These days, Android variants probably run into the thousands. That’s because every vendor modifies the system for its own requirements, and certainly not always for the better. But at the heart of Android lies a well-designed operating system that is becoming more secure with each new version.
Or rather, it’s becoming more secure when the user does things right. To get hold of a chunk of interesting data in shared storage or gain access to a function that might be unsafe, Android apps always needs the user’s explicit permission. And it’s crucial to set these permissions properly.
We already discussed how to configure these settings correctly in Android 6, so now let’s talk about a more recent version of the operating system — Android 8. First of all, version 8 has way more settings than before, which is both good and bad. Good because you can make the system safer. Bad because setting up all these things is now more complicated and time-consuming. What’s more, the settings are now located in various places, including some fairly nonintuitive ones. But this guide should make sense of it all.
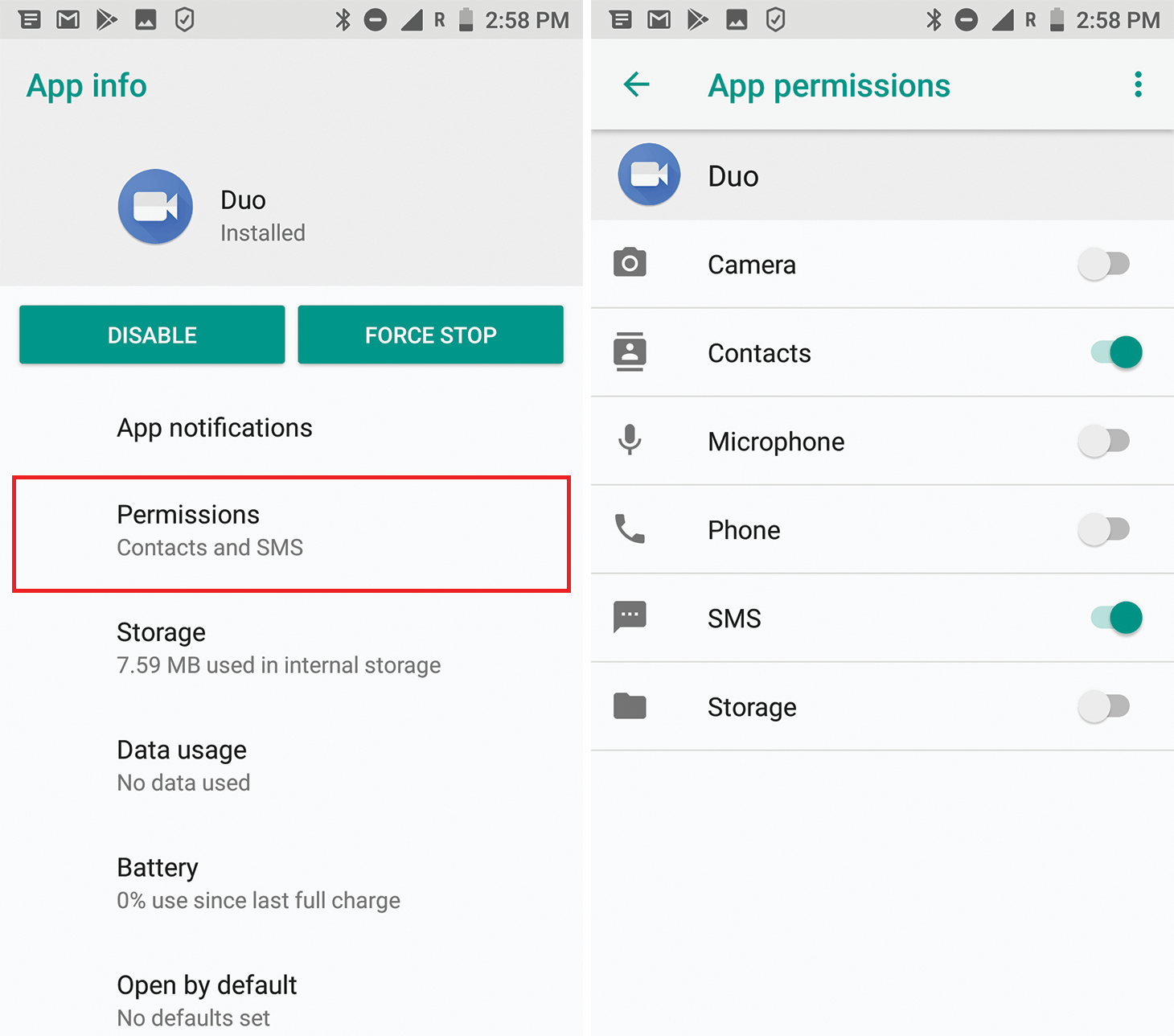
Permissions configured in the App permissions list
This list includes permissions giving apps access to personal info stored on the smartphone (contacts, call history, SMS, photos) and to built-in devices through which personal data can be retrieved (camera, microphone, phone, GPS receiver).
Before an app receives any kind of permission, it must explicitly ask the user for it. You decide what apps can access
Giving an app any of these permissions means that from now on it can obtain information of this type and upload it to the cloud without asking your explicit consent for whatever it intends to do with your data.
Therefore, we recommend that you stop and think before granting permissions to apps, especially if they are not needed for the app to work. For example, most games have no need to access your contacts or camera, messengers don’t really need to know your location, and some trendy filter for the camera can probably survive without your call history.
Ultimately, it’s your decision, but the fewer permissions you hand out, the more intact your data will be.
