Streaming services have become the cornerstone of Gen Z’s entertainment habits, transforming how this tech-savvy and culturally diverse generation consumes media. Platforms like Netflix, Amazon Prime Video, Disney+, Apple TV Plus and HBO Max have reshaped movies, series, and anime watching into an immersive, on-demand experience that caters to Gen Z’s love of personalized content and global storytelling. For many Zoomers, streaming is more than a pastime — it’s a way of life, providing a connection to the characters, worlds and fandoms that define their identity.
Known for binge-watching, this generation often spends hours diving into long-running series or eagerly awaiting the release of their favorite films. According to recent studies, Gen Z not only spends more on streaming platforms than any other generation but also actively participates in online fandoms, sharing clips, memes and fan theories across social media. However, this high level of engagement also makes them prime targets for cyberthreats, as attackers leverage fake streaming links, phishing emails and malware-ridden downloads disguised as exclusive content. In this report, we uncover how cybercriminals exploit these behaviors, what makes these beloved titles such enticing targets and how Gen Z can protect themselves while enjoying their favorite content.
Methodology
To understand the cyber landscape around Gen Z’s favorite films, series, anime and streaming platforms, Kaspersky researchers conducted an in-depth analysis using the most popular titles as keywords. This allowed experts to identify the distribution of malicious files and potentially unwanted software associated with them, as well as the number of users impacted by these threats.
The analysis was based on anonymized threat statistics from Kaspersky Security Network (KSN), examining malicious and potentially unwanted application files detected between April 1, 2024, and March 31, 2025. Additionally, researchers analyzed phishing pages and scams using the names of these titles and streaming platforms to lure users, uncovering various tactics employed by cybercriminals to deceive fans and exploit their enthusiasm for digital entertainment.
Our Digital Footprint Intelligence team analyzed records that included compromised credentials later used to access popular streaming services such as Netflix, Amazon Prime Video, HBO Max and Disney+. While these services themselves are not direct targets, their accounts may end up in the hands of cybercriminals as part of broader credential theft campaigns.
The analysis included the following popular entries for each category:
- Streaming platforms: Netflix, Amazon Prime Video, Disney+, Apple TV Plus and HBO Max.
- Films and series: Deadpool & Wolverine, Shrek, Twilight, Inside Out 2 and Stranger Things.
- Anime: Jujutsu Kaisen, Attack on Titan, Demon Slayer, One Piece and Naruto.
Key findings
- Throughout the reported period, Kaspersky detected 96,288 attempted attacks disguised as the names of five major streaming platforms: Netflix, Amazon Prime Video, Disney+, Apple TV Plus and HBO Max.
- Netflix was the most exploited streaming platform, accounting for 85,679 attempted attacks, with its wide appeal and global availability making it a prime target for cybercriminals.
- The DFI analysis revealed that the total number of detected leaked accounts for streaming services in 2024 counts for 7,035,236.
- Anime proved to be a much more popular target than films and series, with a total of 251,931 attacks disguised as popular anime titles detected throughout the reported period.
- The top targeted anime titles were Naruto, Demon Slayer and Attack on Titan, in descending order.
From Netflix to HBO Max: The cyber risks around the streaming culture
Streaming platforms have become an essential part of Gen Z’s daily lives, offering endless entertainment at their fingertips. However, this cultural shift has also created fertile ground for cybercriminals. Throughout the reported period, Kaspersky detected 96,288 attempts to distribute malicious or unwanted files disguised as the names of five major streaming platforms: Netflix, Amazon Prime Video, Disney+, Apple TV Plus and HBO Max. Such attempts show consistent popularity across all 12 months, as can be seen below.

Attempts to attack users through malicious or unwanted files disguised as streaming platforms throughout the reported period
The steady interest in exploiting streaming platforms could be attributed to their constant relevance in digital culture. Unlike seasonal trends, streaming platforms offer a continuous flow of content, from highly anticipated premieres to hidden gems that viewers discover months or even years after release. The evergreen nature of streaming keeps these platforms at the forefront of user engagement, making them an attractive and reliable bait for cybercriminals.
Another factor is the increasing reliance on streaming services as a primary entertainment source. Whether it’s binge-watching series, catching up on the latest film or revisiting childhood favorites, streaming platforms cater to a wide demographic. This constant demand provides cybercriminals with a steady pool of potential victims, ensuring their tactics remain effective throughout the year.
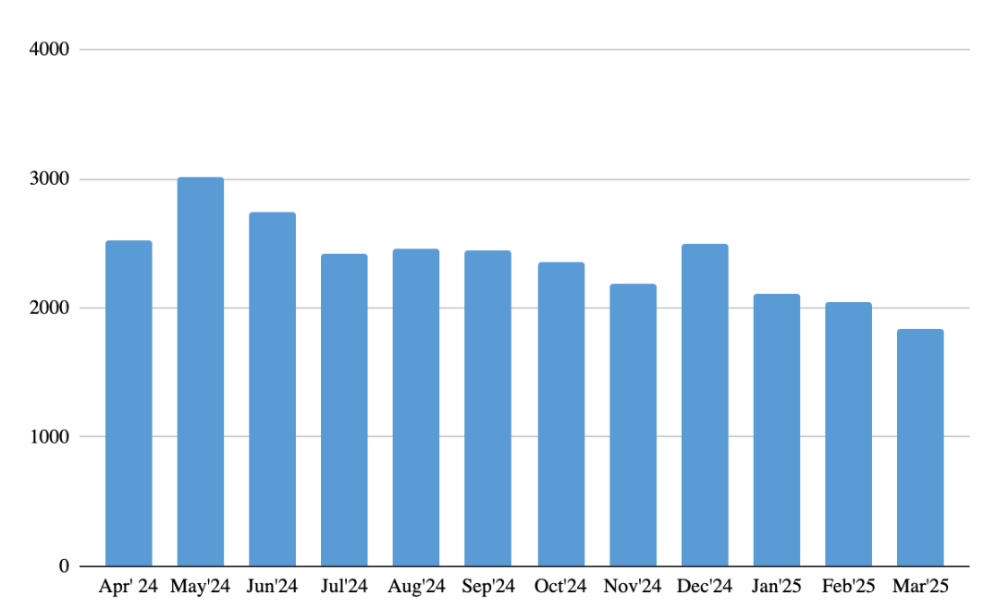
The number of unique users affected by malicious or unwanted files disguised as streaming platforms throughout the reported period
Throughout the reported period, a total of 18,198 users worldwide became targets of attempts to distribute malicious or unwanted files disguised as streaming platforms like Netflix, Amazon Prime Video, Disney+, Apple TV Plus and HBO Max.
