Data leaks have become alarmingly common of late. Cybercriminals use all kinds of tricks to gain access to databases and the records stored there. The most logical way to secure databases would be to use encryption, but this is often impractical. After all, the more often a service needs to access a database, the slower it will respond. And if that database is also encrypted, the response time may be even higher. And that’s not all — as was shown in a 2009 study of the main problems with database encryption. Fast forward to early June of this year, however, and the developers of the MongoDB database management system (DBMS) announced a breakthrough in their latest release: support for Queryable Encryption. Queryable Encryption is a way of storing data in encrypted form with acceptable query response times.
Real-world performance
The brains behind the new technology belong to Seny Kamara, Associate Professor of Computer Science at Brown University (in Providence, Rhode Island State, in the U.S.A.) and his longtime collaborator Tarik Moataz, who have worked extensively on the application of reliable encryption in the real world. At the time Aroki Systems was acquired by MongoDB, their research was focused on developing a reliable method to protect databases without sacrificing performance.
It’s no secret that database developers and operators have always prioritized speed and reliability over protection. For encryption experts, on the other hand, ensuring the impossibility of data decryption is the priority, while convenience plays second fiddle. Because of this, past solutions have seesawed between encrypting data either quickly but unreliably, or securely but painfully slowly. Kamara and Moataz combine a scientific approach (that is, strong encryption) with the needs of real-life users (that is, fast response times). Here’s how it looks in MongoDB:
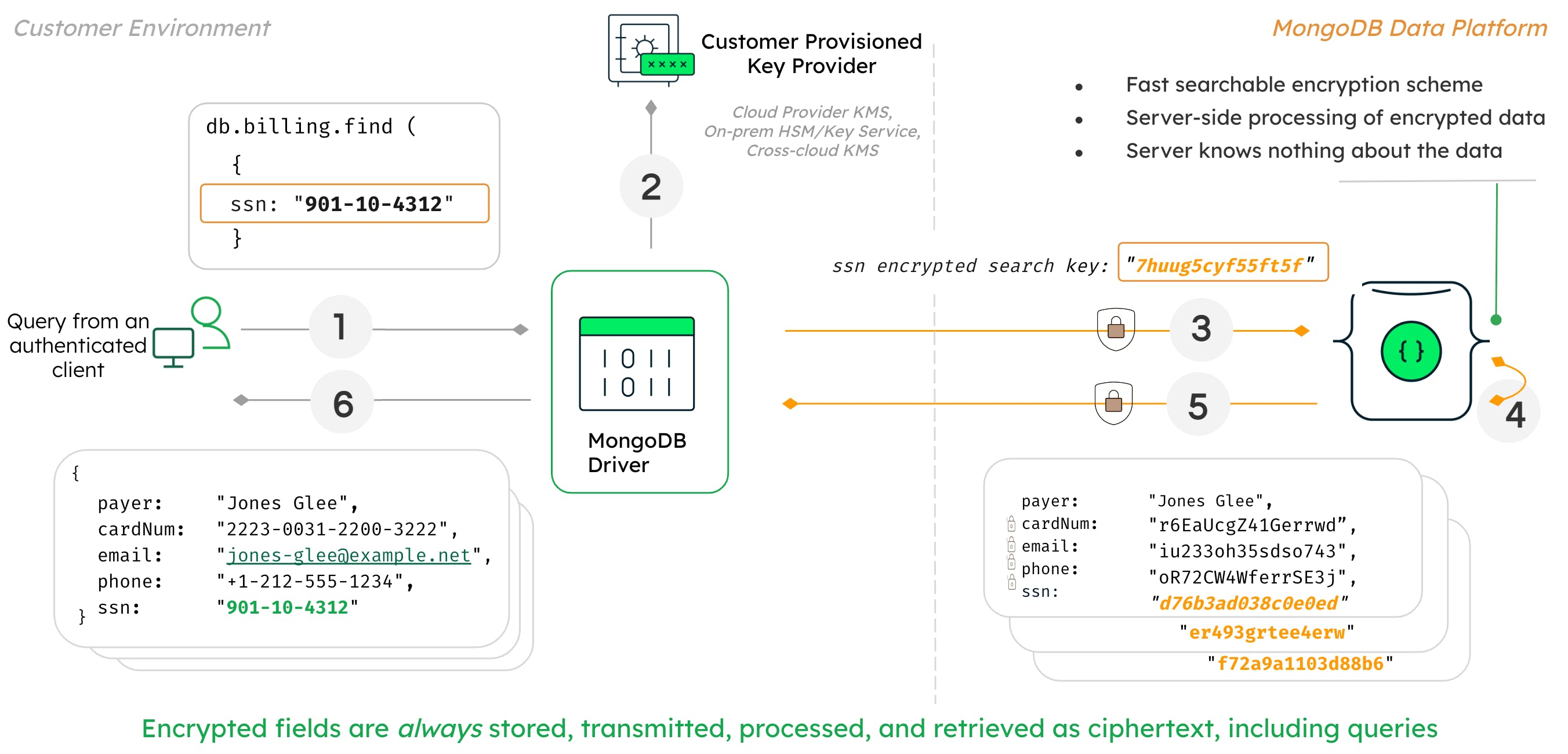
System for encrypted database access. Source.
Suppose we need to retrieve data about a user based on their social security number. We take the SSN, encrypt it, and send it in encrypted form as part of the query to the database. In response, the database returns other information about the user: name, phone number, email address. Note that no decryption at all takes place on the database side. The query contains only encrypted data, as does the response. Importantly, the secret keys for decrypting the data are stored neither on the database server, nor on the client. This means that even if attackers gain access to the database, the users’ data is still safe.
A bright future — hopefully
If this is such a major issue, you ask, why have there been no database encryption solutions before? Well, there have been some, and they’ve been around for quite a while. But these were mostly performance-oriented, with encryption as a sideshow — for example, to demonstrate to regulators that protection had not been totally neglected. As such, existing solutions have a number of vulnerabilities. In particular, it was found that if an entire CryptDB-encrypted database were compromised, most of its contents could be decrypted. In other words, such encryption is a mild nuisance to hackers, nothing more. This solution, like others, has never been formally audited to determine the strength of its encryption method.
This happens to be a common problem of practical cryptography — when the developers of an information system feel compelled to craft something in-house that meets their particular data encryption requirements. This “something” then often turns out to be vulnerable because the development process failed to take into account the latest scientific research. And the vulnerabilities are usually such that their presence can be determined only by analyzing the algorithm and predicting its operation. The upshot is that your data is theoretically encrypted, but in practice has long been up for sale on the underground market.
In terms of functionality, Queryable Encryption in MongoDB lies at the intersection of science and business — apparently a first. It remains only for the new encryption method to pass a formal audit to prove the security of the data (preliminary feedback is overwhelmingly positive). Real users should also provide their input: does the encryption interfere with performance? And it would be nice to see the appearance a rival system based on similar principles: healthy competition is, after all, the key to progress.
So, what next?….
In companies that care about client data, almost everything is encrypted anyway: backups, email, communications between devices and the corporate network. So databases may well be the last stronghold of important information stored in plain text. Yes, such databases have maximum protection against outside penetration, but they’re still vulnerable. Let’s hope, then, that the successful rollout of encrypted database management systems will help prevent wholesale theft of user data. Sure, it will still be possible to attack individual users; or to harvest open data, which by definition is available online. But to steal a hundred million accounts all at once? Advances in database encryption could render such incidents extremely unlikely.
 leaks
leaks

 Tips
Tips