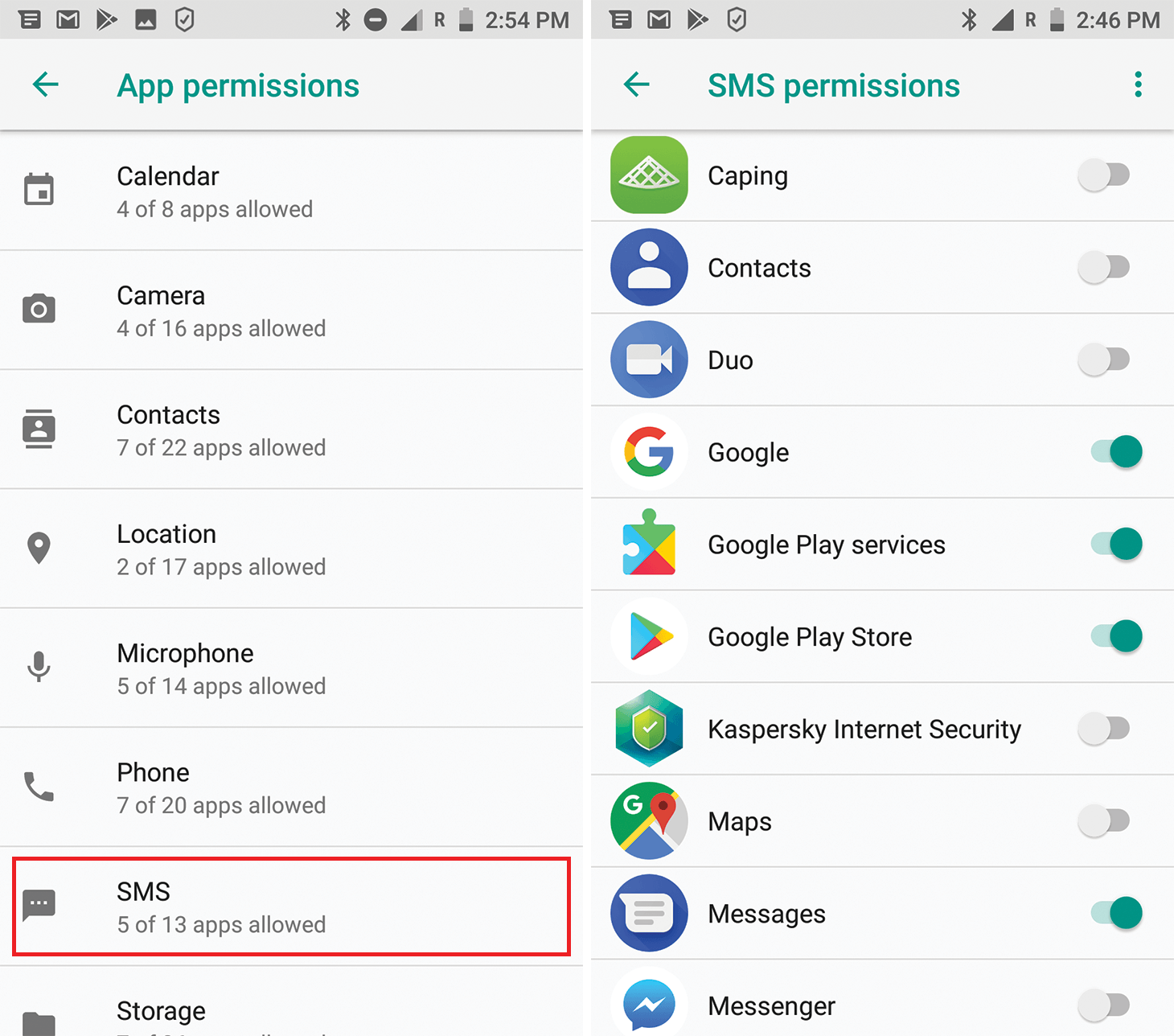
SMS
What it is: Permission to send and receive SMS, MMS, and WAP push messages, as well as view messages in the smartphone memory.
The danger: An app with these rights will be able to read all of your SMS correspondence, including messages with one-time codes for online banking and confirming transactions.
Using this permission, the app can also send spam messages in your name (and at your expense) to all your friends. Or sign you up for a premium “service.”
Where it’s configured: Settings -> Apps & notifications -> App permissions -> SMS
Calendar
What it is:Permission to view, delete, modify, and add events in the calendar.
The danger: Prying eyes can find out what you’ve done and what you’re doing today and in the future. Spyware loves this permission.
Where it’s configured: Settings -> Apps & notifications -> App permissions -> Calendar
Camera
What it is: Permission to access the camera so the app can take photos and record video.
The danger: Apps with this permission can take a photo or record a video at any moment and without warning. Attackers armed with embarrassing images and other dirt on you can make life a misery.
Where it’s configured: Settings -> Apps & notifications -> App permissions -> Camera
Contacts
What it is: Permission to read, change, and add contacts in your address book, and access the list of accounts registered in the smartphone.
The danger: With this permission, an app can send your entire address book to its server. Even legitimate services abuse this permission, never mind scammers and spammers, for whom it’s a windfall.
This permission also grants access to the list of app accounts on the device, including Google, Facebook, and many other services.
Where it’s configured: Settings -> Apps & notifications -> App permissions -> Contacts
Location
What it is: Access to your location — both approximate (based on data from mobile base stations and Wi-Fi access points) and precise (based on GPS and GLONASS data).
The danger: Allows the app to track all your movements.
Tracking the movement of a smartphone soon reveals where the owner lives (nighttime location), works (daytime location), and other things as well.
Even if you don’t mind apps spying on your movements, consider one more thing: Geolocation is one of the biggest battery drainers. So the fewer apps you give this permission to, the longer your phone’s battery life is going to be.
Where it’s configured: Settings -> Apps & notifications -> App permissions -> Location
Microphone
What it is: Permission to record sound from built-in smartphone microphones.
The danger: With this permission, apps can record anything within earshot of your phone. All your calls and face-to-face conversations, the lot.
Where it’s configured: Settings -> Apps & notifications -> App permissions -> Microphone
Body sensors
What it is: Access to data from health sensors, such as a heart-rate sensor.
The danger: Allows the app to monitor your body functions using data from sensors in, say, a fitness bracelet (built-in smartphone motion sensors are not included in this category). Such data can be used by healthcare companies, for example, in evaluating the cost of your insurance.
Where it’s configured: Settings -> Apps & notifications -> App permissions -> Body sensors
Storage
What it is: Reading and writing files to the smartphone’s shared memory. In Android, every app has its own small storage that only it can access; the remaining storage area can be accessed by all apps with this permission.
