Almost a year ago, we wrote about a classic phishing scheme aimed at unlinking a stolen iPhone from the victim’s Apple ID account. The purpose was to resell the phone not for spare parts, but as a full-fledged second-hand smartphone that’s way more valuable.
Last time, fortune favored the scammers, who were able to phish out the iCloud username and password they needed. This time around, we’ll investigate a more complex scheme for extracting the confidential data of phone-theft victims, including its Plan B, which is almost bound to catch anyone who manages to dodge Plan A.
Step 1: iPhone theft
It all began ordinarily enough, with my colleague Anna leaving her phone on a lounge chair in the park. When she returned 20 minutes later, the phone was gone. No one saw anything, and when she called the number, it was not available. Without hesitation, Anna activated Lost Mode in Find My iPhone app using a friend’s smartphone, giving an additional number that the finder could reach her on.
A day later, hope of getting a call from the finder had fizzled, and the phone, judging by the info from the Find My iPhone, remained offline. She steeled herself for the Erase iPhone option.
This useful feature wipes all data from the phone and renders it useless as soon as it connects to the Internet. But it seems that the thief was either an iPhone wizard or, more likely, engaged an expert in the dark art of unlinking Apple devices from their owners’ iCloud accounts. Either way, from the moment it was lost, the phone didn’t go online for even a second, so wiping and bricking it wasn’t an option.
Incidentally, although the device was protected by Touch ID, access to Wi-Fi and mobile data can be turned off without unlocking the phone. All it takes is a swipe up on the lock screen to get to the Control Center, where you can turn on Airplane Mode.
During the two days the phone’s SIM card remained unblocked, the scammers had time to use it to find out Anna’s phone number. On day three, the old SIM was blocked by the telephone company, and a new SIM card, with the same number, was inserted into Anna’s new phone.
Step 2: Phishing SMS
On day four, the scammers set about making the stolen iPhone more marketable by trying to unlink it from Anna’s Apple ID. To begin with, they made a few calls from a phone number seemingly from the US. Any attempt to pick up at the other end was met with silence.
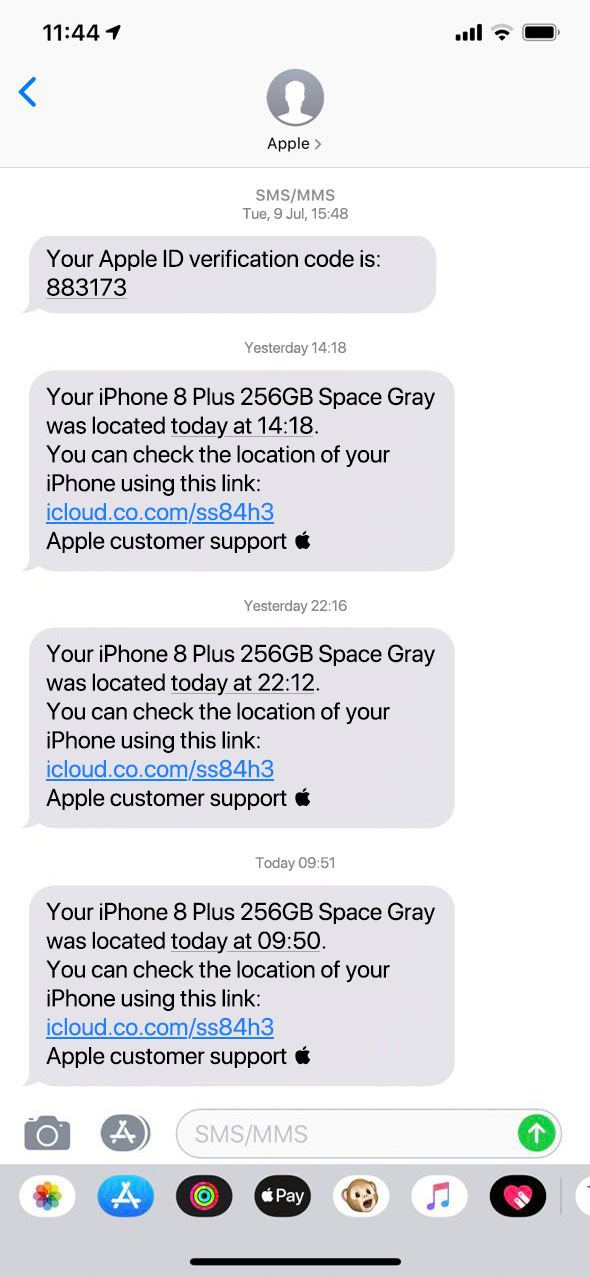
The purpose of the calls was to make sure that the SIM was reissued and the number was active again. Immediately after the last call, Anna received a text message that her stolen phone had gone online and been located.
