Having worked with Software-as-a-Service (SaaS) models for some time, we are now becoming increasingly engaged with similar schemes for providing entire infrastructures (IaaS) and platforms (PaaS). And we think that’s a good direction for organizations around the world; using a turnkey solution helps businesses focus on their core tasks. But is it possible to provide enterprise-grade companies fully integrated protection within a Security-as-a-Service model?
Our understanding of turnkey protection
To answer that question, we must first define what we mean by fully integrated protection. If we’re talking about enterprises, then it means protection of the infrastructure at all stages of threat response:
- At the incident prevention stage, using endpoint solutions on endpoints;
- At the threat detection stage, by monitoring and analyzing data, which flows from client-side security solutions to the security operations center (SOC);
- At the threat-hunting stage, which involves testing hypotheses about new threats and performing retrospective scans of the historical data for new indicators of compromise and indicators of attack (IoCs/IoAs);
- At the threat-validation stage, during which the SOC team determines whether a particular suspicious event is a real threat or a legitimate action (false alarm);
- At the incident response stage, when we recreate the chain of attack and provide recommendations for remediation.
Endpoint Protection Platform and Endpoint Detection and Response (EDR) class solutions handle the first stage in automatic mode. At all subsequent stages, the involvement of SOC experts is critical. However, not every business can afford an in-house SOC.
What about companies without an SOC?
Having an in-house SOC is not a necessary condition for comprehensive protection. In fact, a majority of large companies do not have it — only about 20% do, comparing the total number of reviews for Endpoint Protection–type platforms with the number of reviews for EDR-class solutions (which assume the availability of a SOC) on the Gartner Peer Insights platform.
How do the remaining 80% get by? A sensible option for most is to delegate security functions. Expert work to seek out threats, assess and confirm them, and respond to incidents can be carried out by a managed security service provider (MSSP) or a security solution vendor that essentially takes over part of the MSSP functions (our case).
Under this approach, clients receive a set of solutions with a much wider functionality than ordinary EDR. It includes both threat detection by analyzing network traffic anomalies (Network Detection and Response, NDR) and the option to have incident information interpreted by experts (Managed Detection and Response, MDR). Our SOC is unique in that its experts have quick access to information about incidents and new threats worldwide, on which basis they can take steps in the interests of the client. And although threat detection and response processes (EDR + NDR = XDR) are already fairly well automated, we are constantly improving this area and plan to strengthen it in the future.
ATT&CK Evaluation methodology has already verified the effectiveness of our approach. Because of the specific nature of the approach, MITRE ATT&CK Evaluation Round 2 focused exclusively on the detection capabilities of our solutions. Therefore, incident response, prevention, and threat hunting — in which our SOC experts are uniquely skilled — were intentionally excluded from consideration.
Our EDR solutions are also have proven themselves as reliable and suitable for both in-house and outsourced SOCs. According to the above-mentioned Gartner Peer Insights portal, our Kaspersky Anti Targeted Attack solution has entered the Top 3 and been recognized as a Customers’ Choice for Endpoint Detection and Response. A huge thank-you to all our clients who took the time to leave a review.
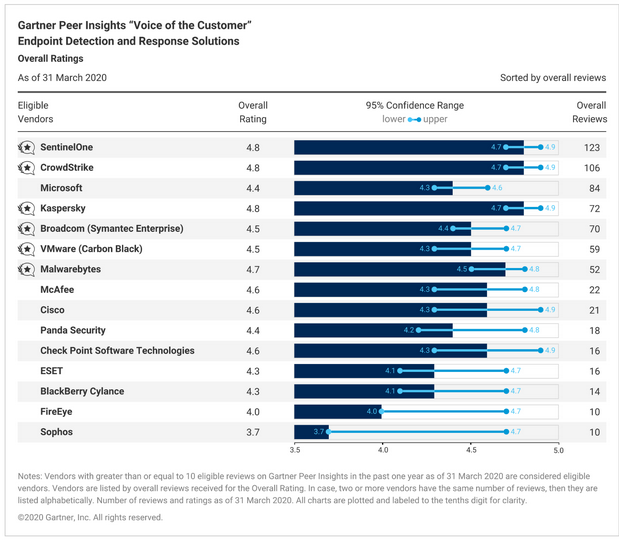
Overall ranking of EDR solutions according to Gartner Peer Insights. Source: Gartner
To sum up, I believe that the future of information security undoubtedly belongs to Security-as-a-Service, but with the option for the client to select the degree of automation of their chosen toolkit and to upgrade their turnkey solution with additional features.
 SOC
SOC


 Tips
Tips