The danger: Allows an app to thumb through all of your files. For example, it can view all photos (including those ones from your vacation you’d rather not share) and upload them to its server. Or encrypt your files and demand ransom for decryption.
This permission is also dangerous because many apps use shared storage for temporal storage of additional modules and updates they download from the Internet, leaving them vulnerable to infection by a malicious app. This is known as a Man-in-the-Disk attack.
Where it’s configured: Settings -> Apps & notifications -> App permissions -> Storage
Phone
What it is: Permission to view and modify call history; obtain your phone number, cellular network data, and the status of outgoing calls; add voicemail; access IP telephony services; view numbers being called with the ability to end the call or redirect it to another number; call any number.
The danger: This permission basically lets the app do anything it likes with voice communication. It can find out who you called and when or prevent you from making calls (to a particular number or in general) by constantly terminating calls. It can eavesdrop on your conversations or, of course, make calls anywhere at your expense, including to pay-through-the-nose numbers.
Where it’s configured: Settings -> Apps & notifications -> App permissions -> Phone
Permissions configured in the Special app access list
The section above looked at app permissions for accessing personal data. But there’s another list of permissions — for accessing various Android functions. In the hands of a malicious app these permissions can cause a lot of harm, so give them sparingly.
They are buried deep in the settings and far from intuitive, so to understand how they are used and what their consequences might be, the user needs a good idea of how Android and mobile malware work. But don’t worry, we’ll give you a rundown of the ins and outs.
Battery optimization
What it is: New versions of Android severely limit the ability of apps to operate in background mode, primarily to save battery power. That said, developers whose apps require background operation (music players, fitness apps, not to mention antiviruses) retain the ability to ensure full-fledged background operation. But for this, they must request user permission to become an exclusion that is not affected by the battery-optimization feature.
The danger: Spyware apps, for example, might also want to run in the background to monitor the user’s movements. Therefore, this permission should be treated with care, and the list of apps that can operate freely in the background should be periodically checked.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Battery optimization -> Not optimized.
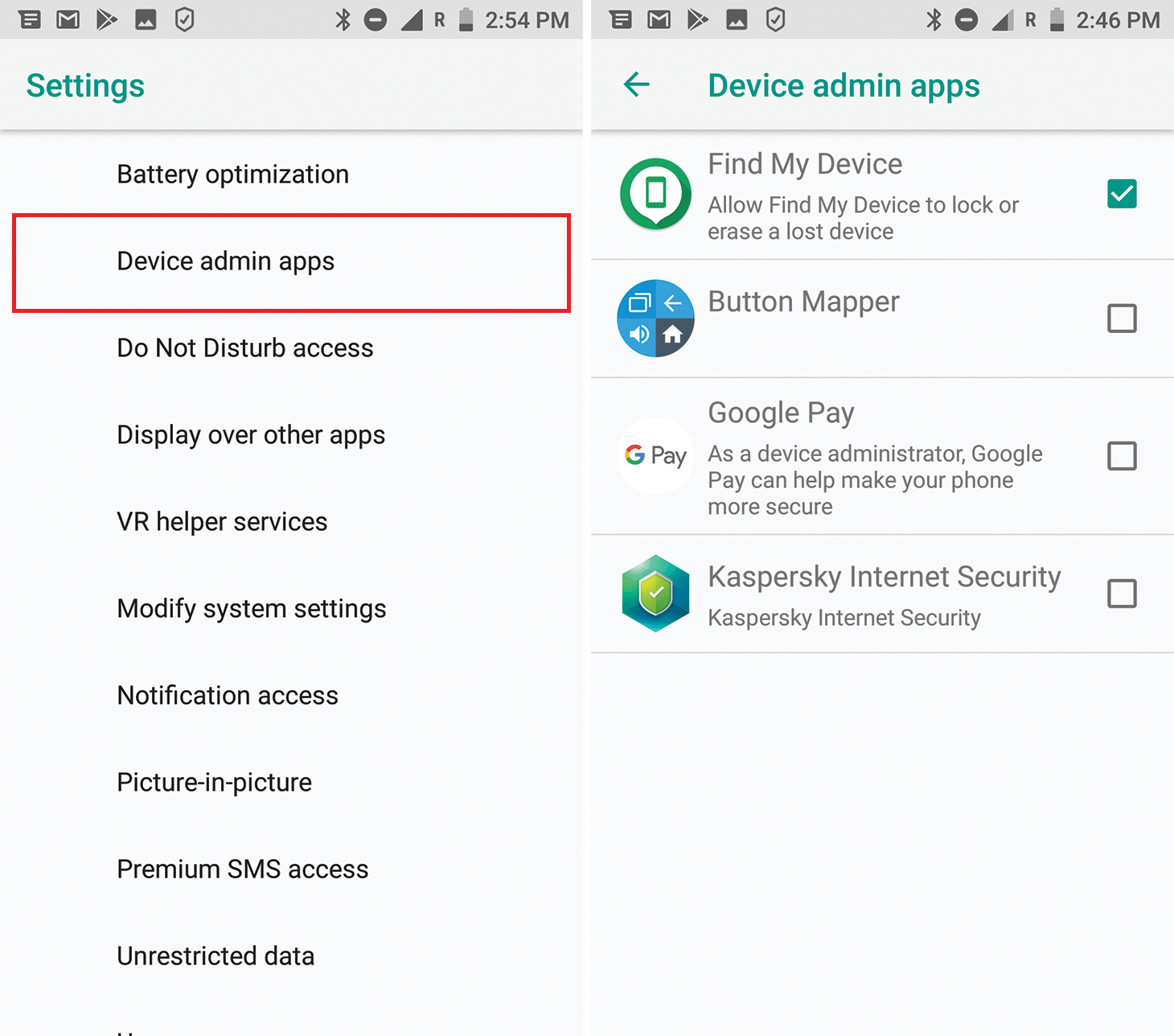
Device admin apps
What it is: This permission grants apps the right to use remote admin functions. This set of functions was initially designed to enable corporate IT services to correctly configure employees’ smartphones remotely from the workplace, without having to physically chase them down.
