Information security has multiple layers of complexity. Effective yet technically simple attacks through phishing emails and social engineering are well known about. We also often post about sophisticated targeted attacks that exploit vulnerabilities in enterprise software and services. And among the most sophisticated are attacks that exploit fundamental hardware features. Although such attacks aren’t cheap, the cost doesn’t deter all threat actors. Or at least researchers.
Researchers at two US universities recently published a paper with a fascinating example of an attack on hardware. Using the standard operating system feature for switching between tasks, the researchers developed an attack they named Sleepwalk, which can crack a cutting-edge data encryption algorithm.
Side-channeling — sleep-walking
Sleepwalk is a type of side-channel attack. In this context, “side channel” typically refers to any method of stealing secret information by indirect observation. For example, imagine someone is typing a password on a keyboard. You can’t see the letters/symbols, but you can hear the keys being pressed. This is a feasible attack in which the sound of the keystrokes — the side channel — reveals what text is being typed. A classic example of a side channel is monitoring changes in the power consumption of a computer system.
Why does power consumption vary? Simple: different computing tasks require different resources. Serious number crunching will max out the load on the CPU and RAM, while typing in a text editor will see the computer mostly idle. In some cases, changes in power consumption give away sensitive information, such as private keys for data encryption. This is similar to how a few barely audible clicks can reveal the correct rotor positions to pick the combination lock on a safe.
Why are these attacks sophisticated? Because a computer performs multiple tasks simultaneously. And all of them affect power consumption in one way or another. Extracting useful information from this noise is a highly complex job. Even when analyzing the simplest devices such as smart card readers, researchers take hundreds of thousands of measurements in a short period, repeating them tens or hundreds of times, then apply sophisticated signal-processing methods to confirm or refute the possibility of a side-channel attack. Sleepwalk in a sense simplifies this work: the researchers were able to extract useful information by measuring the pattern of power consumption just once, during a so-called context switch.
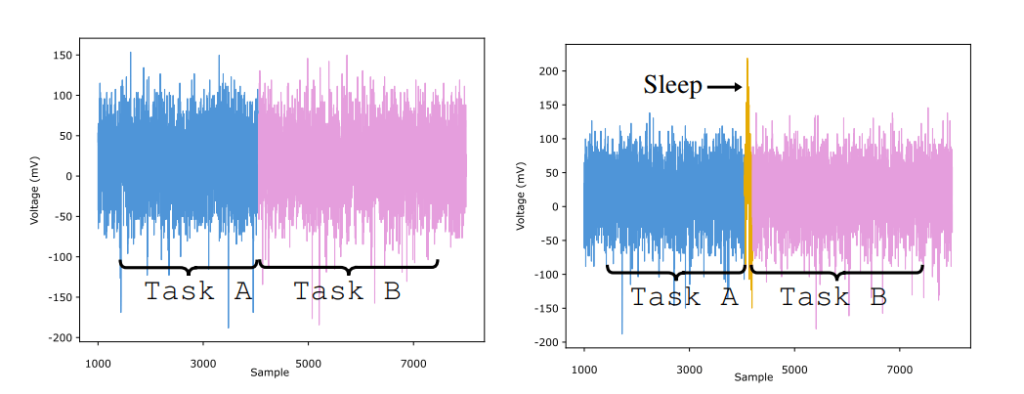
Voltage fluctuations during CPU context switching. Source
Context switching
We’re all used to switching between programs on a computer or smartphone. At a deeper level, such multitasking is enabled by various mechanisms behind the scenes, one of which is context switching. The state of one program is saved, while data from another is loaded into the CPU. The decision on which program to give priority to, and when, is made by the operating system. That said, there’s a simple way for a programmer to force a context switch by adding a sleep instruction to the program code. The operating system then sees that the program doesn’t require CPU power for the time being, and switches to another task. Context switching, especially when the sleep function is called, is an energy-consuming activity that requires saving the state of one program and loading data from another into the CPU. The screenshot above shows a spike in the measured voltage during such a switch.