As with the number of attack attempts, the number of affected users remained relatively consistent month to month, reflecting the ongoing appeal of streaming platforms as bait. However, a notable spike occurred in May 2024, when 3,000 users attempted to download such files representing a 20% increase compared to the monthly average for the rest of the reported period.
The top-3 exploited streaming platforms by the number of attempted attacks throughout the reported period
| Title | The number of attack attempts |
| Netflix | 85,679 |
| Amazon Prime Video | 6,865 |
| Disney+ | 1,675 |
When examining which streaming services were most frequently used by cybercriminals as bait throughout the reported period, Netflix emerged as the overwhelming leader, accounting for the vast majority of attack attempts. Specifically, Kaspersky security solutions detected 85,679 attempted attacks using this streaming platform as a lure. It’s no surprise that cybercriminals focus their efforts here: the platform’s wide-ranging content, including binge-worthy series, exclusive releases, and viral hits like “Stranger Things,” ensure a constant stream of engagement. Additionally, Netflix’s global availability makes it a universal target, providing attackers with a broad pool of potential victims regardless of geography.
Amazon Prime Video ranks second, though with significantly fewer attack attempts compared to Netflix — 6,865. Disney+ follows in third place, with around 1,675 attempted attacks. This disparity is likely linked to the platforms’ differing levels of popularity with Netflix being the most popular streaming platform in the world.
The top-10 cyberthreats using streaming platforms as a lure throughout the reported period
During the reported period, cybercriminals used a variety of cyberthreats disguised as popular streaming platforms.
| Threat | Attempted attacks |
| RiskTool | 74,292 |
| Trojan | 7,987 |
| HackTool | 3,148 |
| Downloader | 3,002 |
| Adware | 2,135 |
| Dangerous Object | 1,799 |
| Trojan-PSW | 1,035 |
| Trojan Spy | 973 |
| Trojan-Downloader | 397 |
| Trojan-SMS | 366 |
RiskTools dominate the list, accounting for nearly 80% of all recorded attacks. These are applications that can be exploited to harm users. For example, they may disable security settings, collect system data or serve as gateways for other malware. The high prevalence of RiskTools underscores how cybercriminals can use them as a foundation for further attacks.
Furthermore, cybercriminals also used various types of trojans. Trojans are classic malware disguised as legitimate files, tricking users into downloading them. Once activated, they can steal sensitive data, install additional malware or give attackers remote control over a device. For instance, Trojan-PSWs (Password Stealing Ware) are specifically designed to harvest login credentials, such as passwords and usernames. When disguised as streaming platform files, they can jeopardize users’ accounts, compromising not only personal information but also payment details linked to these platforms.
Spam, scams and streaming
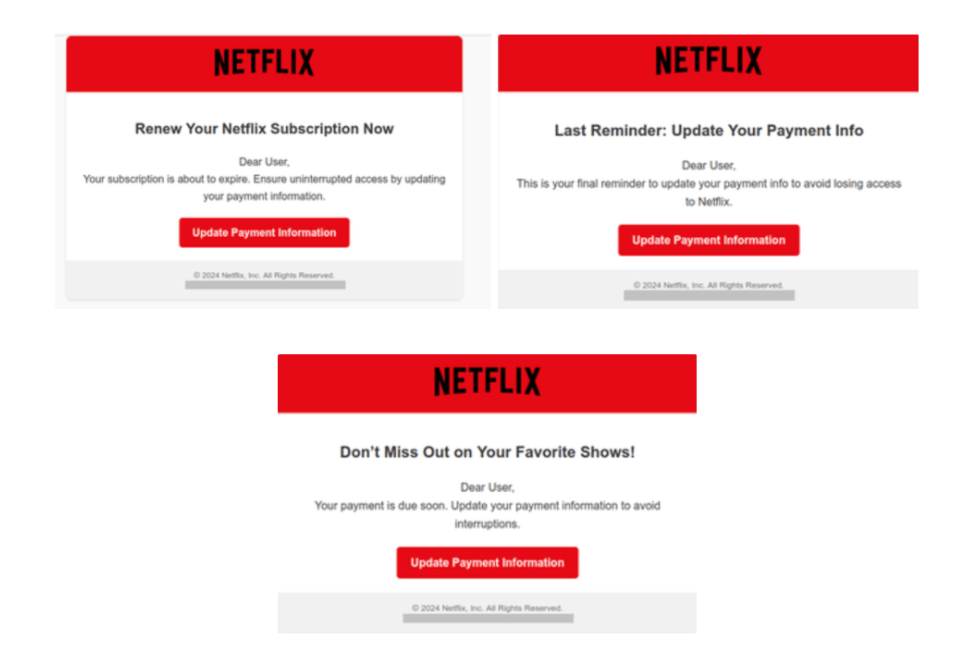
The overwhelming majority of phishing and spam examples detected as part of our research were carried out under the guise of Netflix, cementing its position as the primary target for cybercriminals. These scams often took the form of emails with urgent sounding subject lines such as “Your Netflix subscription expires tomorrow,” “Did you forget to pay for your subscription?” or “Check out our new shows” — all cleverly designed to trick users into updating their payment information.
For many, Netflix is a daily habit, and the idea of being cut off — whether from the latest shows or personal watchlists — creates a sense of urgency that drives users to act impulsively without verifying the legitimacy of the message. That is why cybercriminals likely exploit the emotional response triggered by the thought of losing access to a beloved service.
