Apple OS X Yosemite (10.10) has arrived, and it’s time to look at what it’s going to offer us from a security point of view. Apple has actually set up a special page dedicated to security for OS X with a lengthy amount of text – there’s a lot of it, but it’s comprehensible and rather easy to read. Unfortunately, it doesn’t say a lot about what features are new.
First of all, Apple states, security was “the first thought. Not an afterthought.” This is something that is extremely welcomed these days. Actually, it always has been, but not every developer has been thinking about building in security from the ground level. Apple does it right, or at least it says it does.
Most of the security tools involved are given specific names – Gatekeeper, FileVault, etc. It’s a marketing approach but it also helps to explain which tool does what. So, let’s look at them.
Gatekeeper
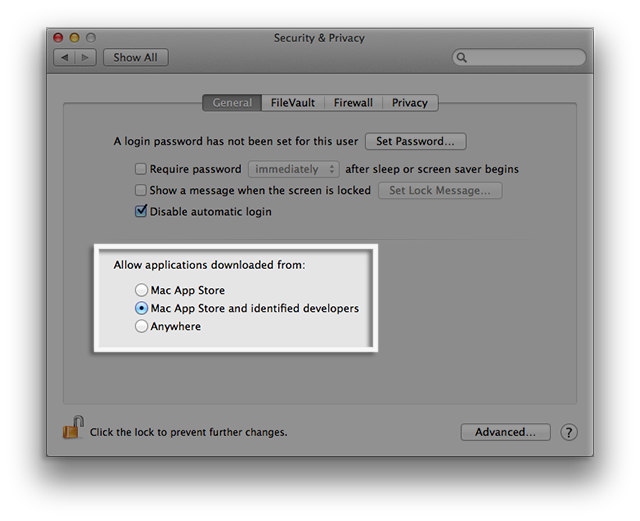
It’s an old feature (presented in OS X Mountain Lion 10.8) that protects a Mac from malware and “misbehaving apps downloaded from the internet.” It’s similar in its purpose and behavior to the Windows User Account Control (UAC). In a nutshell, Gatekeeper checks whether the app, downloaded from other places rather than the Mac App Store, has the proper Developer ID. If it does not, it will not launch, unless the settings are changed.
By default, Gatekeeper allows users to download apps from the Mac App Store as well as those with a Developer ID. Otherwise, they are blocked, but a manual override is possible. Other options include “Anywhere” (the least safe) and “Mac App Store” (nowhere else; it’s the highest security setting).
FileVault 2
This security tool encrypts the entire drive on a Mac, protecting the data with XTS-AES 128 encryption. Apple says that the initial encryption is fast and unobtrusive. It can also encrypt any removable drive, helping the user secure Time Machine backups or other external drives.
RT @threatpost: Mobile Device Encryption Could Lead to a ‘Very, Very Dark Place’ FBI Dir. Says http://t.co/8aqN4R4IXc #Crypto #Surveillance
— Kaspersky Lab (@kaspersky) October 16, 2014
FileVault 2 also allows users to wipe all the data on the drive, and it is done in two stages. First, it kills the encryption keys from the Mac, which is supposed to make the data “completely inaccessible,” according to Apple. Then it proceeds with a thorough wipe of all data from the disk. So, those who would like to recover anything from that drive will have a lot of “fun.” As a way to secure sensitive data and keep it from getting into the wrong hands, it’s extremely useful. As is next tool called…
Remote Wipe
This tool allows users to delete all of their personal data and restore their Mac’s to the factory settings, if it has “changed the owner” without the user’s consent. A milder option is to set a passcode lock remotely.
#Security features in #Apple OS X #Yosemite
Tweet
iCloud.com and the Find My iPhone app on iOS devices, allow users to locate their missing Mac’s on a map. If it is offline, then as soon as it makes a Wi-Fi connection, the user will get a message. There is also an option to display a message on the screen with information about how to return the missing computer.
Passwords
The Safari Browser is equipped with Password Generator, which creates strong passwords for your online accounts. There’s also iCloud Keychain that stores your logins and passwords (as well as your credit card information) with 256-bit AES encryption. iCloud also allows users to sync all usernames and passwords between Apple devices – Mac, iPhone, iPad and iPod touch.
