No need for sophistication
At the end of 2015, Kaspersky Lab’s Global Research and Analysis Team (GReAT) made a series of predictions about changes to the threat landscape that are to be expected in the immediate future. One of the key trends highlighted was the simplification and cost-effectiveness of targeted attacks. This would involve the (re)use of off-the-shelf malware, legitimate free or commercial software – and the leveraging of failures in corporate IT security implementation. Sadly, the level of these failures never seems to decrease, despite all the efforts made by IT security vendors and the community at large.
One of the most popular techniques used to penetrate corporate defenses is the use of vulnerabilities found in working software, which, in fact, do not need to be brand-new 0-days. Even security holes with a ‘critical’ rating, allowing the execution of arbitrary commands on targeted endpoints, too often remain unpatched, offering cybercriminals and digital spies a virtually open door into the systems that interest them. This is even more true if the organization fails to implement a proper multi-layered security system, with highly efficient detection mechanisms working on different infrastructure levels. Some vulnerabilities are still being exploited by attackers months and even years after the release of their respective patches – because they still can yield positive results when used against careless victims who have failed to patch them.
Read the Attachment, Please!
A good example of an older vulnerability getting increasingly popular with both cybercriminals and cyber-espionage masterminds is CVE-2015-2545, an MSOffice security hole allowing arbitrary code execution through the use of a specially prepared Encapsulated PostScript (EPS) image file. Discovered by security researchers in March, 2015, it remained unpatched for 4 months. Then Microsoft issued a patch (MS15-099), ending the matter for everyone keen on maintaining a strong security posture. But during this time, the existence of the vulnerability provided an excellent opportunity for hackers.
In August, 2015, the first known attempts to use CVE-2015-2545 for targeted attacks, made by the Platinum (TwoForOne) group, were discovered. In September the vulnerability was, at last, patched by Microsoft, effectively stopping Platinum from using it. But other hackers now increased their efforts against those who left the vulnerability unpatched, trying to develop their own techniques to leverage it. Presumably, they reverse-engineered the patch and, having obtained a detailed knowledge of the security hole, they created new exploits for it.
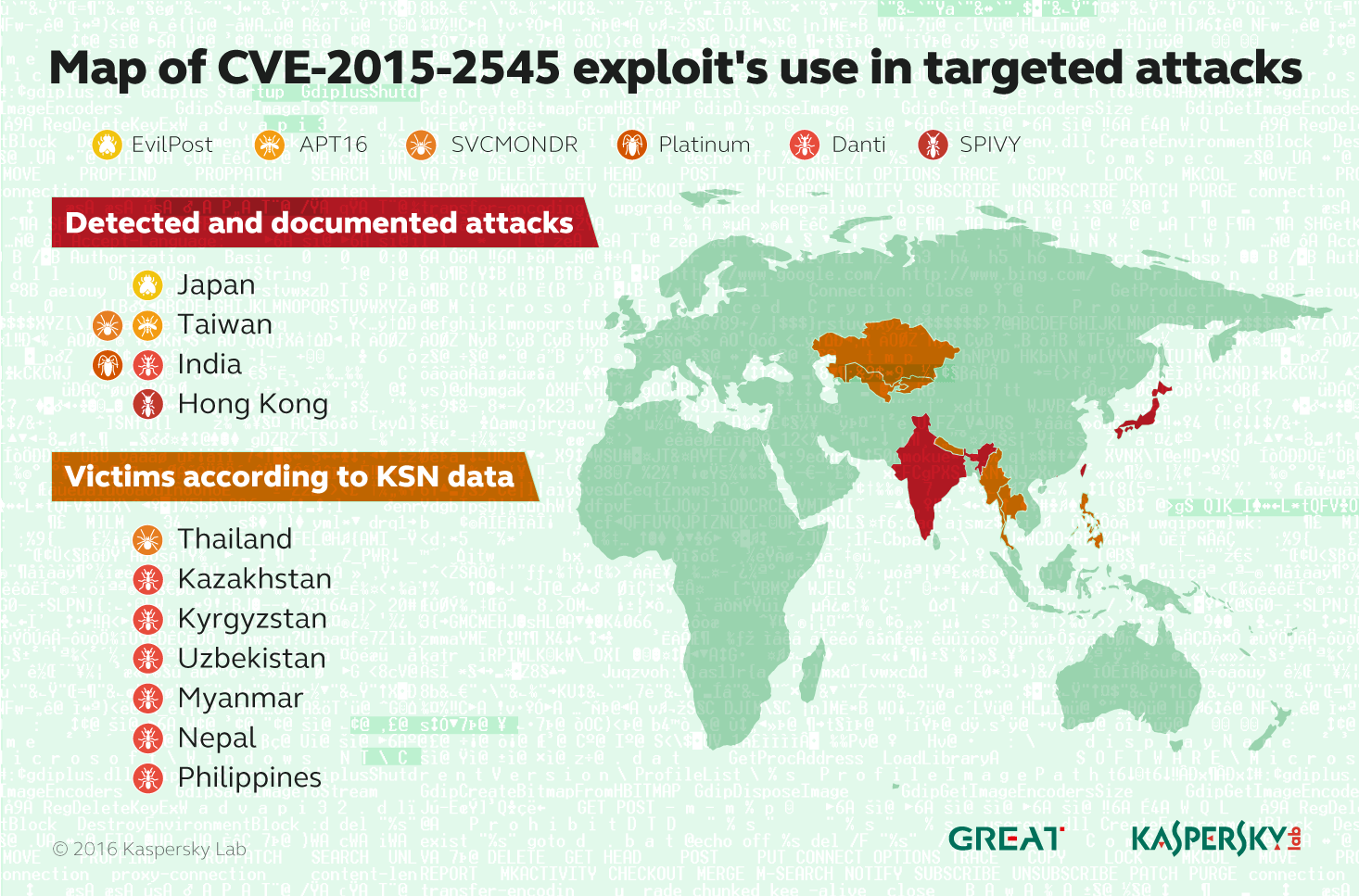
In November-December, two more cyberespionage groups, APT16 (FireEye classification) and EvilPost (discovered by Kaspersky Lab) started using this weakness to break into targets’ security perimeters. Systems where the vulnerability still remained unpatched were now subject to a greater degree of threat than ever – from attackers now fully aware of the vulnerability and how it could most easily be exploited.
A well-crafted decoy letter by EvilPost, written in fine Japanese and targeting the state defense sectorIn all cases, the attack scenario was remarkably simple: neatly made spear-phishing emails containing an attachment resembling an MS Word file (in fact, a Web Archive file), with an embedded EPS containing an exploit, triggering a download sequence for additional malware components from the Command & Control servers. After that, several more groups, such as SPIVY, used different builds of the exploit to break into target systems, with considerable success.