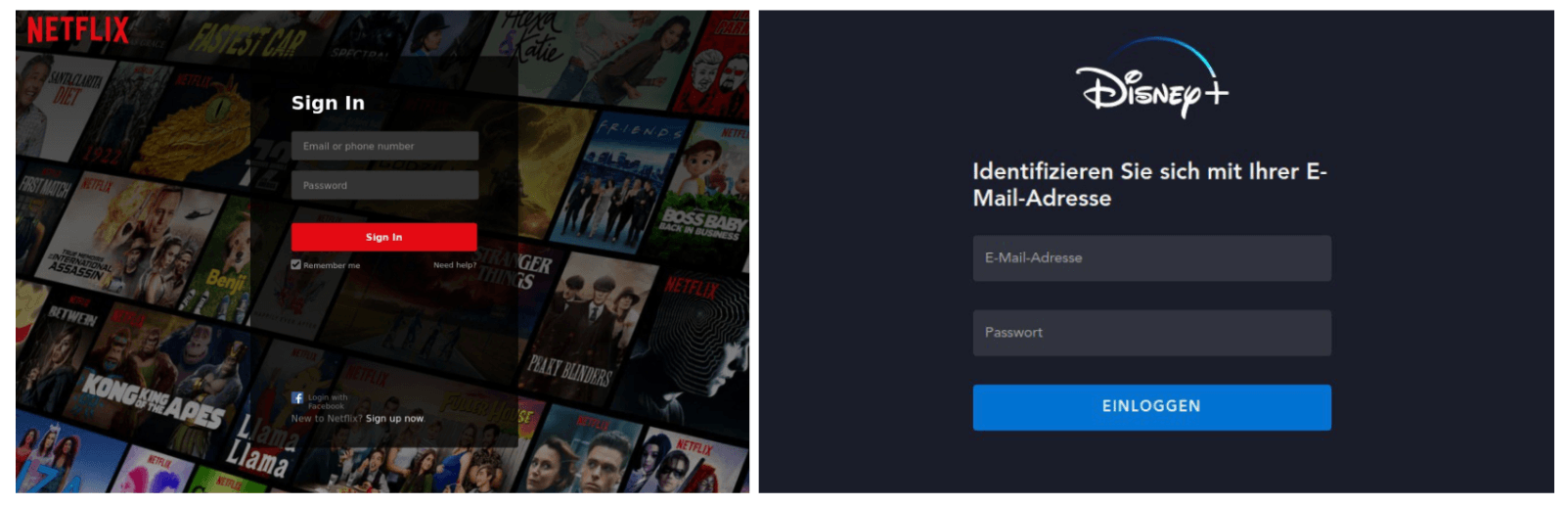
The primary target for scammers is user credentials. We discovered phishing scams mimicking the reviewed platforms’ login pages as a way to harvest credentials. Just like any sign-in page, most of these ask users to enter an email and password for the viewer account. As a result, the users’ credentials end up in cybercriminals’ hands. After that, scammers may start using that data for malicious purposes, e.g., launching spam attacks, and gaining access to users’ email or other accounts on various websites: as many users reuse passwords for shopping platforms, social media, online banking, etc. And often, stolen data is put up for sale on the dark web.
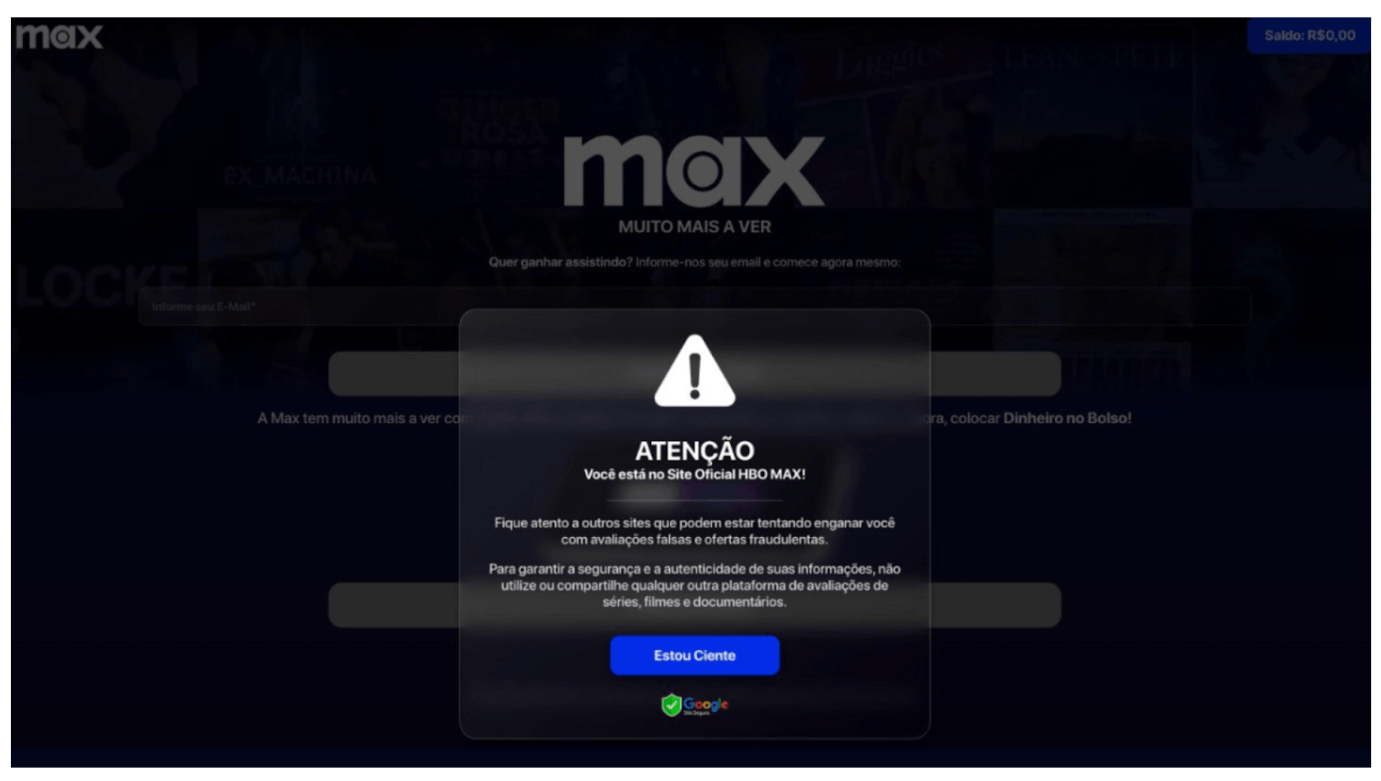
Sometimes, to further exploit the emotional connection users have with streaming platforms, cybercriminals add pop-ups with additional information to phishing pages — either triggering a sense of urgency or, conversely, attempting to reassure the user that the page is not a phishing site. For example, one phishing scheme Kaspersky discovered preys on unsuspecting users by masquerading as the official HBO Max website, using deception and urgency to trick victims into divulging sensitive information. At first glance, the page mimics the design and branding of the legitimate streaming platform, complete with a prominent warning message intended to instill trust. The message declares: “You are on the official HBO Max site,” while also cautioning users against fraudulent platforms, creating a false sense of security. The integration of a fake Google security badge at the bottom of the warning adds another layer of deception, leveraging the reputation of a trusted brand to lend credibility to the scam.
Beneath the surface, however, the true intent might be malicious. The “Estou Ciente” (I understand) button, prominently displayed in the center of the screen, acts as a gateway to further stages of the scam. Clicking it redirects users to a form where they are prompted to input personal information such as login credentials, credit card details or other sensitive data under the guise of verifying or renewing their subscription.
