Soon after new malware strikes, security analysis papers appear. You can learn a lot from this research, such as the malware’s origins, penetration methods, creator’s goals. Of course, you also update the databases of your security systems to block the threat, although if you are already under attack, it’s too late — especially if it’s a multistage APT.
Now, imagine that you don’t have to wait for other people’s research. Instead, you start the malware investigation, as soon as you get a suspicious file. That way, you can ensure rapid response and counter the threat before any significant damage is done to your organization.
In this post, we show you how to speed up your own research with the help of our Threat Intelligence Portal. You can request your access to Kaspersky Threat Intelligence Portal here.
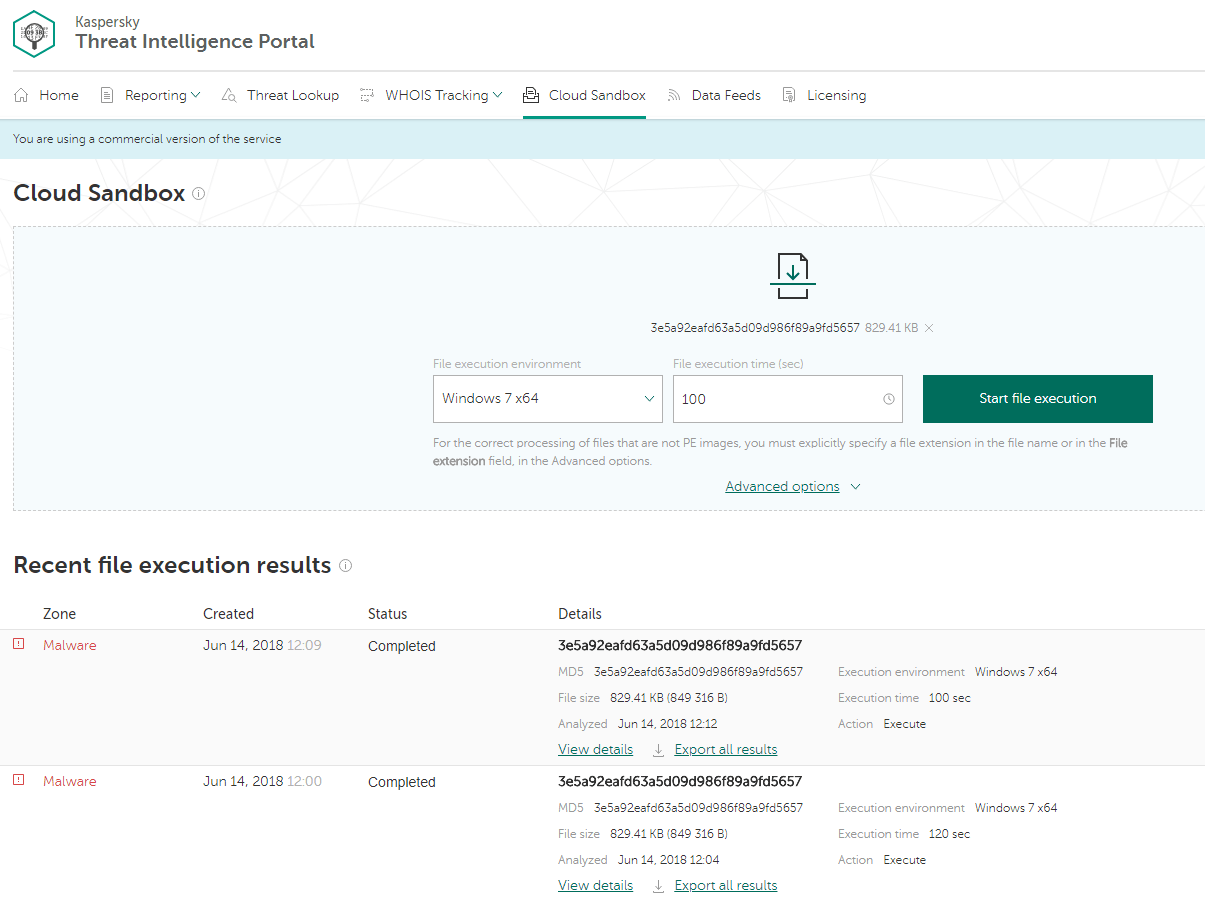
