Kaspersky Lab has launched a new visual tool dedicated to real-time monitoring of APTs – “Targeted Attacks Logbook”.
Aside from looking extremely pretty, it provides brief, yet exhaustive data on every advanced persistent threat known today. Let’s take a look at what it offers and how it works:
#TargetedAttacksLogbook: new visual tool by @Kaspersky
Tweet
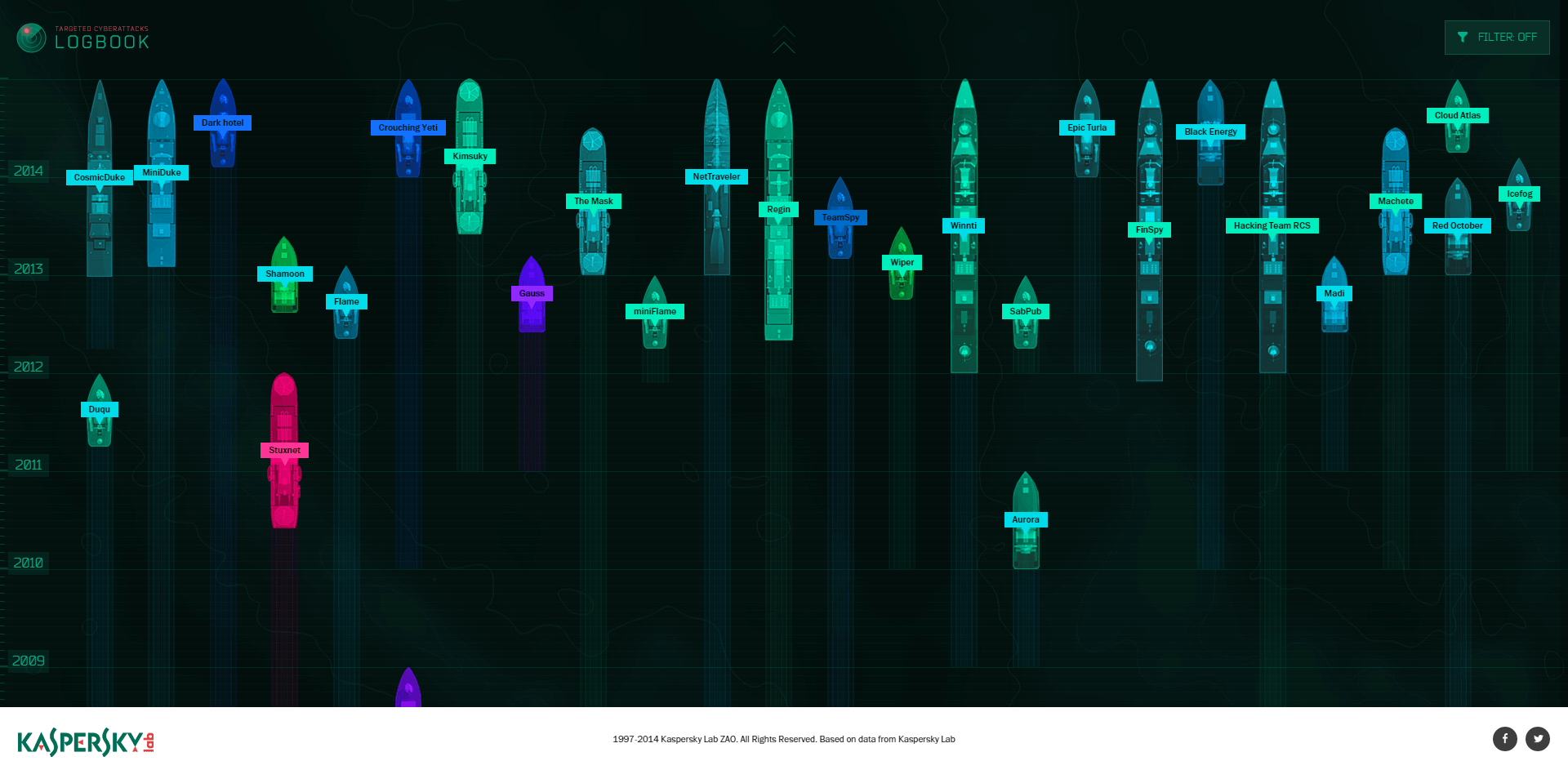
The first screen shows the APTs as a large fleet of military vessels afloat over time, with their stern wakes’ length indicating how long the threat has been active. The length of the vessel is a time period between its discovery and “current status” – i.e. is it currently active or not. Those with bows ahead in 2014 are still active, the rest are not. Unfortunately, most of them are active now, including the last one disclosed – Regin campaign, which was discovered back in 2012, and apparently had been active since 2003.