The danger: For a start, this permission allows an app to change the smartphone’s password, forcibly lock the screen, turn off the camera, and even wipe all data. Second, an app with this permission is tricky to remove, and malware loves using it to gain a foothold in the system. So this permission should be given only if you are 100% sure that the app requesting it is squeaky clean.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Device admin apps
Do Not Disturb access
What it is: The newest versions of Android feature the Do Not Disturb function with lots of settings, allowing voice call and message sounds and vibration to be turned off and pop-up notifications to be hidden. It is also possible to schedule when this mode takes effect and set exclusions (for all or starred contacts) so that certain calls and messages are not affected when in Do Not Disturb mode. This permission allows apps to change the settings of this mode.
The danger: A malicious app can enable Do Not Disturb mode as required so that the smartphone owner misses important calls or messages — for example, a call from your bank regarding a particularly suspicious transaction.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Do Not Disturb access
Display over other apps
What it is: This permission allows the app to display its own windows on top of any other apps.
The danger: Malicious apps can hide important warnings from view, and also superimpose fake forms for entering credit-card details or passwords over legitimate app windows. This permission is one of two key mechanisms used in so-called Cloak & Dagger attacks.
Also, this permission is widely used by adware to shove ads into users’ faces more effectively, and by blockers, ransomware that overlays a phone’s interface with its own window and demands ransom for getting rid of it.
All in all, most apps should not be given this permission.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Display over other apps
VR helper services
What it is: This permission allows apps access to virtual reality apps and devices, as well as the ability to run in the background while the user has VR apps open.
The danger: Aside from the ability to run in the background, which is something malware highly appreciates, this permission doesn’t look really dangerous. However, we recommend denying it to apps that have nothing to do with VR, just in case.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> VR helper services
Modify system settings
What it is: Android has two types of system settings: common and global. Note that all of the really dangerous settings have migrated to the latter category, and secondary options such as changing the brightness or sound level belong to the former. Permission to modify system settings allows apps to change the common settings, but not the global.
The danger: It sounds risky, but it’s actually a fairly harmless permission. There is nothing genuinely dangerous left in the settings that can be changed with this permission.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Modify system settings
Notification access
What it is: This permission is for processing notifications. For example, Google Wear needs it to forward notifications to your smartwatch. It is also used by the launcher — Android’s “home app” — to display pop-up notifications on the desktop next to the relevant app icons.
The danger: Lots of confidential information (SMS and IM messages, etc.) finds its way into notifications. If a spyware app or banking Trojan were to take a peek, it might learn things you’d rather keep to yourself. This permission should not be handed out to random apps.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Notification access
Picture-in-picture
What it is: Android allows apps to output video in picture-in-picture (PIP) mode, where it appears as a small window in the lower-right corner of the screen displayed over the windows of all other apps.
The danger: Same as the Display over other apps permission. For example, a malicious app can use it to hide an important warning, and adware can use it to deliver ads. PIP permission should be given only to apps that you fully trust.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Picture-in-picture
Premium SMS access
What it is: Google has a list of premium SMS service numbers in different countries worldwide. If an app attempts to send an SMS to a number in this list, the system prompts the user for permission.
The danger: Entire families of malware earn their crust by secretly subscribing users to premium SMS services. It’s not clear how comprehensive the Google’s list is, but it probably guards against the most common Trojan subscribers at the very least.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Premium SMS access
Unrestricted data access
What it is: To save mobile data and battery charge, Android lets you configure which apps can use data transfer in background mode (customized for each app individually — there is no full list for this setting with easily checkable boxes).
In addition, Android has the stricter Data Saver mode (Settings -> Network and Internet -> Data Usage -> Data Saver). When this mode is enabled, data transfer in the background is turned off for most apps. For an app to continue to have access to data transfer when Data Saver is activated, it must request this permission.
The danger: Background data transfer in strict data-saving mode is generally required only by communication apps (messengers, e-mail clients, social networks) to ensure the prompt delivery of messages.
If this permission is requested by an app that has nothing to do with communication, stop and ask yourself whether it might be trying to spy on you.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Unrestricted data access
Usage access
What it is: This permission allows apps to access your device’s metadata: for example, what apps you use and how often, who your operator is, what language is set in your phone, and so on.
The danger: This permission does not give the app any private data as such. However, indirect data about smartphone use can be used to compile a sufficiently unique digital fingerprint, which could be handy for surveillance.
Aside from that, banking Trojans use this function to detect which app is currently running and to overlay it with a phishing windows crafted for that specific app (for example, the app of a certain bank).
