Pornography has always been part of human culture, and this continues in the digital age. When technologies started changing the way people entertained themselves visually (first through photography, then through cinema, television and video and, after that, the internet) adult content was always there, hiding in the shadows of mainstream art and entertainment content. With the arrival of the internet, adult content rapidly migrated from physical home collections and the upper shelves of video shops to the web and mobile applications.
With this transition, adult content became readily available to a wider and larger audience, at lower cost and often even for free. Today, porn can be found not only on specialist websites, but also in social media networks and on social platforms like Twitter. Meanwhile, the ‘classic’ porn websites are turning into content-sharing platforms, creating loyal communities willing to share their videos with others in order to get ‘likes’ and ‘shares’.
In other words, from a niche, secret and tabooed type of content, porn is turning into mainstream entertainment with an audience comparable to non-adult sites. Sex sells, as they say in the advertising industry. However, in cyberspace it not only serves as a means of generating sales, but also as a tool for malicious activity.
This is not a new development. In fact, Kaspersky Lab researchers have observed criminals using porn as a lure to malware or a fraud scheme almost from the first day of adult online content. However, until now we haven’t had a chance to look more deeply into the issue.
The idea for this overview came to us during some completely unrelated activity. While observing underground and semi-underground market places on the dark web, looking for information on the types of legal and illegal goods sold there, we found that among the drugs, weapons, malware and more, credentials to porn websites were often offered for sale. Unlike many other digital goods available to buy on the dark web, these accounts were being sold at very low prices and in almost unlimited numbers. And we asked ourselves: where are these accounts coming from in such impressive quantities?
The sources could be the websites themselves. Based on our brief dive into open sourced information, since 2016 more than 72 million sets of account credentials for adult content websites were stolen and later appeared online. These include data from Cams.com (62.6 million), Penthouse.com (7.1 million), Stripshow (1.42 million), 380,000 of xHamster accounts, and about 791,000 thousand from Brazzers data. And these stats do not include the enormous leak of around 400 million sets of credentials from the AdultFriendFinder website – which focuses on setting up offline encounters rather than content for viewers.
But is that all? And is the loss of credentials to a premium porn website account – with the resulting threat of exposure or extortion – the only risk users face when it comes to online pornography? We decided to find out: to look into the malicious landscape to see how, on what scale and for which purpose cybercriminals are using adult content in their activity. The overall goal of this overview is to raise awareness among consumers of adult content about cybersecurity, as they may find themselves an easy target for a cybercriminal.
Key Findings
Threats to desktop users:
- Kaspersky Lab identified at least 27 variations of PC malware, belonging to three infamous families, which specifically hunt for credentials to paid-for porn websites.
- In 2017, these malicious families were seen more than 300,000 times, attempting to attack more than 50,000 PCs across the world.
Threats to mobile users:
- In 2017, at least 1.2 million users encountered malware with adult content at least once. That is 25.4% of all users who encountered any type of Android malware.
- Mobile malware is making extensive use of porn to attract users: Kaspersky Lab researchers identified 23 families of mobile malware that use porn content to hide their real functionality.
- Malicious clickers, rooting malware, and banking Trojans are the types of malware that are most often found inside porn apps for Android.
A peek into the underground:
- Hacked premium accounts for porn websites are being sold in their thousands on dark market websites; more than five thousand unique sales offerings were identified during the course of our research.
- Credentials to accounts for Naughty America, Brazzers, Mofos, Reality Kings, and Pornhub are the ones most often found for sale on the dark web.
- The average price on the dark market for an unlimited annual account is usually around one tenth of the official cost.
More details on these findings can be found in the report.
Part 1 – Threats to desktop users
When it comes to threats users may face when consuming porn on a desktop computer, we divide these into two major categories: phishing and malware. While malware is something that PC users are more likely to encounter than Mac users, phishing scams are a common threat to both platforms, so we’ll start there.
Porn phishing
Phishing is a type of Internet fraud, the purpose of which is to obtain user identification data: passwords, credit card numbers, credentials to bank accounts and other confidential information. Most phishing schemes have nothing to do with porn and are based on fake emails from banks, service providers, payment systems and other organizations, informing the recipient of an urgent need to update their personal data. Some cybercriminals use porn in phishing campaigns, but in this case it is often used as a tool for delivering so-called ‘scareware’ schemes, and sometimes to lure people into installing malware on their computers.