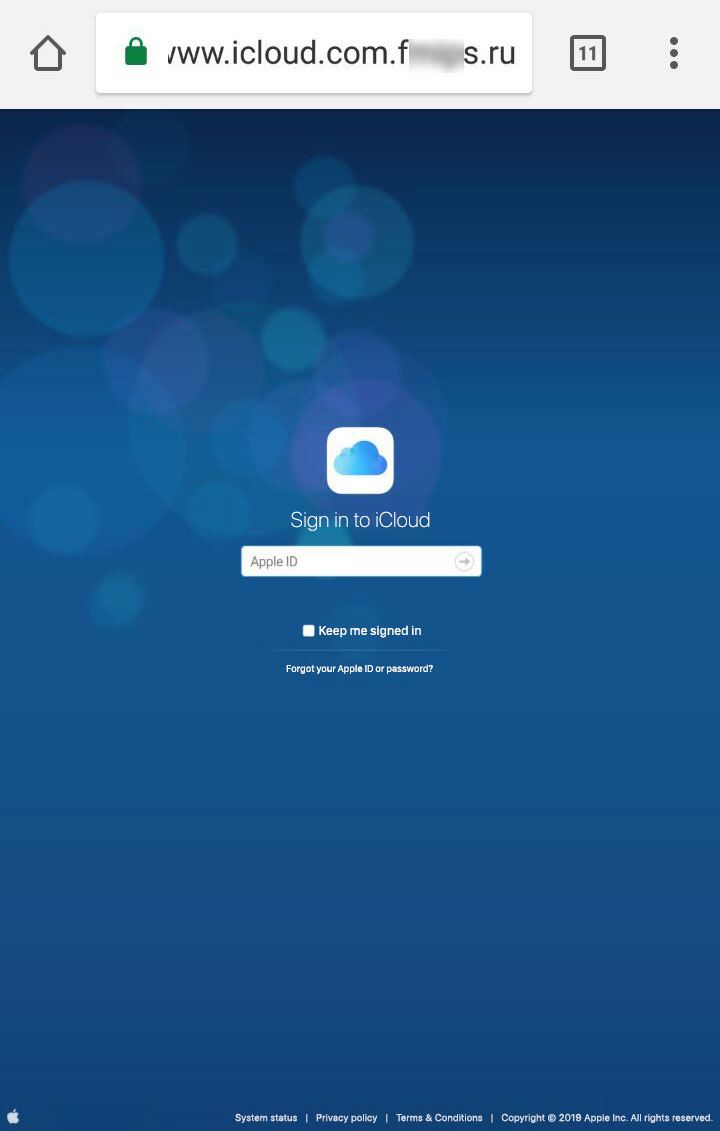
The phishing message was smart. So that Anna did not smell a rat, the message was sent from a service able to substitute “Apple” as the sender. The phishing link in the message also looked very plausible. Entered manually, the URL leads to a nonexistent page. But clicking the link resulted in redirection to a phishing site. What’s the secret?
In fact, the domain icloud.co.com does exist — and belongs to Apple — but the link in the text pointed to icIoud.co.com — that’s a capital I, not a lowercase L. Upon clicking it, Anna was redirected to a convincing phishing page, where she was prompted to enter her Apple ID and password to search for the missing phone. A careful look at the page would reveal that the address has changed and therefore entering data is not safe.
Interestingly, the page looks different depending on the device and browser viewing it. Most likely, the attackers use this site for various phishing schemes tailored for different platforms.
Anna did not fill out the phishing form because she immediately realized the service was fake. What’s more, her phone was still offline in the Find My iPhone app, as it had been ever since the theft.
That could have been the end of it, but without unlinking the phone from Anna’s Apple ID, the thieves weren’t going to get as much money from the resale. So they switched to Plan B.
Step 3: Phone call from a “friend”
Three hours after the phishing message was sent, when it was clear that Anna was not going to enter her account details on a phishing page, she received a voice call. The caller introduced himself as a service center employee, named the precise model and color of the phone, and then asked if she had lost it. He went on to say that the phone was at the center, located in a shopping mall on the other side of town, and invited Anna to come and collect it.
