E-mails imitating business correspondence with malicious attachments are nothing new. We’ve been observing them in junk traffic for the last three years at least. The more precise the fake, the higher the likelihood that the victim will not suspect anything.
Such phishing is especially dangerous for employees of companies that sell goods, because e-mails with delivery requests or orders are run-of-the-mill. Even someone trained to spot a fake can sometimes struggle to determine whether a message is phishing or a legitimate order from a client. Therefore, the number of convincing yet fake e-mails keep on growing. They are not encountered as often as traditional malicious spam, but that’s because they are designed for a specific purpose and are sent to targeted addresses.
These past few weeks, scammers have been exploiting the coronavirus outbreak to give their missives extra credibility. The e-mails often cite virus-related delivery problems, prompting the recipient to wonder what delivery they are talking about. In other cases, attackers use the pandemic to press the need to process a request urgently because their usual partners cannot deliver goods in time. Whatever the case may be, the goal is to get the victim to open a malicious attachment. Standard tricks are used as a pretext, usually involving a request to check shipping details, payment data, an order, or product availability.
Below are some specific examples of this type of phishing and the risks involved.
Delayed delivery
The scammers write that Covid-19 has caused the delivery of something to be postponed. They kindly attach the updated delivery information, along with new instructions. In particular, they ask if the delivery time is suitable, thus prompting the recipient to open the attached file, which at first glance looks like an invoice in PDF format.
But instead of an invoice, inside is an NSIS installer that executes a malicious script. The script then starts a standard cmd.exe process, and runs malicious code through it. That way, the code gets executed in the context of a legitimate process, bypassing standard defense mechanisms. The end goal is to spy on the user’s actions. Our e-mail security products detect this threat as Trojan-Spy.Win32.Noon.gen.
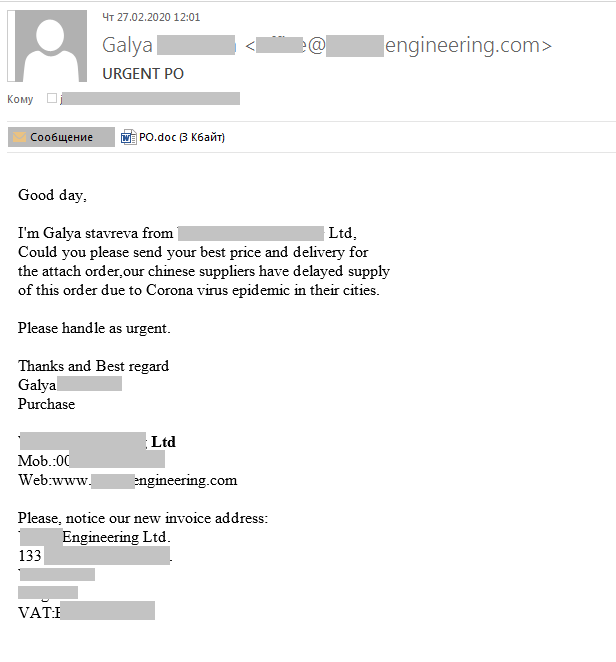
Rush order
The scammers claim that due to the coronavirus outbreak, their Chinese suppliers cannot meet their obligations. It sounds convincing enough under current circumstances. To avoid disappointing their customers, they are supposedly looking to place an urgent order for some goods (unspecified in the letter) from the company where the recipient works. What business can resist such a sudden opportunity?
Surprise,surprise, the attached file contains no such order, but Backdoor.MSIL.NanoBot.baxo. When launched, it executes malicious code inside the legitimate RegAsm.exe process (again in an attempt to circumvent defense mechanisms). This results in the attackers gaining remote access to the victim’s computer.
Another rush order
This is a variation on the above. Again, scammer mentions that a fictitious Chinese supplier is having delivery problems, and inquires about pricing and delivery terms for goods listed in an attached DOC file.
A DOC file is used for a specific reason. Inside is an exploit targeting the CVE-2017-11882 vulnerability in Microsoft Word (our solutions detect it as Exploit.MSOffice.Generic). When opened, it downloads and runs Backdoor.MSIL.Androm.gen. The objective, like all backdoors, is to gain remote access to the infected system.
No time to lose!
This scheme is aimed at companies that are experiencing workflow disruptions due to the coronavirus pandemic (quite a large group and growing). The scammers press the recipient into acting, while expressing hope that the company can resume work after the coronavirus disruption.
Instead of an order, the attachment contains Trojan.Win32.Vebzenpak.ern. When launched, it executes malicious code inside the legitimate RegAsm.exe process. The goal is again to provide the attackers with remote access to the compromised machine.
How to guard against malicious e-mail attachments
To prevent cybercriminals from slipping you a Trojan or backdoor in the form of an attachment, follow these tips:
- Carefully examine the extensions of attached files. If it’s an executable, the chances of it being unsafe are close to 100%.
- Check if the sender company actually exists. These days, even the tiniest firms have an online footprint (for example, social media accounts). If you find nothing, do nothing; either way, it’s probably not worth doing business with such a company.
- Check if the details in the sender field and the automatic signature match. Strangely enough, scammers often overlook this detail..
- Remember that cybercriminals can pinch information about their “company” from open sources. So if you have doubts even though the e-mail seems to contain bona fide information, reach out to the company for confirmation that theysent the message.
- Most importantly, make sure that your company uses a reliable security solution both at workstations and at the mail server level. And make sure that it is regularly updated and uses up-to-speed databases. If not, it can be difficult to determine whether an e-mail attachment is harmful, especially in respect of Office documents.
 phishing
phishing




 Tips
Tips