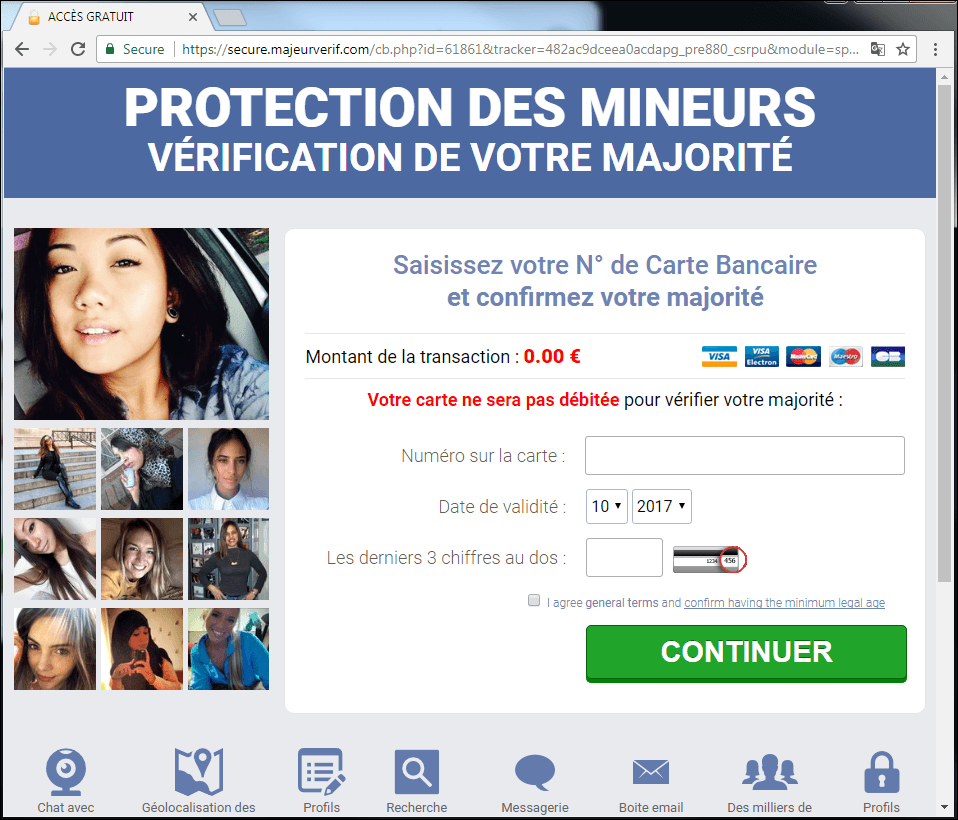
The scareware schemes work in the following way: when a user – while searching for porn – clicks on the phishing link, they are redirected to a page with a pop-up window that carries a warning that the user’s device has been infected with dangerous malware.
The same message invites the user to call what appears to be Microsoft’s technical support service in order to disinfect the device and protect their files. The message claims that the cost will be toll free, but this is not always the case. And even if it is, the phone number usually connects the victim to a fraudster who then uses social engineering to get their personal or banking data.
Another scenario suggests that a ‘technical support’ employee will provide technical assistance and then charges the victim a fee for the service.
Based on what we see in our telemetry such fraud schemes are fairly popular and exist for both PC and Mac users.
The other type of phishing fraud schemes that users risk encountering while searching for porn is aimed at infecting the user’s device with malware disguised as an update for Flash Player – the software application needed to run the video the user is looking for.

Fig. 3: Example of phishing fraud scheme, luring user into installing malware disguised as Flash Player update
This type of fraud has existed for years, and can be fairly easily identified ‘with the naked eye’. However, given that our detection technologies continue to regularly catch such pages, we can assume that criminals still consider it a worthwhile approach.
Some phishing fraud schemes we’ve seen mimic sex dating services. The scheme usually starts with an ad banner on a porn website, which promises a quick and easy date with a woman who lives locally and is looking for a date. If the user clicks on the ad, they are redirected to a page where they are informed that another user is ready for a date.
However in order to get in touch with the potential date, the victim is required to provide their credit card details, for example to prove that they are over the age of consent. This requirement promises not to charge anything to the card and is positioned as a mandatory component of the service. Of course, once the data is entered, the session ends and the victim is left with nothing but compromised payment details.
