Imagine receiving an email that says Google has received a subpoena to release the contents of your account. The email looks perfectly “Googley”, and the sender’s address appears legitimate too: no-reply@accounts.google.com. A little unnerving (or maybe panic-inducing?) to say the least, right?
And what luck — the email contains a link to a Google support page that has all the details about what’s happening. The domain name in the link looks legit, too, and seems to belong to Google…
Regular readers of our blog have probably already guessed that we’re talking here about a new phishing scheme. And they’d be right. This time, the scammers are exploiting several genuine Google services to fool their victims and make the emails look as convincing as possible. Here’s how it works…
How phishing email mimics an official Google notification
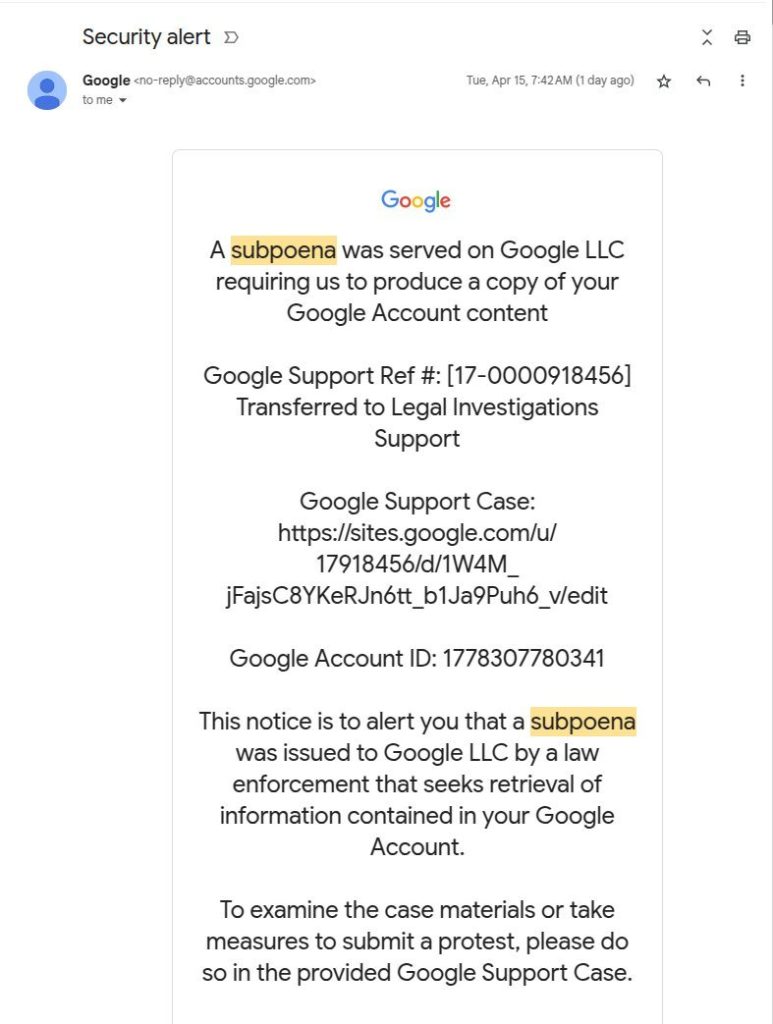
The screenshot below shows the email that kicks off the attack; and it does a really credible job of pretending to be an alert from Google’s security system. The message informs the user that the company has received a subpoena requesting access to the data in their Google account.
The “from” field contains a genuine Google address: no-reply@accounts.google.com. This is the exact same address Google’s security notifications come from. The email also contains a few details that reinforce the illusion of authenticity: a Google Account ID, a support ticket number, and a link to the case. And, most importantly, the email tells the recipient that if they want to learn more about the case materials or contest the subpoena, they can do so by clicking a link.
The link itself looks quite plausible, too. The address includes the official Google domain and the support ticket number mentioned above. And it takes a savvy user to spot the catch: Google support pages are located at support.google.com, but this link leads to sites.google.com instead. The scammers are, of course, counting on users who either don’t understand such technicalities or don’t notice the word substitution.
