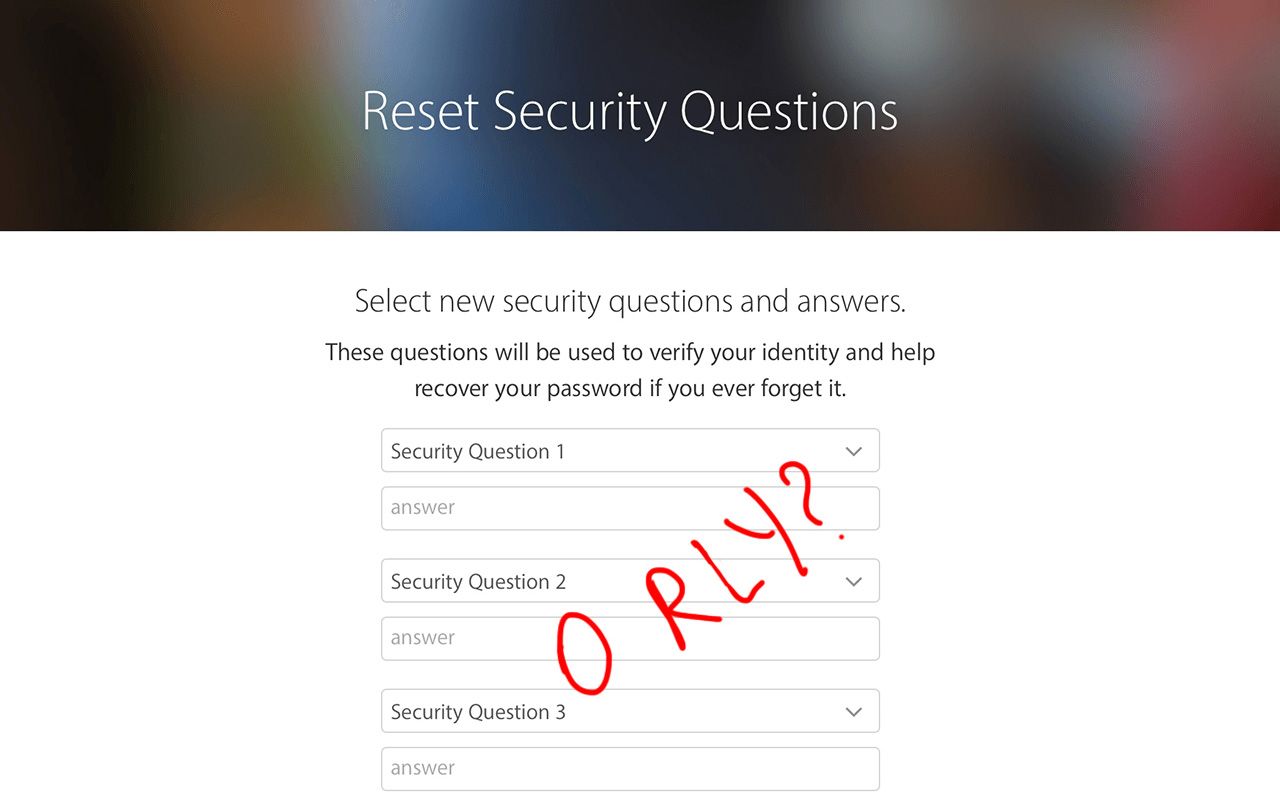
If I knew all of the answers, then why didn’t my answers match? It’s simple: I had English as the main language of my account, and that meant the security questions were also shown in English. But four years ago I answered them in Russian. When I switched languages and reentered the same answers, they matched. But even for people who don’t switch languages, security answers may become problematic: Did you use proper capitalization? Abbreviations? Nicknames?
I began thinking about what makes a good security question — and answer.
What is a good security question? If you have to choose a question from a list, which should you choose?
Five criteria help us distinguish good security questions from bad.
1. Obscurity — questions must be hard to guess or research. For example, a favorite of many banks — your mother’s maiden name — sucks for sure. I won’t waste your time covering the 9000 ways to figure that one out.
2. Stability —answers must not change over time. Avoid “favorite” questions: Your favorite job, food, band, movie, restaurant, vacation spot might change in a few years.
3. Memorability — we enter passwords relatively often, but it’s rare we have to answer security questions. Even if you remember the name of your first-grade teacher when you’re a teenager, you may have forgotten it by the time you’re in your thirties — or sixties — so try not to choose questions whose answers you’re likely to forget in a decade or two.
4. Simplicity — some questions have multiple correct answers. Where was your first kiss? That might be “New York,” “New York City,” “NYC,” “Central Park,” or at least a few other options. Don’t give yourself easy options to fail; avoid questions you might answer in a variety of ways.
5. Choice multiplicity — questions that require “yes” or “no” answers are terrible. Even a stranger has a 50% chance of guessing right! Good security questions can be answered in infinite ways — and you should be the only person who knows the right answer.
Beware social media phishing
You’ve probably seen some social media surveys or quizzes inviting you to wax nostalgic and share the “first 7 places I worked…” or “your first airplane trip….” Those are a treasure trove for social engineers. Actually, they often originate with criminals.
If you want, you can change the answer to even the worst security question ever such that nobody could guess it — what is your mother’s maiden name? XCU*(&S1042! — but of course, you need to be careful not to confuse yourself as well.
As a better option, you might take the maiden name Woodhouse and strip it down to the consonants: wdhs. Evenly intersperse the birth date 04.08.80 to get 04wd08hs80. Not a brilliant trick, but much better than the original.
This kind of method is best for those security questions you have to answer often — for example, when you call your bank. If you have to remember it from time to time, the combination will stay fresh in your memory.
Ultimately, however, there are better ways to protect your accounts than security questions — for example, two-factor authentication.
 Apple ID
Apple ID

 Tips
Tips