Kaspersky Lab’s researchers have discovered what is possibly should be called “mother of all APTs”: the Equation group has already been compared to Death Star in the APT universe. The research on The Equation group was presented February 15th at Kaspersky Security Analyst Summit.
What’s going on?
Equation is an APT which likely has been active for two decades already. Some C&Cs used by the group appear to have been registered as early as 1996, although presumably main command and control server dates back to August 2001.
Massive, Decades-Long Cyberespionage Framework Uncovered – http://t.co/GxpNfmktuf #TheSAS2015
— Threatpost (@threatpost) February 16, 2015
Since 2001, the Equation group has been busy infecting thousands, or perhaps even tens of thousands of victims throughout the world, in the following sectors:
- Government and diplomatic institutions
- Telecoms
- Aerospace
- Energy
- Nuclear research
- Oil and gas
- Military
- Nanotechnology
- Islamic activists and scholars
- Mass media
- Transportation
- Financial institutions
- Companies developing encryption technologies
The Equation group uses a potent arsenal of “implants” (they apparently call their Trojans that way), only some of which are currently known.
The array is astonishing, but…
Perhaps the most powerful tool in the Equation group’s arsenal is a mysterious module known only by a cryptic name: “nls_933w.dll”. It allows them to reprogram the hard drive firmware of over a dozen different hard drive brands, including Seagate, Western Digital, Toshiba, Maxtor and IBM.
Vendors affected by nls_933w.dll #EquationAPT #TheSAS2015 Format won't help! pic.twitter.com/X8zxWEzje6
— Dmitry Bestuzhev (@dimitribest) February 16, 2015
This is an astounding technical accomplishment and a clear indication of the group’s exceptional abilities.
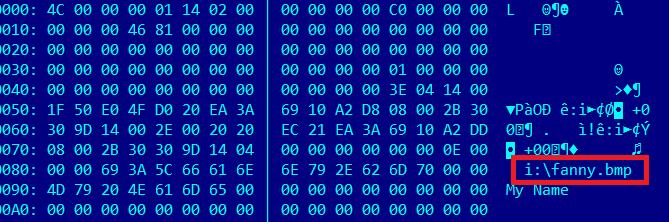
Fanny-wormy
Among other attacks apparently performed by Equation one stands out: the Fanny worm, first observed and blocked by Kaspersky Lab’s systems in December 2008. It used two 0day exploits, those were yet to be discovered then.
These exploits were used by Stuxnet worm. And, vice versa, Fanny used Stuxnet LNK exploit and USB sticks. For escalation of privilege, Fanny used a vulnerability patched by the Microsoft bulletin MS09-025, which was also used in one of the early versions of Stuxnet from 2009.
To clear up the confusion…
Yes, the Fanny worm, first reported in 2008, used the 0day exploits two year prior Stuxnet used them, and until 2010 they remained unknown. It looks like Equation had access to these zero-days before the Stuxnet group .
“For many years they [Equation group] have interacted with other powerful groups, such as the Stuxnet and Flame groups; always from a position of superiority, as they had access to exploits earlier than the others”, Kaspersky Lab researchers said.
Kaspersky Lab is currently publishing data on Equation APT. So far there is a general overview of this group and its tools available at Securelist, as well as a detailed research on Fanny worm. Updates will follow, so stay tuned!
 EquationAPT
EquationAPT

 Tips
Tips