It would be fair to say that porn phishing is not the most sophisticated threat. The criminals behind such schemes generally target users who are not very cyber-savvy and, unlike five or six years ago there are fewer such users out there. Perhaps that is why, overall, porn phishing is a type of threat we rarely encounter when analyzing the threat landscape. This is, however, not the case when it comes to malware.
Malware and porn
When it comes to malware, porn serves two main purposes:
- Porn websites are a tool to deliver malware to the victim.
- The malware itself is used to collect different kinds of personal data, including account credentials for porn websites.
Multiple times we’ve seen porn websites serve as watering holes for different kinds of malicious software. The scheme is quite simple: first, the cybercriminal hacks the porn website or the advertising platform that is used to show ads on the pages of a porn site. Then they set up a redirection mechanism that automatically redirects a visitor to a malicious webpage that serves them with malicious software.
This is one of the most convenient ways to spread malware and it is often utilized by cybercriminals. We didn’t do a deep dive into the topic to collect exact numbers. However, we did a brief search through our malware collection and almost immediately identified several different malicious tools that were served through porn websites. In most cases, these are not very popular sites, like 2porno-in.ru, pornopriz.loan, pornohd24.com etc. It is possible that many of these and other websites were specifically created as watering holes for malware. However, in a few recent cases we’ve seen dangerous malware being served from popular porn websites, like PornHub, which was used for a short period of time last year to spread advertising malware known to us as Trojan.Win32.Kovter.
Banking Trojans with unusual purpose
When it comes to spyware and Trojans, it is no secret that there are plenty of them, targeting any type of credentials available on a victim’s PC. A special place among this kind of malicious program is taken by banking Trojans. This type of malware is aimed specifically at online banking and is made so that – once installed on the victim’s PC – the malicious program can monitor which pages are opened in the browser and when the victim opens an online banking page. The malware can then modify certain parts of the webpage loaded in the victim’s browser in such a way that the victim enters their credentials into fake login/password fields instead of the real ones. The malware subsequently sends this information on to the criminals.
This is a very widespread technique, used by multiple different banking Trojans. Each such Trojan comes with a number of specific web-injects: pieces of code that are injected into the online banking webpage code instead of the legitimate code. As each online banking system has its own unique code, it requires an exclusive web inject in order to make the credential-stealing work. The most powerful banking Trojans are usually equipped with tens of different web-injects to be able to attack the users of multiple banks. This is a classic feature of most banking Trojans, and that is why we were quite surprised when we found samples that were targeting porn websites instead of banking ones. In total we found 27 variants of three different families of banking Trojan (betabot, Neverquest and Panda) with this unusual target preference.
Ten of those variants were specifically hunting for PornHub.com accounts; five others – for Brazzers.com accounts; three – for chatrubate.com; and the remaining 12 variants were aimed at other popular adult websites like Xvideos.com, Xnxx.com, Motherless.com, Youporn.com and Myfreecams.com.
According to Kaspersky Lab telemetry, in 2017 these 27 pieces of malware were spotted 307,868 times, attempting to infect more than 50,000 PCs across the world.
In comparison to the typical distribution scale of many other types of malware, for example traditional banking Trojans, which are sometimes spotted at a rate of tens or even hundreds of thousand times a month, these are fairly low numbers. That is why it is quite difficult to understand what the existence of these porn-credentials hunting malicious programs means: it could be just an artifact of criminals testing new variants of banking malware, in which bank web-injects are temporarily replaced with web-injects for other sites. Or it could be criminals testing new ways of making money via stealing credentials to paid porn websites and then selling them on hacker forums. Given that the most popular porn websites have user communities that are tens of millions in size, with many users prepared to pay for premium access, the idea of trying to steal those account details may seem quite a good one to cybercriminals.
Whatever the motives are behind the development of malware to hunt for porn-account credentials, it is obvious that users of these kinds of websites are of interest to cybercriminals. This fact is further substantiated when we look at malware aimed at Android users.
Part 2 – Threats to mobile users
When we talk about mobile threats, we mean threats such as malware targeting Android users. And when it comes to malware that uses porn content to lure users into installing a malicious program, the Android threat landscape is much more vivid than that of other desktop.
Android Trojans actively use porn themes, generally distributed from fake porn sites that users are apparently redirected to through advertising on genuine sites. The reason for the uncertainty around dissemination is that redirection depends on many parameters (e.g. the mobile operator, country, device type etc.), which makes it extremely difficult to reconstruct the entire user’s path. In addition, each of the advertising servers in the chain of redirects can change advertising at any time. As a result, it becomes increasingly difficult to track the intruders.