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Usage access
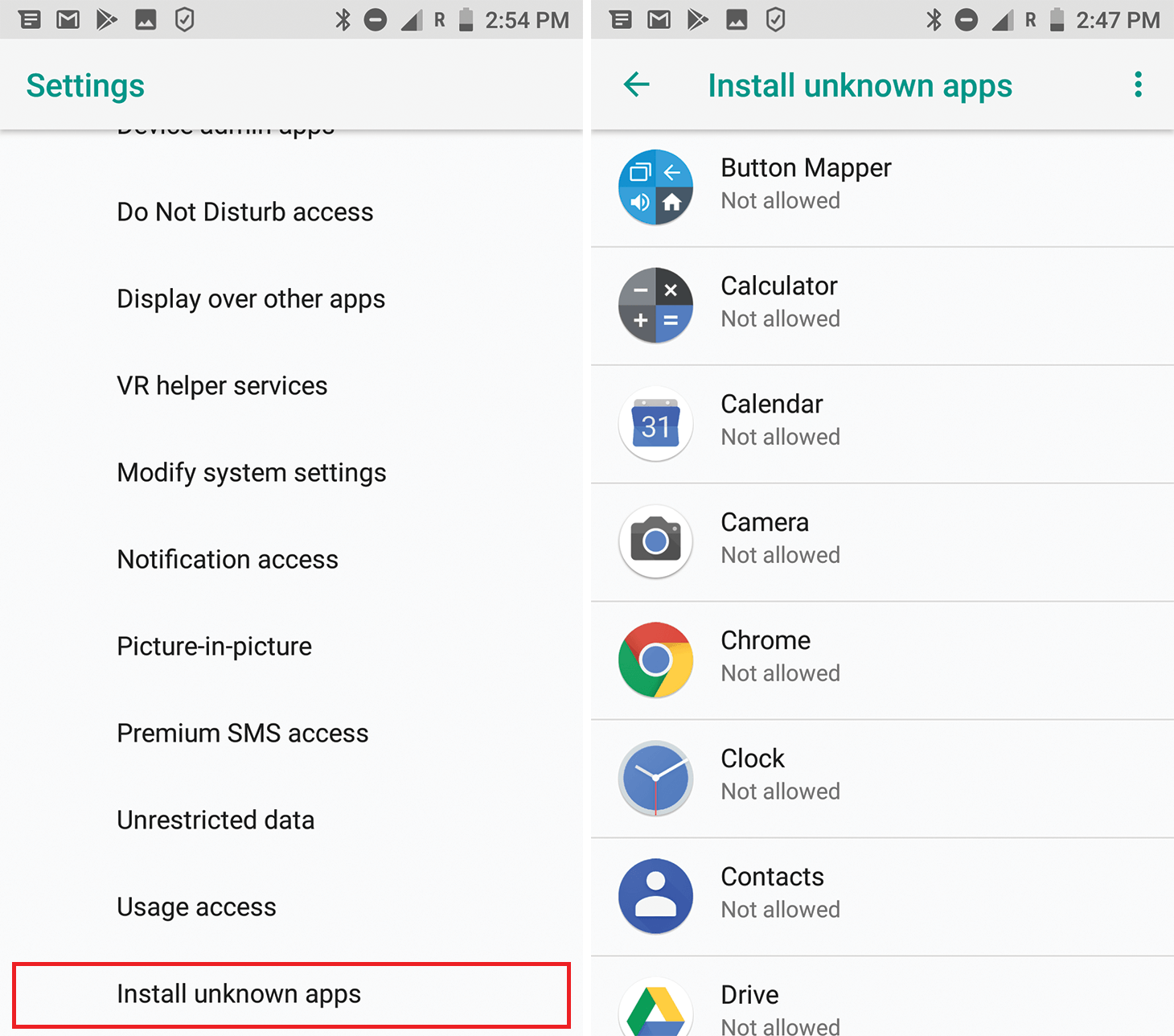
Install unknown apps
What it is: Essentially this is the same as the Install from unknown sources permission in earlier versions of Android. But whereas before it was just one check box, the Android 8 settings are more complex. Now individual apps can request the right to install other apps, which you can allow or block for each of them. For example, you could grant this permission only to the file manager (that’s not recommended, incidentally).
The danger: Even Google Play is occasionally hit by malicious apps. As you can imagine, when it comes to programs downloaded from who knows where the situation is much worse. We recommend blocking the Install unknown apps permission for all apps on your smartphone — especially the browser, to protect yourself against automatic downloading and installation of malware from hacked sites.
If you really need to install something not from an official store (think more than twice before doing so), don’t forget to restore the block immediately after installing the app. And always scan unknown apps with a reliable antivirus such as , which can be installed free of charge.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Special app access -> Install unknown apps
Individually configured permissions
In addition to the App permissions and Special app access settings sections, Android 8 has several important permissions that should be noted. These permissions, if misused, can be even more dangerous than those in the preceding two sections. They should never, ever be given to random apps.
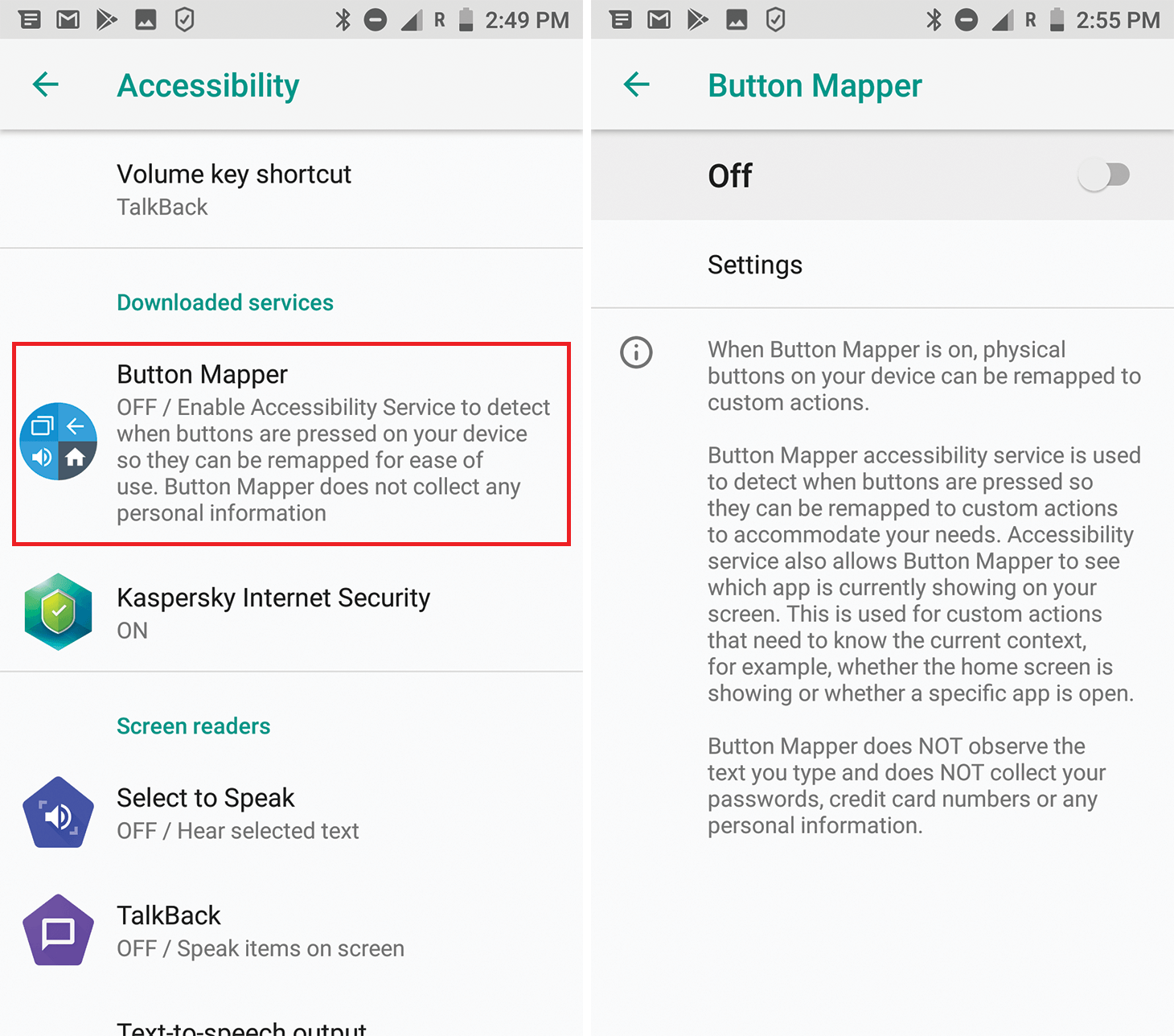
Accessibility
What it is: A powerful set of features originally created to make life easier for visually impaired users. For example, Accessibility allows an app to read aloud everything that happens on the screen, and the converse, to implement user voice commands through a graphical interface.