If the user isn’t logged in, clicking the link takes them to a genuine Google account login page. After authorizing, they land on a page at sites.google.com, which quite convincingly mimics the official Google support site.
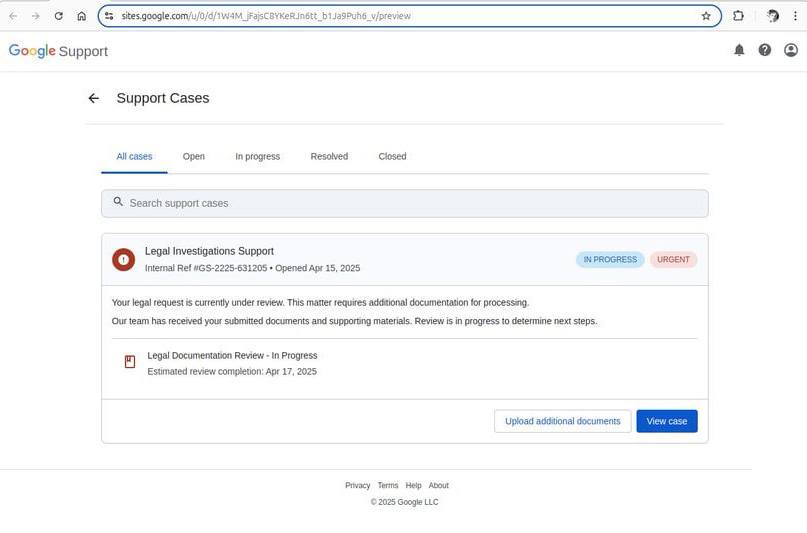
This is what a fake Google Support page linked in the email looks like. Source
Now, it just so happens that the sites.google.com domain belongs to the legitimate Google Sites service. Launched back in 2008, it’s a fairly unsophisticated website builder — nothing out of the ordinary. The important nuance about Google Sites is that all websites created within the platform are automatically hosted on a google.com subdomain: sites.google.com.
Attackers can use such an address to both lull victims’ vigilance and circumvent various security systems, as both users and security solutions tend to trust the Google domain. It’s little wonder that scammers have increasingly been using Google Sites to create phishing pages.
Spotting fakes: the devil’s in the (email) details
We’ve already described the first sign of a dodgy email: the address of the fake support page located at sites.google.com. Look to the email header for more red flags:
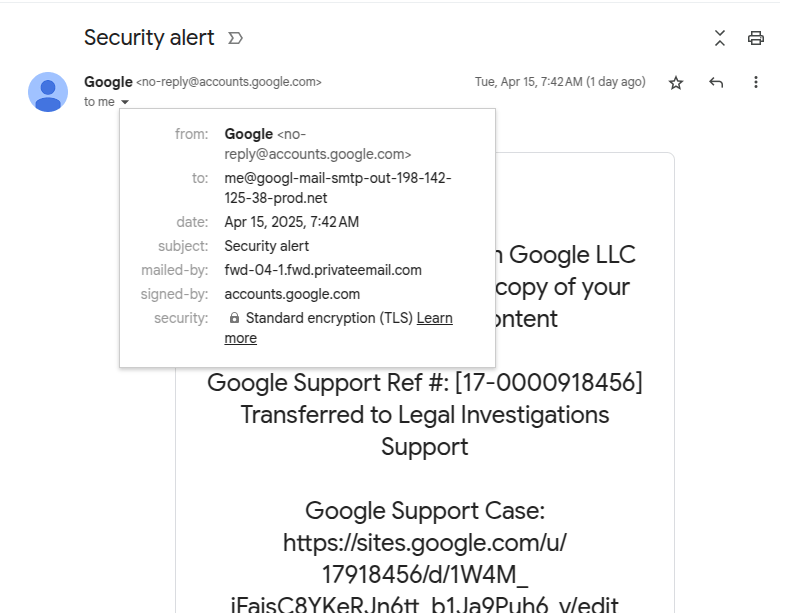
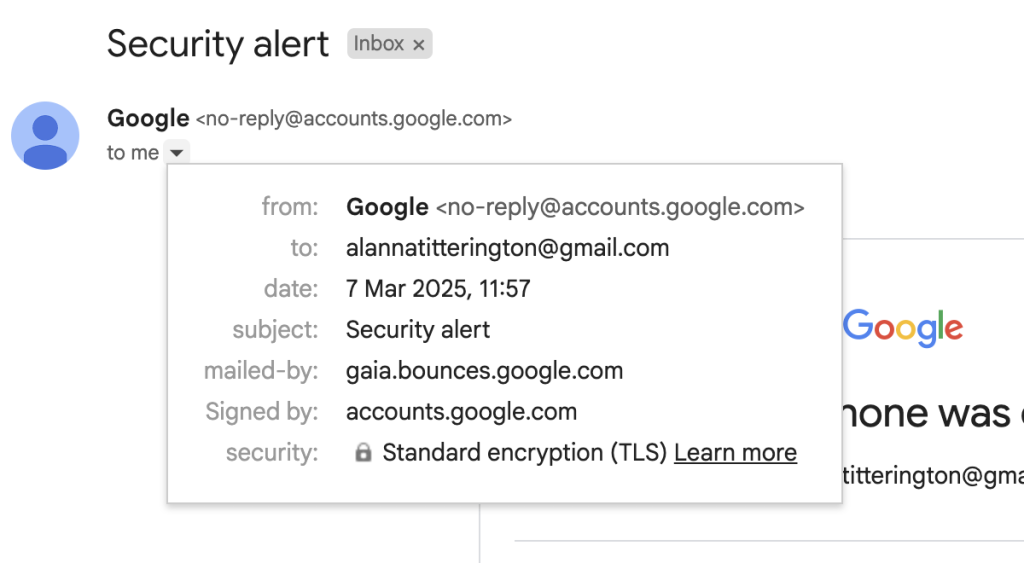
Spot the fake: look at the “to” and “mailed-by” fields in the header. Source
The fields to pay attention to are “from“, “to“, and “mailed-by“. The “from” one seems fine: the sender is the official Google email, no-reply@accounts.google.com.
But lo and behold, the “to” field just below it reveals the actual recipient address, and this one sure looks phishy: me[@]googl-mail-smtp-out-198-142-125-38-prod[.]net. The address is trying hard to imitate some technical Google address, but the typo in the company domain name is a dead giveaway. Moreover, it has absolutely no business being there — this field is supposed to contain the recipient’s email.