For many users, especially those on tight budgets, the monthly fees on streaming services can feel burdensome. Adding to this, Netflix recently introduced a strict policy against account sharing, limiting the ability to split costs with friends or family. This frustration creates a perfect storm for cybercriminals, who exploit the desire for free or cheaper access through scams like the “Netflix Mod APK.” It promises access to Netflix’s premium features for free, claiming that the modified app unlocks all content without any restrictions, eliminating the need for a subscription. The page even provides detailed instructions, making the process seem easy and legitimate.
However, this is a classic bait-and-switch scam. Instead of granting access to Netflix content, the APK file likely contains malware designed to steal personal data or financial information, or compromise the user’s device. By downloading and installing the file, users expose themselves to a variety of cyberthreats, such as spyware, ransomware or unauthorized remote access.
Data breach analysis
Phishing attacks have long been a primary tactic used by cybercriminals to gain unauthorized access to users’ credentials. However, phishing may also lead to far more dangerous consequences, for instance, malware infection. Cybercriminals use malware to silently monitor and extract user data. As a result, the damage caused by malware-based breaches can be far-reaching: not only can the stolen data be used for identity theft, financial fraud or further cybercriminal activity, but if the user’s device remains infected, their accounts may be compromised again even after a password reset.
Once malware has infected a device and gathered sensitive information, cybercriminals often turn to underground cybercriminal forums to sell the stolen data. These forums serve as a marketplace for malicious actors to buy and sell stolen information. In some cases, cybercriminals may also distribute data for free in order to build a reputation within these communities or to demonstrate their hacking capabilities.
The digital marketplace for stolen data is highly active and accessible to a wide range of cybercriminals. On these forums, stolen data, including login credentials for Netflix, Amazon Prime Video, and Disney+, are often shared openly or at a low cost, making it relatively easy for attackers to sell or exchange valuable data. By observing trends and activity within these forums, we gain insight into the scale of the threat, as well as the motivations behind these data-sharing practices.
The total number of detected accounts in 2024 (Netflix, Amazon Prime Video, Disney+, Apple TV Plus, Max) counts for 7,035,236.
Netflix: A major target for cybercriminals
In 2024, we detected 5,632,694 accounts belonging to users of the Netflix streaming service. For Netflix, Brazil accounted for the highest number of detected records compared to other countries, with Mexico and India being in second and third place.
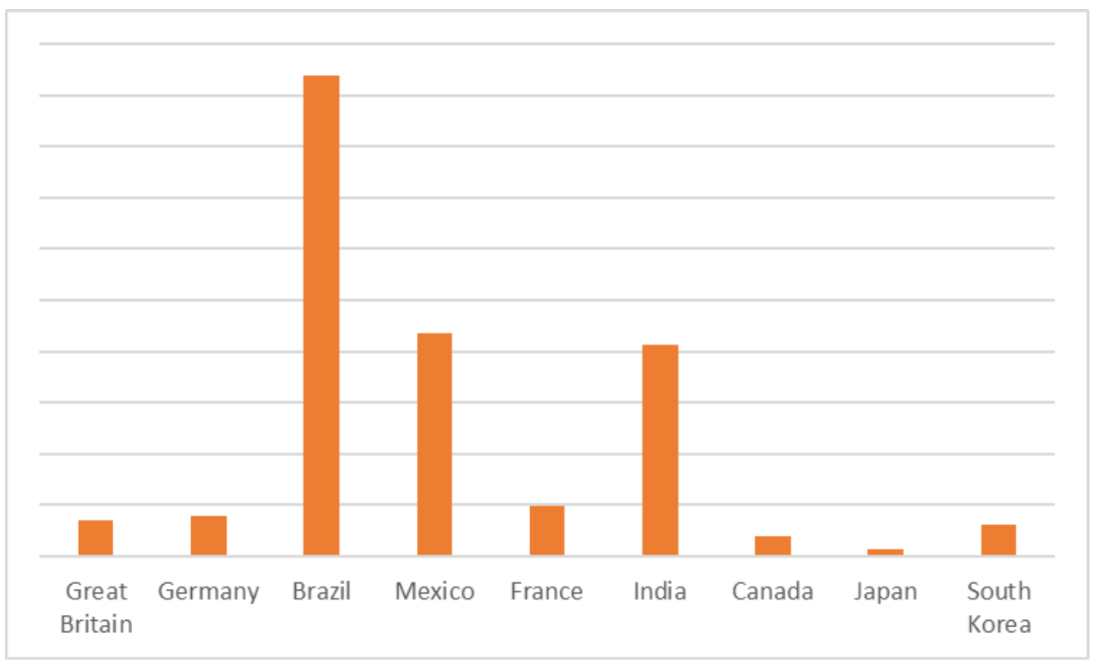
Distribution of records with malware-compromised Netflix accounts across the countries with the highest subscriber counts
Amazon Prime Video
In 2024, we detected 1,607 accounts belonging to users of the Amazon Prime Video streaming service. For Amazon Prime Video, Mexico accounted for the highest number of detected records compared to other countries, with Brazil and France being in second and third place.
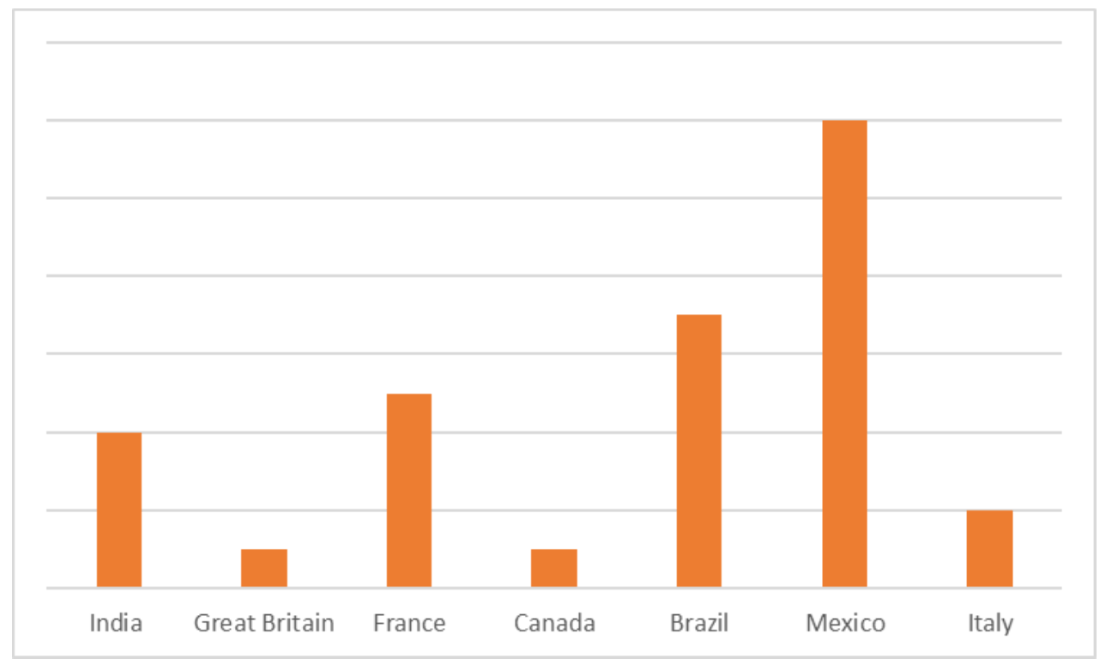
Distribution of records with malware-compromised Netflix accounts across the countries with the highest subscriber counts
Disney+
In 2024, we detected 680,850 accounts belonging to users of the Disney+ streaming service. For Disney+, Brazil emerges as the country with the highest number of compromised accounts among the top countries.