Among the most interesting cyberattacks were those discovered recently by Kaspersky Lab. One of these is attributed to the previously unreported Danti group (according to Kaspersky Lab nomenclature) and the other, though very similar in terms of malware structure, is still described separately and named after its main malware file name: SVCMONDR. Current targets of choice for Danti’s espionage seem to be Indian diplomatic entities; but signs of the group’s activity were also detected in several Asian and Pacific countries, including Kazakhstan, Kyrgyzstan, Uzbekistan, Myanmar, Nepal and the Philippines.
Unlike its counterparts used by other groups, Danti’s (and SVCMONDR’s) initial penetration package also included a packed malware dropper binary within a (pseudo)DOC-embedded .EPS file. In the meantime, the whole build of the group’s toolset suggests simplicity and cost-effectiveness, very much in accordance with the Kaspersky Lab GReAT team’s prediction for 2016.
Again, the same approach was used – exploiting a long-patched vulnerability – which, obviously, still served their shady purposes well.
In each case we are looking at comparatively simple attack mechanisms based on a simple and all-too-common scenario – key patches not applied promptly, leaving the door wide open to attackers.
Grandma, Close the Door!
There are many factors preventing organizations from fixing security holes in a timely and appropriate fashion. Often there is a definite failure in IT security implementation. But this failure is too often dictated by the sheer complexity of the IT security scope being addressed, without sufficient resources to hand. Many companies just cannot afford to hire dedicated IT security staff, and some, even with the necessary budget, find themselves thoroughly confused by the task of juggling many heterogeneous software solutions, each with a different console and management principles.
The most logical way to address the issue is to choose a solution offering a unified approach to different aspects of IT security – including automated vulnerability management – therefore considerably reducing the complexity of this truly overwhelming task.
Fortunately, Kaspersky Endpoint Security for Business Advanced was designed with exactly this thought in mind. Among its many functions, it features a Systems Management component[1] that includes automated Vulnerability Assessment and Patch Management tools. This functionality means the company’s software – both OS and Apps – can automatically be kept up-to-date, saving time which can be used for other aspects of corporate IT security. And, equally important, multi-layered security offers additional proactive technologies to protect against exploits: Automatic Exploit Prevention discerns actions characteristic of exploits and ultimately blocks them, while Network Attack Blocker is designed to block specific network-based exploits.

Another important security layer of Kaspersky Lab’s solutions is our leading Threat & Technology expertise
The notable CVE-2015-2545-using malware is detected by Kaspersky Lab, one of only a few security vendors whose products are currently capable of doing it, under the verdict:
- Exploit.MSOffice.CVE-2015-2545.a
The dropped main backdoor versions are detected under the following verdicts:
- Backdoor.Win32.Danti.b
- Backdoor.Win32.Danti.d
If you would like to know more about CVE-2015-2545-based attacks and the Danti cyber-espionage group, read this GReAT report on Securelist!
[1] Also available as a standalone solution.
 0days
0days

 Tips
Tips