With the phishing attempt still fresh in her mind, Anna asked a few reasonable questions about how he had got hold of the phone and her number, testing whether the caller himself was a scammer. In response, the stranger answered curtly: “If you don’t need the phone, don’t come.”
He added that the people who brought the phone to the service center had seemed shady, so he looked it up in the database and saw it was listed as lost. The same (obviously magical) database also contained Anna’s phone number. Long story short, she had an hour to pick up the phone before the finders came back for it.
Let’s pause for a couple of technical details. To learn if a phone is lost, first one needs to turn it on. The phone will then display a notification about the loss with a phone number to contact the owner. Remember, because her old SIM card was stolen with the phone, and a new card was being issued, Anna provided a friend’s number instead of her own. Accordingly, if anyone tried the contact-me number, it would reach out to the number Anna had specified.
Moreover, during the conversation with the alleged service center, Anna checked whether her phone had come online. Seeing that it hadn’t, she informed the caller, to which he nimbly replied that perhaps the phone had already been relinked — to another Apple ID. If we could remove emotions and psychological pressure from the situation, that would be a clear spot-the-scam moment. But let’s see how events unfolded in reality.
Next, the man posing as a service rep told Anna that the store would not hold up other customers for her and that the phone would be returned if and when the other people came for it. He also asked Anna to call if she couldn’t get to the shopping mall in an hour. Then came the kicker: He asked her to bring the original phone packaging and her ID. The trick worked. Taking along some friends for safety’s sake, Anna called a cab and set off on her quest. The mall was 30 minutes away by car, well within the deadline.
On the way, Anna called the “service center” for an update. The man asked her to open the Find My iPhone app and began firing questions about what she saw there, what color ball was next to the phone’s icon, and so on, as if he really was investigating her case.
When Anna said she was nearly there, he asked her to log in to iCloud again and check to see if the device had appeared, and then asked her to press the Remove button and to say whether the warning message contained certain words. Anna pressed the button and reported what the warning message said. The man happily stated that everything was clear: The phone had been unlinked from iCloud, and relinking it required a click to confirm removal, after which it would reconnect.
Anna, of course, did not do this — despite the stressful situation, she remembered that under no circumstances should a phone be unlinked from its owner’s account. So she replied that she would sort it out at the center.
A few minutes later, the scammer called again, armed with the most effective social engineering technique there is. To pressure the victim, he claimed that the finders had come back for the phone, so he had to decide right there and then whether to give them back her phone.
Hearing the typical background noise of a public place, voices asking “Well?” and the scammer saying “Just a second, guys,” while continuing to insist that Anna remove the phone from the cloud, Anna said she was now approaching, and that she had called the police, who were also on the way. The man said he’d hand over all CCTV footage, but he couldn’t keep the customers waiting any longer. He said he was going to give them the phone.
As expected, when she arrived at the shopping mall, Anna found no service center. Moreover, a local police officer later assured her that no such place existed, said that scammers often directed victims to that location, and detailed schemes that were carbon copies of the one tried on Anna.
After that, the scammers didn’t get in touch again, but the phishing messages continued arriving for another few days, evidently in the hope that Anna would buckle and give up her password.
Ultimately, Anna did not get her iPhone back. But didn’t she swallow the scammers’ bait, either. The stolen phone remained tied to her Apple ID with Erase iPhone Mode still activated — as soon as it went online, it would be wiped and “bricked” — so the thieves would have to settle for selling it as spare parts.
What to do if your iPhone is lost or stolen
In conclusion, here are some tips on what to do if your iPhone gets lost or stolen.
- Immediately enable Lost Mode in the Find My iPhone app.
- Contact your service provider to block the SIM card, especially if you did not protect it with a PIN code (by default, PINs are usually either disabled or something simple, like 0000).
- Activate Erase iPhone mode right away if it becomes clear that the phone is not going to be returned to you.
- Remember that SMS messages and, even more so, voice calls can be faked. If the information in the messages does not match what you are seeing in Find My iPhone, someone is probably trying to take you for a ride.
- Check your e-mail for any real Find My iPhone messages. If nothing’s there, any texts you may get about your phone are likely to be fraudulent.
- Enter icloud.com manually (and carefully) in your browser rather than following a link from a text message, and never enter your Apple ID and password on a page that you opened from a link.
- Stay calm. Scammers will likely try to rush you into making a snap decision. That’s a standard trick — do not give in.
- Never, ever remove the lost phone from the Find My iPhone app, no matter how hard the scammers pressure you to.
 iphone
iphone






 Tips
Tips