Early in June, Kaspersky Lab rolled out an update for its products which included Intrusion Detection System, and now it has an ability to detect RDP (Remote Desktop Protocol) bruteforce attack attempts. The statistics gathered since then appears to be pretty much “sunless”: dozens of thousands victims, +1000 unique detects each day since June 3rd. A number of possible attackers had been identified already, but the investigation is ongoing. IDS detects this type of attack as Bruteforce.Generic.RDP.
Remote Desktop Protocol is Microsoft’s proprietary protocol providing a user with a graphical interface to connect to another computer over a network connection. It’s widely used by system administrators to control servers and other PCs remotely, and occasionally – by common (okay, advanced!) users too.
A brute-force attack has its peculiar name for a reason: since it consists of systematically checking all possible keys or passwords until the correct one is found (which is brutishly primitive), it requires a formidable computing power, but, in turn, it can also be successfully used against almost any encrypted data, except for the one encrypted in an information-theoretically secure manner (Wikipedia has some layman-comprehensible explanation for this).
But still, when it comes to dealing with short passwords, this method can be fast-and-easy, especially when good computing resources are available and the passwords are weak (the weakest are the simple dictionary words). It’s less effective with longer and complex passwords, but again, with distributed resources (a large botnet, for instance) it’s relatively easy to crunch passwords – and in numbers.
Last year we saw a wide-scale bruteforce-attack on WordPress admin consoles: someone behind a massive botnet launched a “gut check” of users’ passwords. The bombardments were so heavy that they had effects of plain DDoS-attacks.
Now (and, apparently, for quite a long time) it’s RDP that is actively targeted with brute-force attacks.
Although developed by Microsoft, RDP clients are available for all the most used modern OS, including Linux, Unix, OS X, iOS, Android even. Server software exists for Windows, Unix and OS X. By default, the server listens on TCP port 3389 and UDP port 3389.
Hacking an RDP-connection is very lucrative: once an attacker gets login-password pair for RDP, he or she effectively owns the system where the RDP server is installed. Attackers can then plant malicious software in the affected system, exfiltrate data, etc. He (or she) also can gain access to your company internal network, given that the “penetrated” workstation is connected to it, or attempt to check out all of the passwords in the browser installed on the affected system. Opportunities are multiple, and the consequences can be dire.
Criminals are well aware of it. There is already a handful of off-the-shelf software purposed for cracking RDP login-password pairs – ncrack, Fast RDP Brute, for instance.
As the screenshot shows, the interface of Fast RDP Brute is very straightforward and simple. There’s only one thing shown wrong: the “good” pair “admin:admin” is actually as bad as it gets. :-)
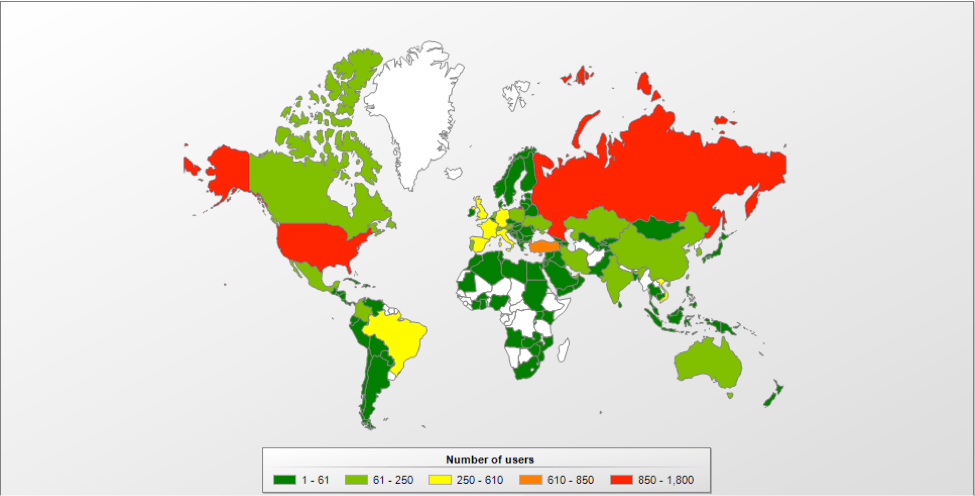
And here is what the statistics on RDP attacks on our users looks like:
As we can see, Russian Federation and United States are the most attacked countries overall, followed by Turkey. Western European countries are under fire too, as well as Brazil.
About 64% of the targets are servers which is no surprise either.
Attackers usually don’t choose specific targets from the start. First they launch some wide-scale campaigns in order to gather a most-likely lengthy list of vulnerable targets that they would then sort by their potential value. Still, hijacking a server is a much more lucrative result than infecting a lowly Windows XP-based 10 years old PC. While both can be used to relay spam or launch DDoS-attacks, owning a server means getting much more computing resources and broader communications channels, as well as, potentially, a total control over all outgoing and incoming traffic. And that is something to go for in a case of a targeted attack on the business, to which this server belongs.
Apparently there’s just one way to counter such attacks: chose passwords wisely, and change them often.
 brute force attack
brute force attack


 Tips
Tips