The Threat Intelligence Portal start page has many tabs, but in this case, we have live evidence (a suspicious sample), so let’s go straight to the Cloud Sandbox tab in the top menu. The sandbox runs a suspicious object in a virtual machine (VM) with a full-featured OS. It detects an object’s malicious activity by analyzing its behavior. VMs are isolated from the real business infrastructure, so detonation won’t cause real damage. Just upload your file, select the environment (Windows 7, in this case), select the time (let’s try 100 seconds) and start the execution:
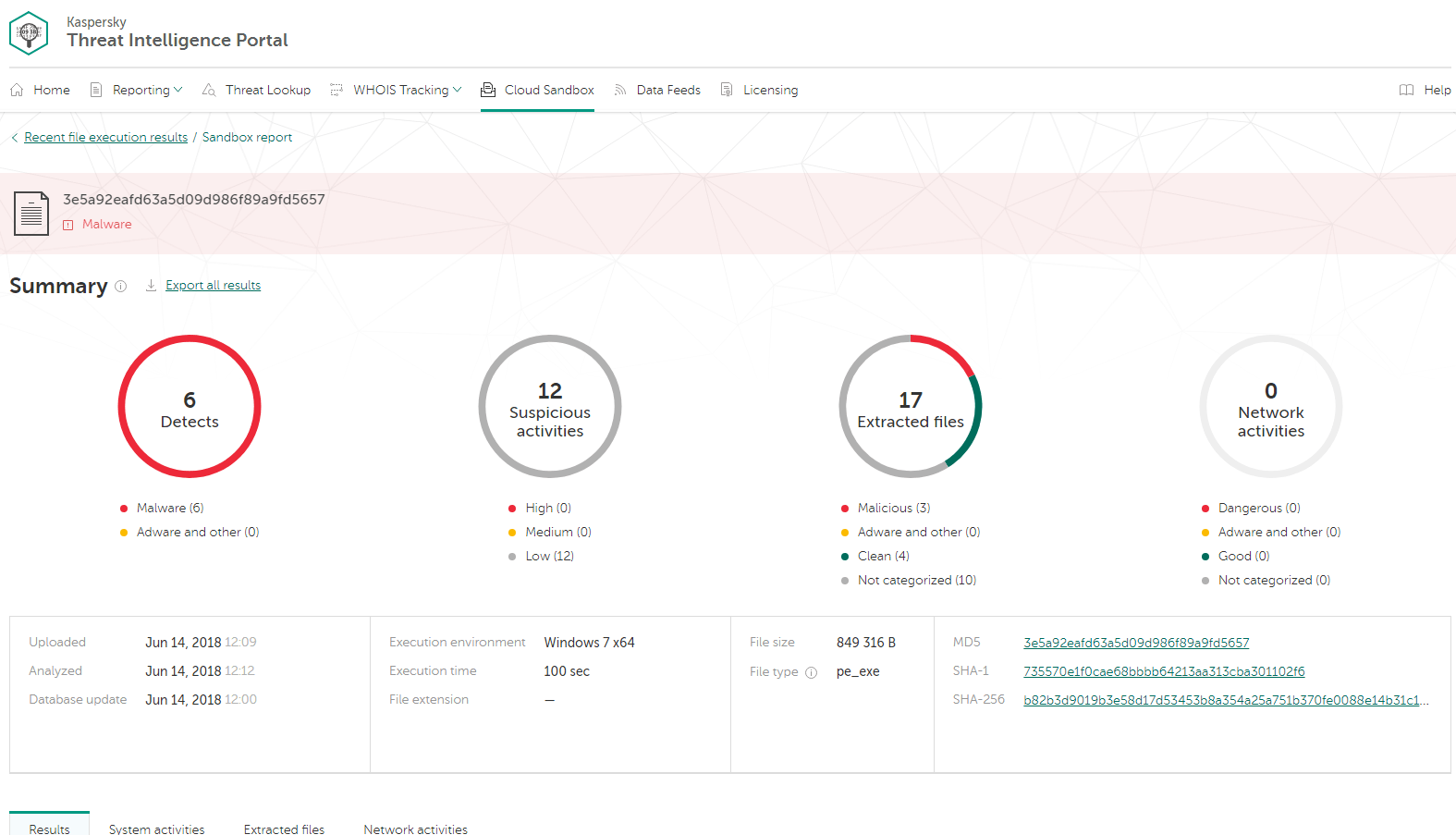
Sandboxes are effective against malware that evades static analysis — that’s why your antivirus could completely miss a suspicious file. Even if this file was identified as “bad,” most antivirus systems won’t explain how bad it is, or what’s actually going on. We need more details. So, let’s see what happens in our Cloud Sandbox after detonation:
Running the tested object, a sandbox collects artifacts, analyzes them, and delivers its verdict. Here’s the summary: detections (6), suspicious activities (12), extracted files (17), and network activities (0). It’s not just a “bad” file; it does a lot of bad things, and they are all listed.
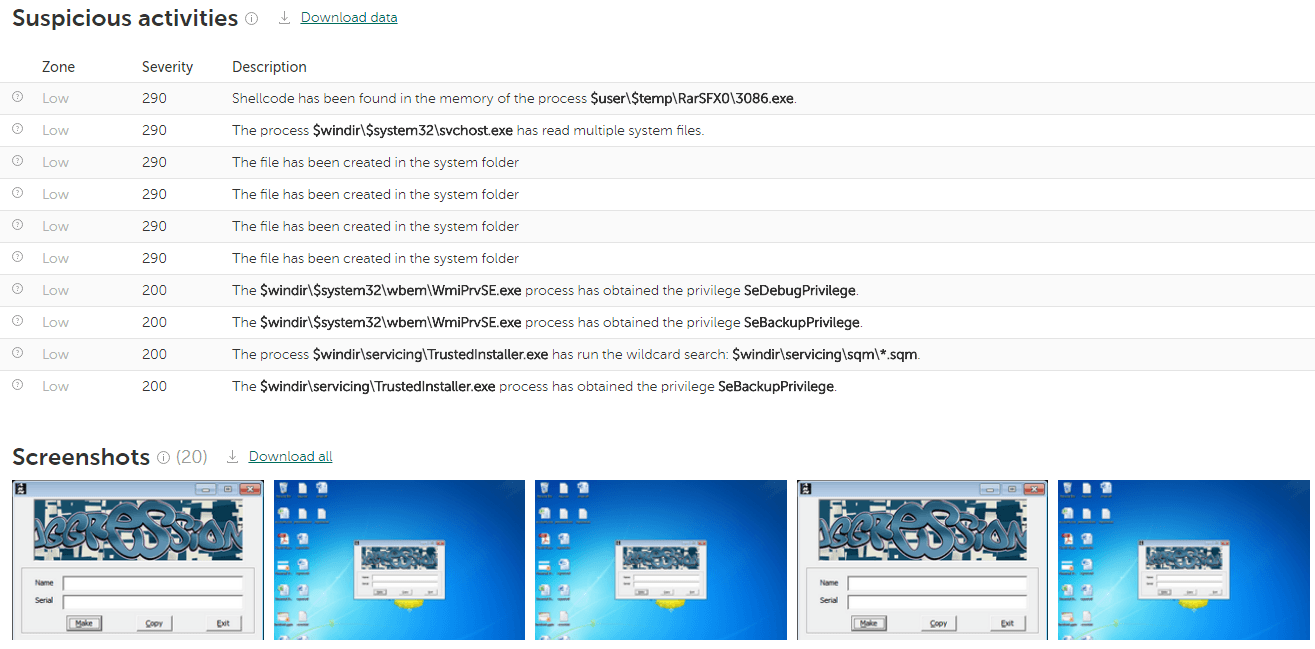
In the Results tab, you can see screenshots taken during execution. In some cases, the malware tries to evade automatic analysis by waiting for user interaction (entering a password, scrolling through a document, moving the mouse, etc.). Our Cloud Sandbox knows many evasion techniques and uses human-simulating technologies to counter them. Screenshots could be helpful too: A researcher can see what’s happening in the “test tube” from a human point of view.