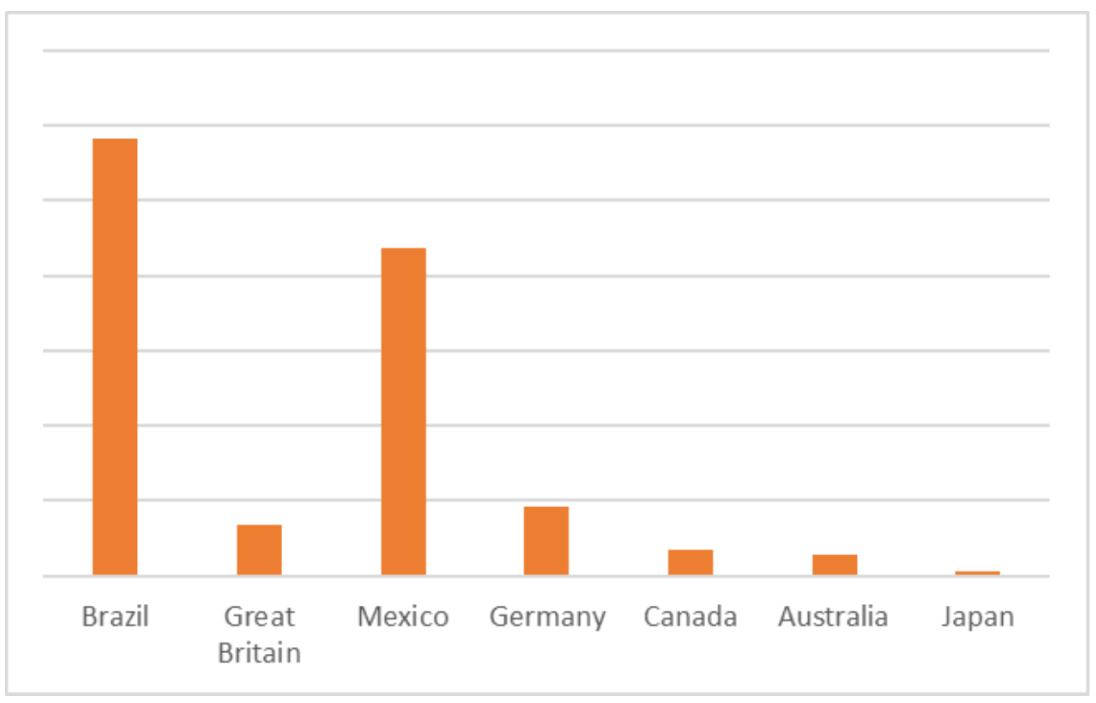
Distribution of records with malware-compromised Disney+ accounts across the countries with the highest subscriber counts
For users, the risks of a device’s infection go beyond the loss of access to entertainment services. Malware infections can expose sensitive personal data, enable unauthorized access to banking or work accounts and open the door to repeated compromises, even after passwords have been changed. As cybercriminals continue to refine their tactics, users must remain vigilant to protect against these threats.
In case signs of devices’ compromise by malware are detected, we recommend:
- Change passwords for the potentially compromised accounts and ensure there has been no suspicious activity associated with these accounts.
- Perform a full antivirus scan on all devices and remove any malware if detected.
- Use strong passwords and regularly update them.
From Shrek to Naruto: How cybercriminals exploit pop culture favorites
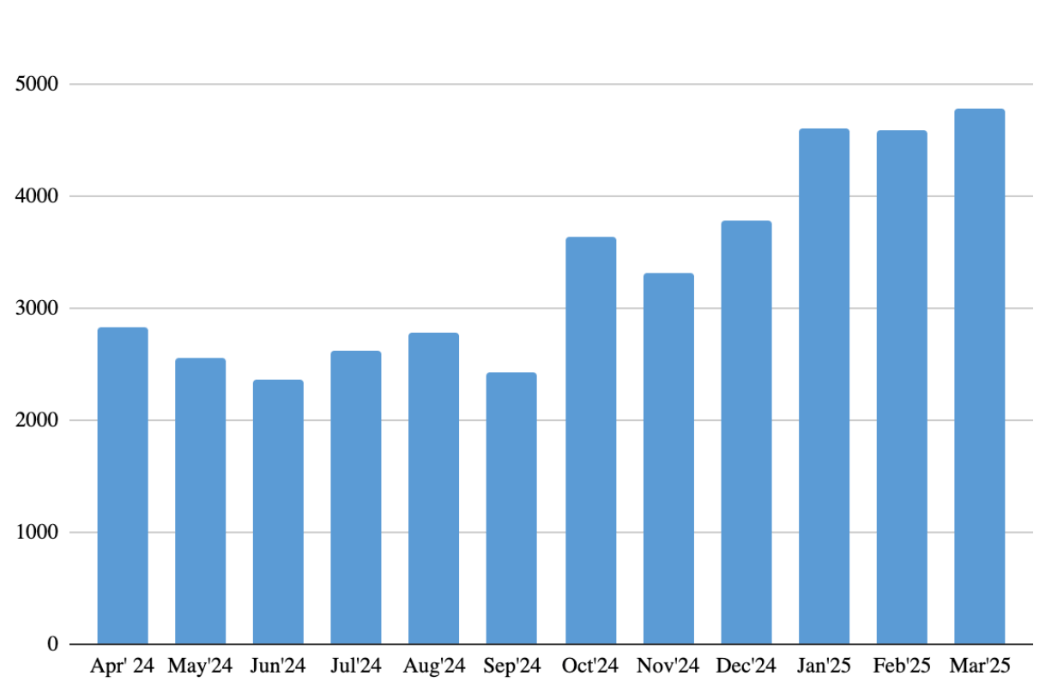
Attempts to attack users through malicious or unwanted files disguised as Gen Z’s favorite films and series throughout the reported period
Throughout the reported period, Kaspersky detected 43,302 attempts to distribute malicious or unwanted files disguised under the names of five iconic films and series: Shrek, Stranger Things, Twilight, Inside Out 2 and Deadpool & Wolverine. These titles, beloved by Gen Z, remain cultural touchstones that are widely searched for and watched, even years after their original release. What’s interesting, we saw special attention of cybercriminals to these titles at the beginning of 2025. This is primarily connected to the rise of attacks on Shrek – the number of attempted attacks increased two-fold by March 2025, compared to the average figure in 2024. This is most likely connected to the boom in attention to this title with the trailer for Shrek 5 being dropped, anticipated for years after the latest Shrek Forever After released in 2010.