As it turns out, the nature of this power spike is determined both by the task that was running before and by the data being processed. Essentially, the researchers hugely simplified implementing a side-channel attack in which the system’s energy consumption is measured. Instead of measuring over a long period, a single spike is analyzed at a predetermined time. This serves up indirect data of two types: what program was running before the switch, and what data was being processed. All that remains is to carry out the attack according to the scheme below:
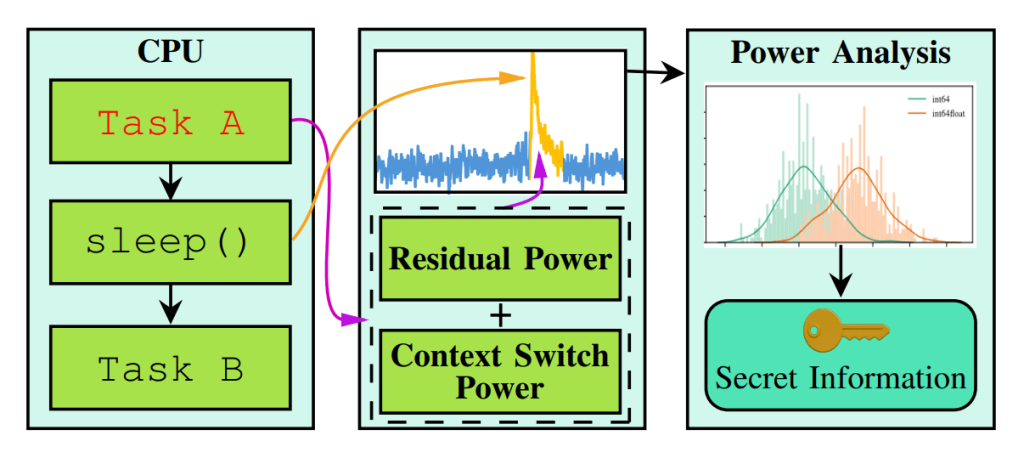
Outline of the Sleepwalk attack Source
Sleepwalk attack in the real world
The researchers did their experiments on a single-board Raspberry Pi 4, demonstrating first of all that the power spike produced by different computing tasks during context switching has a unique fingerprint. Let’s suppose that this computer is performing data encryption. We can feed any text to the encryption algorithm as input, but we don’t know the key for encrypting the data.
What if we trigger a context switch at a specific point in the encryption algorithm’s operation? The operating system will save the state of the program, causing a spike in power consumption. Using an oscilloscope to repeatedly measure the nature of this spike, the researchers were able to extract the secret key!
That was just one of many important things learned in the experiment. They also succeeded in fully reconstructing a SIKE private key. The fairly new encryption algorithm SIKE is proposed as a replacement for traditional algorithms to protect data even in the quantum age. Yet despite its apparent innovativeness, questions are already being asked about the algorithm’s strength. Moreover, to extract the secret key, the researchers didn’t just carry out a Sleepwalk attack, but also exploited a weakness in the algorithm itself.
The Sleepwalk attack was unable to fully crack the traditional and reliable (but not post-quantum) AES-128 algorithm. But the team was able to reconstruct 10 of the 16 bytes of the private key — and this in itself is an achievement since Sleepwalk is somewhat simpler than other side-channel attack methods.
Sure, there’s no talk yet of deploying Sleepwalk in practice. The researchers merely wanted to demonstrate that power spikes during context switching can reveal secret information. Which they did. But bad guys one day might be able to develop the attack so as to steal real secrets — be they from a computer, secure flash drive, or crypto wallet.
As result of this research, existing and in-development encryption algorithms should become a little more reliable. Not only that, the Sleepwalk attack indirectly points up a key aspect in the implementation of cryptographic systems. Future algorithms will need to be resistant to analysis using quantum computing (so-called “post-quantum cryptography”); but no less vitally, this will need to be done correctly. Otherwise, a new, theoretically more secure algorithm may turn out to be more vulnerable to traditional attacks than a pre-quantum one.
 side-channel attack
side-channel attack
