(Post updated on August 29; Instagram has introduced applying for verification)
Instagram is not just the second most popular social network in the world. It’s also a means of income for numerous photo bloggers, models, and other Internet celebrities. Eye-catching accounts with many thousands of followers are of interest not only to fans, but also cybercriminals. If such an account is stolen, the consequences can be nasty. But how exactly do Instagram accounts get hijacked, and how can you avoid yours getting snared?
Hijack method No. 1: Fake verification
You’ve probably noticed a blue tick next to some Instagram accounts, a . Until very recently, these status symbols were worn by accounts belonging to celebrities, large companies, and popular bloggers. The sacred badge is especially important for accounts with large audiences because it adds prestige and distinguishes these accounts from fake ones. Getting hold of a badge wasn’t that easy: There was no application form or “badge store”— the social network decided for itself who to award them to.
However, Instagram recently changed its policy regarding verification, and now you can request verification from the app (to do that, go to Settings -> Request Verification) and get the badge if your account meets the necessary criteria.
This change was implemented quite recently — on August 28, 2018 — and many users don’t know exactly how to get the cherished blue tick. Scammers are, of course, exploiting that, creating sites that masquerade as Instagram help center pages and request details from Instagram users such as their username, password, e-mail address, full name, and date of birth — all for the promise of a badge.
Having entered this data, the unsuspecting user is told to wait 24 hours for a decision, and not to change their account settings during this period. The information goes straight to the attackers, while the user just sits and waits, unaware that their account is now compromised.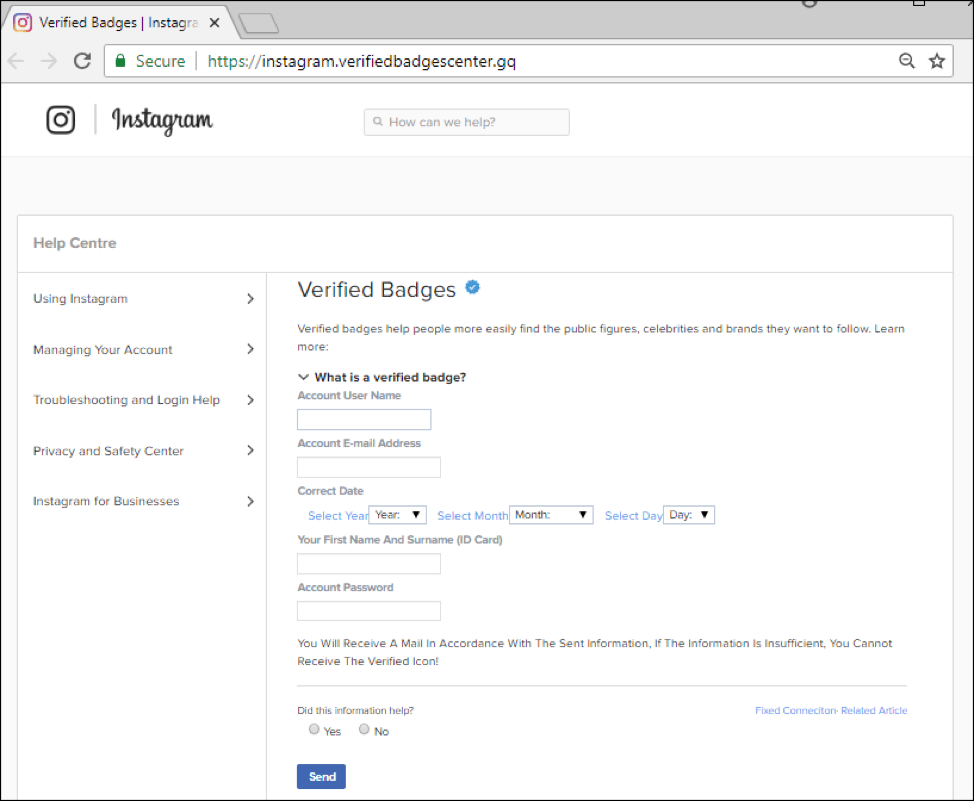
This method can also be used to get personal information belonging to the victim, which can help the cybercriminals bypass two-factor authentication processes. To do this, criminals display a message saying that the support service may contact the account owner to clarify their details. When the “support service” does make contact, it’s the scammers themselves asking for an SMS code or other security information. They might also send a fake support service message requesting information supposedly needed for verification, which they can use when dealing with the real support service behind the account owner’s back (the data requested might include, for example, a photo or other data that the genuine service might ask for).