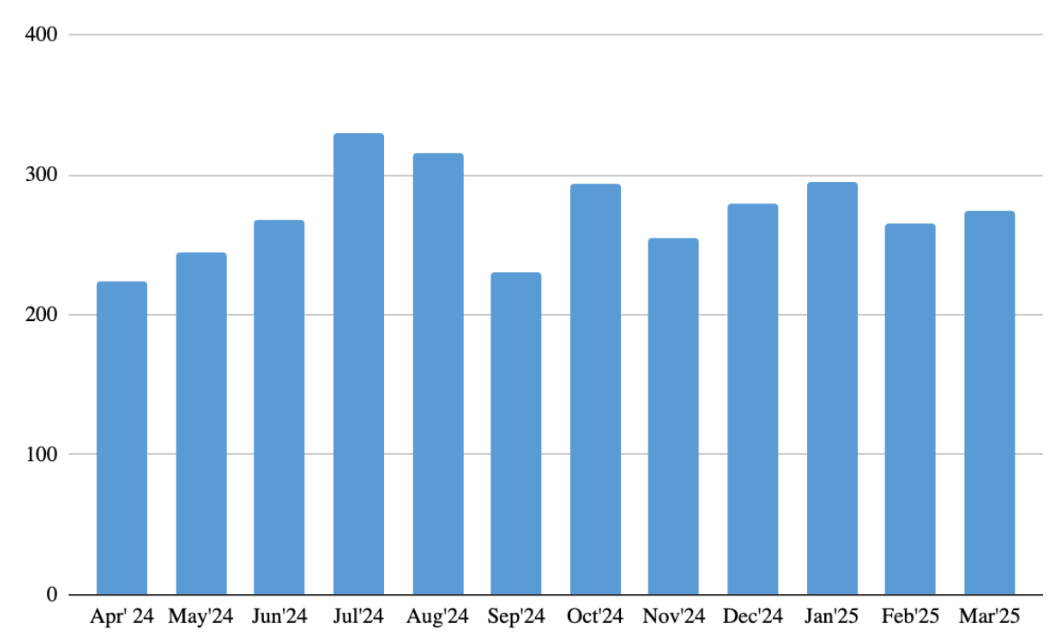
The number of unique users affected by malicious or unwanted files disguised as Gen Z’s favorite films and series throughout the reported period
Throughout the reported period, a total of 1,794 users attempted to download dangerous files disguised as five popular films and series. However, when we look at the monthly distribution, we don’t see the same decline trends throughout specific months as we do in the attack attempts chart. This means that even with a decrease in the overall number of attacks, the number of users targeted can still remain high.
This indicates that cybercriminals may be shifting their tactics, focusing on more targeted, convincing campaigns that continue to attract a significant number of users. This suggests that cybercriminals may be employing more sophisticated or persuasive phishing methods, resulting in a high number of affected users despite fewer overall attempts.
The top exploited Gen Z-beloved films and series by the number of attempted attacks throughout the reported period
| Title | The number of attack attempts |
| Shrek | 36,747 |
| Twilight | 2,876 |
| Stranger Things | 2,681 |
| Inside Out 2 | 797 |
| Deadpool & Wolverine | 201 |
Shrek – which got over 36,000 attempted attacks under its guise and became the most targeted film throughout the reported period, is the ultimate nostalgia trip for Gen Z, many of whom grew up watching the lovable ogre’s adventures. Beyond its iconic humor and heartwarming story, the franchise has found a second life as a meme factory, with endless references and remixes circulating on social media platforms. This keeps Shrek perpetually relevant, particularly among a generation that thrives on internet humor and shared cultural moments.
Twilight, once a cultural phenomenon, remains a guilty pleasure and ironic favorite for Gen Z, which saw almost 3,000 attempted attacks throughout the reported period in 2024. Its dramatic love story, supernatural elements, and over-the-top moments have transitioned from teenage obsession to a cult classic among young adults. Social media has played a big role in revitalizing interest in the saga, as fans poke fun at its quirks while celebrating its iconic status.
Stranger Things captures Gen Z’s love for suspense, retro aesthetics and relatable characters. Even as the seasons progress, fans continue to rewatch earlier episodes, deepening their attachment to the characters and the universe. Throughout the reported period, Stranger Things was used as bait by cybercriminals in 2,681 attack attempts, highlighting its continued popularity and appeal to this generation.
Interestingly, despite their lower rankings in terms of attack attempts, Kaspersky experts found more examples of phishing and scams involving Inside Out 2 and Deadpool & Wolverine than Shrek, Stranger Things and Twilight. This may be due to the fact that these two titles are newly released, meaning they still have a fresh appeal and a lot of buzz surrounding their launch. These fresh releases might not yet have the same level of skepticism as older, well-known titles, making users more susceptible to malicious schemes disguised as exclusive content or early access to the new films.
