Public studies aren’t fear-mongering, however some cybersecurity-related news may make one feel uneasy. That’s the case with the Kaspersky Lab’s Global Research & Analysis Team (GReAT) field study of the security of hospitals’ IT systems. As one may have already guessed, the situation there is, let’s say, not good.
The reason for this research is practical. As GReAT’s Sergey Lozhkin writes in his report at Securelist, the year 2016 started with a number of security incidents related to hacks of hospitals and medical equipment.
“They include a ransomware attack on a Los Angeles hospital, the same in two German hospitals, a case of researchers hacking a patient monitor and drug dispense system, an attack on a Melbourne hospital and so on – in just two months of 2016! This should be a real concern for the security industry.”
Indeed.
One could expect as much
Unfortunately, it is not a surprising development. Hospitals are very attractive targets for cybercriminals: lots of data, including the patients’ personal information; also lots of internet-connected devices, including specialized medical equipment, not just PCs and staff’s and patients’ handhelds.
Mr. Lozhkin’s research proved that attackers can gain full access to the entire medical infrastructure.
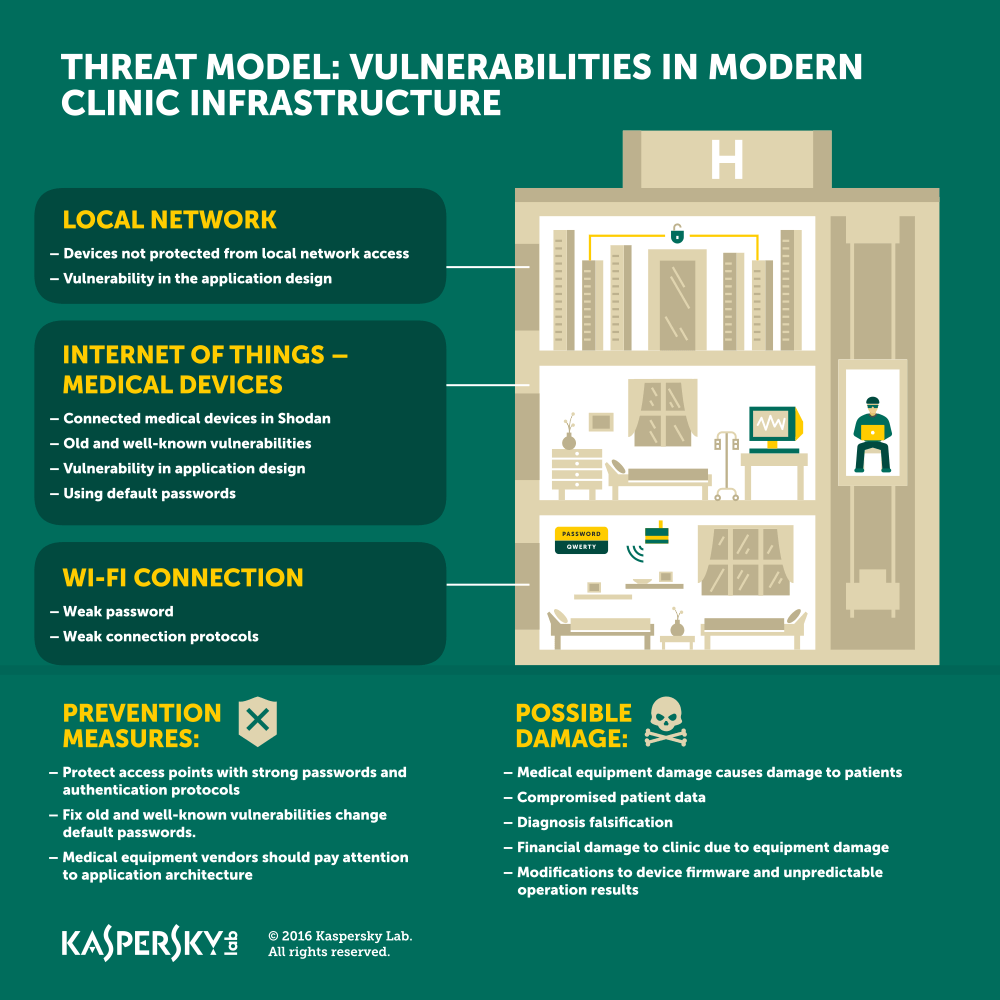
“Imagine a scenario – one that could be called a truly “targeted attack” – whereby cybercriminals with full access to the medical infrastructure at a specific facility can manipulate the results of diagnosis or treatment systems. Because doctors in some cases will depend heavily on these sophisticated medical systems, such manipulation could result in the wrong treatment being given to a patient, worsening his or her medical condition.”
If it sounds like a scenario from some ‘Mission Impossible’ movie, i.e. unrealistic, we have to state regretfully that it is actually very realistic.
And at the recent Kaspersky Security Analysts Summit Sergey Lozhkin presented his research showing how easy it was to find a hospital, get access to its internal networks, and gain control of an MRI device – locating personal data about patients and their treatment procedures, and then getting access to the MRI device file system.
“The problem is not only one of weak protection of medical equipment, it has a much wider scope – the whole IT infrastructure of modern hospitals is not properly organized and protected, and the problem persists worldwide”, Lozhkin says.
His report for Securelist is available here.
Below is 10-minute video interview with Mr. Lozhkin regarding his presentation at the SAS 2016.
Internet of scary things
The reason for this problem is rather familiar: while the industry of internet of things – which means that next to every new electric and electronic device is getting network-enabled for whatever reason – is on the rise, cybersecurity isn’t (yet) perceived as a competitive advantage.

Modern medical devices are, in fact, fully-functional computers with operating systems and apps installed on them. These devices and their software are written with their primary goal in mind (i.e. medical treatment), but the cybersecurity aspects are often overlooked.
This is highly characteristic of the entire IoT industry: the same has been observed before with cars and their infotainment systems.
With medical equipment, however, the level of peril is even higher than with cars, as there’s not much sophistication required to conduct an attack on them.
As Mr. Lozhkin has shown, all it actually takes is Shodan search engine, which allows for the finding of thousands of medical devices exposed – in all meanings – to the Internet.
“…A hacker could discover MRI scanners, cardiology equipment, radioactive medical and other related equipment connected to the Internet. A lot of these devices still operate under the Windows XP OS and have dozens of old, unpatched vulnerabilities that could lead to the full compromise of a remote system. Moreover, in some cases these devices have unchanged default passwords that could easily be found in manuals published on the Internet”, – Sergey Lozhkin writes.
Yes, default passwords are there. At the life-saving equipment. Because – “who would ever want to hack MRI device?”…
Lozhkin also mentions that these devices aren’t protected from being accessed from local networks too, and have their share of vulnerabilities in software as well.
Neglecting even basic security measures – either by the equipment developers or users or both – becomes an issue of dramatic proportions and consequences if the worst scenario becomes a reality. Even if no serious damage to patients’ health is inflicted, from the business angle, the “hackability” of medical equipment and hospital infrastructure is also a tremendous reputation risk.
Kaspersky Lab experts recommend implementing the following measures to protect clinics from unauthorized access:
• Use strong passwords to protect all external connection points;
• Update IT security policies, develop on time patch management and vulnerability assessments;
• Protect medical equipment applications in the local network with passwords in case of an unauthorized access to the trusted area;
• Protect infrastructure from threats like malware and hacking attacks with a reliable security solution;
• Backup critical information regularly and keep a backup copy offline.
 healthcare
healthcare