During our research we were able to identify 23 different families of Android malware that are heavily using porn. They belong to five major types: clickers (WAP-subscription malware), banking Trojans, ransomware, rooting Trojans, premium SMS malware, fake porn subscriptions and one more type, which we failed to attribute to any known group. Given that the total number of Android malware families we’ve got in our collection is 1,024, 23 families that are hiding behind adult content is a fairly low number. However, if we look at the scale at which these malicious apps are distributed, things look very different. In 2017 alone, more than 1.2 million users encountered one of the apps from those 23 families at least once. The number of detection events for the same period was over 4.5 million.
In total, in 2017 around 4.9 million users faced some kind of Android malware, which means that in at least 25.4% of them encountered a piece of malware that somehow uses adult content.
Here is how the distribution of users attacked by different kinds of porn malware looks for 2017:

Fig. 6: The distribution of users who encountered different types of malware disguised as adult content applications.
The chart above gives a clue as to what type of threat users risk encountering when they face an unknown app promising adult content. Below we elaborate on how these examples of malware work.
Clicker/WAP-subscription malware
45.8% of users who encountered any type of porn malware, faced this threat in 2017
The main function of so-called clickers is to open a web page and click on some buttons without the knowledge of the user, with two goals:
- To click on advertising, i.e. to receive money for a shown ad, but not showing it to the user. This is humane in relation to the user, but, due to the fact that the user does not see it, the malware can continuously click on advertising, consuming battery power and generating traffic. In addition, this also represents the theft of money from advertising companies.
- To enable WAP-subscriptions, which leads to direct financial losses for the victim. This functionality is particularly dangerous in countries where pre-paid cellular plans are popular.
At first glance, it is really hard to imagine what is so special about yet another advertising Trojan, since it only clicks on ad links and doesn’t steal anything.
But while doing the analysis of one of such Trojan, we spotted that through clicking it ate more than 100 Mb of mobile traffic, and totally drained the battery in one night! Given that this was only one night, it is easy to imagine what would be the traffic bill of the victim a week or two after infection.
In addition to that, clickers can collect information about the data device – contacts, call history, and coordinates, can crawl web pages using JS-files received from the command server, install applications, and delete incoming SMS. In some cases, they have a modular structure, elements of which are responsible mainly for self-defense and for clicking through sites. The Trojans of the ‘clicker’ type often use the administrator rights of the device to make it difficult to remove them from the OS. And when it comes to older versions of Android, it could be even impossible to do so
A prime example of a clicker appeared recently: Trojan.AndroidOS.Loapi. This is a modular Trojan, the behavior of which depends on additional modules that are downloaded from the attacker’s server. The main functionality of Loapi is to click-jack ads and WAP-subscription web pages. In addition, the Trojan can mine cryptocurrency. Mostly it is distributed under the guise of various useful programs or games, but there have been cases when it was downloaded directly from web pages with porn themes.
Along with Loapi, another five Trojans – Trojan.AndroidOS.Agent.rx, Trojan-SMS.AndroidOS.Gudex, Trojan-Spy.AndroidOS.SmForw.gr, Trojan.AndroidOS.Hiddad.de, Trojan-SMS.AndroidOS.Podec.a – have been hiding within porn apps and video players, stealing users’ data and money by the second.
Bankers and ransomware
30.38% of users who encountered any type of porn malware faced one of these threats in 2017
Bankers and ransomware have also been using porn for their distribution for a long time – mostly under the guise of a specific porn player, which instead of showing porn compromises the security of the attacked device and the devices financials. In general they have the same functionality as other mobile malware, being able to show phishing windows, steal SMS from banks, and so on. However when it comes to the differences between how banking Trojans and ransomware Trojans utilize porn content, it is easy to see that while banking Trojans mostly use porn websites to distribute themselves, or just present themselves as a specific video player needed to launch an adult video, ransomware often present itself as a legitimate porn app.