The danger: This set of features allows an app to access what is happening in other apps, thus violating Android’s isolation principle.
A malicious app can use Accessibility to spy on what you are doing, and basically do what it likes with the graphical interface — literally click any buttons. For example, it can change settings, confirm actions, or even buy apps on Google Play. This set of features is one of the two key mechanisms employed in Cloak & Dagger attacks.
Where it’s configured: Settings -> Accessibility.
Requesting Accessibility permissions is not always a direct sign of malicious activity. Some legitimate apps do so with good reason. For example, mobile antiviruses need it to detect suspicious behavior in other apps before it’s too late and Accessibility helps them to do so. But in general, before giving an app Accessibility permissions, it’s a good idea to think it through; the consequences can be very unpleasant indeed.
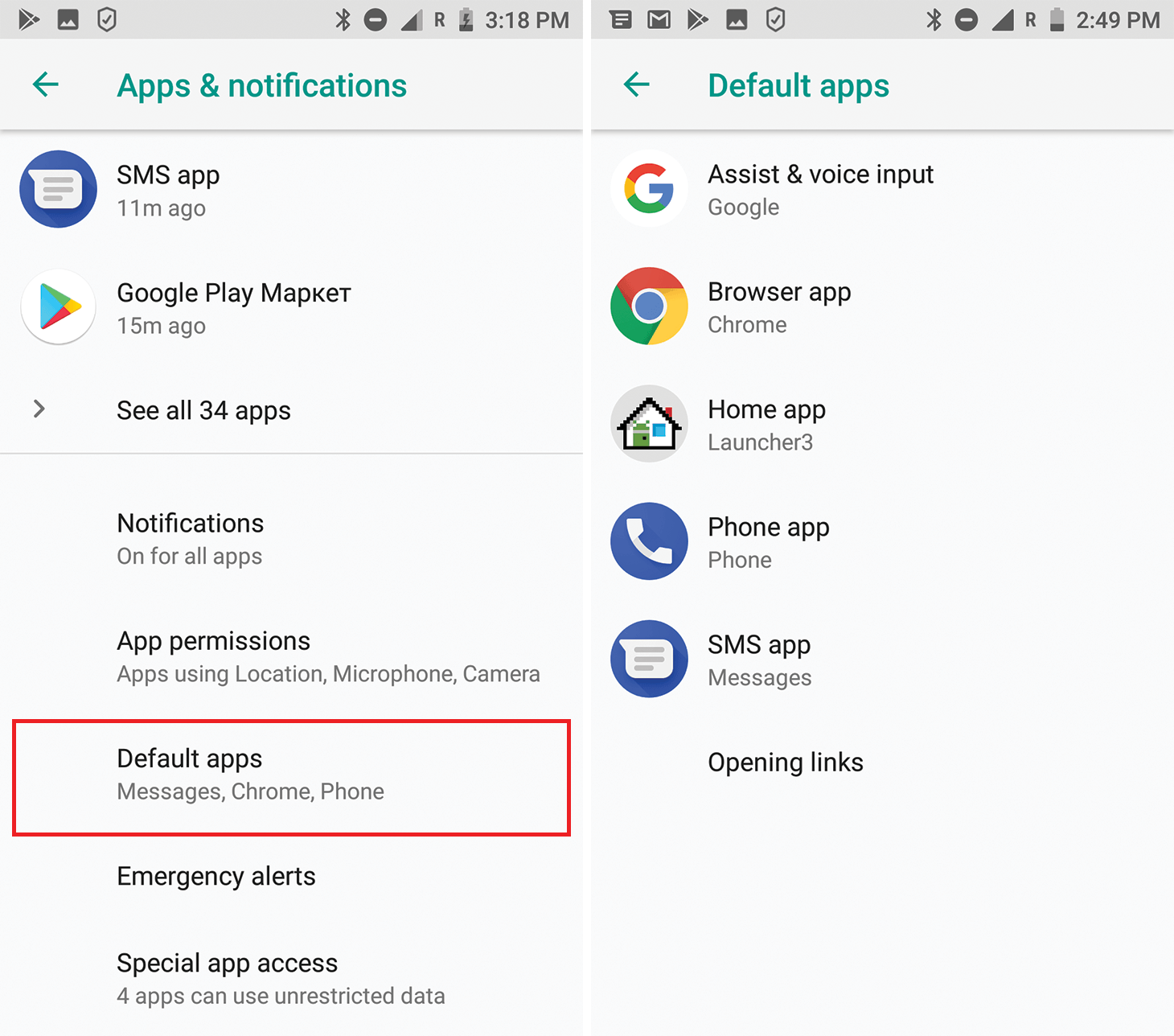
Default apps
What it is: Another list of permissions implemented as a separate settings section and worthy of particular attention. Android has a set of default apps used for key smartphone functions:
• Assist & Voice input — a default voice-controlled assistant app, like Google Assistant.