As we keep examining the header, another suspicious address pops up in the “mailed-by” field. Now, this one is clearly nowhere near Google territory: fwd-04-1.fwd.privateemail[.]com. Yet again, nonsense like this has no place in an authentic email. For reference, here’s what these fields look like in a real Google security alert:
Unsurprisingly, these subtle signs would likely be lost on the average user — especially when they’re already freaked out by the looming legal trouble. Adding to the confusion is the fact that the fake email is actually signed by Google: the “signed-by” field shows accounts.google.com. In the next part of this post, we explain how the criminals managed to achieve this, and then we’ll talk about how to avoid becoming a victim.
Reconstructing the attack step by step
To figure out exactly how the scammers managed to send such an email and what they were after, cybersecurity researchers reenacted the attack. Their investigation revealed that the attackers used Namecheap to register the (now-revoked) googl-mail-smtp-out-198-142-125-38-prod[.]net domain.
Next, they used the same service again to set up a free email account on this domain: me[@]googl-mail-smtp-out-198-142-125-38-prod[.]net. In addition, the criminals registered a free trial version of Google Workspace on the same domain. After that the scammers registered their own web application in the Google OAuth system, and granted it access to their Google Workspace account.
Google OAuth is a technology that allows third-party web applications to use Google account data to authenticate users with their permission. You’ve likely encountered Google OAuth as a way to authenticate for third-party services: it’s the system you use every time you click a “Sign in with Google” button. Besides that, applications can use Google OAuth to obtain permission to, for example, save files to your Google Drive.
But let’s get back to our scammers. After a Google OAuth application is registered, the service allows sending a notification to the email address associated with the verified domain. Interestingly enough, the administrator of the web application is free to manually enter any text as the “App name” — which seems to be what the criminals exploited.