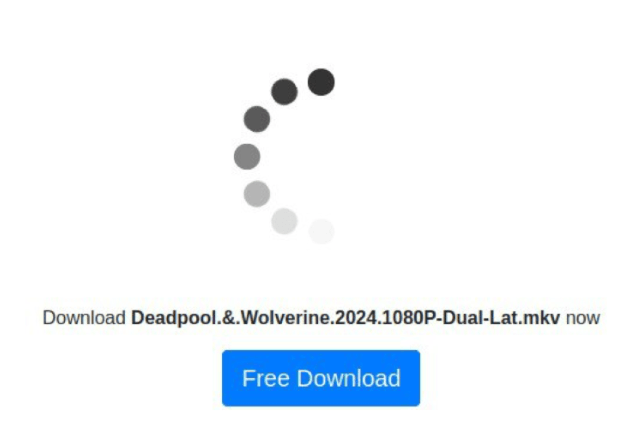
For instance, Kaspersky experts found a typical scam targeting users who are seeking free access to the latest movies, in this case, Deadpool & Wolverine 2024. The website poses as a legitimate platform offering a “free download” of a high-quality movie file, but this is a trap designed to trick users into downloading malicious software instead of the promised content. After the malicious software download, the user is left with no movie file and may be unaware that their device is now compromised, potentially exposing sensitive data to cybercriminals.
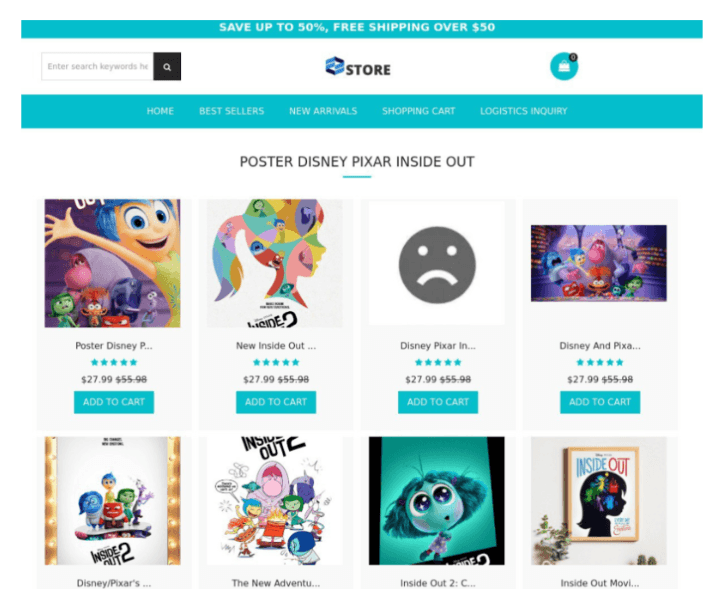
This scam is not just limited to users downloading malicious files disguised as movies or shows. Another common trap is fake online stores, like the one seen in the screenshot, offering “exclusive” merchandise, such as posters of popular titles like Inside Out 2. These sites use appealing offers, such as significant discounts and free shipping, to lure fans of the film into making purchases. Users may be drawn to buy merchandise related to this year’s most popular animated movie, as it’s a highly anticipated release. The scam relies on the excitement surrounding Inside Out 2, preying on the trust and eagerness of fans who want to buy unique items. However, instead of receiving their orders, victims end up with either no merchandise or their payment details stolen.
Attacks on the most beloved Gen Z’s anime
When talking about the tastes of Gen Z, it’s important not to focus solely on films and TV series. Unlike any other generation, Gen Z watches more anime than any previous one. According to recent data, over 65% of Zoomers tune in to watch anime. This is clearly reflected in the number of cyberattacks disguised as popular anime titles among Gen Z.
For our analysis, we selected five popular anime titles among Gen Z: Naruto, One Piece, Demon Slayer, Attack on Titan and Jujutsu Kaisen. As a result, throughout the reported period, cybercriminals launched 251,931 attack attempts, which is almost six times higher than the number of attacks disguised as films and TV series. With the rise of anime’s influence on social media and streaming platforms, it’s no surprise that these titles have become key lures for malicious campaigns, exploiting the strong emotional connection fans have with these beloved series.
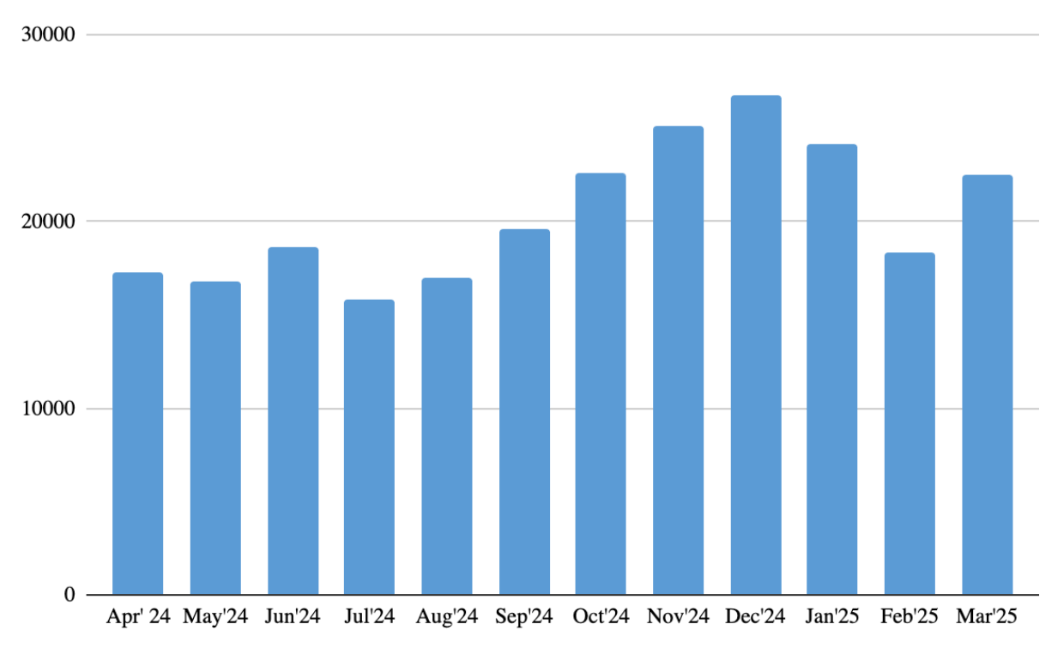
Attempts to attack users through malicious or unwanted files disguised as Gen Z’s favorite anime throughout the reported period
Interestingly, when we look at the monthly distribution, we see that the number of attack attempts disguised as anime follows a similar seasonal decline to the attacks disguised as films and TV series. This could be due to several factors.
One possible reason is that, just like with movies and TV shows, people’s anime-watching habits may change during the warmer months. As the summer approaches, many people spend more time outdoors or take vacations, leading to less time spent watching content online. This seasonal shift can result in a temporary decrease in anime-related search traffic and content consumption, which in turn reduces the effectiveness of cybercriminals’ attempts to lure users with these scams.