Now, if we roll the mouse over certain “vessels”, for instance that pretty Flame motor boat, we will see the ties between this particular APTs and some others – Gauss, Duqu, miniFlame and Stuxnet, with the last one looking a lot like a submarine.
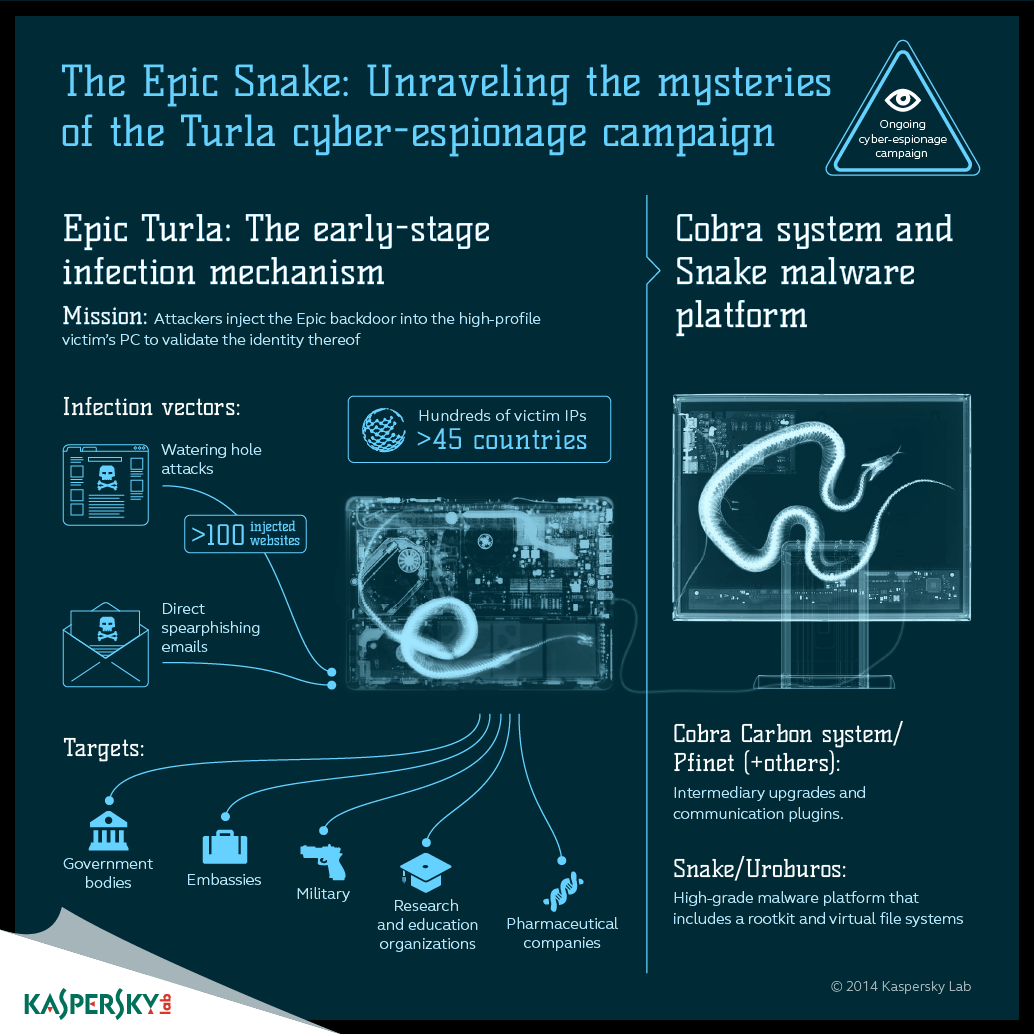
As we all know, if it wasn’t for a coding mistake, Stuxnet would have never been discovered and the history of APTs would look a bit different – although at least two of the APTs were known earlier: Agent.btz and Aurora. Agent.btz, by the way, has certain links to Epic Turla, the big bad campaign, that is still becoming bigger and, well, “badder” as new data arrives.
