Kaspersky Lab hosted the Kaspersky Cybersecurity Summit 2015 in Singapore this April, dedicated to enterprise IT Security challenges – and solutions.
The motto for the event was: “Business under attack: adapting to the inevitable”. Enterprises are targeted, of course, but in some cases – given the amount and sophistication of threats – companies don’t have to be targeted to become victims. We now live in the world of “when”, not “how”, and that’s what the Kaspersky Security Summit is about, among other things.
Risks to business continuity #enterprisesec
Tweet
The most advanced and sophisticated threats tend to emerge at the enterprise level, where criminals are hunting for the “top prizes” such as secret and highly sensitive information valued at millions, or access to corporate banking accounts where millions are stored. After these advanced hacking techniques are successful at the enterprise level, criminals start using them against lower-level targets. Among the recent examples – Carbanak APT: the eventual attacks on ATMs have been preceded by the massive “recon” operations to gather and analyze data.
Working the cyberthreats at the enterprise level we are almost certainly capable of mitigating them at any other level, too.
One of the key areas of focus and responsibility for the enterprise CIOs is, of course, the continuity of the business. Certainly not the only one, but for a large business its continuity is especially critical. Processes should not halt; every interruption will have dramatic and long-playing repercussions. Especially when it comes to a larger businesses: restarting everything and restoring it to normal requires huge efforts – just imagine stopping and then relaunching an entire array of production lines or halting and then relaunching logistic processes. A large enterprise with lean processes – ordering, production, shipments – suddenly experiences a severe interruption because of a certain cyberincident: one of its departments systems go offline, the entire company experiences heavy drawbacks, and direct and indirect losses, and so do its partners.
Just because of a single piece of nefarious code.
Another good – if not extreme – example here is a successful cyberattack on industrial systems, SCADA or even PLC, that effectively halts production lines. Industrial networks were considered more secure because of higher isolation from public networks. But 35% of all cyber incidents there happen because of malware attacks; and that malware arrives on USB sticks or injected through third party software and firmware. Moreover, today’s industrial systems were often built without an “IT security-in-mind” approach – a design flaw which was not at the time these systems were built.
A simpler example would be a potent DDoS attack that cripples entire data centers, or knocks them out of commission: even if just a single entity leasing that data center facilities are targeted, overkills are numerous. What is more troubling is that downtime may be too long for all affected parties: almost every fifth cyber incident takes longer than 24 hours to recover, which is absolutely unacceptable for anyone, especially large enterprises.
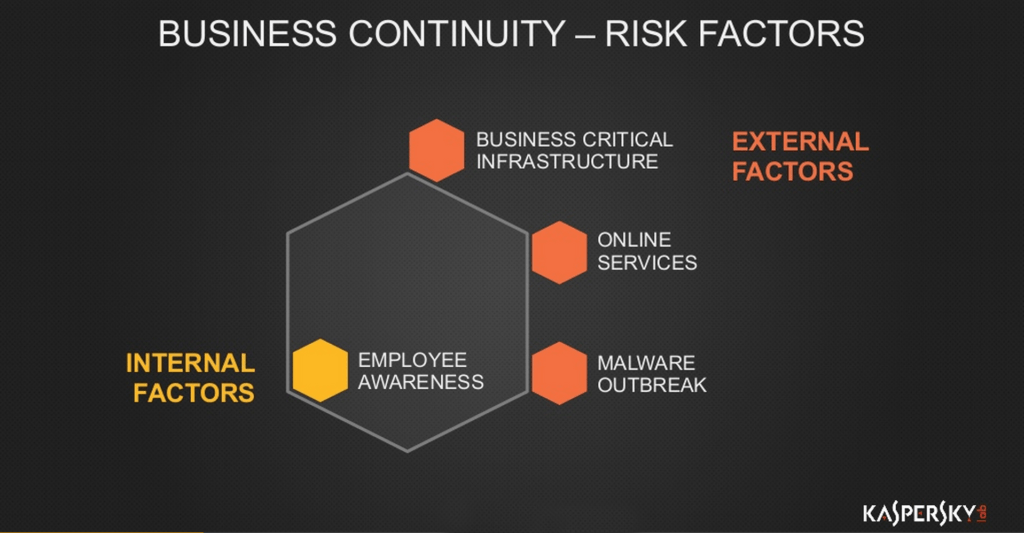
One of the charts in my keynote today (see below), shows major risk factors for business continuity:
The first group of risk factors include such external causes as malware outbreaks that may happen on desktop, mobile or virtual environments, unless those are properly secured; DDoS attacks that are aimed to disable customer-facing services such as online registrations, ticketing, etc. Today, the truth is even grimmer: there are sophisticated DDoS attacks that may be launched against any online service, including non-public ones.
#Cyberattacks on any given organization are merely a question of time
Tweet
Internal factors aren’t to be discarded either: unless employees have a notion of information hygiene, cyberattacks and malware incidents capable of interrupting the business continuity are very likely. Attempts at cyberattacks are inevitable. Their success, in turn, depends on how well-prepared the businesses are to stand against them, and how well suited their IT security is.
Our key message is that to prepare for the inevitable, you need to rethink your IT Security. As IT security has become a broad issue, it is time to invest in a comprehensive security suite that is provided by a trusted partner with deep security intelligence – such as Kaspersky Lab.
Learn more about Kaspersky Lab new Enterprise portfolio at http://www.kaspersky.com/enterprise-it-security.
Check out our Enterprise Security Vision:
 Kaspersky Cybersecurity Summit. KCSS
Kaspersky Cybersecurity Summit. KCSS