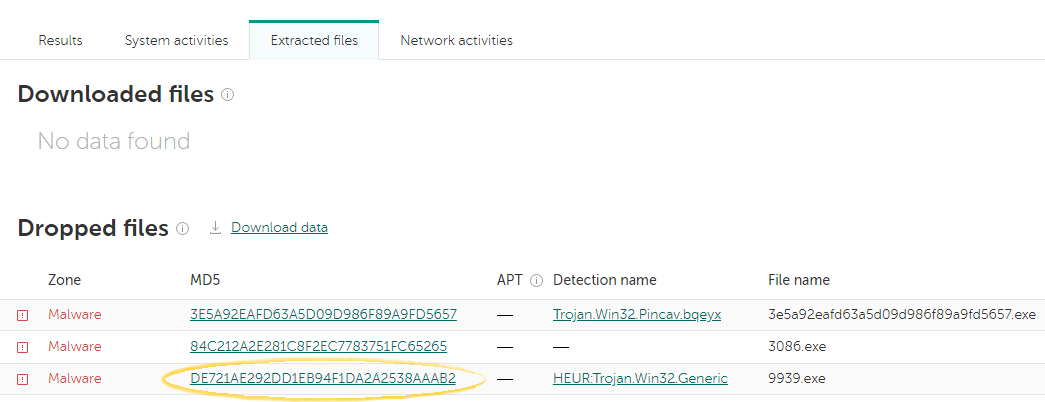
Let’s switch to the Extracted files tab to see what objects were downloaded, extracted, or dropped. In this case, a malicious file was dropped:
Classic sandbox capabilities would end at this point: you ran the file and you got the list of malicious activities — and that’s all. But with our Threat Intelligence Portal, we can jump straight to Threat Lookup to reveal more detailed intelligence on indicators of compromise and their relationships.
Threat Lookup is our search engine for security. It contains about 5 petabytes of threat intelligence, collected and categorized by Kaspersky Lab over the past 20 years: file hashes, statistical/behavior data, WHOIS/DNS data, URLs, IP addresses, and so forth.
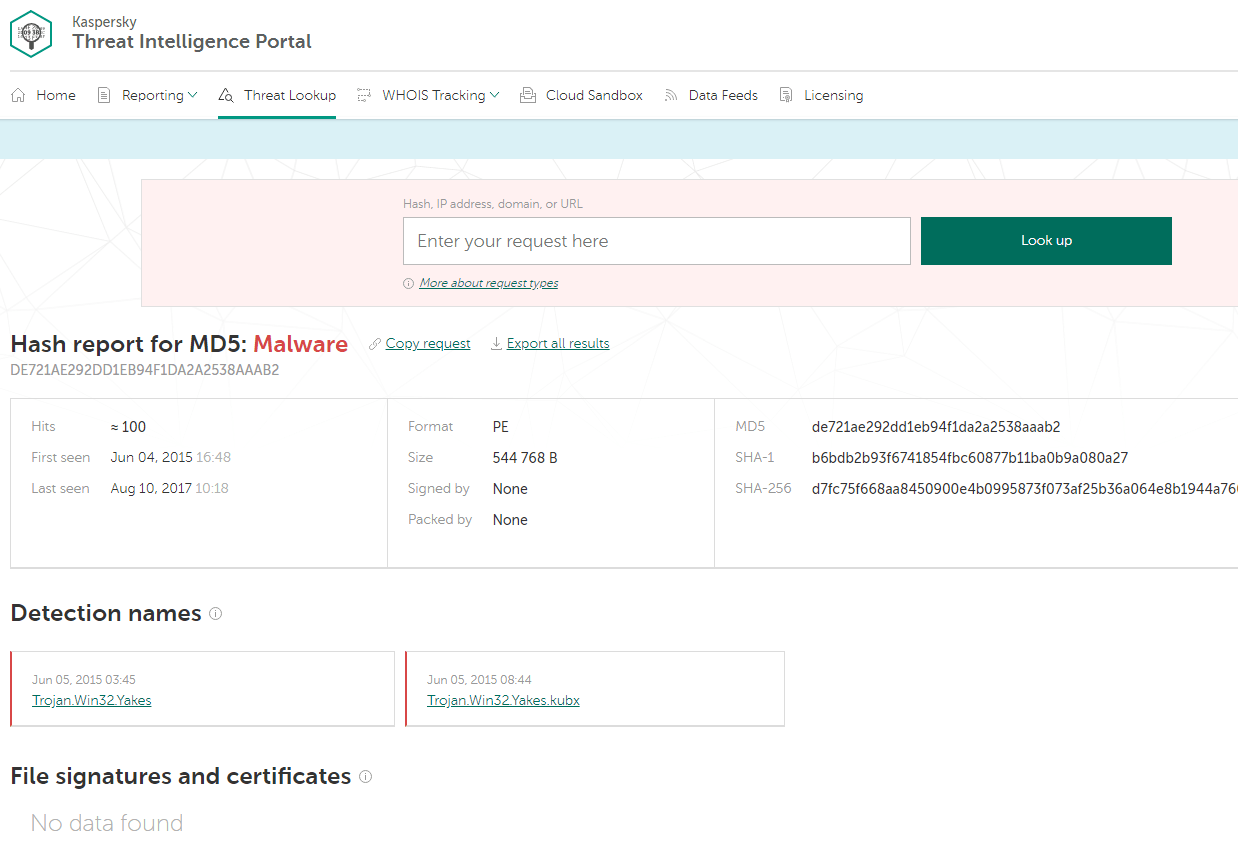