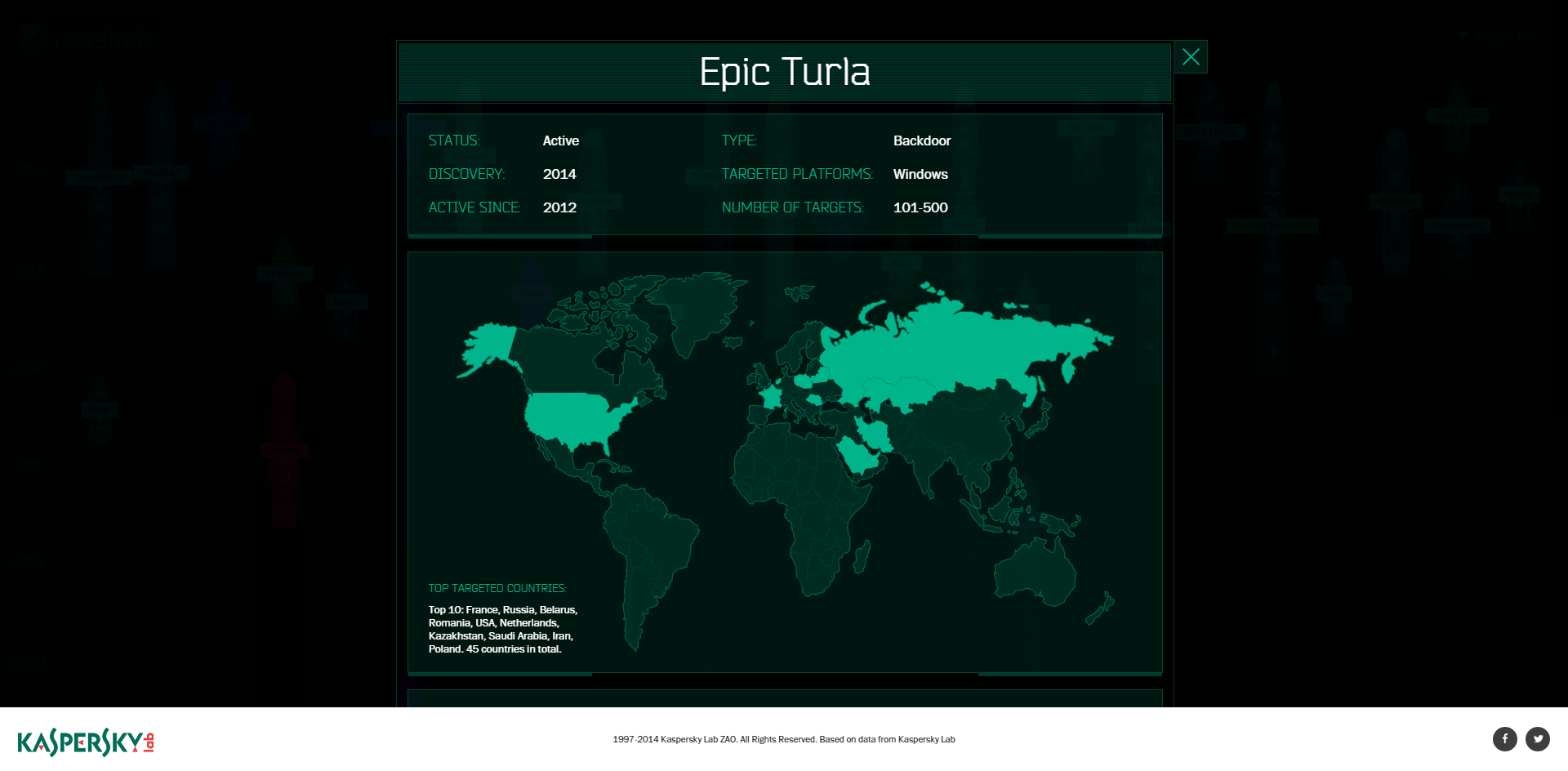
If we click on Epic Turla, we’ll see its status, type, time of discovery, longevity, number of targets, targeted platforms, and a map of the most affected countries.
Below is additional data on the threat, including the way of propagation, purpose, special features and identified targets along with artifacts that point to possible attribution.
And then there is a link to Securelist’s detailed research on the threat.
