On June 19, Opera Software, the developer of one of the most popular Internet browsers- mainly used on mobile devices, admitted that the company’s internal network infrastructure was attacked and an Opera code signing certificate was stolen.
Here is a quote from the Opera’s official statement:
“The current evidence suggests a limited impact. The attackers were able to obtain at least one old and expired Opera code signing certificate, which they have used to sign some malware. This has allowed them to distribute malicious software which incorrectly appears to have been published by Opera Software, or appears to be the Opera browser.
It is possible that a few thousand Windows users who were using Opera between 01.00 and 01.36 UTC on June 19th may automatically have received and installed the malicious software. To be on the safe side, we will roll out a new version of Opera which will use a new code signing certificate.”
There is a link to Virustotal given with the description of the malware that the attackers seem to have signed with an Opera certificate, a Trojan of the Tepfer family, for stealing usernames and passwords.
Evidently, “a few thousand users” may be considered as “a limited impact;” the actual number of victims is yet unknown. The scale of the Adobe’s disaster in late 2012 was far greater. In this incident, the hackers managed to sign 5100 malicious programs with the stolen certificate. Nevertheless, the Opera incident is definitely an emergency case, if not due to the actual consequences, then due to the scale of reputational damage.
For in such cases users cannot help but wonder what measures are taken to protect important data and why they prove insufficient.
Is it possible to completely secure the company’s data against any thieves ever? Absolute protection is hardly attainable, but the chances of successful intrusions can and must be minimized. What does it take? All it takes is the will of the company’s administration to set up an adequate security system.
What should that system include? You need to evaluate the main attack vectors. The attackers may try to intrude remotely by utilizing exploits of software vulnerabilities. You can reduce the likelihood of such an attack by providing the regular and centralized updates of software and system files. But you should also take zero-day exploits into consideration. Hence, you are going to need the automatic means of blocking malware and unauthorized legitimate programs, such as the technology of Automatic Exploit Prevention.
In addition, critical data must be isolated: the hacked computer of an employee not working in the accounting department should not result in financial records being stolen.
Can attackers try and hack a personal computer or a mobile device of any of the employees of the company to reach the data? Certainly- they can and have done it many times. To prevent this, you need to provide multilayered antivirus protection with the maximum possible limitations on running unauthorized software, including legitimate programs.
The most popular software used on a variety of devices all over the world (office programs, Java, Adobe Reader, Adobe Flash) is unfortunately known to be the most vulnerable. In addition, users never hurry to update and attackers frequently try cracking these programs. So what’s to be done? We know the white listing option (the Default Deny mode) is not very popular with IT pros, but they would hardly deny that this approach is extremely effective.
Mobile devices may also become the breach that attackers would try to get through. When a company enables the BYOD principle, the most urgent thing to do is separate corporate and personal data. Besides that, it is necessary to prevent users’ programs installed on personal devices from accessing critical data in any segment of the corporate network and making unauthorized changes to them.
In addition to the access control, the critical data can and must be encrypted lest it proves to be valuable to attackers when they manage to get ahold of it. If the stolen Opera certificate had been stored in an encrypted form, it would have been impossible to sign malicious software with it.
How do you implement these general guidelines in practice?
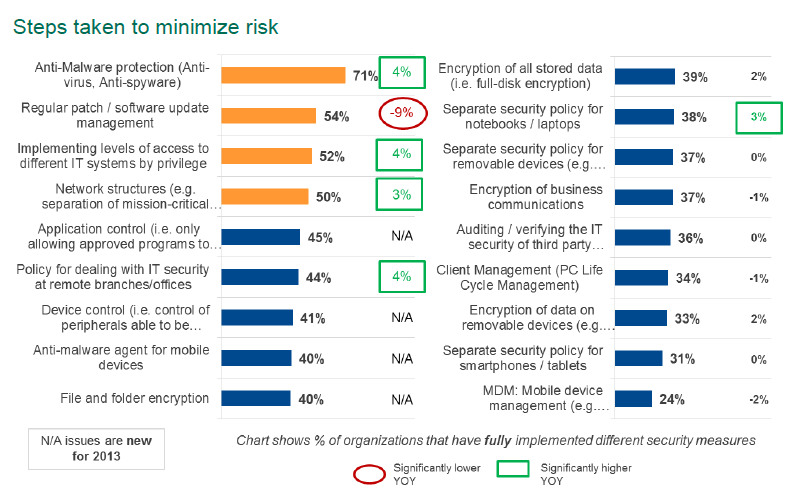
We have recently published a new study – Global Corporate IT Security Risks: 2013. I would like to draw your attention to the chart below, because it provides a clear answer regarding the measures needed to reduce risks. We interviewed almost three thousand IT professionals from companies all over the world.
You see that only 71% of respondents fully implemented protection against viruses and other malicious software in their systems (they reasonably believe that applying at least the basic principles is necessary). Just a little less than a half of respondents set up regular software updates and restricted the access to different systems, and only half of the IT pros separated the segments of their corporate networks to isolate the critical data from all the rest.
The control of running applications, the control of devices within the corporate network and the data encryption were implemented by less than a half of the respondents. The means of controlling mobile devices were introduced by less than 25% of the respondents.
At the same time, the recent survey by Ovum states that about 75% of the employees of commercial companies in the emerging markets use personal devices. In the developed markets this quantity is much lower – 44%, but by all means the global average of only 20% of employees signed the documents regulating the use of personal devices in their workplaces. In the U.S. and India their quantity nearly reaches 50%, yet the problem is still neglected by IT departments everywhere.
Any system is as reliable as its weakest part. If there is a vulnerable spot in the defensive lines, sooner or later someone will try to take advantage of it. Our technologies and solutions are intended to provide a comprehensive and equally distributed defense of the whole corporate infrastructure to minimize its vulnerability to external threats that may result, as with Opera, in severe reputational damage.
 corporate security
corporate security