These days, the propagation of zero-day exploits occurs almost literally at the speed of light. As soon as such useful exploit makes it to the public, APT authors can begin adding them into their creations right away. During a month when we have already written about the latest forays of Darkhotel attackers, who adopted a zero-day from the Hacking Team’s stolen materials, we now find this Adobe Flash vulnerability reaching the Land of the Rising Sun. On this occasion, APT actor BlueTermite decided to embed it into their toolset.
From Italy to Japan with persistence
This attack itself is “persistent” in more senses than one. It has been active since at least November 2013, and has an interesting peculiarity, in that, geographically, it strongly references Japan. Its victims, of which the Japanese Pension Service and Health Insurance Services are examples, are located only in this country, as are BlueTermite’s own control servers.
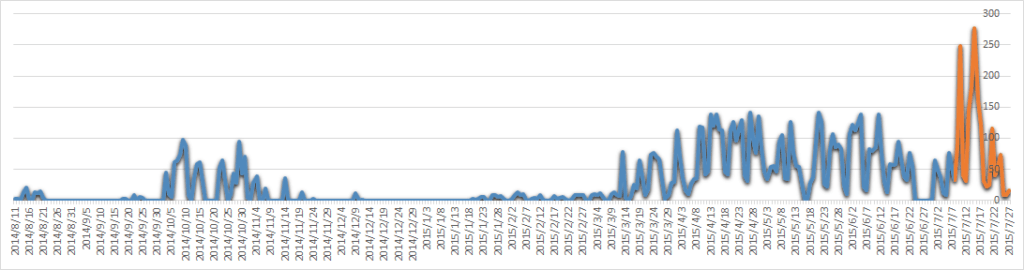
A burst of activity in mid-summer of 2015, as shown on the above graph, is easy to explain. This is the point at which the APT received the new infection method. While prior to July 2015 BlueTermite used only spear-phishing to spread itself, this is the point at which drive-by infection was added. It’s interesting to note that amongst the infected web-sites was the network resource of a Japanese government member. Such waterholing precisely targets the country’s political circles.
Japanese national threat cuisine: served individually, with zero-day flavor #APT
Tweet
One more interesting aspect of attacks is that, in order to decrypt code in the infected “emdivi t20” BlueTermite uses the decrypt key generated from a unique ID based on victim’s hardware. Once again, the attack is “persistent” on many fronts: besides sticking to its own country, its toolset clings to the infected system, forestalling any attempts at cloning or similar research methods. A more detailed description of BlueTermite can be found here.
Also, check out our new video with Suguru Ishimaru, Junior Security Researcher Kaspersky Lab Japan, who has authored the linked above Securelist article, reports on BlueTermite discovery:
In view of the above, it may appear that actor’s interest in the HackingTeam exploit is massive. But, in all truth, the same story could be told about every emerging zero-day that hits the wider public: cybercriminals hurry to reap the benefits of the ‘still not patched’ period.
If companies don’t want to become victims, they need to acknowledge the possibility of such attacks and be prepared. At the very least, businesses should immediately install critical patches, as soon as they are provided. Of course this won’t nullify the probability of a targeted attack, but greatly reduces the risk.
How Kaspersky Lab products defend from BlueTermite APT
Kaspersky Lab products detect the BlueTermite’s modules using verdicts from the table below.
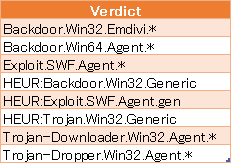
Zero-day malware prevention
Heuristic algorithms exist for previously unknown malware samples that cannot be detected using databases. These algorithms are based on a knowledge of both structure and emulated behavior typical patterns. Actual process behavior is subject to monitoring as well; System Watcher module is capable of discerning suspicious behavior patterns and blocking unwanted activity.
Kaspersky Lab’s Automatic Exploit Prevention functionality is designed to fight exploits, including zero-days, and is highly effective in detecting BlueTermite components. The Heuristics and Automatic Exploit Prevention components of Kaspersky Lab’s advanced antimalware engine form a crucial part of a multilayered, comprehensive defense.
Meet the BlueTermite #APT
Tweet
Apply patches in time
Regularly updating to the latest version of installed software and patching OS will help prevent a vast range of attacks. Timely patching is most easily achieved using a Patch Management toolkit, such as by Kaspersky Lab’s, working together with or instead of Microsoft WSUS. Vulnerability Assessment and Patch Management[1] combined will also update all popular third party software to the latest versions. Employing Kaspersky Lab’s automated tools helps reducing the ‘patching gap’ between the release of the patch and its deployment, therefore greatly reducing the risk of falling victim to ‘yesterday’s 0-day’.
Control servers known URLs
When command and control (CnC) servers of any targeted attack are determined we add their addresses into our security database. Kaspersky Lab clients can obtain all the current information about active CnC servers from our special data feed. This feed could be used (e.g. in customer’s SIEM system) to alert system administrators about any communications with these malicious servers.
[1] Vulnerability Assessment and Patch Management are included in Kaspersky Total Security for Business, Kaspersky Endpoint Security for Business Advanced and Kaspersky Systems Management.
 APT
APT

 Tips
Tips