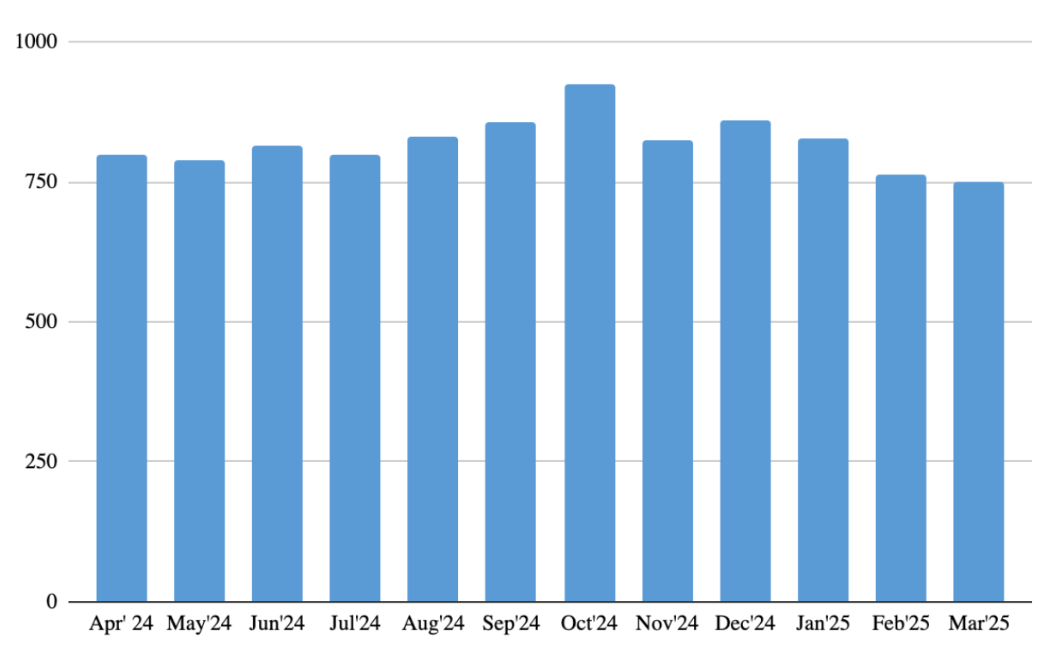
The number of unique users affected by malicious or unwanted files disguised as Gen Z’s favorite anime throughout the reported period
Throughout the reported period, about 5,200 users attempted to download malicious or unwanted files disguised as Gen Z’s favorite anime. The number of users remained stable throughout the year. This indicates that the demand for anime-related content, and consequently the risks associated with it, is consistently high among Gen Z. Even as the number of attacks disguised as films and series fluctuated, cybercriminals maintained a steady focus on anime, a genre with growing popularity.
The top exploited Gen Z beloved anime by the number of attempted attacks throughout the reported period
| Title | The number of attack attempts |
| Naruto | 114,216 |
| Demon Slayer | 44,200 |
| Attack on titan | 39,433 |
| One Piece | 29,886 |
| Jujutsu Kaisen | 24,196 |
Interestingly, the distribution of the most targeted anime remained consistent throughout the year, with the same titles maintaining their positions as the top five most exploited by cybercriminals. Throughout the reported period, cybercriminals targeted Gen Z’s favorite anime titles, with Naruto leading the charge as the most exploited anime. Even though the title was launched in 2002, the number of attempted attacks disguised as Naruto reached a staggering 114,216 throughout the reported period, making it the highest-targeted title of the year.
Following Naruto, Demon Slayer was also a top target, with 44,200 attempted attacks. This anime has seen a significant surge in popularity in recent years, particularly with the growing fanbase and strong online presence making it an obvious choice for cybercriminals aiming to exploit the buzz around the series. Attack on Titan ranks third with 39,433 attempts to distribute malicious files. Despite its longer run compared to newer titles, the series maintains a strong position in the anime world, making it a highly targeted option for cybercriminals looking to take advantage of its enduring popularity.
Conclusion and recommendations
As the world of entertainment continues to evolve, so do the tactics used by cybercriminals to exploit popular content, whether through fake downloads or fraudulent merchandise offers. From beloved movies like Shrek and Stranger Things to the latest blockbusters like Inside Out 2, scammers have found new ways to take advantage of Gen Z’s affinity for digital culture and streaming platforms. With the rise of these cyberthreats, it’s more important than ever for users to stay vigilant and understand how to protect themselves online.
To help Gen Z tackle digital threats in the entertainment space, Kaspersky has launched an interactive game “Case 404” that speaks their language. It immerses players in a world where seemingly harmless downloads and offers conceal serious cybersecurity risks. As they play, users uncover hidden dangers and learn how to protect themselves from malware, scams, and personal data leaks.
As a reward for completing the game, participants receive an exclusive discount on Kaspersky Premium — giving them the trusted tools they need to navigate the digital world safely.
Play, learn and stay safe — because cybersecurity should be engaging, not overwhelming.
- Always use a legitimate, paid subscription when accessing streaming services and ensure you’re using apps from official marketplaces or the official websites.
- Always verify the authenticity of websites before entering any personal information. Stick to trusted, official pages when watching or downloading content and double-check URLs and company name spellings to avoid phishing sites.
- Be cautious about the file extensions you’re downloading. Video files should not have.exe or.msi extensions — these are typically associated with harmful programs.
- Use a reliable security solution, like Kaspersky Premium, to detect malicious attachments that could compromise your data.
- Ensure secure browsing and safe messaging with Kaspersky VPN, blocking malicious and phishing websites if you accidently open the links.
- Avoid clicking on links that promise early access to new content. If something seems too good to be true, confirm the content’s authenticity with your streaming provider.
- Never open attachments or click on links in unsolicited emails claiming to be from streaming services, especially if they create a sense of urgency. Instead, navigate directly to the official website and log in securely.
- Never download unofficial versions or modified applications for streaming platforms. These could lead to malware or other cybersecurity risks.
Threat Research
The Threat Research team is a leading authority in protecting against cyberthreats. By actively engaging in both threat analysis and technology creation, our TR experts ensure that Kaspersky’s cybersecurity solutions are deeply informed and exceptionally powerful, providing critical threat intelligence and robust security to our clients and the broader community.
The Security Services
Delivering hundreds of information security projects every year for Fortune 500 organizations worldwide: incident response, managed detection, SOC consulting, red teaming, penetration testing, application security and digital risks protection.