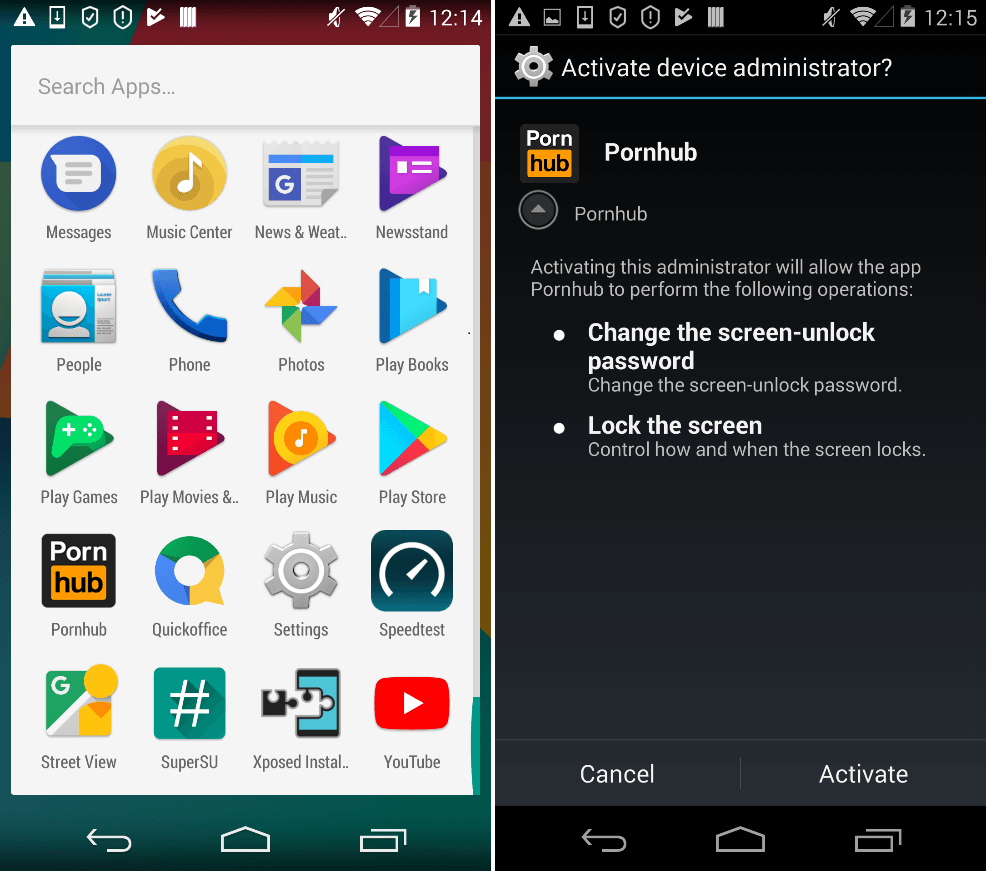
Fig. 9: Example of ransomware app disguised as the legitimate PornHub application. Once installed it locks the device.
In many cases they also use scareware tactics. They lock the screen of the device and show a message stating that illegal content (usually child porn) has been detected on the device, and the device has been locked. In order to unlock the device, the victim has to pay a ransom. This message usually comes with screenshots from actual child porn videos.
Recently, we’ve seen two major ransomware families utilizing these tactics: Svpeng and Small. While Small targets apparently live mostly in Russia and neighboring countries, Svpeng has been targeting U.S. citizens in the first place, showing them a message allegedly from the Federal Bureau of Investigation (FBI). This is confirmed by our telemetry – the vast majority of users (more than 95%) who encountered this malicious app, were U.S. based.
The scariest thing about mobile ransomware is that these Trojans change (or set) the device PIN code to random, so even if the user can delete the Trojan, the phone will remain locked.
Rooting malware
22.38% of users faced this threat in 2017
Continuing the theme of dangerous Trojans – rooting malware has also been seen actively using porn topics for distribution. Once installed on the victim’s device, it may exploit vulnerabilities in Android and practically get ‘god mode’: the capability to access any data on the user’s device, silently install any applications and get direct remote access. The most active, according to the Kaspersky Lab investigation are two families:
- Trojan.AndroidOS.Ztorg – consisting of encrypted modules that use exploits to get root rights on the device, flock to system folders and annoy the user with ads.
- Trojan.AndroidOS.Iop – in general, the same rooter as previously mentioned.

Fig. 11: Example of rooting malware Ztorg, disguised as an app with “Everything you want online video collection”.
What is unusual about rooting malware is that such apps are often spread as part of legitimate applications. Cybercriminals just pick a porn app, add malicious code to it and distribute it as if it were legitimate.