• Browser app — an app for displaying Web pages.
• Home app (also called the launcher) — a graphical shell that handles the app menu, desktop, widgets, etc.
• Phone app — an app for making calls.
• SMS app — for everything SMS-related.
For an app to become a default, user permission must be requested and obtained.
The danger: Many banking Trojans would dearly love to be the default SMS app, letting them hide notifications about bank withdrawals and steal one-time confirmation codes.
Note that this ruse has already been perfected by most banking Trojans and is commonly used by cybercriminals. Unpleasant scenarios involving the use of default apps are plenty, so think very carefully before granting an app default status.
Where it’s configured: Settings -> Apps & notifications -> Advanced -> Default apps.
Root privileges
What it is: A superuser is like a superhero: someone with superpowers which, combined with the right skills, let them bypass all of Android’s numerous security mechanisms and do almost anything they like with the operating system. On a rooted smartphone (one with superuser rights), it is possible to change any setting, gain access to any file (including system files), delete and install any apps from any source, install any firmware, and the list goes on.
The danger: It’s not only the user receiving root privilege superpower; any apps installed on the smartphone get it as well. And apps can take advantage of that status to steal smartphone data and engage in spying and other harmful activities.
Whereas all of the abovementioned permissions give access to some of the data and functions generally provided for in the Android operating system, root privileges grant access to data and functions that were never intended to be shared. Not to mention that an app with root access can automatically configure all permissions as it pleases.
So think carefully before going ahead and rooting your smartphone. If malware capable of using root privileges gets into the system, the consequences can be far nastier than in the case of an unrooted Android device. Find out more in our post Rooting your Android: Advantages, disadvantages, and snags.
Besides, even if you don’t root your own smartphone, someone else might do it to you. For example, when spyware apps are installed on a victim’s device, their developers recommend or even require getting root privileges in advance. What’s more, some Trojans are able to get root privileges through exploiting vulnerabilities in Android. It is worth checking from time to time whether your smartphone has been rooted without your knowledge.
Where it’s configured: Acquiring superuser rights is not a standard Android feature and cannot be configured in the operating system. Moreover, it is not even possible to check whether your phone is rooted using standard OS facilities. Instead, you can use one of several apps specially created for checking root access (choose the app carefully though).
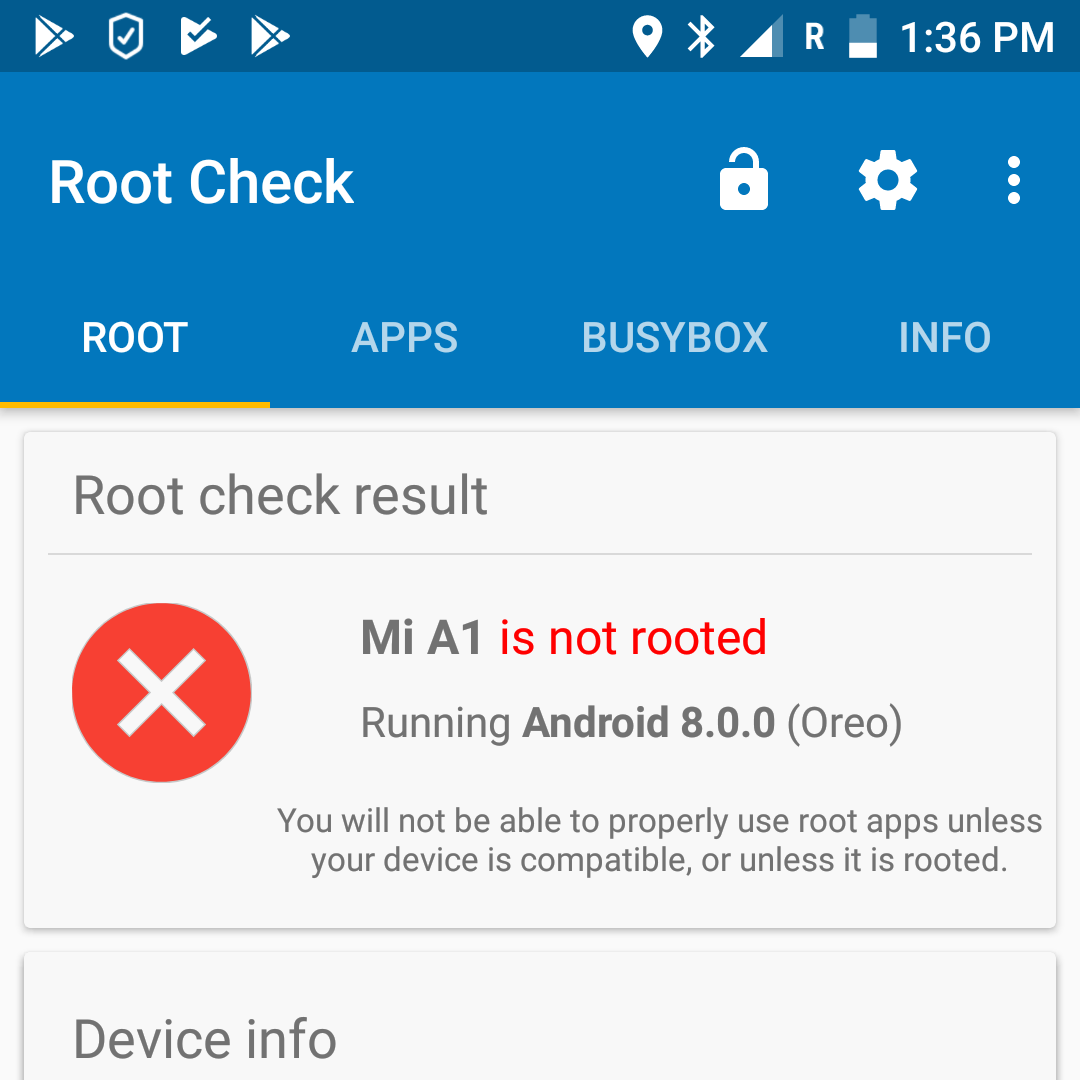
The root access check is a rare case when a red message means everything is fine: superuser rights on this smartphone have not been acquired
If the check shows that your smartphone is rooted, but you didn’t do anything to it, it’s a sure sign that something nasty is lurking inside. Maybe you were unlucky enough to download a Trojan, or perhaps someone installed a spyware app to keep tabs on you. In this case, we recommend saving personal files elsewhere and ridding your device of root access — different methods work for different phones.