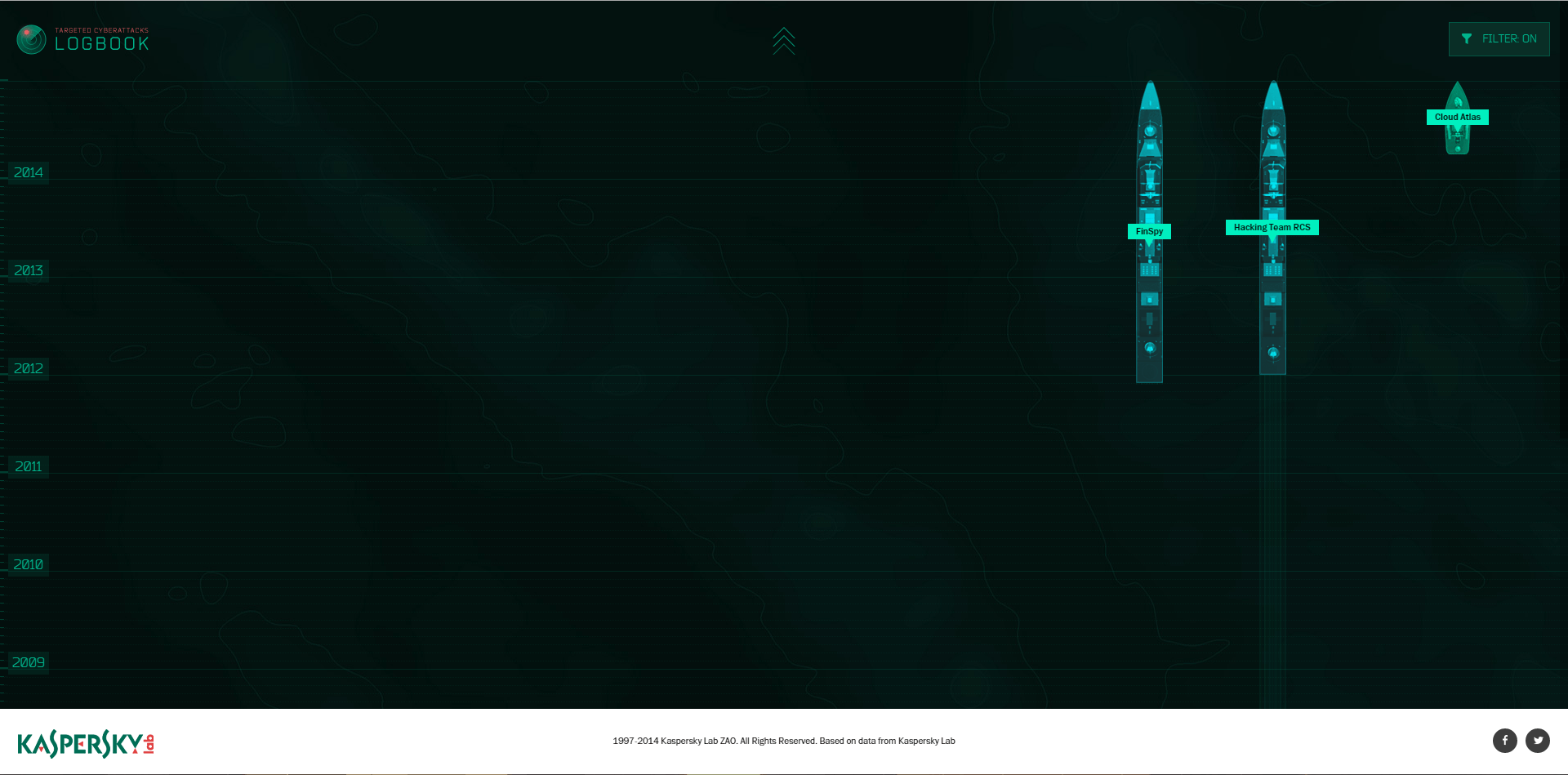
Back to the main screen, we see a “filter” that allows us to pick out the APTs based on a number of features. For instance, if we want to see what APTs are targeting iOS – quite an exotic query, right? – we can set this preference and we’ll see two “destroyers” and one “missile boat”:
These are FinSpy, Hacking Team RCS, and the newly discovered Cloud Atlas – the successor to notorious RedOctober APT. All three are targeting iOS devices among other platforms. And Hacking Team RCS appears to have been active since 2008.
The term ‘APT’ was coined back in 2006, but despite attempts to make it clear and exhaustive, it is still quite vague. This is largely because the term Advanced Persistent Threat was meant to designate attacking entities – hacking groups, hostile cyber warfare units, etc., but the term has somewhat slid towards designating the malware used by APT groups and the campaigns they wage, correctly or not.
We previously published a couple of blogposts [1, 2] explaining what APTs are.
In a nutshell an APT is a threat posed by skilled, motivated, organized, and well-funded cyber-attackers. It is called “advanced” since operators behind the threat have a full spectrum of intrusion, intelligence-gathering, and data stealing tools at their disposal. These tools are usually custom-made, although partial “code intercrossing” between different APTs isn’t uncommon.
It is also called persistent because attackers give priority to a specific task such as exfiltration of certain data from particular entities. They don’t seek information opportunistically, as common criminals do. Besides, the attacks are anything but one-offs: usually they are continuous, staying active for years, as illustrated above. Operators prefer a stealthy, hushed approach, and they try to keep access to the target’s infrastructure for as long as possible without being discovered.
Kaspersky Lab experts assume that in the near future, a wider range of cybercriminals will adopt APT tactics since the continuous malicious presence in the compromised infrastructure may bring a larger profit than the one-off attacks.
 APTs
APTs

 Tips
Tips