Porn with a subscription and other premium SMS Trojans
2.81% of users who encountered any type of porn malware faced this threat in 2017
These primitive Trojans only know how to send SMS or make calls to paid numbers in order to access the porn site – even though in reality the content of the site is usually available without payment. During the period from 2014 till 2016 there were a lot of SMS-Trojans, most of which were distributed under enticing porn names such as PornoVideo.apk, XXXVideo.apk, XXXPORN.apk, PornXXXVideo.apk, Porevo.apk, Znoynye_temnokozhie_lesbiyanki.apk, Trah_v_bane.apk, Kamasutra_3D.apk, and Russkoe_analnoe_porno.apk.
Android SMS Trojans started with Trojan-SMS.AndroidOS.FakePlayer.a. Active since 2012, this Trojan has still not acquired new functionality and continues to spread under the guise of a video player, often with the ‘pornoplayer’ name. Another example that we found – Trojan-SMS.AndroidOS.Erop.a was being distributed under the guise of a porn player, usually with names like ‘xxx_porno_player'[RU1] . While a further one – Trojan-SMS.AndroidOS.Agent.abi was distributed under the name AdobeFlash from sites with porn themes.
The number of slightly more developed SMS Trojans has intensified recently, despite being originally detected by Kaspersky Lab experts as early as 2012. The Trojan-SMS.AndroidOS.Vidro, not-a-virus: RiskTool.AndroidOS.SMSreg.mq, and Trojan-SMS.AndroidOS.Skanik.a trio is distributed under the guise of porn applications from porn sites. They refuse to work without a SIM-card, since the main purpose of the applications is to send a paid SMS (and remove the SMS reply with cost information from the mobile operator), and only then to open the porn video site.
The most lucrative examples of this type of malware are Trojan.AndroidOS.Pawen.a and its development: Trojan.AndroidOS.Agent.gp, which can make calls to paid numbers and squander their victims’ budgets. An interesting feature is that the application icon is absent, so it’s rather difficult to find it, as well as to remove it because the app uses the device’s administrator rights.
Despite its primitiveness and old-fashioned approach, Trojan SMS have been around for years. At some point their number started to decline steadily, due to range of anti-fraud measures enabled by cellular companies. However, these Trojans are still around: according to Kaspersky Lab telemetry, in 2017 many thousands of users around the world were protected by our product against this type of malware pretending to be porn apps.
Mysterious Soceng
To finish the story of Android malware, it is worth mentioning an interesting Trojan that does not fall into any of the categories above: Trojan.AndroidOS.Soceng.f. The malware is distributed mainly under the guise of games and programs, but also sometimes under the guise of porn. In the sample that was analyzed during the research, we found that after launching it sent an SMS to the victim’s entire phone book, with the text “HEY!!! {user name} Elite has hacked you. Obey or be hacked.” It then deleted all files from the memory card, and overlaid Facebook, Google talk, WhatsApp and MMS applications with its own window.
We couldn’t spot any attempts at financial gain through this malware, apparently its only purpose was to ruin the victims’ digital life. Or it was a test attempt by another yet unknown cybercriminal operation.
That said, you can’t really say the listed above malware is different to any other malware threatening Android users. It is not. What is different and perhaps a bit surprising is how heavily these examples rely on adult content in their infection strategies. Perhaps this is because these strategies have proved effective – something that can be seen clearly if we look at the distribution rate of these porn-powered apps. Another quite interesting finding of this part of our overview is that, apparently, cybercriminals behind Android malware are not very interested in stealing credentials. At least, we couldn’t identify a malware that is specifically hunting for credentials from porn websites. Instead, Android criminals are using adult content to draw victim into a fraud scheme or to get a ransom.
Nevertheless, given how few porn-related threats we found when looking into PC malware, and how many of them are in the mobile threat landscape, porn is moving to mobile. And that doesn’t contradict the insight from one of the industry leaders, which has spotted significant growth of mobile traffic on their website in 2017.
Part 3 – A peek into the underground
As we mentioned at the beginning of this overview, the idea of looking into how cyberthreats deal with porn came to us when we were poking around on dark web sites to see what is sold there, and eventually spotted porn accounts for sale. This made us look deeper into the details.
For a better understanding of the field, we have analyzed 29 top-rated Tor marketplaces. The list can be easily found on DeepDotWeb, an open Tor site, which contains all the inside information about dark market news – including changes in the list of black markets (since there are constant renovations in structure and the number of illegal stores). The markets’ rating comprises an evaluation of each shop by Tor administrators on criteria for enrollment and reviews, easiness of registration and navigation, vendor bond and commission.