So, after we run our sample in the sandbox, we instantly use sandbox results as search queries for Threat Lookup — just by clicking on the object (an MD5 hash in this case):
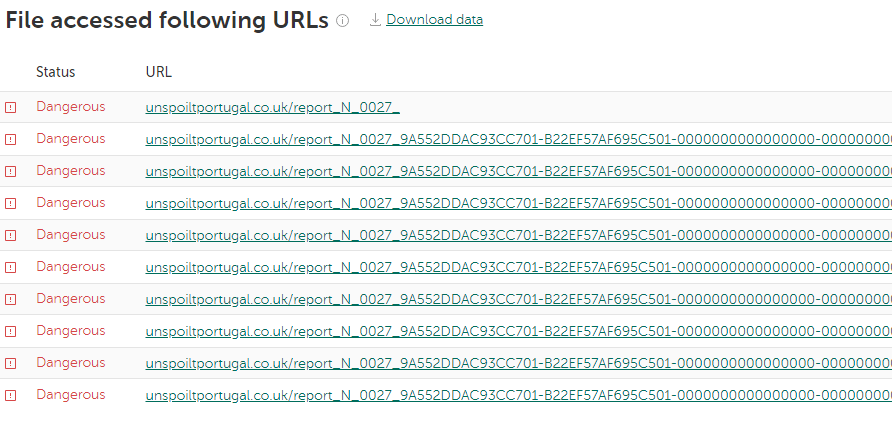
Now we have a more detailed report on the malware. Let’s scroll through the Threat Lookup results to see which URLs were accessed by the malware we’re exploring:
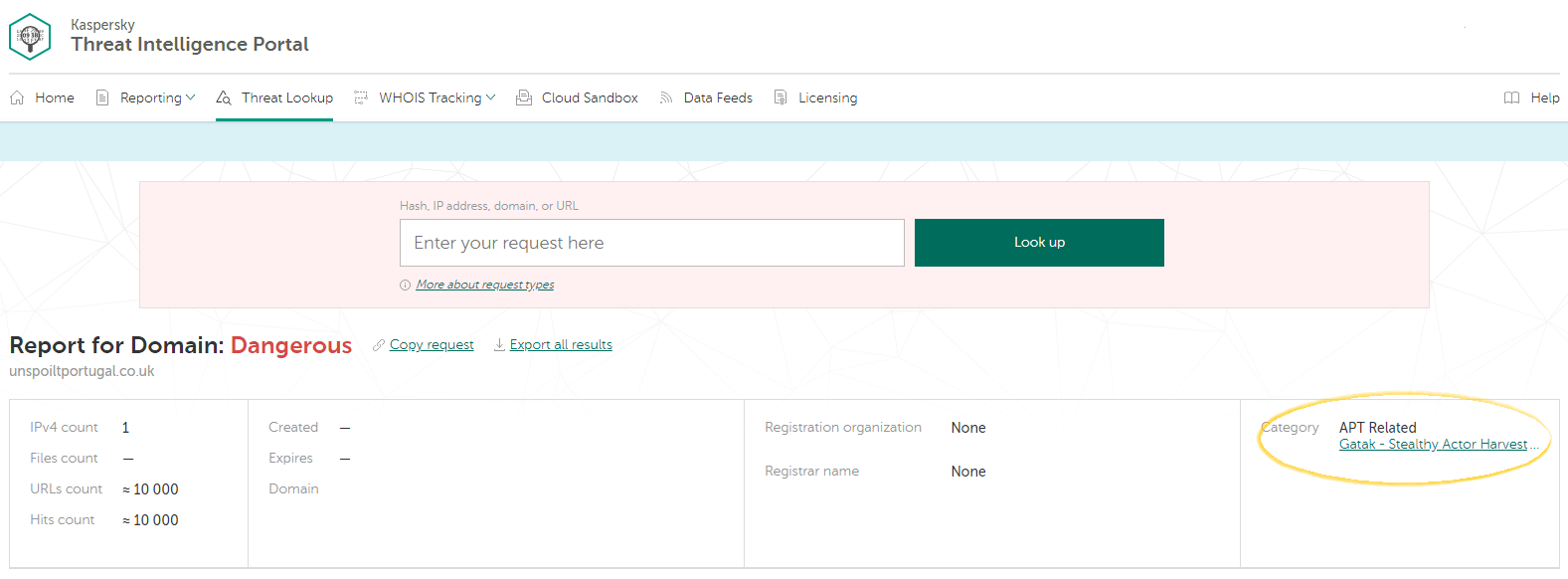
Here’s a URL marked as “Dangerous.” Again, let’s drill down to that malicious URL to see what our Threat Lookup has on it:
It turns out that the malicious URL in question relates to an APT attack! Our Portal offers to download an APT report. This PDF includes an executive summary, deep technical details, and a list of related indicators of compromise. It’s worth checking to find out if anything similar has happened to your organization.
Next Steps
Of course, this isn’t the end of the story: Real incidents require much more analysis. But it’s a good example of how an analyst can begin to build a threat intelligence workflow to run effective and complex investigations. We just put some of the necessary research tools together in one place.
Cloud Sandbox, Threat Lookup, APT Reports, Threat Data Feeds: What other tools could be added to this box? From our point of view, a comprehensive toolbox should include:
- A sandbox for URLs,
- A visualization graph for researching how threat elements relate to one another,
- Malware binary similarity checking,
- Lookup in OSINT and popular social media sources,
- Tailored threat intelligence reporting,
- Expert services including in-depth malware analysis of client samples.
The above are features or capabilities we are currently developing for the platform.
 threat intelligence
threat intelligence




 Tips
Tips