How to configure app permissions
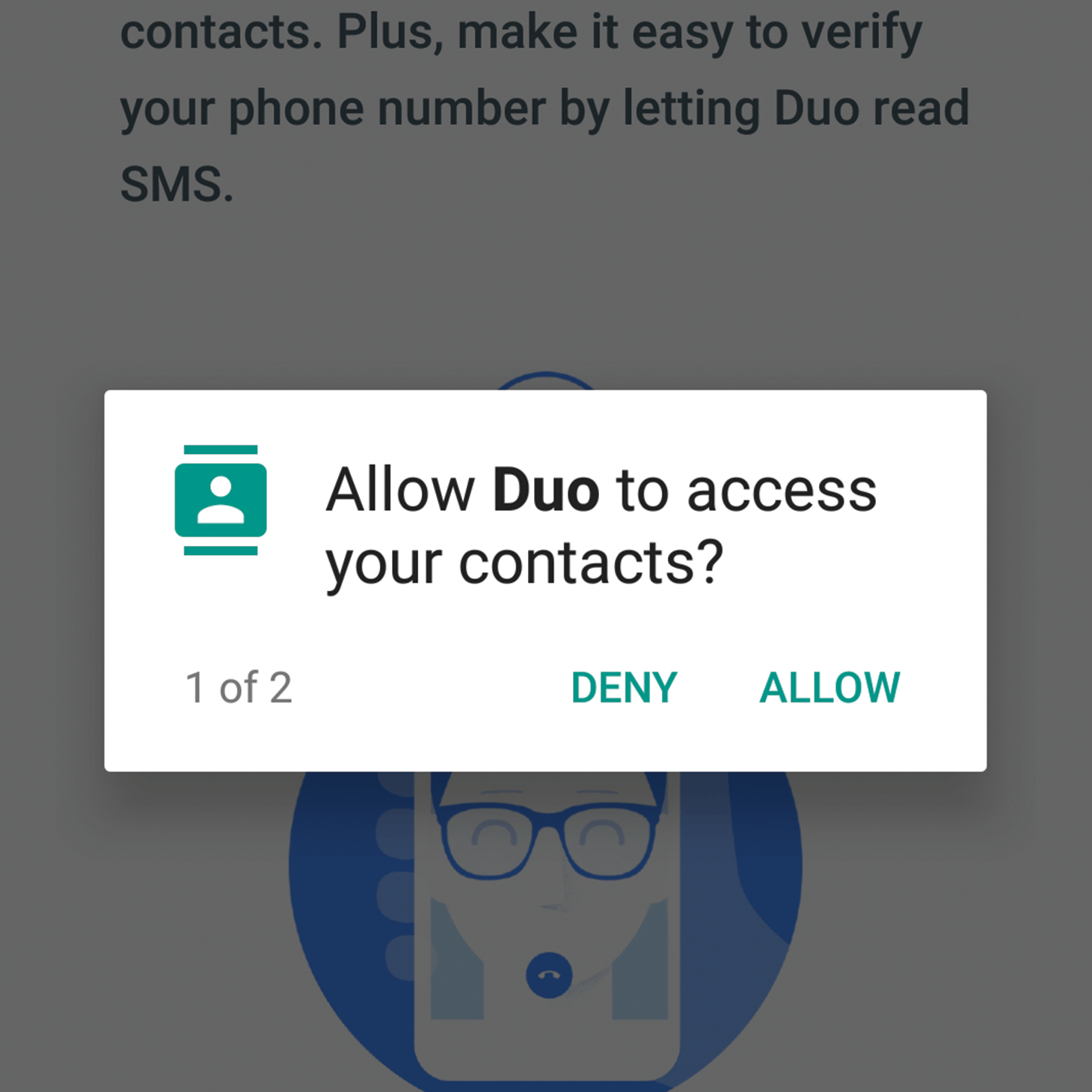
There are several ways to configure app permissions in Android. First, apps request permissions when corresponding features are about to be used — you can grant or deny them. In Android 8, such requests look something like this:
Second, you can use groups of permissions to view a full list of apps that have requested, might request, or have already received a particular permission. If something looks suspicious among the permissions already given, you can revoke them right away. See above for details of where to do this for each permission.
Third, another option is to see what permissions each installed app already has and what it might someday request. Again, you can revoke any permission from an app if something doesn’t look right — just be prepared for something in the app to stop functioning properly.
By the way, the Android 8 settings feature a handy search system for locating any item in the settings menu (as long as you know what it’s called), including setting pages for each of the apps, which can be found using their names.
Conclusion
As we have seen, Android 8 can be easily and flexibly configured to protect your valuable information and prevent data-hungry or outright malicious apps from gaining access to the most sensitive operating system functions. Make use of this flexibility, always think about the consequences of giving certain permissions, and don’t be afraid to deny access if something looks suspicious.
In many cases, apps request permissions they don’t actually need for normal operation. Don’t worry — if you refuse, nothing terrible will happen.
“I need your clothes, your boots, and your motorcycle.”
“No.”
“OK, sorry to bother you. Have a nice day.”
 Android
Android

 Tips
Tips