During the research it turned out that of all the marketplaces we found, four offered the most choice: with more than 1,500 offers on sale, while others proposed only limited user data from well-known and less well-known porn sites. Such results, however, were expected, because Tor’s basic aim was originally the sale of drugs, guns and malware.
For the purpose of analysis we choose five major marketplaces with the largest number of sales offerings. In total that gave us 5,239 unique offers to buy one or more accounts to popular porn sites. The actual quantity available was not always clear: sometimes sellers simply do not disclose how many sets of account credentials they’ve got. But based on several examples which actually provided the available number of accounts, we can say that one offer could contain up to 10 thousands accounts.
Based on this information, we’ve created a top five of the most-often sold porn accounts on those underground markets (number of offers in descending order):
- Naughty America (2,575 sales offers)
- Brazzers (1,228 sales offers)
- Mofos (789 sales offers)
- Reality Kings (294 sales offers)
- Pornhub (153 sales offers)
To be clear: this ranking doesn’t mean that this particular website or users of this websites are more vulnerable to cyberattacks and that is why there are so many offers on the market. What this list could potentially show is the popularity of these websites among the audience of dark web markets.
Speaking of the audience. Question here: why would someone go to buy a porn account on the dark web if they are available from legitimate sources in practically any quantity? We think there are two main reasons for that:
The first one is of course the price. Based on our observations, an average subscription to a popular official site (such as Brazzers, RealityKings, etc.) is as follows:
- Annual unlimited access (no ads): one payment of $119.99 or $9.99 / month
- Three months of unlimited use: one payment of $59.99 or $ 19.99 / month
- One month of unlimited use: one payment of $29.99 or $29.99 / month
- 1-2 days of trial use: $1.00 / day
Not a lot of money in general; nevertheless on the dark web those same accounts appear at a significantly lower price. We’ve seen multiple offerings of unlimited access for a price as low as 10$. So, economically, the purchase of a stolen account on the dark market totally makes sense.
The other possible reason for the popularity of porn accounts on the dark market is anonymity. Although some legal websites offer customers a chance to buy a subscription more-or-less anonymously, on the dark market you can buy things via cryptocurrencies and the purchase will not eventually appear in your credit card history. Even though nowadays porn is becoming ever more mainstream, in general the perception of this type of content is not always neutral.
That said, purchasing this type of goods on the dark web brings certain risks for the customer. First of all, doing so is illegal, given that all or most of the accounts are stolen from other users or the websites themselves. Second, the latter also casts doubt on the very validity of the account purchased. Sooner or later, the user whose account has been stolen will understand that and report it to the vendor and the compromised account will be blocked. The situation is the same when website owners identify a breach. Compromised accounts are being blocked almost immediately after that. In other words, clients of dark net markets risk paying money for nothing, because although there are some exceptions, in the vast majority of cases we’ve seen, dark market traders do not offer a refund option. The ability to buy an account at a significantly lower than official price is what the client gets in exchange for the risk that they are paying for a blocked account.
Conclusion and Recommendations
As our overview has shown, adult content serves as a tool for cybercriminals to lure victims into fraudulent schemes involving phishing, PC and Android malware. The outcome of such involvement is loss of financial data or even direct money loss and compromised privacy. It would be fair to say that the very same consequences come from any other type of malicious attack, whether they use adult content or not. The difference is that, in general, victims of porn malware, especially the most severe scareware types of it, are unlikely to report the crime to anyone, because they would have to admit they were looking for or watching porn. As we said earlier, the latter is not necessary perceived as something that it is OK to be proud of or even to let others know about. Perhaps this is the reason why criminals use adult content in their schemes so actively. They know that porn by default attracts a lot of users, and that victims of porn-related malware would keep quiet about the incident rather than disclose it.
To prevent any malware or cyber-fraud related troubles when it comes to adult content we strongly recommend users to follow this advice:
- Use only trusted web sites when it comes to adult content. Cybercriminals often set up fake porn sites for the single reason of infecting victims with malware
- Do not install Android applications from unknown sources, even if they promise you access to the content you were looking for. Instead use official applications from official sources, like Google Play.
- Avoid purchasing hacked accounts to porn websites. This is illegal and such accounts may already be blocked by the time you buy them.
- Use reliable internet security solution capable of protecting all your devices from any kind of cyberthreats.
 porn
porn