Hijack method No. 2: Plain old phishing
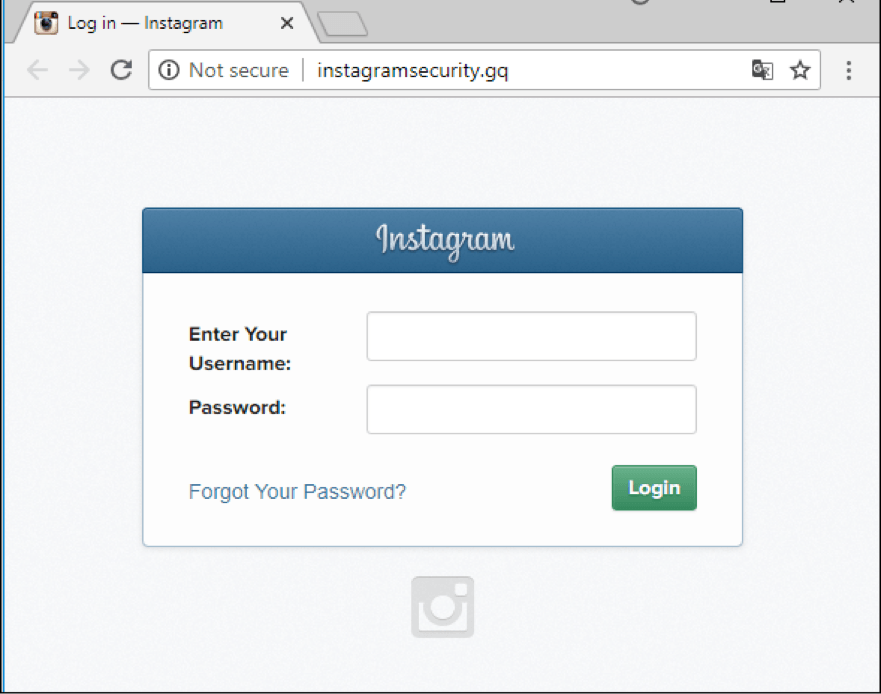
Scammers are also continuing to use common phishing techniques to lure victims to a fake login or password reset page. For example, they might send a scary message saying that a user’s account has been hacked or that their login credentials need updating, or simply offer to “rate a photo” which supposedly requires the user to login to the social network.
With more than a billion users worldwide, Instagram has long been a target of choice for all kinds of scammers. Having hijacked an account, they get access to the user’s personal information and messages. Not only that, the account can be used to spread spam, phishing, and malicious content. Quite often, on taking possession of an account, the attackers change the handle, profile photo, and e-mail address and phone number to which it is linked. That makes it nearly impossible for the true owner to restore access to their Instagram account.
How to protect against Instagram hijacking
As always, prevention is better than cure — especially if a cure is next to impossible. By observing these simple rules, you can stay safe:
- Don’t click on suspicious links.
- Always check the address bar for the URL of the Web page. If instead of Instagram.com it says something like 1stogram.com or instagram.security-settings.com, get out of there quick, and don’t even think about entering any personal data.
- Use the official social network app from the official store — such as Google Play for Android, or App Store for iOS.
- Don’t use account login credentials for authentication on third-party services and apps.
- Use a reliable security solution that sifts out suspicious messages and blocks phishing pages. Kaspersky Internet Security can handle that task for you.
Lastly, check out our post on how to configure Instagram properly. It’s a must-read for Instagram users.
 Instagram
Instagram