In the screenshot below, researchers demonstrate this by registering an app with the name “Any Phishing Email Text Inject Here with phishing URLs…”.
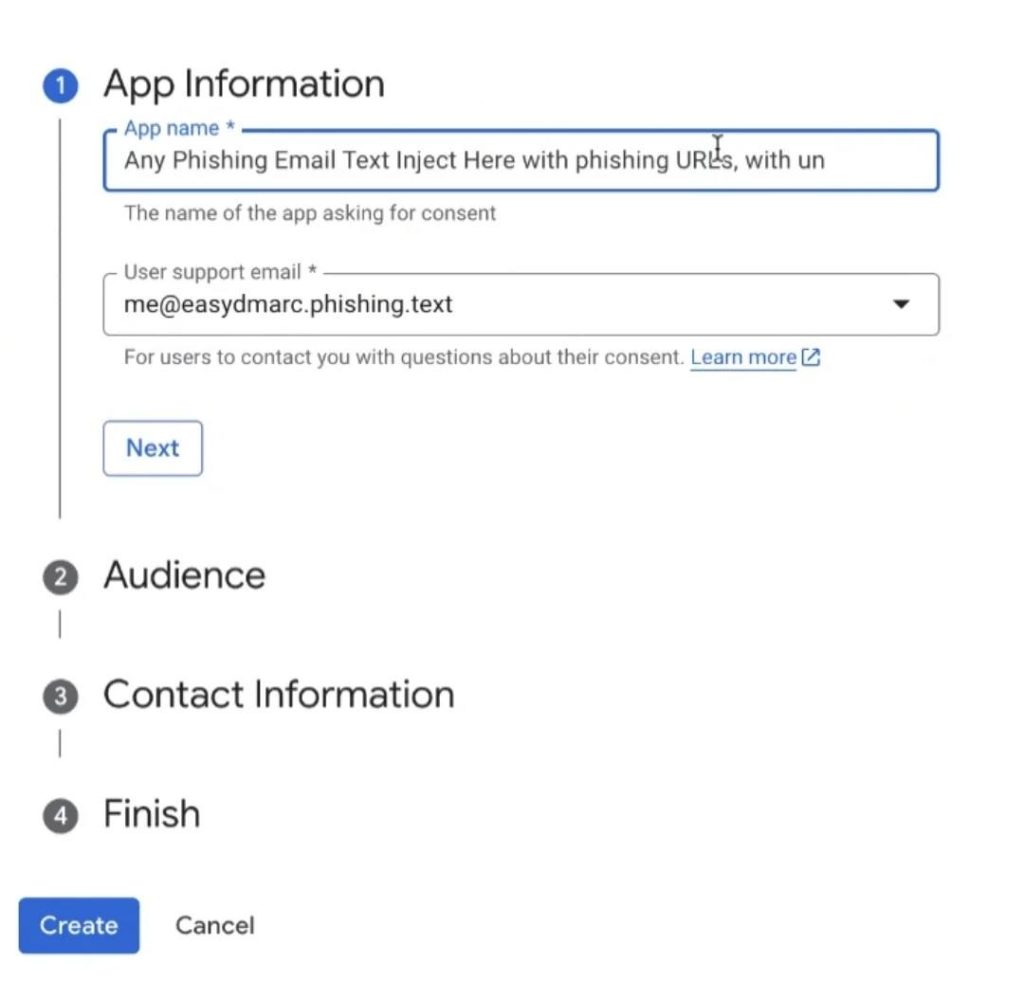
Registering a web app with an arbitrary name in Google OAuth: the text of a scam email with a phishing link can be entered as a name. Source
Google then sends a security alert containing this phishing text from its official address. This email goes to the scammers’ email address on the domain registered through Namecheap. This service allows forwarding the received notification from Google to any addresses. All they need do is set a specific forwarding rule and specify the email addresses of potential victims.