Privacy criticism hits OSX Yosemite over location data https://t.co/UmOsSXHT8H pic.twitter.com/zB4rExnEYb
— Eugene Kaspersky (@e_kaspersky) October 20, 2014
This autofill option has just one setback: if someone unfriendly gets a chance to use your Mac in your absence, there may be ramifications. Therefore, it is strongly recommended that users apply the Disable Automatic Login in their Security & Privacy settings.
Privacy controls
These options allow (or disallow) certain apps to request your location data, with an explanation on how Location Services may interfere with privacy. There are also certain “Accessibility” tabs, which allow users to permit certain apps to “control your computer” (an obvious counterpart to Windows – some applications, especially legacy ones, request a “Run as an Administrator” setting to get going). It’s up to the user to decide what apps will have these privileges. While it is not necessarily affecting privacy on its own, it is certainly worth mentioning as an extra security feature.
Apple shows the right direction for improving #security of OS X.
Tweet
Actually, Apple could have done even more with privacy: it appears as though Spotlight on Yosemite reports a user’s current location (at the city level) and all of their search queries, by default, to Apple and third parties. To get rid of this, Spotlight Suggestions and Bing Web Searches should be disabled in System Preferences > Spotlight > Search Results. Spotlight Suggestions also require separate disabling in Safari settings.
Antiphishing
The tool (actually introduced quite some time ago) is in place. An increasingly common problem, phishing requires special countermeasures, and it’s a good thing that Apple provides them.
#Spam in September: Financial #Phishing Accounts for Highest Percent of Detections http://t.co/vpLfxTUoKN pic.twitter.com/JoB7d8qPFd
— Kaspersky Lab (@kaspersky) October 23, 2014
It’s a basic tool that allows users to accept or deny incoming connections to your Mac by application. However, it doesn’t provide outbound firewall protection, so it would be reasonable to install something more robust.
Sandboxing and Core-level Protection
Here we have App Sandbox, a feature introduced in Mac OS X Lion 10.7; it is an isolated environment for the apps that could become harmful to the system. Interestingly, OS X delivers sandboxing protection in Safari by sandboxing the built-in PDF viewer and plug-ins such as: Adobe Flash Player, Silverlight, QuickTime, and Oracle Java – exactly the software that is among the most vulnerable and exploited.
But also, OS X sandboxes apps like the the Mac App Store, Messages, Calendar, Contacts, Dictionary, Font Book, Photo Booth, Quick Look Previews, Notes, Reminders, Game Center, Mail, and FaceTime, so that nothing potentially malicious creeps in.
A few simple tips for keeping your #Mac secure and maintaining its hygiene http://t.co/upPQ1sBfz5 via @e_Kaspersky
— Kaspersky Lab (@kaspersky) September 29, 2014
Here we also have run time protection at the core level: it is built into the processor XD (execute disable) feature that “creates a strong wall between memory used for data and memory used for executable instructions.” According to Apple’s description, this protects against malware that attempts to trick the Mac into treating data the same way it treats a program in order to compromise your system.
Also, Address Space Layout Randomization (ASLR) is used for the memory used by the kernel, randomly arranging the positions of key data areas of every program. This technique protects from certain attacks (such as buffer overflows) by making it more difficult for an attacker to predict target addresses. Apple introduced randomization for system libraries with Mac OS X Leopard 10.5, and expanded it to the entire system with Mountain Lion 10.8 in July 2012. So it is there for the time being.
WireLurker is no more. #WireLurker is gone: https://t.co/yjdK4xgX06 pic.twitter.com/gSGd2tSELf
— Eugene Kaspersky (@e_kaspersky) November 7, 2014
Judging by the features listed above Apple made an effort to make OS X more secure, and apparently will keep doing so. This shows that Apple is moving in the right direction by addressing cybersecurity problems and diminishing the possible attack surfaces through various means and tools, both basic and advanced.
It doesn’t, however, mean that it is an “absolutely” protected operating system – unfortunately, there are no such systems. Moreover, the number of threats targeting OS X, specifically, is growing as is the number of Mac users. This certainly has drawn the attention of criminals, who are looking into vulnerabilities and occasionally finding them.
 Apple
Apple

 Tips
Tips