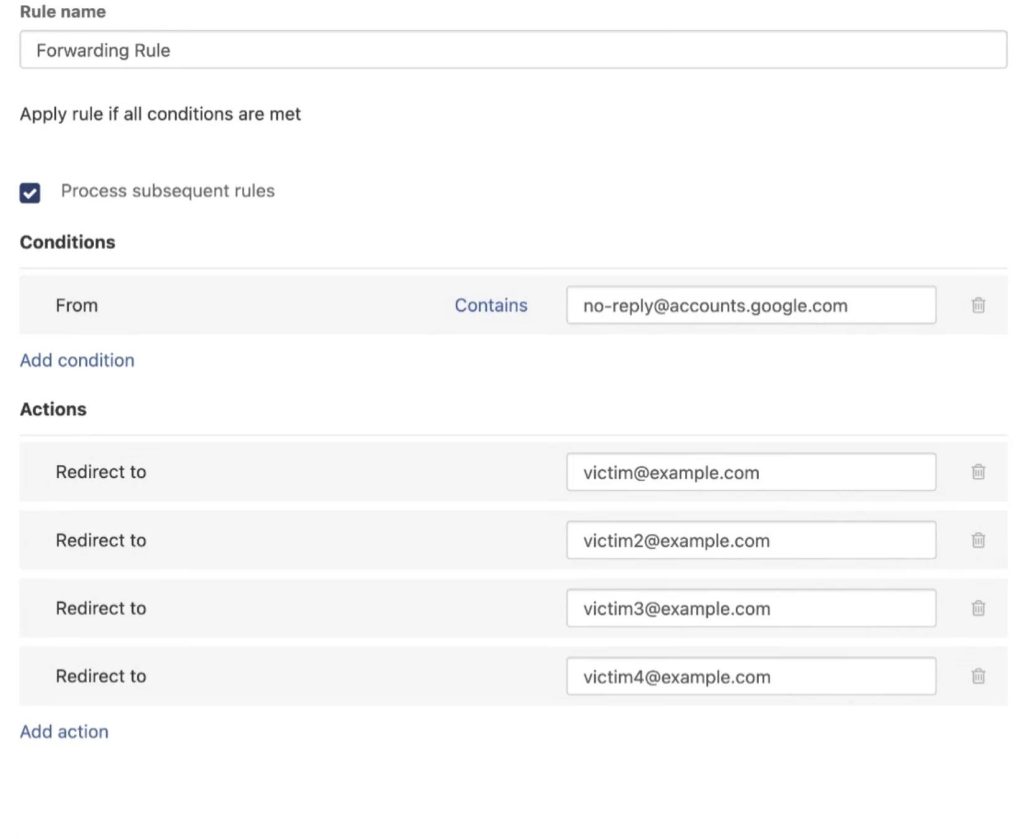
Setting up a forwarding rule that allows sending the fake email to multiple recipients. Source
How to protect yourself from phishing attacks like this one
It’s not entirely clear what the attackers were hoping to achieve with this phishing campaign. Using Google OAuth to authenticate doesn’t mean the victim’s Google account credentials are shared with the scammers. The process generates a token that only provides limited access to the user’s account data — depending on the permissions the user authorized and the settings configured by the scammers.
The fake Google Support page the deceived user lands on suggested that the goal was to convince them to download some “legal documents” supposedly related to their case. The nature of these documents is unknown, but chances are they contained malicious code.
The researchers reported this phishing campaign to Google. The company acknowledged this as a potential risk for users and is currently working on a fix for the OAuth vulnerability. However, how long it will take to resolve the issue remains unknown.
In the meantime, here’s some advice to help you avoid becoming a victim of this and other intricate phishing schemes.
- Stay calm if you get an email like this. Begin by carefully examining all the email header fields and comparing them to legitimate emails from Google — you likely have some in your inbox. If you see any discrepancies, don’t hesitate to hit “Delete”.
- Be wary of websites on the google.com domain that are created with Google Sites. Lately, scammers have been increasingly exploiting it for a wide range of phishing schemes.
- As a general rule, avoid clicking links in emails.
- Use a robust security solution that will provide timely warnings about danger and block phishing links.
Follow the links below to read about five more examples of out-of-the-ordinary phishing.
 phishing
phishing

 Tips
Tips